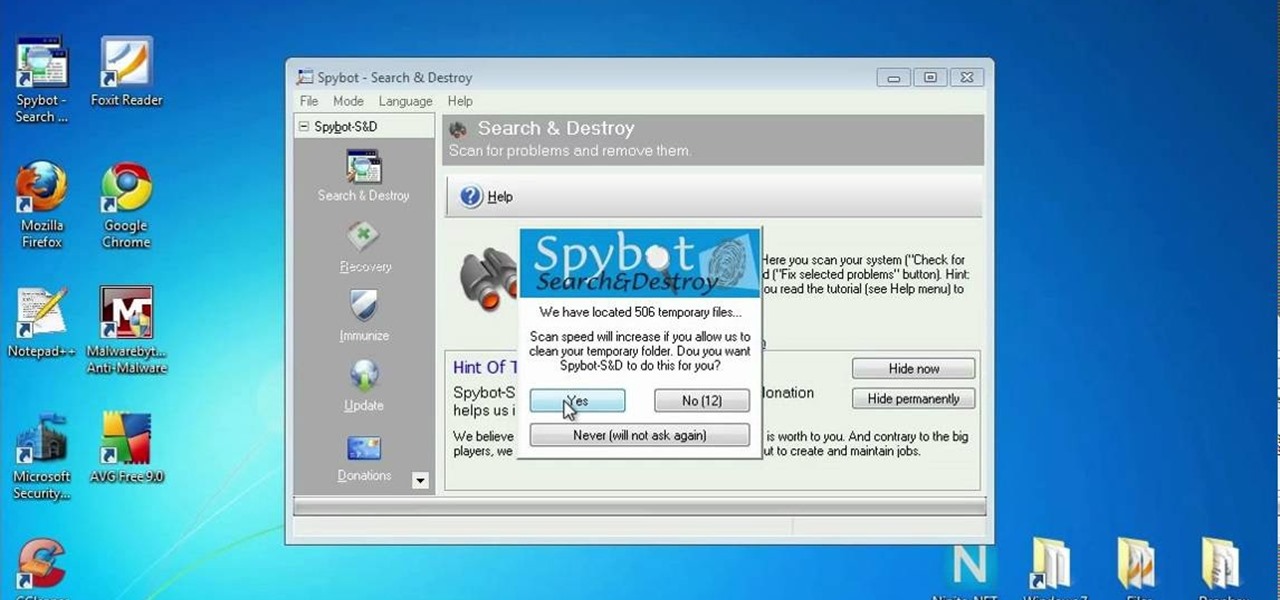
Looking for fast cash with no questions asked? There are legitimate ways to get it, if you're willing to pay the consequences. You will need a credit card with unused credit, a tax refund, a car, a small loan company, a signature loan company, or a payday loan. Watch this video tutorial and learn how to get money quickly by finding a loan shark.

In this three-part video tutorial, learn how to manage loans with an amortization table in Excel. The three parts of this video go over the following:

Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to secure your Gmail account.

Are you under a backbreaking amount of debt? In this economy, we don't blame you. If credit card bills, mortgages, and bank loans are making you want to crawl into bed and pull the covers over your face, then check out this video to learn how to consolidate debt.
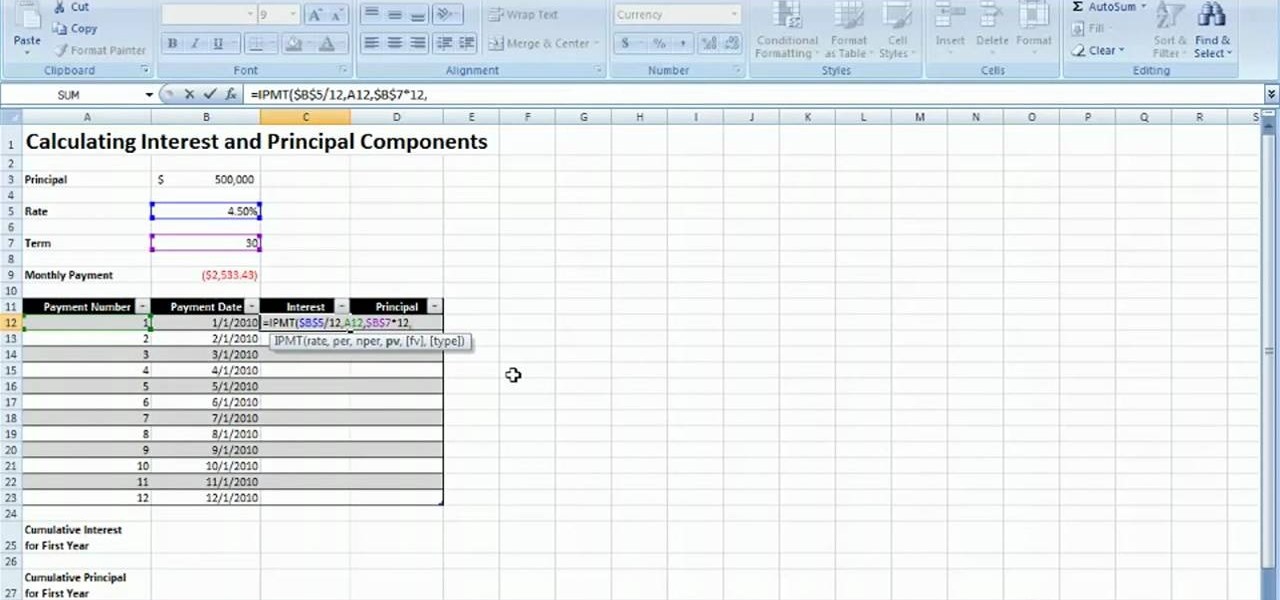
Learn how to calculate interest on loan payments with Microsoft Excel 2007. Whether you're new to Microsoft's popular digital spreadsheet application or a seasoned business professional just looking to better acquaint yourself with the Excel 2007 workflow, you're sure to be well served by this video tutorial. For more information, and to get started making your own loan payment calculations, watch this free video guide.
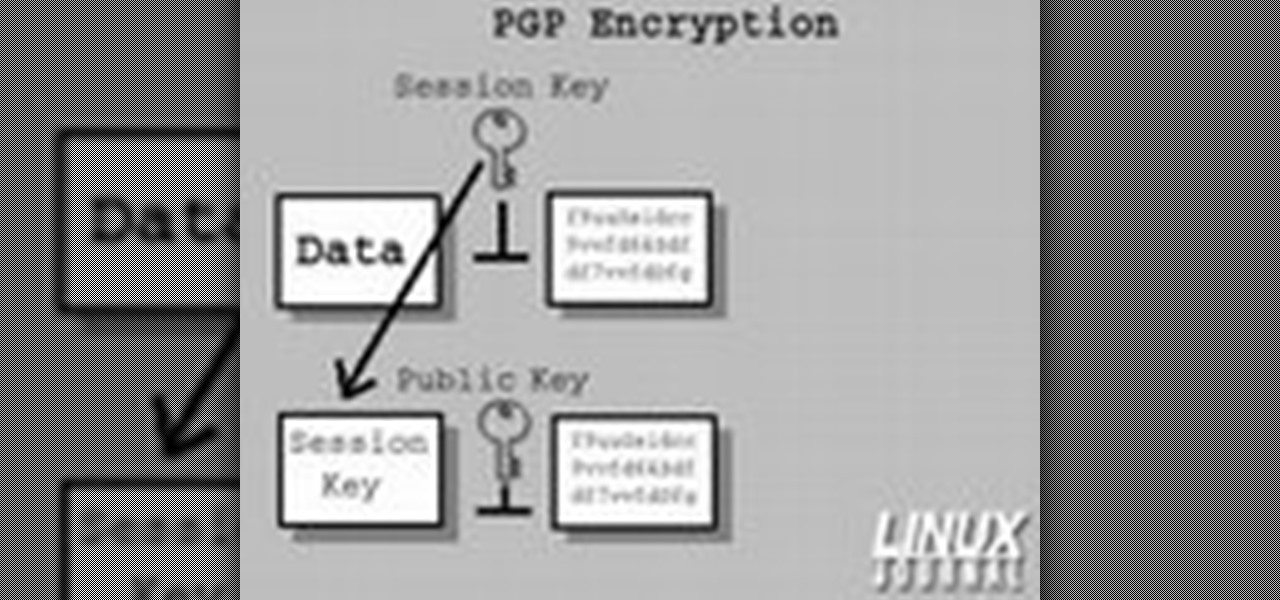
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

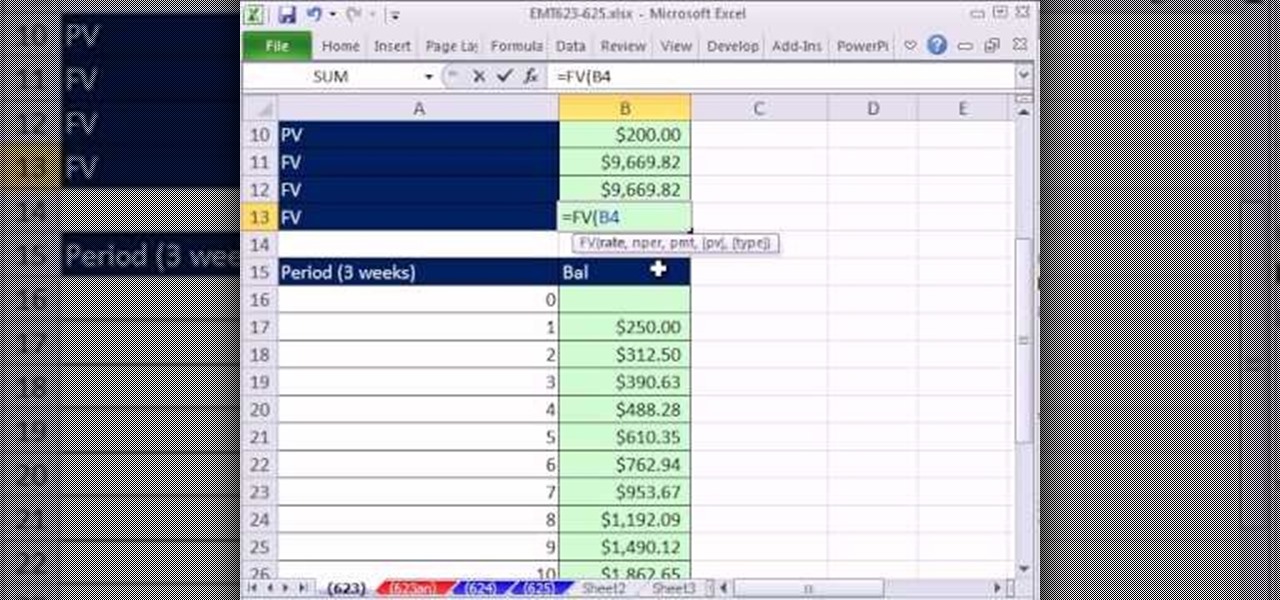
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 623rd installment in their series of digital spreadsheet magic tricks, you'll learn how to see the pain that pay day loans inflict on people using Excel. Learn how to calculate APR (Annual Percentage Rate), EAR (Effective Annual Rate), an Amortization Table and the EAR for a loan that takes a fee out up front. Learn ...

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 47th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to use the PMT function to calculate payments. Specifically, this video addresses the following topics:

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

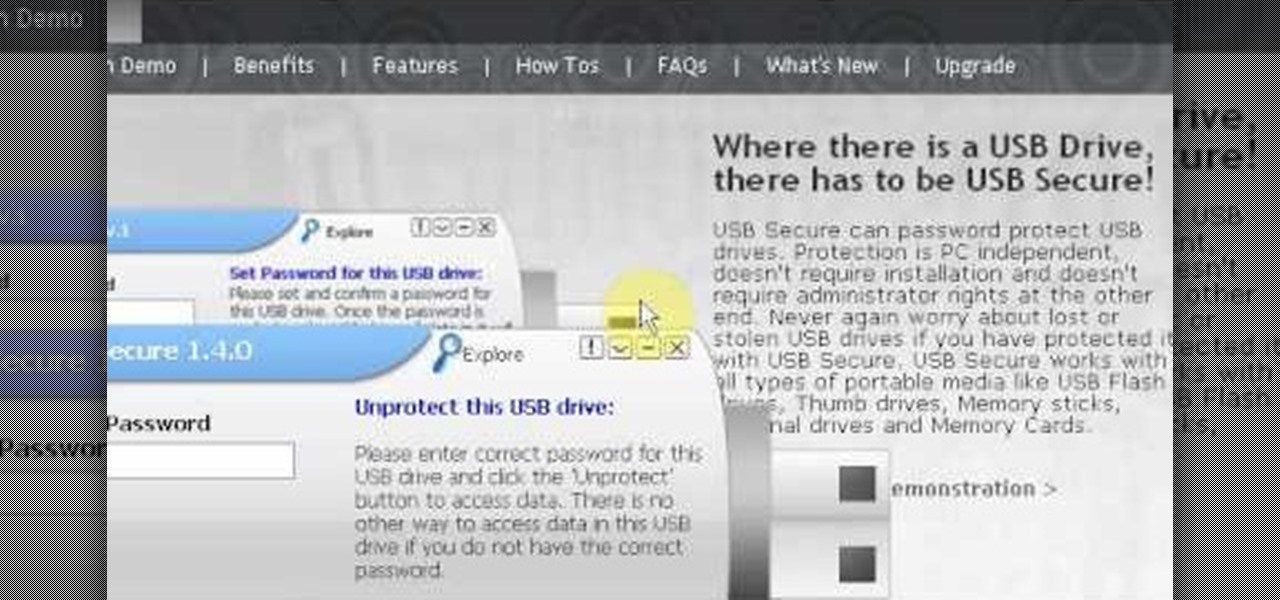
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

Use three tools to create a simple ponytail. Use a hairbrush, a bobby pin, and a bungee band holder for this look. Using a bungee band instead of a standard ponytail holder eliminates some of the issues typically caused by pulling hair through ponytail holders. Start by using a bristled brush to brush the hair to one location on the head. Secure one hook of the bungee band in the ponytail and wrap the tail around the rest of the hair. Wrap it around again, and secure the other bungee band hoo...

Using ASP.NET Secure Services and Applications Services

Need to know how to tie a Bowline with a few ways of securing it? This way shows you how to secure it with a seizing so that it won't accidentally come undone. Included is a little variation of the bowline with a built-in seizing. If you don't have electrical tape to secure the bowline feed the bitter end back through the hole. It also makes it so you don't have a tail line dangling if you're towing something.

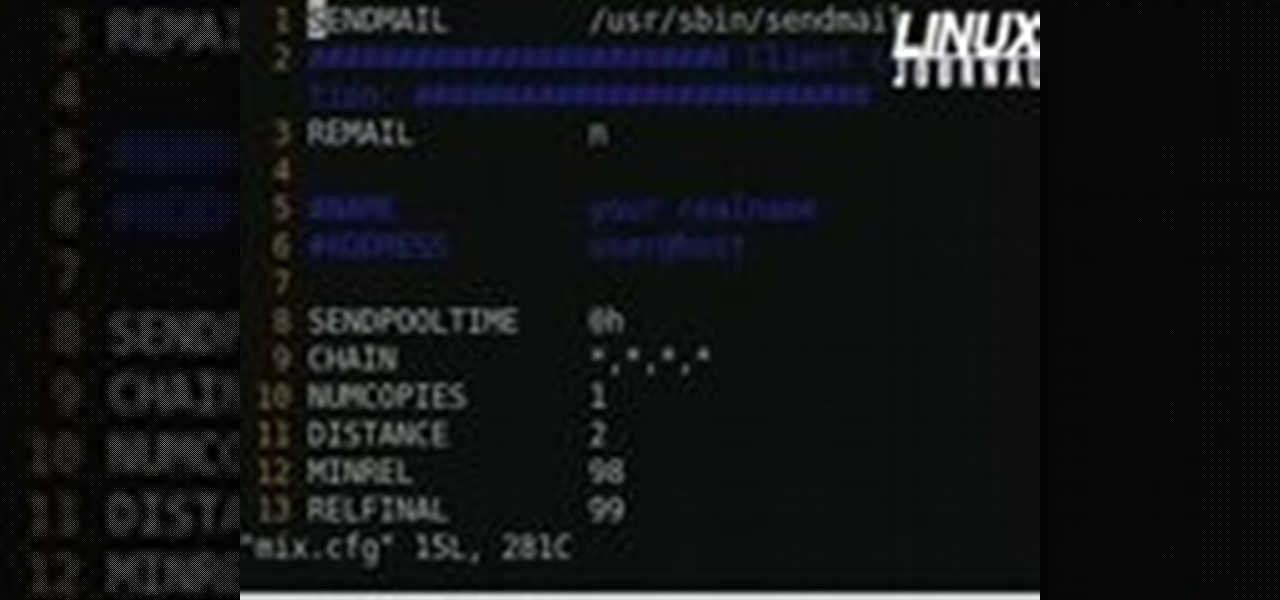
In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Buns and updos are gorgeous hairstyles, with one caveat: If they're not pinned perfectly and securely in place, all your hard work braiding and curling will go to waste as your hair slowly unravels.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

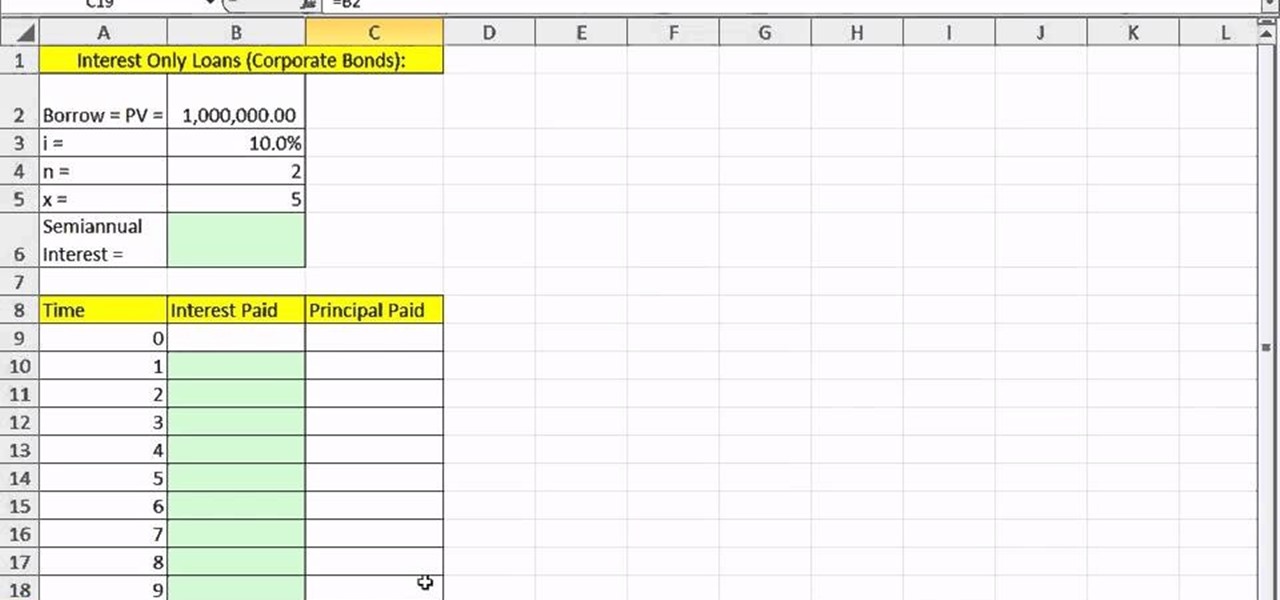
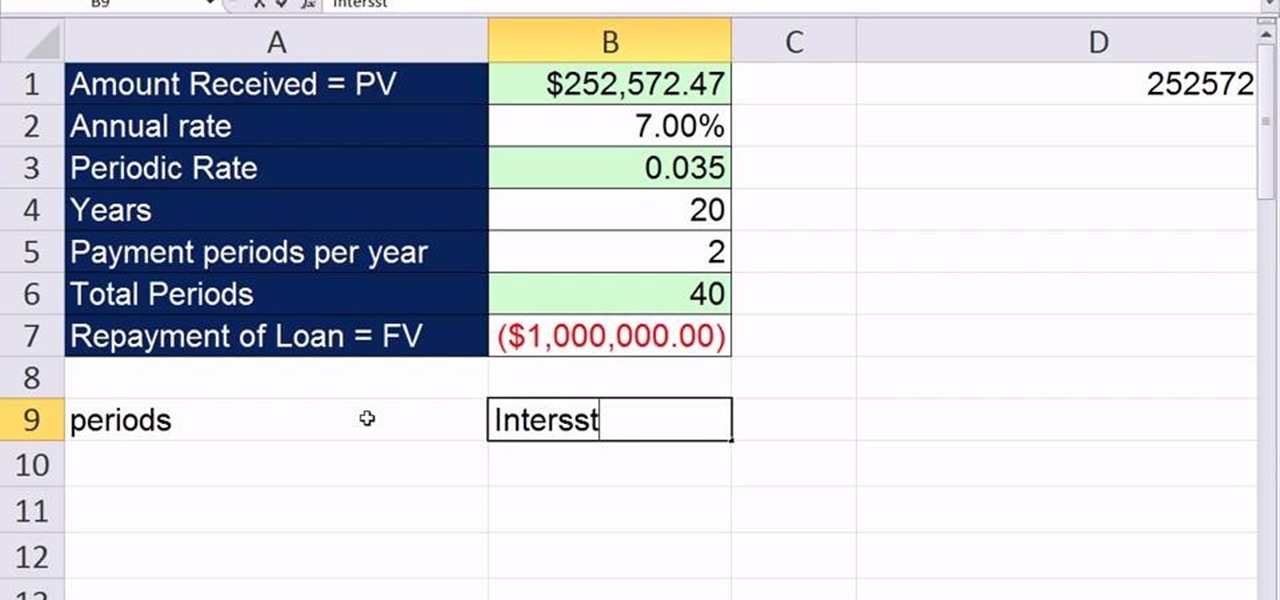
As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 12th installment in his "Excel Finance Class" series of free video lessons, you'll learn how to create an interest-only loan schedule in Excel.

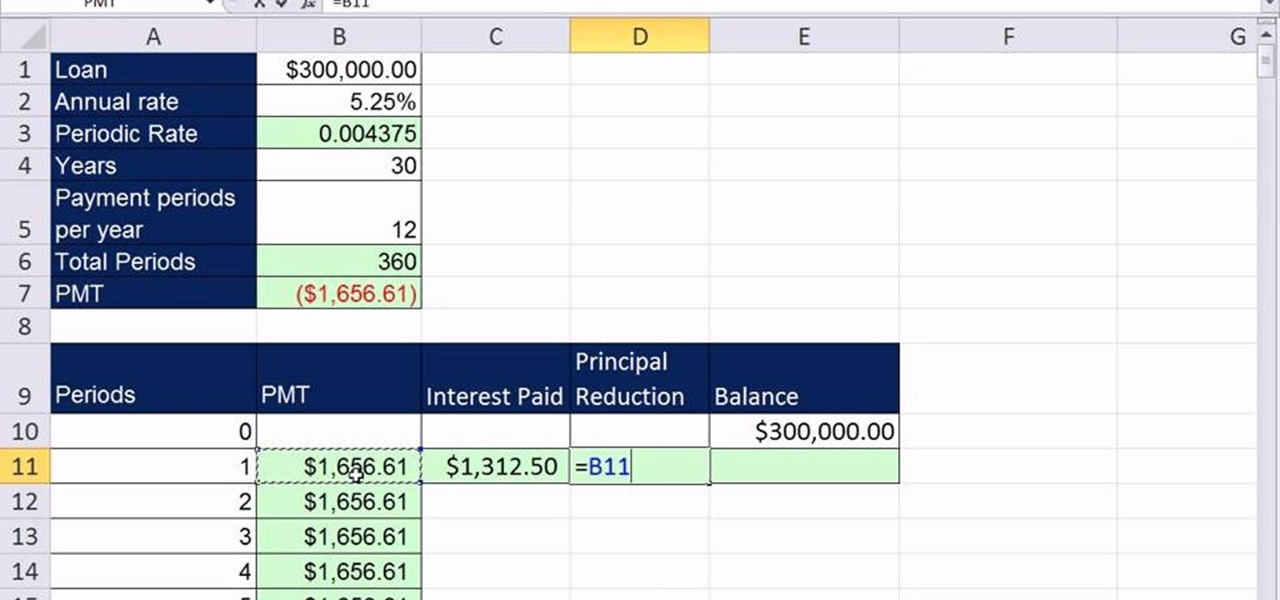
As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 4nd installment in his "Excel Finance Class" series of free video lessons, you'll learn how to build an amortization table for a consumer loan in Excel with the PMT function.

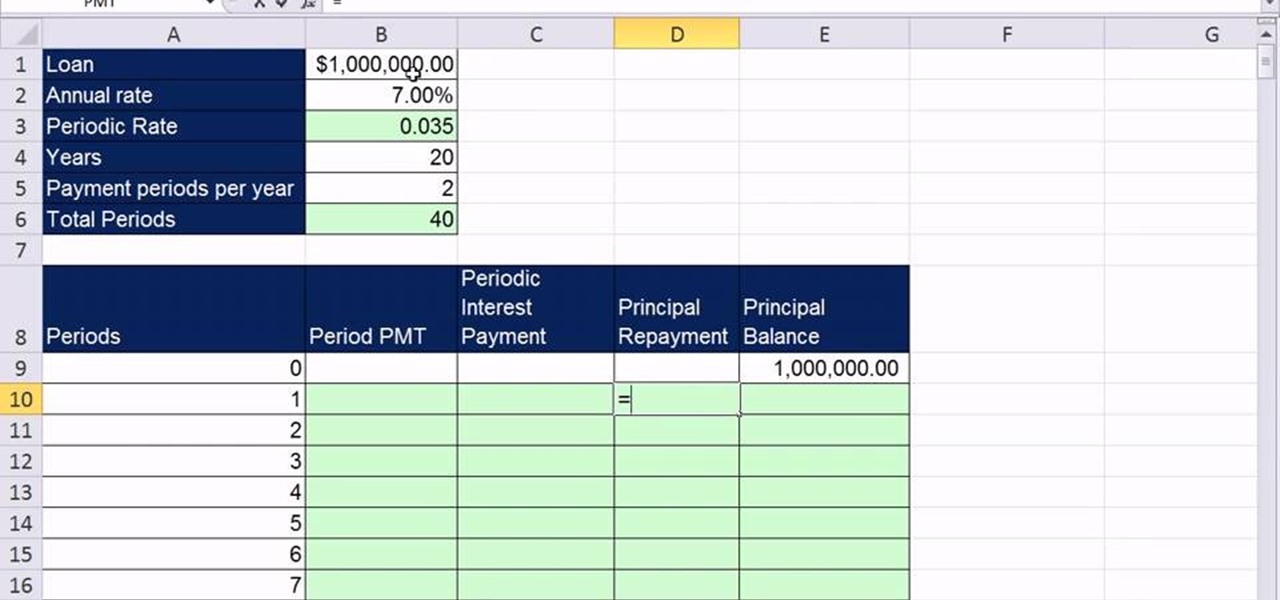
As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 43rd installment in his "Excel Finance Class" series of free video lessons, you'll learn how to create an amortization table for a business loan with Excel's PMT function.

As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 44th installment in his "Excel Finance Class" series of free video lessons, you'll learn how to build an amortization table for a deep discount loan in Excel.

Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and using high-security passwords yourself, watch this video tutorial.

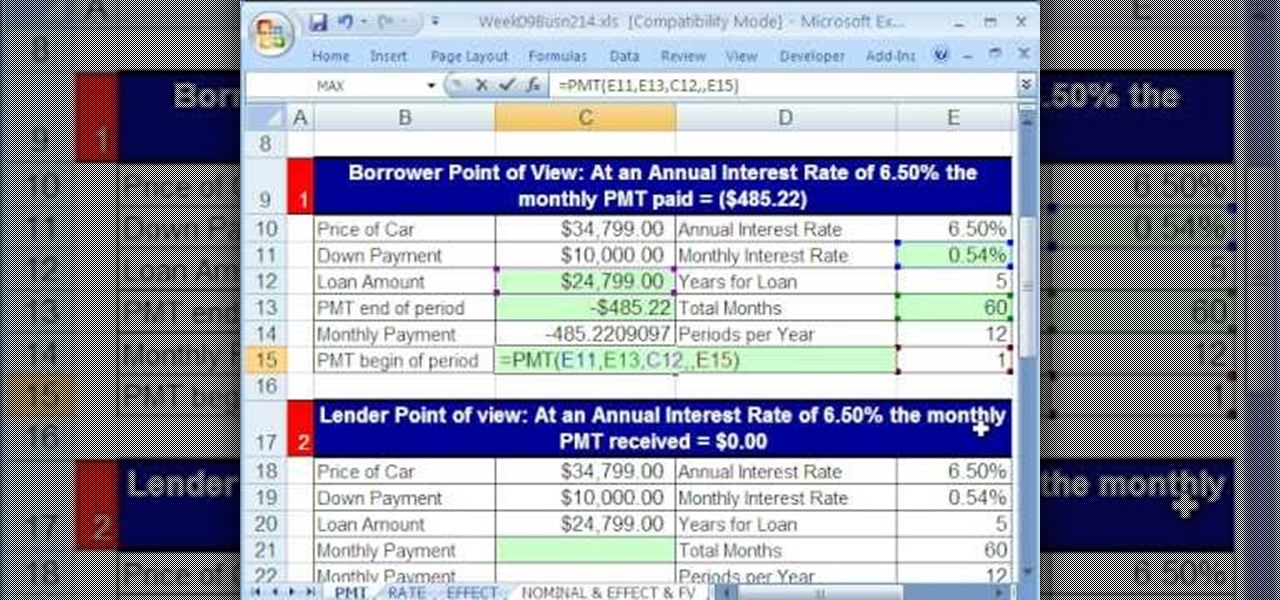
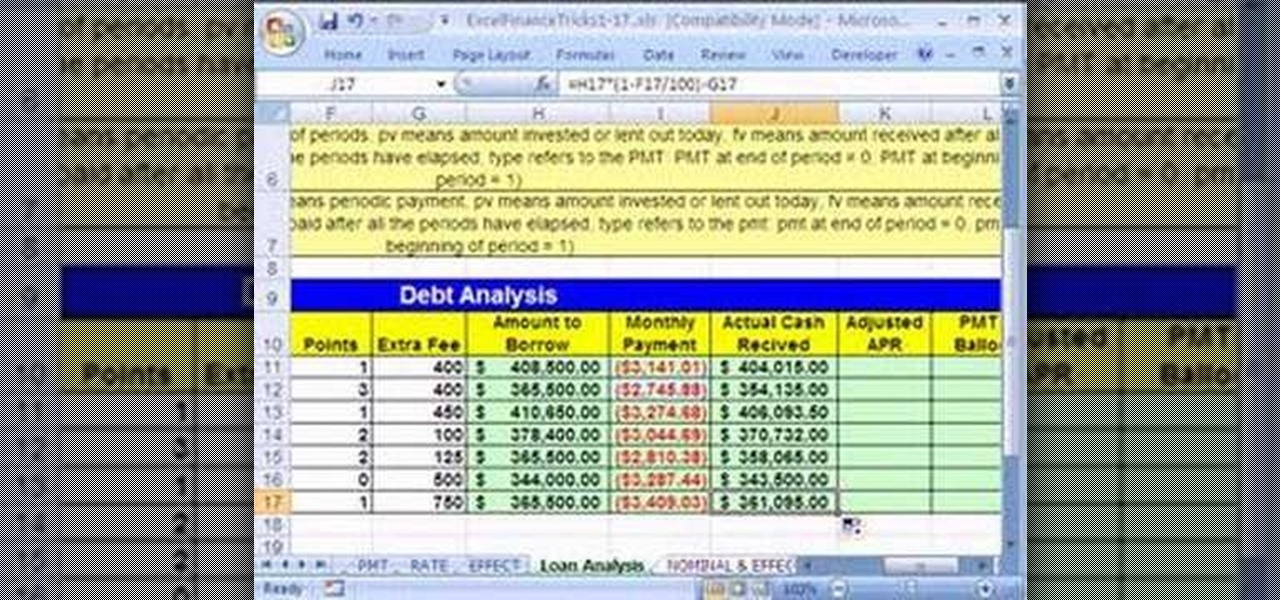
As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 18th installment in his "Excel Finance Trick" series of free video lessons, you'll learn how to use the PMT and RATE functions for a complete debt/loan analysis.

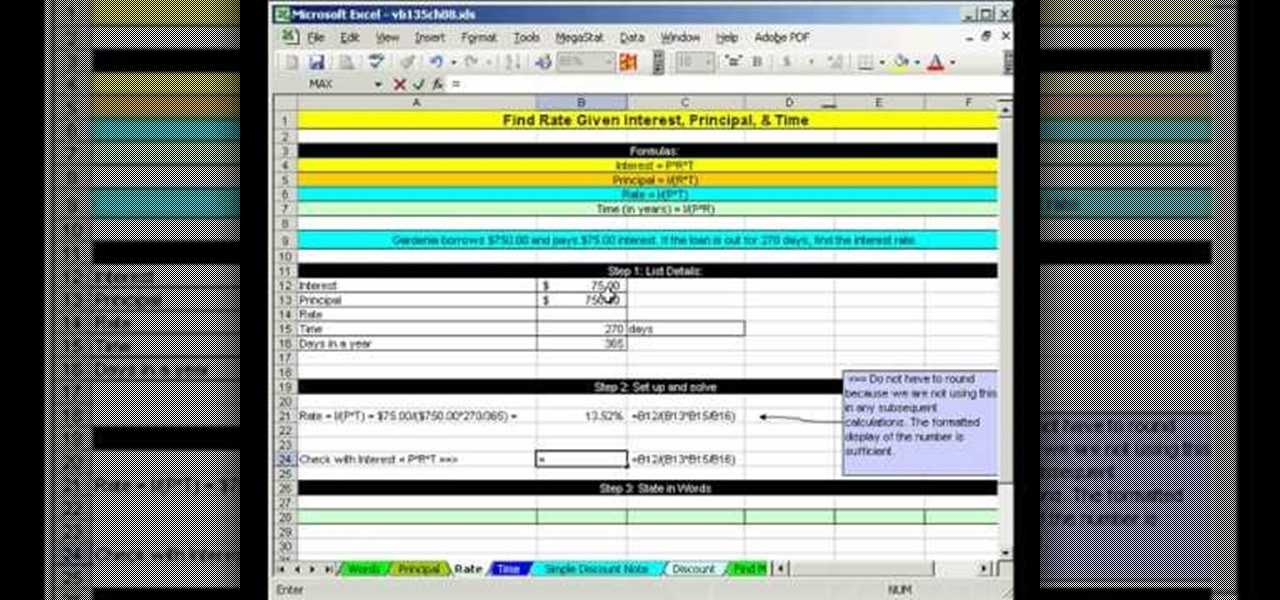
As you might guess, one of the domains in which Microsoft Excel really excels is business math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 54th installment in his "Business Math" series of free video lessons, you'll learn how to solve a simple interest loan problem for part, base, or rate.

The Clinch Knot is used to secure your fishing line to your fishing lure. In this video, learn how to tie a secure clinch knot, step by step. You can't fish without a sturdy lure, so watch the video and practice until you master the knot on your own. Once you've got it, attach your bait and you are on your way! Happy fishing!

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Looking to get an FHA loan? The Federal Housing Administration, FHA for short, provides mortgage insurance on loans made by FHA-approved lenders throughout the U.S. Here's how to get your FHA-insured loan. Learn how to get one with help from this video.

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

A formal occasion calls for a classic look. You Will Need

Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

A little precaution can go a long way to securing your online banking experience. Use these tips from Tekzilla.

Secure a square knot with tips from this video.

Like everyone, you're on Facebook. And, also like everyone, you'd like to control the access your Facebook apps have BEFORE you even install them. Well, you can, with a sweet little Firefox add-on called FB-Secure. Take control of Facebook app privileges before they read your secret diary.

In this clip, you'll learn how to secure a new Microsoft Windows desktop or laptop computer. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started protecting your own new Microsoft Windows PC, take a look.

If your home has a garage with a fairly standard garage door opener, that garage door is probably the easiest way for a burglar to gain entrance to your house. If you want to secure your home against such breakins, watch this video. It offers tips for securing your garage door so that thieves cannot gain access to your property and your family.

In this tutorial, we learn how to lash a bamboo tripod. First, you will tie a clove hitch by taking one piece of bamboo and wrapping the rope around it, then crossing the two sides of the string together to make a hitch. Next, you will secure the clove hitch around the third piece of bamboo. Now, you will rap all the pieces of bamboo together with the rope. Continue to do this until all the pieces feel secure together. Wrap the rope several times around each of the pieces, then wrap it in the...

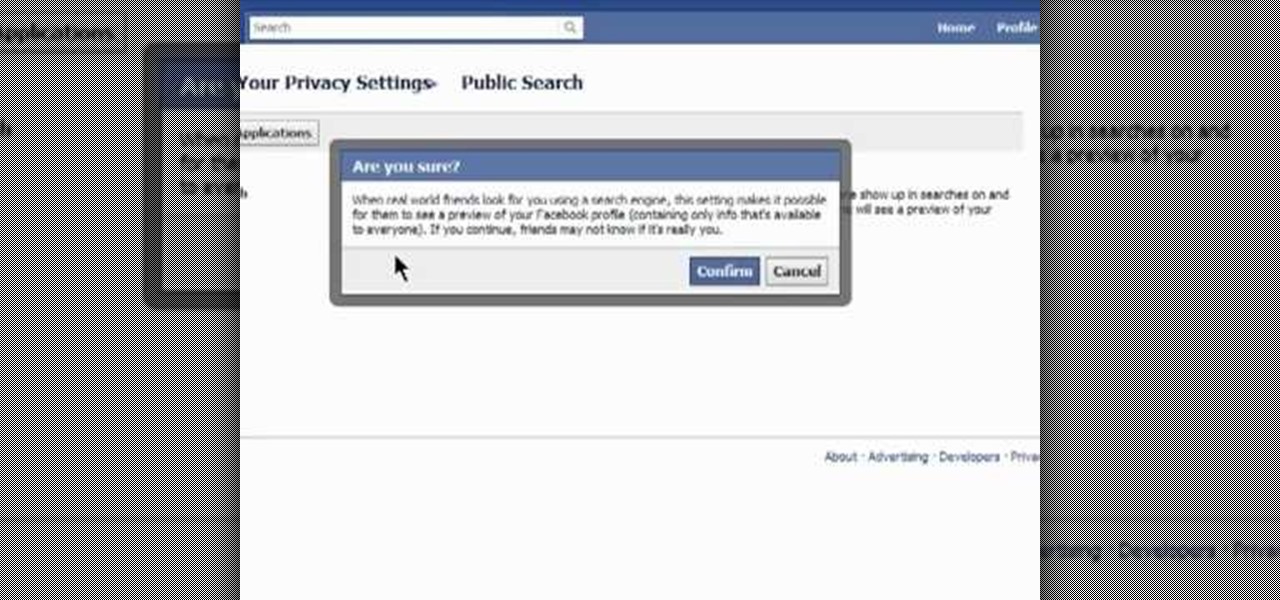
Looking for a guide on how to secure your public Facebook profile? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.