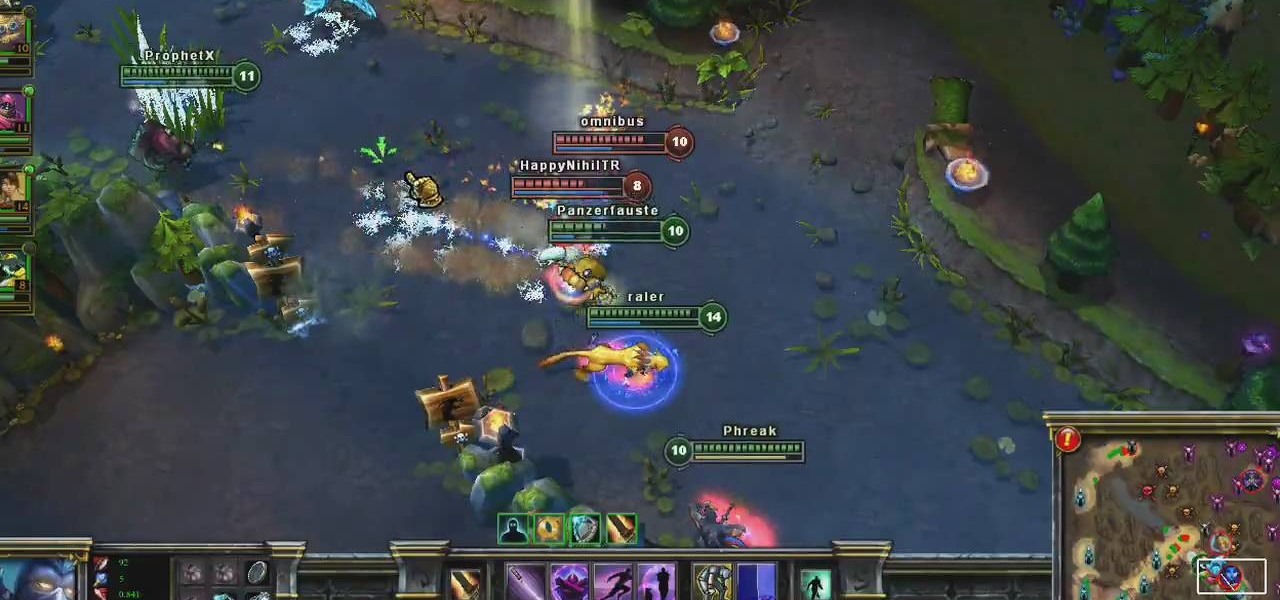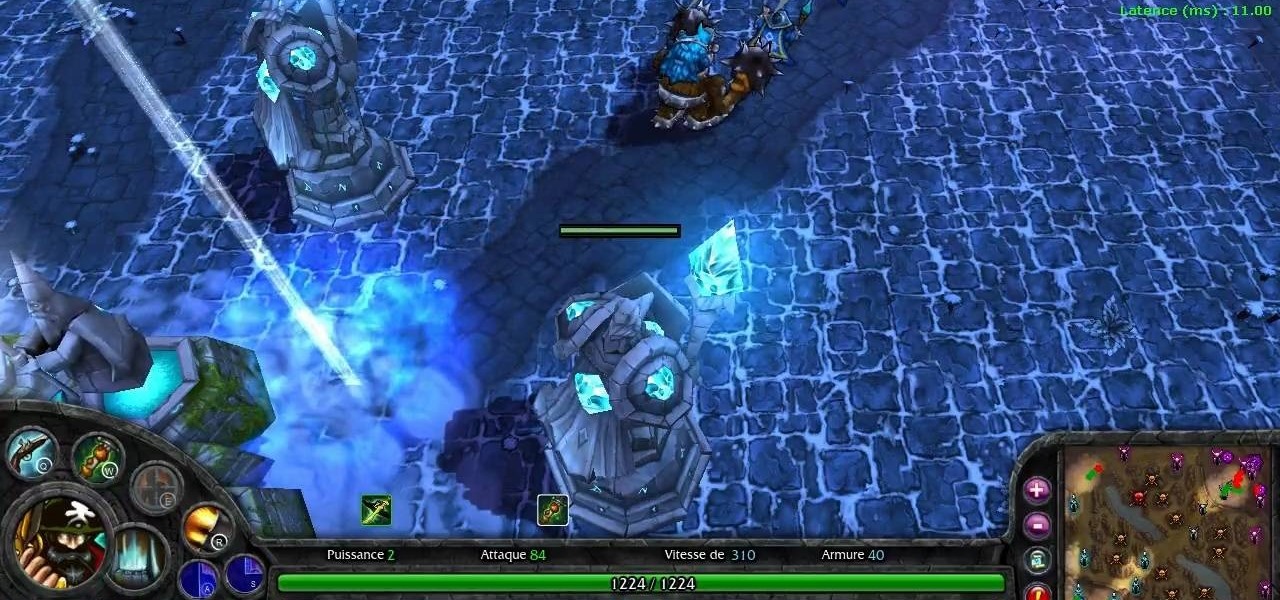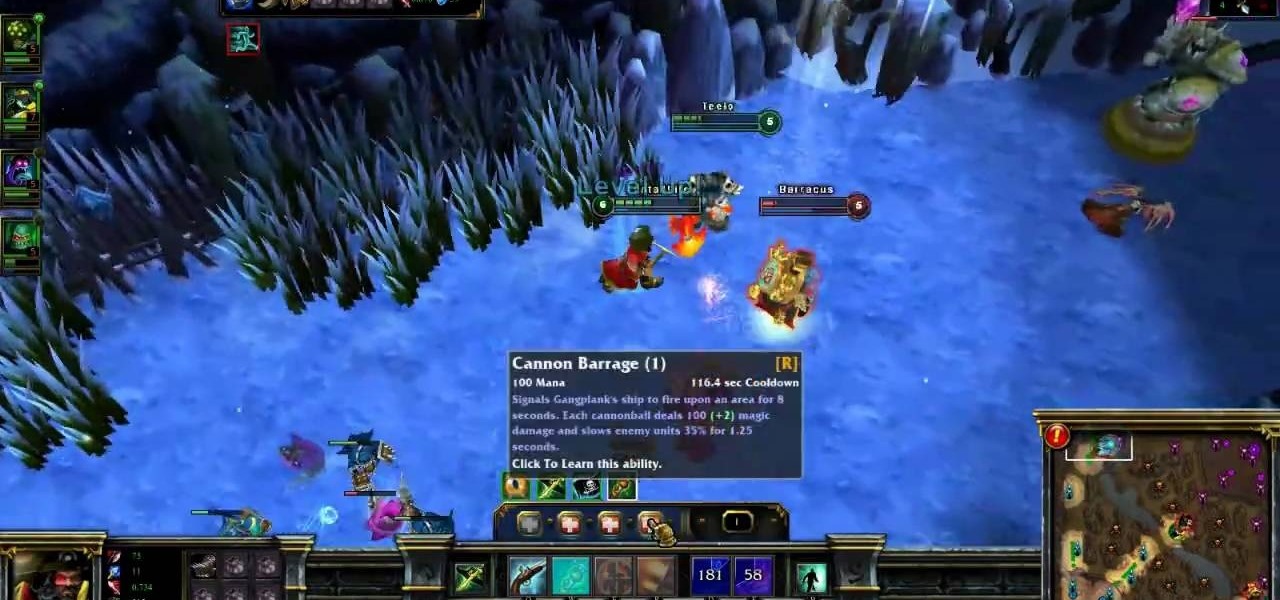
Want to play a pirate in League of Legends? Go with Gangplank, the Saltwater Scourge! He can put out an amazing amount of damage while giving some good buffs to his teammates. This tutorial shows you the best way to put this pirate to work for your summoner on the Fields of Justice.
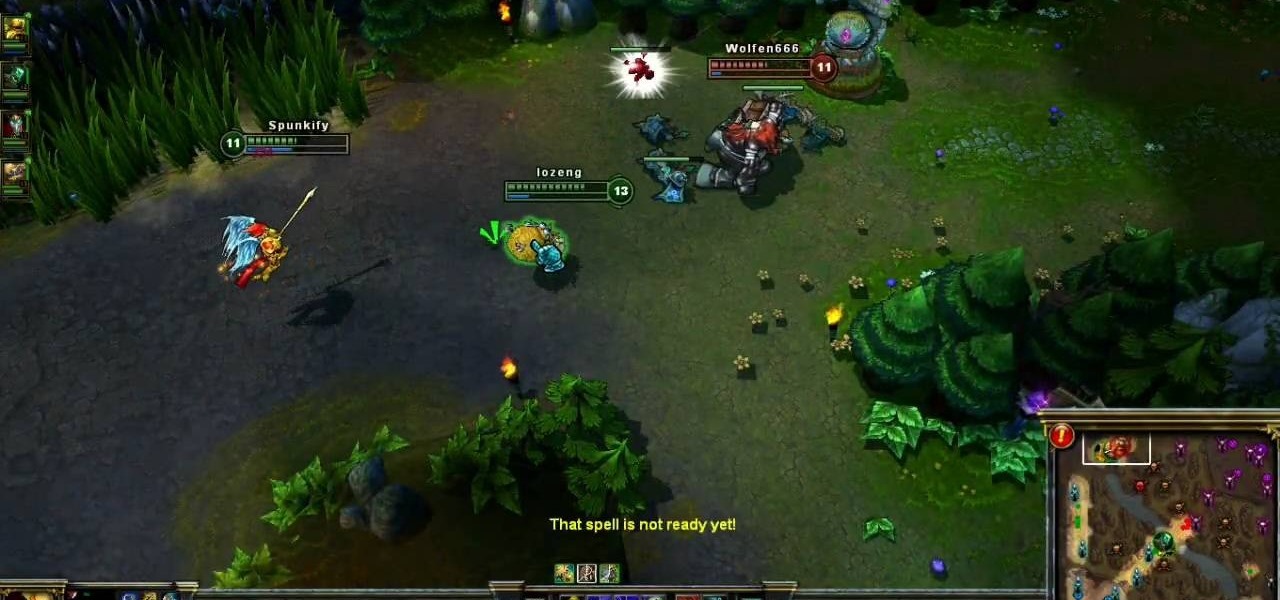
With his abilities to slow, heal and deal splash damage, Kayle the Judicator is useful as a support DPS champion to fight with on the Fields of Justice. This tutorial shows you how to build Kayle as a strong caster to ensure victory for your summoner in your next League of Legends game.
Despite the perception that Zilean is only a support champion, if you build him properly, he can hold his own, even an 1v2 battle. Here are some good insights into how to use Zilean effectively on the Fields of Justice.
Personalize your League of Legends champions by altering their skins! This method will only change their appearance for you. This shows you how to obtain custom skins and apply them to your favorite champion (or one you just want to change around).

Even if you're not a graphic artist, you can still use Photoshop to recolor the available skins for your League of Legends character. This tutorial shows you the tools and techniques to create your own skins for your favorite champion.
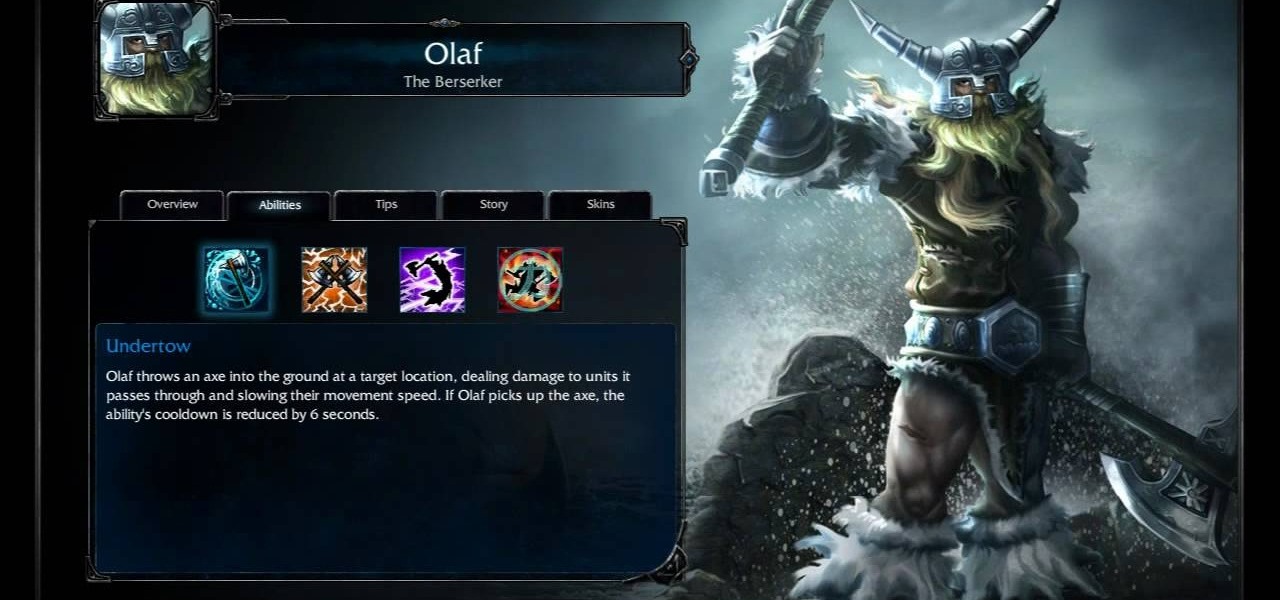
Olaf the Berserker is a melee DPS champion available for your summoner to play in League of Legends. There are many different ways to build an effective Olaf. This video shows you what you should keep in mind as you assign your own abilities and runes to the Berserker.

Shen is a useful champion to play as a tank, despite also being able to ninja. Here's a detailed tutorial on how to build Shen to take advantage of all his abilities, masteries and runes (as well as items) so you can always stay fighting with Shen.

Minions are computer generated NPCs that spawn from the base nexus and attack enemies. You can't control your minions, but you can influence them by using smite and heal on them. Use your minions well and you'll win your games on the Fields of Justice!

In League of Legends, you play the role of a powerful summoner, who may bring other champions to do battle on your behalf at the Fields of Justice. This short video explains how you can track your game stats and maintain your stable of champions using the summoner screens in the game.

You don't want anybody to have access to your cell phone. Nobody. Well, instead of the standard unlock mechanism, the one anybody can unlock your cell phone with, the Motorola DROID, and Android enable mobile device, allows you to create your own unlock pattern, secret to anyone else, which wakes it from sleep mode. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up a secure lock on a Motorola DROID cell phone.

In order to begin, you will need the following: Three hair tiesBobby pinsHair spray or spray gelRat tail combHair net

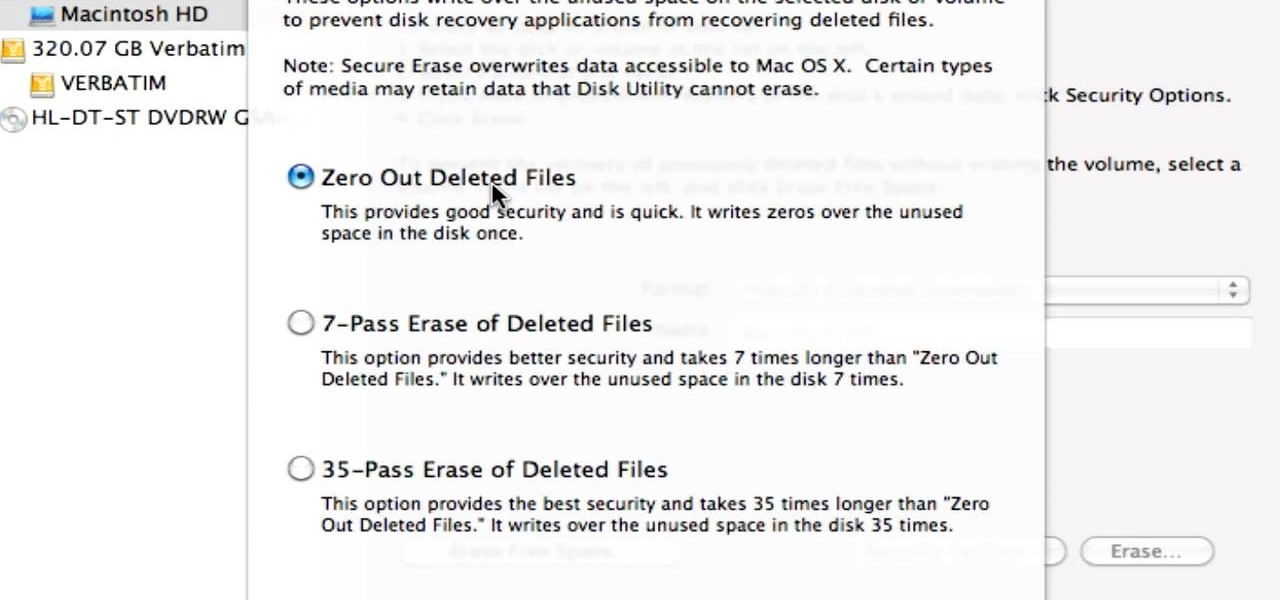
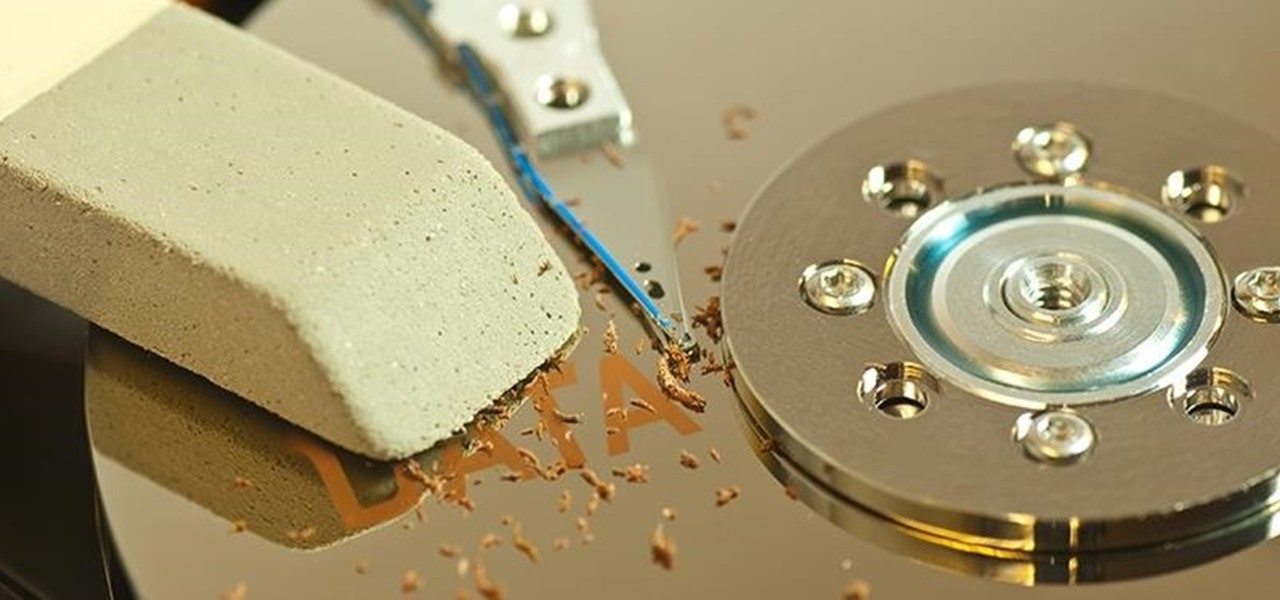
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...

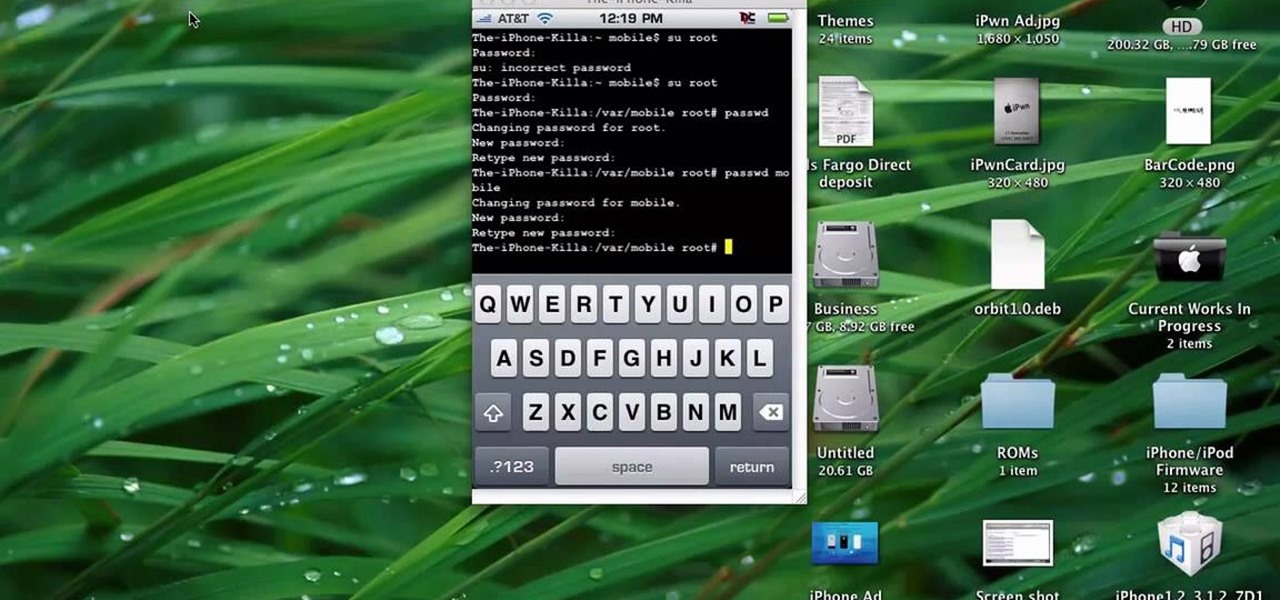
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

Do you need to lock the door but don't have the keys? This may happen if you are sharing your keys with someone else, staying at a friend's house, or for a variety of other reasons. Check out this video for a sneaky way to secure that door tight without even sticking a key in the lock.

One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. It's like having a safe built right into your smartphone, and it couldn't be easier to set up.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Start with Ryze as your champion at Level 1 and play him straight up through until Level 12. This tutorial shows you how to start his build and what spells, items and abilities to invest your points into so you can maximize his damage potential.

Malzahar can certainly be a viable champion to play on the Fields of Justice. This video shows you how to build up Malzahar by using the correct abilities, items and summoner spells to increase his strength in battle.

Vladimir the Crimson Reaper is the closest thing to a vampire you can bring onto the Fields of Justice. His abilities are focused on taking health from his enemies to build himself up, and this tutorial shows you the best build with spells, runes, abilities and items to take advantage of his unique talents.

What can Pantheon do as your champion on the Fields of Justice? Quite a lot! There are several fun tricks available to the Artisan of War. Here's a good tutorial on how to build Pantheon to take advantage of his strengths while using your runes to compensate for his weaknesses.

Notthecoolmom gives a craft lesson on how to make a diaper wreath for a baby shower. To make the wreath you will need the following materials: a package of 56 size 1 diapers (preferably with a design of some kind), a Styrofoam wreath, a spool of ribbon, and rubber bands (optional). Start by laying your diapers around the wreath to get an idea of spacing. Be careful not to make your wreath too full. You don't have to use all of the diapers it depends on the size of your wreath. To put the diap...

This video shows you how to use an exercise band to do bicep curls, triceps extensions and shoulder raises along with some fun extensions of these basic exercises. When doing the bicep curl with the band it is very important to ensure that the band is firmly secured under your shoe, so that it does not slip forwards and snap. Once the band is secure you must curl the arms up towards the shoulders, keeping your elbows bent and close to your sides. The arms are still working in a negative resis...

Ever had a spoke break on your bike wheel? Don't throw the wheel away! Repairing a spoke only takes a few tools and some patience. You will need, at a minimum: a freewheel tool (used to remove the part of the wheel that engages the bike chain), a wrench, and a screwdriver. First, remove the tire and inner tube from the wheel. Next, remove any parts of the broken spoke that are accessible from the underside of the wheel rim. If the spoke is attached to the side of the wheel where the freewheel...

Carmilla is a reoccuring character in the Castlevania universe, for those who have been following the series, although seeing as Lords of Shadow is a reboot, her strategies in battle are...different. She can't even really be harmed in the first half of the fight! In this video you will get a walkthrough on how to defeat Carmilla in Castlevania: Lords of Shadow!

The final boss of Castlevania: Lords of Shadow is Satan himself, quite literally the Lord of Shadow, King of the Underworld, there's more, but that I think you get the picture. He's a tough guy to beat, but there's a strategy! In this video you will get a tutorial on how to crush Satan himself and beat Castlevania: Lords of Shadow!

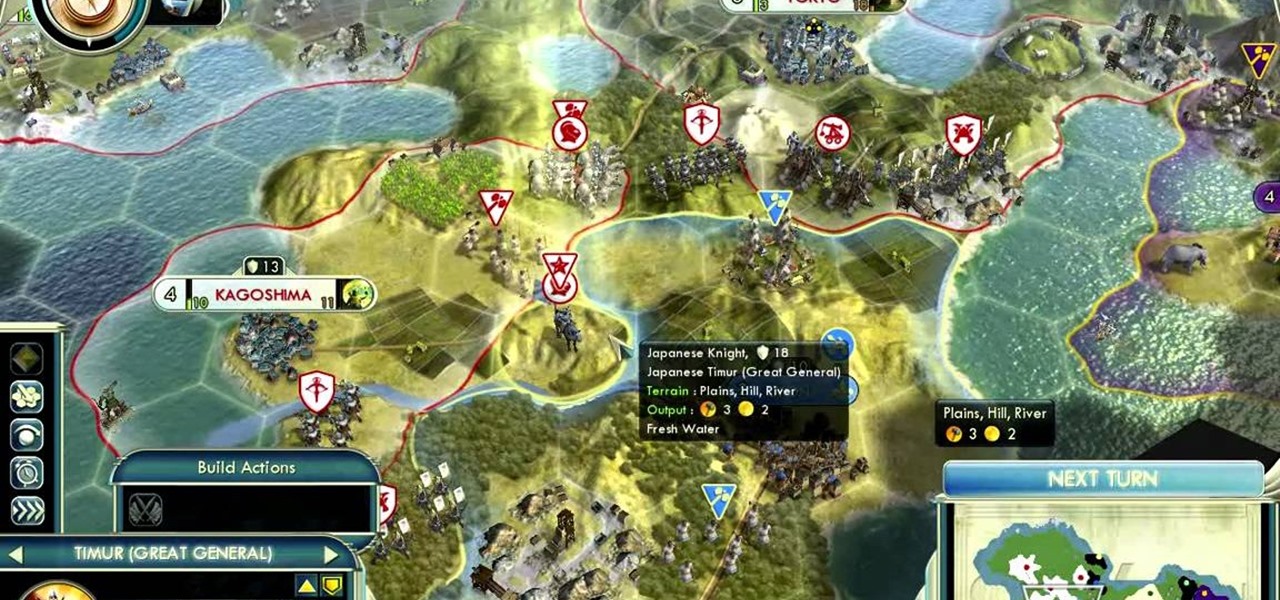
Crush your enemies beneath your well-equipped and well-trained boots! Whether you're primarily a defensive or offensive player, and no matter what civilization you are playing, you'll need to know how combat works to be able to win at the newest and most popular real time strategy game, Civilization 5.

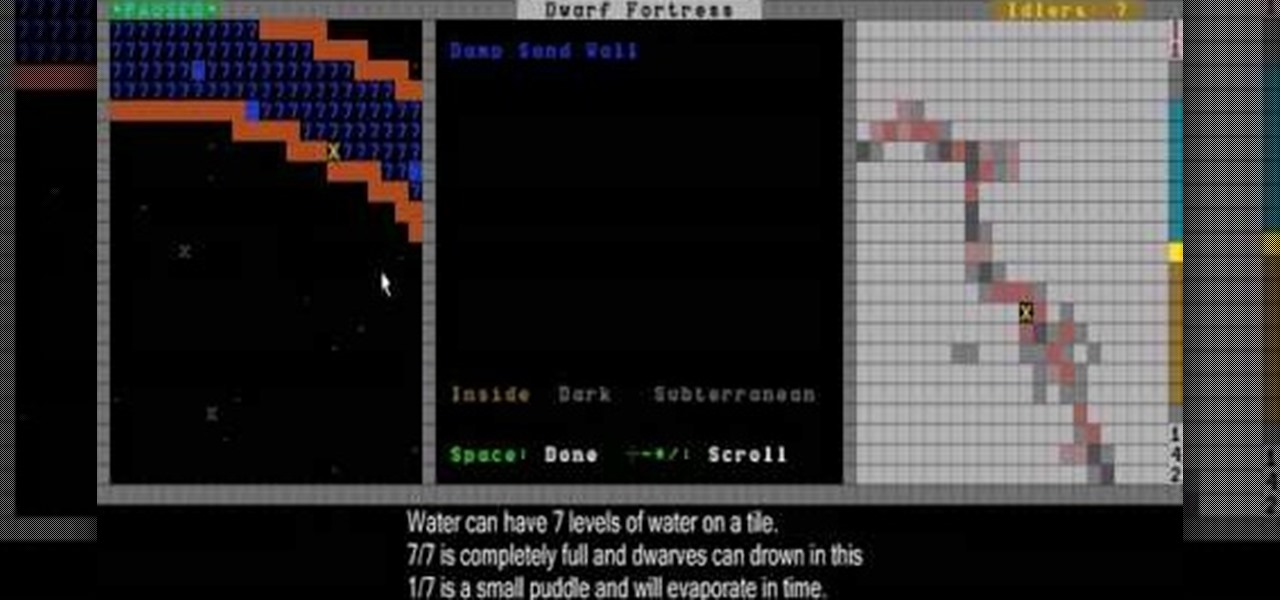
THis video will show you how to use the immensely useful magma forges to make items without using fuel, and also how to use roads, sculpture gardens, and ponds to improve your fortress.

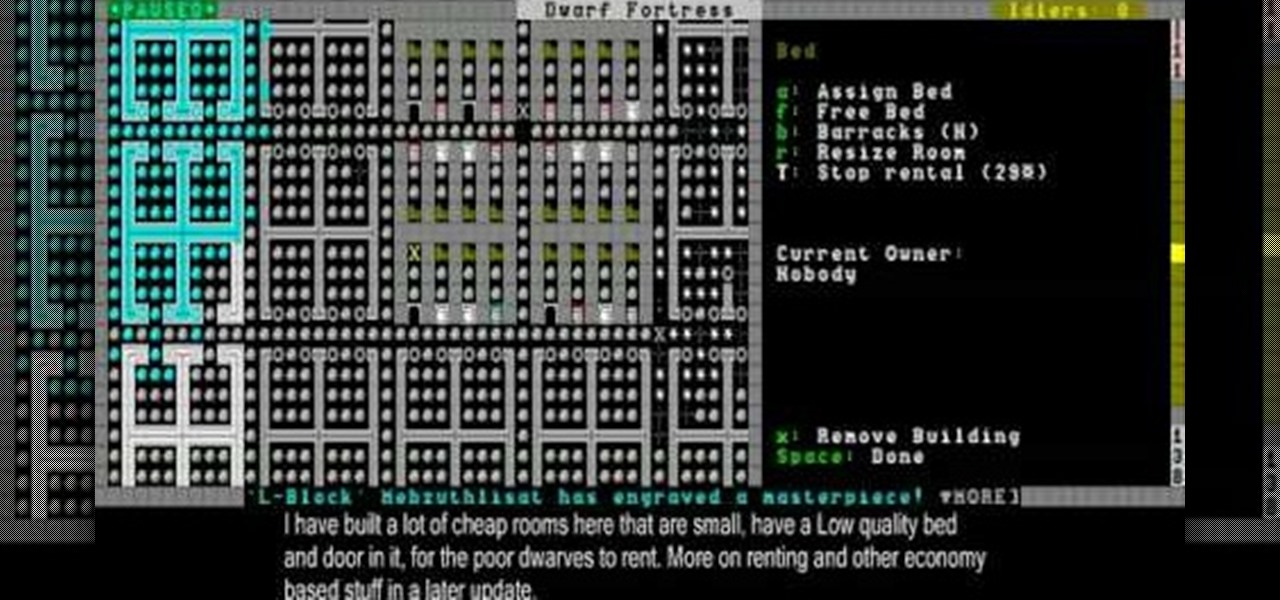
Now you've got a little bit of a fortress going, and it's time to continue building your infrastructure. This video will show you how to build bedrooms, farms, and stairs.

Once you've generated a world, picked a fortress location, and prepared seven dwarves, you're ready to start playing! This video will show you how the world map works and how to use it. It also covers how to rename your dwarves.

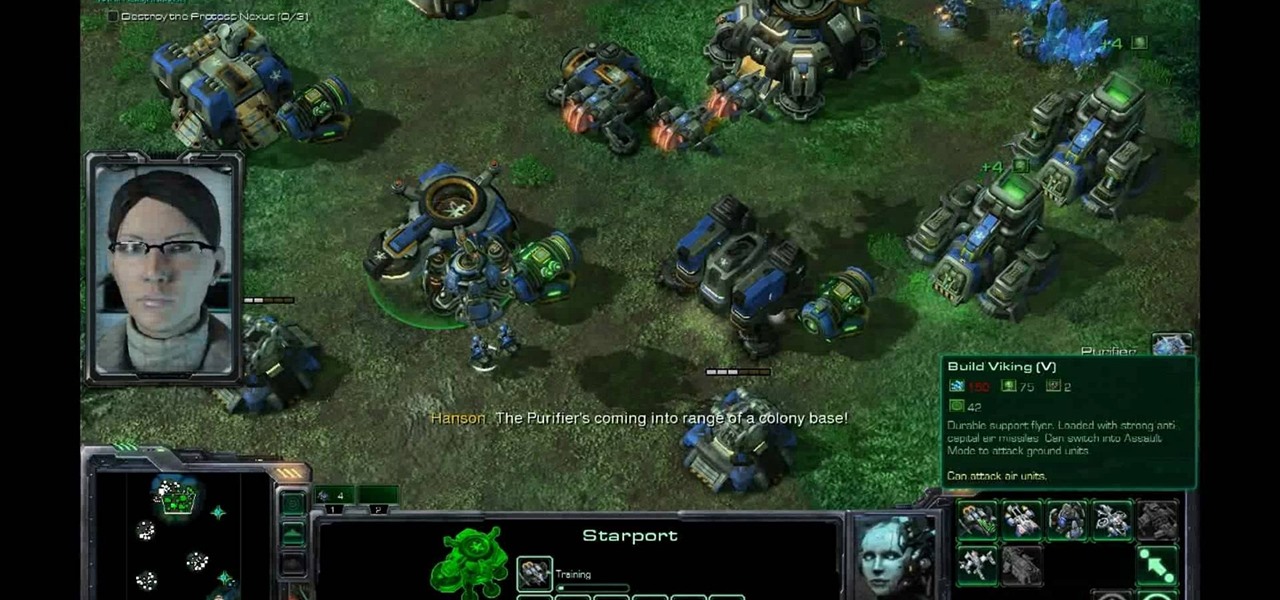
Mission 12 is one of several points in the StarCraft 2 campaign when you are presented with options for what mission you want to do. This video will show you how to beat one of them, Safe Haven.

Merrill offers up some of this best tips for making your works of art more realistic. There's three very important strategies for improving your the lifelike quality of your drawings and paintings, and in this video, he demonstrates them for you.

Starcraft 2 is finally upon us after 12 years of waiting, and it is just as majestic as you would hope it would be. If you're new to the series or just haven't played in five years, the barrier to entry for the unskilled can high, especially if you prefer playing online multiplayer. Fortunately for you, we've compiled videos on just about everything you need to know about the game, including strategies and tips for winning with different races in different modes and situations, and even how t...

Starcraft 2 is finally upon us after 12 years of waiting, and it is just as majestic as you would hope it would be. If you're new to the series or just haven't played in five years, the barrier to entry for the unskilled can high, especially if you prefer playing online multiplayer. Fortunately for you, we've compiled videos on just about everything you need to know about the game, including strategies and tips for winning with different races in different modes and situations, and even how t...

After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to play the The Lost Vikings minigame on your spaceship, which is a ...

TrueCrypt is a free open-source program for encrypting data and it's excellent for securing hard drives, but it also has the ability to hide a secret operating system inside another operating system. CNET shows you how this "insider secret" operating system is created. This operating system will be impossible to prove to people like the Feds.