
How To: Deleting Your Files Completely
What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.


What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.

This video will show you how to secure your GoPro camera to your motocross, Snowmobile, Motorcycle, Skiing helmet so that it will not loosen up and fall off.

This video will explain how to safely weight down and secure a basket ball hoop with a water filled base that has a hole in it.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Millions of laptop batteries have been recalled because of the risk of FIRE. Get some tips from CNET to learn how to keep your laptop battery safe and secure. First, make sure your battery hasn't already been recalled. Second, don't leave the laptop constantly charging because it heats it up. One way to save your battery is to remove it completely when you plug in directly. Third, treat the battery as fragile. And finally, four, avoid buying knockoff batteries.

If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

If you've spent a ton of money on your newest smartphone, you will want to make sure it's secure. In this tutorial from the experts at PCWorld, learn exactly how to activate safety mechanisms on your Android. With these options you can set a complicated passcode (so that anyone who does find your phone won't be able to access your files) and you can also set up a locator. By using the location app, you can text your phone from anywhere else and set off a search alarm so you will be able to fi...

This video tutorial shows you how to use a long wrap product to dress yourself while creating a secure carrier for your baby. The long wrap is brought forward from back to front and round your belly button, criss-crossed over your back and brought forward and criss-crossed once more, then tied. The two criss-crosses (in the shape of an X) help hold the babies legs, as the pass through the criss-crosses and support the baby. You should then try to bring the fabric down as far as possible to su...

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.
If you want to transfer files to or from your iPhone at ease, check out this video on how to SSH / SFTP into your iPhone. SSH (Secure Shell) and SFTP (Secure File Transfer Protocol) all can be used to safely transfer files to your iPhone!

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not.

This half-hour episode of Hak5 covers several topics: Using a DSLR camera to create HD footage, building your own Google TV, unlocking & copying locked files with Lock Hunter, using PicPick for screen capture, using WinDirStat for analyzing & cleaning your hard drive, setting up a secure FTP server with Ubuntu Server, and secretly copying data from USB drives with USB Dumper.
Justice might not have produced any new material in a while, but their place in electronic music history is already secured due to their filthy electro-house beats that have become ubiquitous in the years since they first broke out. Watch this video to learn how to make a dirty electro bass synth line like theirs in Reason 4.

In this video, we learn how to install dry acoustic flooring with Fermacell. To start, you will level the floor and apply compound if you need. Next, you will lay the Fermacell around the room on top of the leveling compound. Push the flooring tightly together so there are no spaces in between them. You may need to cut the flooring to make sure it's the correct shape for the wall. After this, apply flooring adhesive to the seams to make sure they are secure as they are laid down. After this, ...

In this video, we learn how to use secure online passwords. There are a ton of things to consider when creating a password. A weak password is something that someone can easily guess. If you are using a birthday, common dictionary word, child's name, or something common then you are at risk. Your password should combine letters and numbers, and be at least eight characters long. It should also be completely random and have upper and lower case letters. You can use a password assistant if you ...
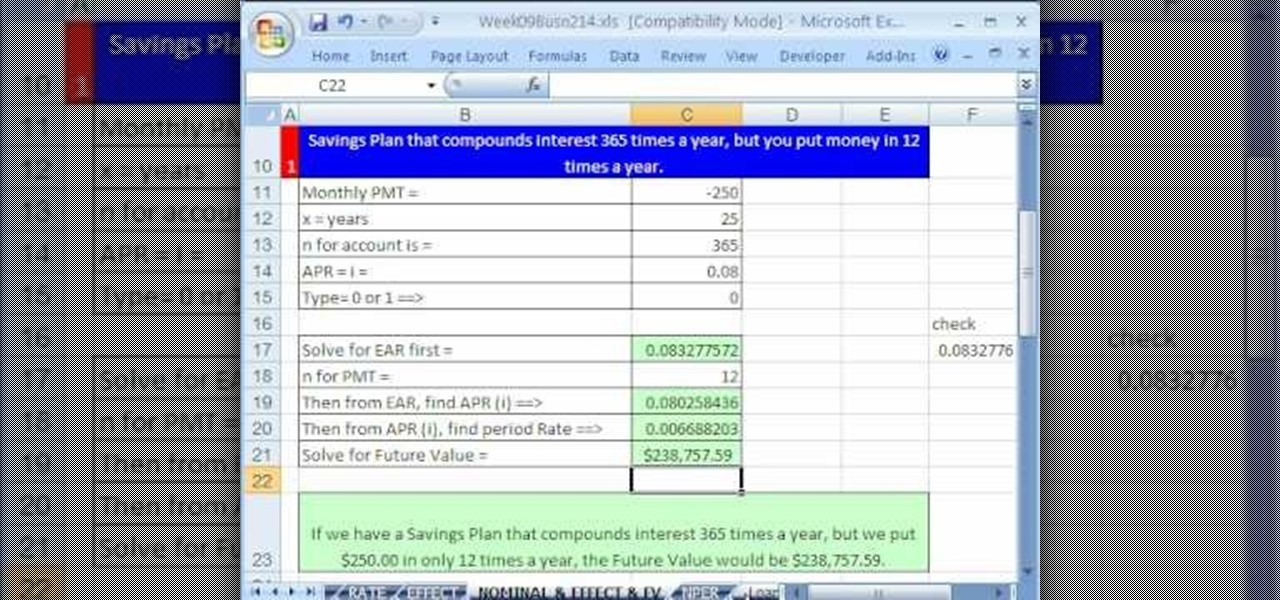
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 48th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to use the RATE, EFFECT, NOMINAL and NPER Excel functions to solve the following problems:

The way to wear hijab shown in this demonstration with a simple wrap around the head, securing the hijab with bobby pins at the back of the neck. The ends of the hijab are pulled forward to the chest. Then a thin scarf in a contrasting color can be wrapped around and tied at the nape of the neck as well. A portion of the hijab is pulled forward over it and pinned over the ear. Then one of the ends is pulled under the chin to the opposite ear and pinned to the head. The other end is wrapped ar...

Several Tanzanian girls demonstrate how to tie a kanga (an African sarong). The first method is to wrap the kanga around the waist and tuck the end in at the waist to secure. The second method is to wrap the kanga into a cylinder to use it as a base for carrying a parcel on the head. Another way to wear the kanga is to wrap it around the neck like a shawl or wrapped under an armpit and tied over the shoulder for a fancier look. To wear the kanga as a scarf, fold it into quarters the long way,...

To create an apostolic or pentecostal hairstyle, start with a poof in the front of the hair. It can be ratted behind for stability. Use two bobby pins to secure the back corner of the poof. Squirt the hair with hairspray before moving on. Then create a low ponytail in the back of the hair, pulling the top up and out slightly while forming the ponytail so it creates another poof in the back of the head. Spray the ponytail with hairspray then smooth out the hair on the top of the ponytail. Wrap...

This video illustrate us how to make a light bulb oil lamp. Here are the following steps; Step 1: Take all the things required that is bulb, socks,adhesive tape,scissors,kerosene, rim with a hole in the center.
In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...
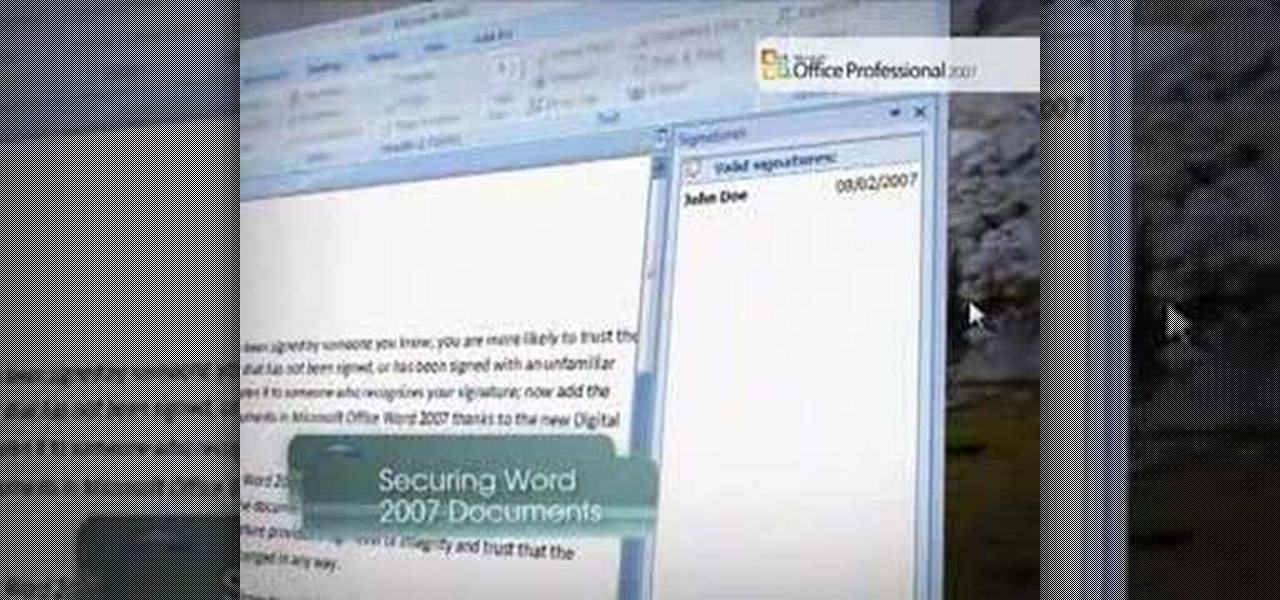
Securing Microsoft Office Word 2007 documents with Digital Signatures - When you receive a document that has been signed by someone you know, you are more likely to trust the contents than those of a document that has not been signed, or has been signed with an unfamiliar signature. Signing a document validates it to someone who recognizes your signature, now add the same degree of integrity to your documents in Microsoft Office Word 2007 thanks to the new Digital Signatures feature. For more...

The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.

Julia, AKA Hairbeauty4you, gives detailed instructions on how to do a quick half up-do with a twist in under 10 minutes. She notes that this style is best for medium to long length hair. Julia starts with straight hair, then sections off the top part and clips temporarily. She then separates another section on either side of the top part- from the ear to the clipped section- and pulls it back into a high pony tail and repeats identically on the other side, securing each with clear rubber band...

Tie a clove hitch knot again, again, and again.

In this video, we learn how to do wrapped pigtails on your American Girl doll. First, separate the hair from side to side. Then, take a small section from the front of the hair and put it aside. After this, you will need to comb the hair back into a ponytail and secure with a rubber band. Secure the other side into a ponytail as well, but put all the hair back into it. After this, you will take the front from the other side and wrap it around the ponytail. Clip it into place and then you will...

In this video, we learn how to tie a Palomar knot to secure a fishing line. This knot is pretty easy to tie, it won't take long. First, you will take the fishing line and make it into a loop. After this, insert it through the eye on the hook. Next, bring it back over and then tie an overhand knot, leaving it a little loose when you tie it. You should be able to see the working end hanging down. Now, take the loop and put it over the hook. Now when you tighten it up, you will have the complete...

In this video, we learn how to do the triple nifty knots hairstyle on your AG doll. First, comb the doll's hair back and then take the hair from the crown of the head. Put this into a ponytail and then secure with a rubber band. After this, section the tail off into two parts and twist them individually. Then, bring these around each other and create a bun at the top of the doll's head. Secure this with a rubber band. Do this with two other sections of the hair on the left and the right. When...

In this tutorial we learn how to fix an RV awning that will not retract. If you find yourself in the situation where the awning on your RV just won't retract, then this is the video for you! To secure the awning you will first need to go to the roof of the RV. When you get on top, you will need to look at the awning and see if something is stuck and causing it to stick. Manually secure the awning when you go to the roof so that it will stay in place for when you need it. If this doesn't help,...

In this tutorial, we learn how to install a cold air intake for a 96-04 Mustang. First, you will need to lift up the hood and locate/disconnect all wiring harnesses. Then remove the bolt around the air filter housing and set aside. Separate the intake and the housing, then pull out the air filter housing. Reinstall rubber grommets that may have come out, then disconnect all hoses from the engine. Put the intake and the pieces together, then you will start to place it back into the car the way...
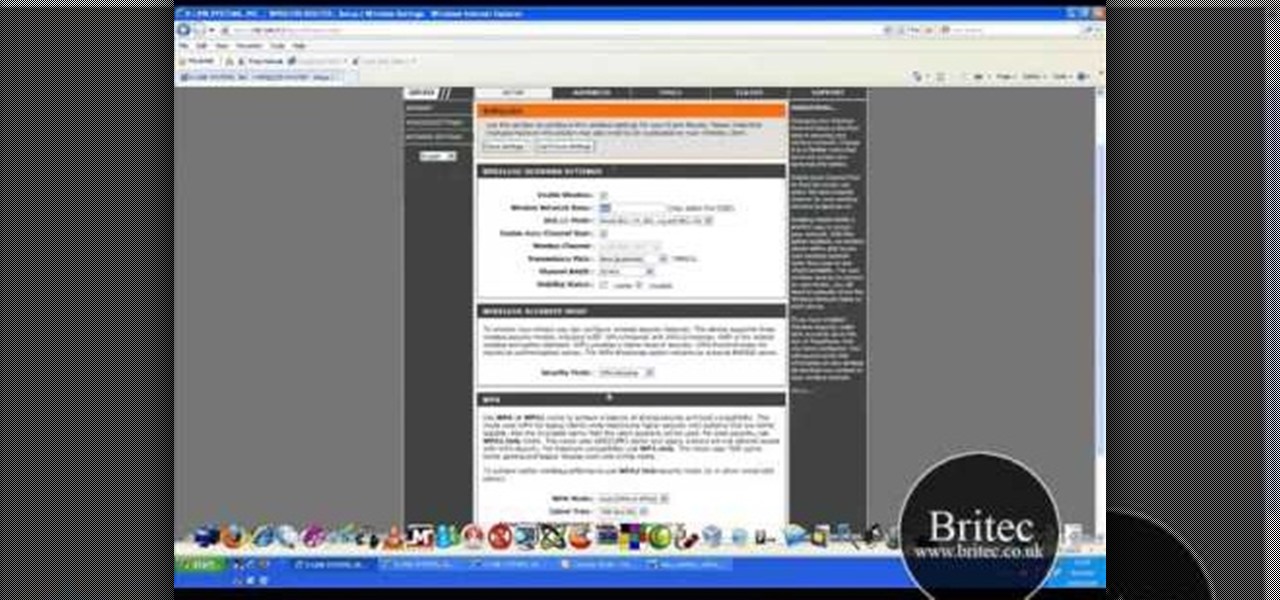
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

In this video, we learn how to make a box. First, fold the piece of paper into a triangle, then another triangle. Now, unfold the paper and fold all the sides into each other, making a square. After this, fold in the sides once more, making sharp creases on the edges. Now, open up the paper and do this again on the other sides, opening up again when finished. Now, fold the sides of the paper and turn it upside down. Follow the creases that you just made to fold the box up into a secure box. M...
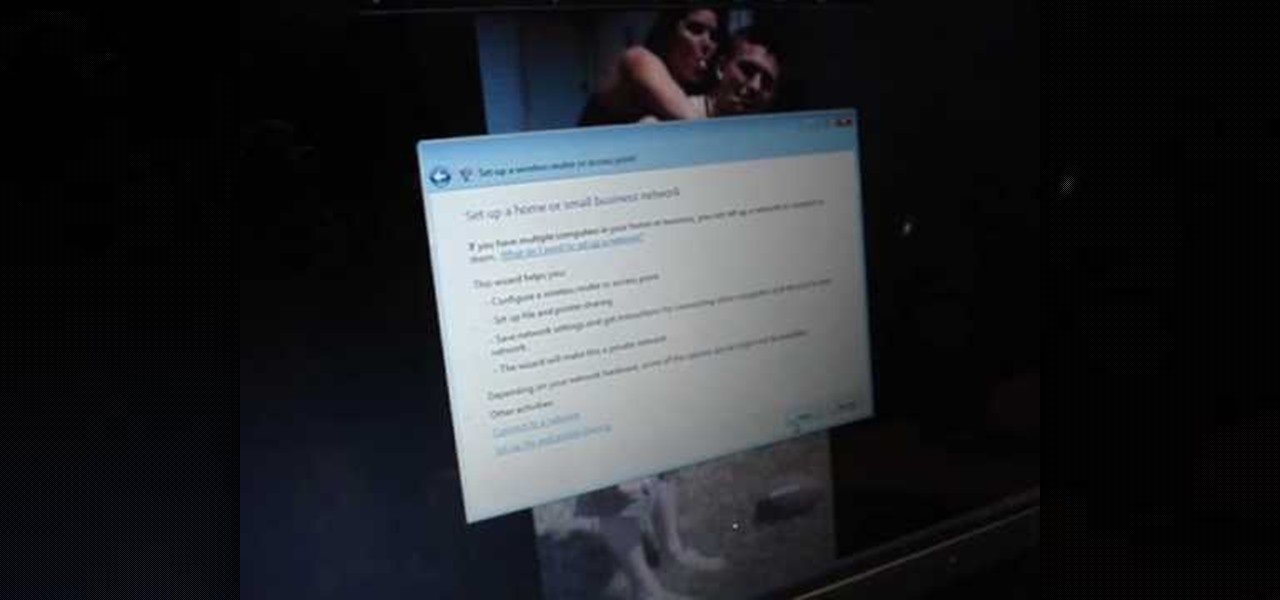
In this tutorial, we learn how to set up and secure a wireless router. First, take your cable and plug it into your modem from your computer. After this, plug in an Ethernet cable into your modem to a wireless router. Now, plug the wireless router and modem into the wall. Now, look for the icon on your computer that says you have connected a new device to it. Go through the set up wizard to make a new wireless network, once it doesn't find one, connect a USB to the computer. Now, click on the...

In this tutorial, we learn how to replace the spark plugs on a 2008 Kawasaki Ninja 250. First look underneath your bike to find out exactly where the spark plugs are at. Next, use wrenches and ratchets to loosen the parts around the spark plugs, then remove the spark plugs completely. After you have pulled them out, replace them with the new one and secure them into place. When finished, replace all the casing around the plugs and make sure you secure them tightly. Add on all bolts when you a...

In this tutorial, we learn how to make a floating illusion style necklace. You will need: beading wire, crimping pliers, wire cutters, beads (your choice), crimp beads, crimp covers (3mm), and a clasp (barrel clasp). First, cut your beading wire to the length you want your necklace, add 3-4 extra inches. Next, space your beads out on a beading board evenly, 1 1/2" apart. Now string a crimp bead onto your wire and take the end of the wire and string it through the crimp bead on the opposite si...

In this video, we learn how to properly pack glass for moving. Make sure you have a table or work area that has a furniture pad on it. Now, place packing paper onto the bottom of a box carton for glasses and china. Glass should be on the top of the box while plates should be placed at the bottom. Put the glasses into a rolled piece of paper until secured, then place upside down into the box. When finished, add crushed paper to the top of the first layer to avoid any glass from breaking. Make ...
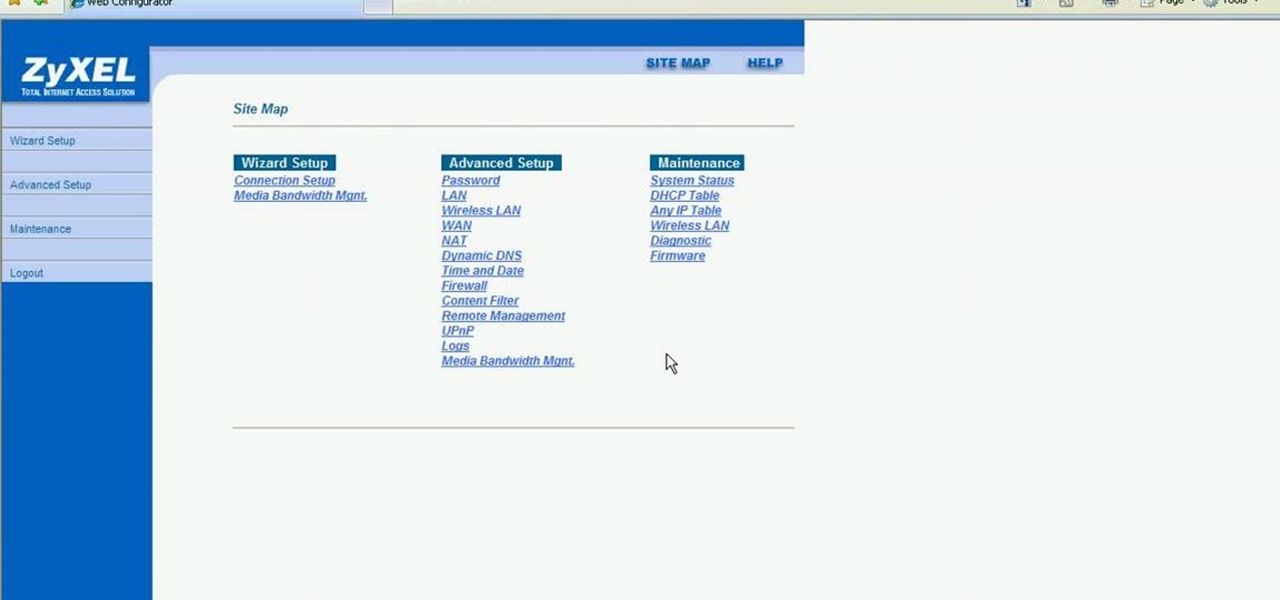
This video shows how to secure a wirelees internet connection on your Zyxel P-660hw-t1. For this, first click on Start button and open Internet Explorer(or any other browser). On the address bar of the browser, type in the IP address of your router. On the next page, enter your password and on the next page, either change the password or ignore. On the next webpage, under Advance setup, click on Wireless LAN. On the next page, click on 8021xWPA. Select authentication required and then click a...

Abigail Goss demonstrates a traditional Apostolic hairstyle, the vertical roll with pin curls. She starts by creating a poof, back combing the roots from the crown to the forehead. Then she creates a section of hair above the ears. She rolls this hair several times in one direction and then puts all of the hair into a ponytail at the base of the neck. At this point the style looks like a french twist with a ponytail at the bottom. She then coats the hair with gel. To make the curls, she takes...