¬¬Just about every business has a website these days but very few businesses know how to effectively use their websites to get more customers. There are two different things that a business owner needs to do to increase their website traffic: optimize their site so that search engines can find them easier and promote their site on the internet so that they have greater visibility. This article will discuss how to optimize a website.

Materials Needed! Video: Undo a door's chain lock from outside with string, yarn or shoelaces.

Step 1: Have most of the Jackass crew think they are doing a photo shoot for the upcoming movie. Schedule the shoot in a tear gas chamber that is dressed to look like a photo set. Have secret film cameras planted in the chamber so you don't have any obvious camera men walking around with gas masks on inside the room.

So, you're all excited you went ahead and 'upgraded' your iPhone 3G to IOS 4.0X so you could reap all the benefits of all the new features.

The two-hook panfish rig is meant for vertical fishing under the boat in fairly deep water, for deep-dwelling fish like crappie, catfish, bluegills, and sometimes even bass. It involves two hooks hanging off the line, off droppers, to fish close to the bottom. Watch and learn as Wade Bourne of MyOutdoorTV shows you how to fish a two-hook panfish rig.

To make a paper shotgun you will need some tape and three pieces of paper. With the first piece of paper roll it up into a medium size tube and tape down the ends. The other piece of paper is going to work as the handle. Roll that piece up into a tight roll and secure it with tape to one of the ends creating the handle. The last piece of paper is going to be used as the bullets. Cut this piece into three even pieces and roll each piece into a cone shape sealing the end of each cone with tape....

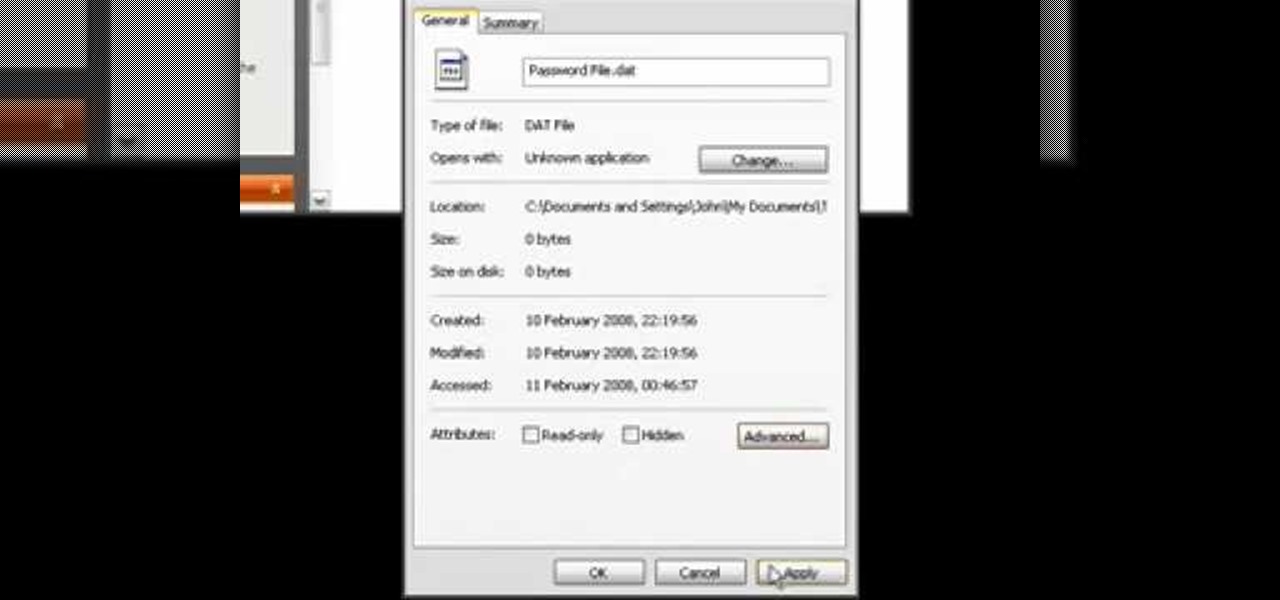
If you have files on your PC that you don't want other window's accounts to be able to access, you can encrypt them. Right click the file that you want to encrypt and select properties from the drop down menu. Once the properties page comes up, choose advanced. Now choose Encrypt contents to secure data and click ok. Now you click on apply. Select encrypt the file only and click ok. Hackers and administrators will not get an access denied message when they try to open the file. To make things...

Learn how to tie the Boy Scouts trucker's hitch knot. The Trucker's Hitch (Lorry Knot in the UK and parts of Canada) allows the scout (or sailor or whatever) to easily tighten a rope, yet easily untie the knot. Its most common use is for tying loads (thus the trucker moniker) such as a canoe to a cartop, a tarp to trailer or any application where a very tight rope is needed. It provides the advantages of a block and tackle, without the heavy hardware.

Learn how to do the Amazing Silk Escape with magician Ryan Oakes. You'll be able to entertain your family and friends with this great trick. You will need a clear glass, a

A well-designed terrarium is essential for the health of your reptiles. This how-to video demonstrates the process of making a backdrop for your pet's terrarium. Start out by lining the aquarium with strips of bark. Then use caulk to secure them into place, and allow to dry for 36 hours. Apply eco-dirt to the bark, and then shake and brush off the excess. Watch this video pet care tutorial and learn how to build a backdrop for a reptile terrarium. Build a backdrop for a reptile terrarium - Pa...

Watch this video from This Old House to learn how to build a stained-glass bar cabinet. Steps:

Watch this video from This Old House to learn how to put in a ceiling fan. Steps:

Watch this video from This Old House to learn how to install a deadbolt lock. Steps:

Watch this video from This Old House to learn how to replace an old threshold. Steps:

Watch this video from This Old House to learn how to install a rain diverter. Steps:

Watch this video from This Old House to learn how to fix a bath sink stopper. Steps:

Watch this video from This Old House to learn how to install a utility sink. Steps:

Watch this video from This Old House to learn how to prevent frozen pipes. Steps:

Watch this video from This Old House to learn how to install a frost proof faucet. Steps:

Watch this video from This Old House to learn how to repair shingle siding. Steps:

Watch this video from This Old House to learn how to repair a baluster. Steps:

Watch this video from This Old House to learn how add stairway headroom. Steps:

Watch this video from This Old House to learn how to transplant a tree. Steps:

How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Angry Birds and FarmVille have become two of the biggest game franchises in the world. And recently their creators, Rovio and Zynga, have hit the news again, but not because of anymore major game announcements.

The days of trundling hoops, hopscotch and painted wooden rocking horses are long since past. The latest trend in toys? Biofeedback. Electroencephalography. A decade into the 21st century, the toy market is awash in products that incorporate functional neural sensors.

The battle between Pepsi and Coke has been a grueling one, with both sides securing their secret formulas for great tasting, addicting sodas behind lock and key.

Health, safety and security are three main issues which determine if your cruise is a successful vacation.

Microsoft's new mobile operating system is officially out on the market, and programmers are hard at work developing new mobile apps for Windows Phone 7 devices. But there's a lot going on in this new platform, which means there's a whole lot to be learned, and the only man in the world with a Windows tattoo is here to help— Charles Petzold.

Willow Smith has what it takes to be a star, just like her parents, Will and Jada Smith, and her brother, Jaden Smith. But this Smith, at the tender age of 9, is quickly becoming a pop superstar and preteen trendsetter, thanks to her music video "Whip My Hair".

How to Build a Basic BirdhouseMaybe you were outside in your back yard and you noticed that it seemed a little lonely and empty. Our maybe you have young kids that love to experience wild life in their own back yard. Whatever reason you have for searching out this article, you have decided to build your very own basic bird house. I recently built a deck in my back and had alot of scrap 1x6 decking boards left over. Instead of letting all that good material go to waste, I decided to build a co...

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a mouse.
From Infowars: “Of course, at this stage Mr. Paul is little more than a distraction to Mr. Romney, and the two candidates are said to be quite fond of each other. Until now, Mr. Santorum had also been pinning some of his hopes on Texas, which, with its 155 delegates, has the most delegates of any contest to date,” writes Gerry Mullany.

Watch out Macs. Flashback is back. Variations of the trojan have reportedly infected 600,000 Mac computers around the globe, with about 57 percent in the U.S. and another 20 percent in Canada.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

In this article, I'll show you how you can make your very own bullet/shell bottle opener. All you need is a .50 caliber deactivated round and some workshop tools!

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.