
How To: Walkthrough Call of Duty World at War: Mission 11
This is a video walkthrough of Mission 11: "Blackcats" in Call of Duty 4 World at War. This includes cheats, glitches and quick play strategies. This game is a first person shooter (FPS).


This is a video walkthrough of Mission 11: "Blackcats" in Call of Duty 4 World at War. This includes cheats, glitches and quick play strategies. This game is a first person shooter (FPS).

This is a video walkthrough of Mission 12: "Blowtorch & Corkscrew" in Call of Duty 4 World at War. This includes cheats, glitches and quick play strategies. This game is a first person shooter (FPS).

This is a video walkthrough of Mission 14: "Heart of the Reich" in Call of Duty 4 World at War. This includes cheats, glitches and quick play strategies. This game is a first person shooter (FPS).

This is a video walkthrough of Salamun Bridge in Killzone 2. This includes cheats, glitches and quick play strategies. This game is an FPS.

Cary Kolat demonstrates wrestling technique in freestyle defense. Coach Kolat covers defending high crotch for 3 point throws.

Cary Kolat demonstrates wrestling technique of the freestyle offense. He shows you how to turn the basic takedowns into 3 point moves: Single Leg Come Up To Inside Grip Hip Toss. This is a wrestling demonstration from KOLAT.com

Check out this Mahalo video walkthrough of Marshlands in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Learn how to tie a Tack Knot - a secure way of attaching a rope to a fixed object such that it won't come undone even if shaken and flogged. This is a fine knot for camping, climbing, sailing or Boy Scout training.

Learn how to tie an Anchor Hitch (also known as a Bucket Hitch) - A very secure means of attaching a rope to an anchor or any other object that you can't afford to loose (like a bucket down a well, I suppose - thus the alternate name). I actually do use this hitch for temporary anchor attachment (preferring to permanently splice instead) as well as for my bucket lanyards when washing down my boat's deck.

Learn how to tie a Draw or Thief Hitch - a means of securing a rope with two standing ends - one end is load bearing, and the other can be pulled to release the knot. I used this knot extensively for raising the mast on my first trailor-sailor - Tie this above the spreaders, stand the mast up, then pull on the release line to untie it without having to climb aloft. This knot can be used in sailing, boating, general use, camping and bondage.

This video shows you how to tie a Thief Knot. This knot looks a Reef Knot to the casual observer and so can be used to determine if a thief is tampering with your belongings bag - secure it with a Thief Knot, and if you find it re-tied with a Reef Knot, you know someone has been messing with your stuff. This is used in sailing, boating, general use, camping and bondage.

March, 2047. A massive nuclear fireball explodes high in the night sky, marking the dramatic beginning to the Third Tiberium War and long-awaited return of the most groundbreaking Real-time Strategy franchise (RTS) of all time. This is Command & Conquer 3: Tiberium Wars.

An amputee shows the way to tie shoe laces with one hand or one arm. He has no prosthetic help meaning he doesn't use a hook. This can be a huge challenge in life for persons with missing limbs or in need of adapted living situations. Shoelaces are tough enough with two hands, let alone one. This is a great first hand account of the strategy in tying one's shoes without a prosthetic. This is an adaptive equipment tutorial for handicapped, disabled or individuals that have lost limbs to amputa...
Jared of the TechCentric crew gives you the lowdown on the basics of keeping your VoIP conversations secure and, on the other side of things, how to use the Cain VoIP sniffing application. For detailed instructions on keeping your VoIP conversations private, watch this hacking how-to.
Mike Lively of Northern Kentucky Universtiy demonstrates how to grab a website's resources for reconstruction in Flex using HTTRACK and Wireshark. This tutorial is especially helpful for sites you want to grab that think they are very locked down and secure. All with the free softwares HTTRACK and Wireshark.

Battlestations: Midway for the XBox 360 takes place at the very start of America's involvement in World War II, beginning with Pearl Harbor. Take a look at this instructional video and learn how to win the Battle of Tulagi and secure the strategic islands with these tips from G4TV.

Watch this quick instructional cinematography video that shows how to balance a Canon XL2 professional HD digital camera on a GlideCam 4000 Pro. Learn how to secure the camera using this handheld camcorder stabilizer to prevent unwanted swaying, shoot fluid traveling shots, and produce professional works.

If you can find people who speak English in China, you'll probably get where you want to go faster. Memorize this basic Chinese phrase and feel a lot more secure once you get to China!

This knot is common in the climbing world. We use it to secure two ropes together. Often used to form a loop on a prussik (cordalette) to construct an anchor. Can also be used to connect two ropes to rappel. This knot has many applications in the real world not just climbing.

In this tutorial, we learn how to make your home safe and secure with tips from Lowe's. You should do a safety check on your house at least once a year. Start with the entryway, making sure you have an insulated wood door in the doorway. Make sure there is a lock and a deadbolt lock on the door as well. Once inside, make sure you have timers to control your lighting, so it can come on even when you're not at home to detract any robbers. In the garage, make sure you have an electronic door ope...

In this video, we learn how to do some easy hairstyle for school. To do an easy bun, take a hair tie and put it in the hair in a side twist bun. Let some of the hair stick out, then take bobby pins and stick them in the bun to secure it, then you're done! The next look requires you to take your bangs and braid them together. After this, pull the braid behind your head and secure it with a bobby pin. The next look requires you to braid a section on the side of your hair, then put it into a pon...
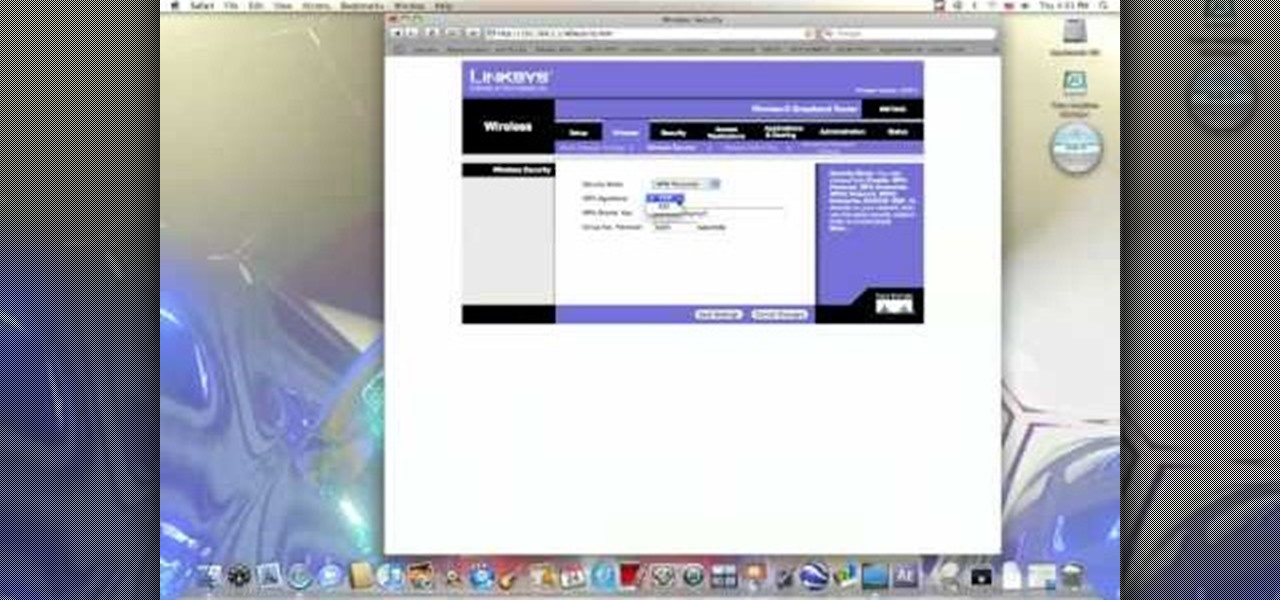
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...

This video is a tutorial on how to make a diaper cake. The cake is not edible. To begin, you will need a pack of diapers and rubber bands. Roll up the diapers from the waist down and secure them with the rubber bands. Put several rubber bands around a bottle of wine and secure the diapers in tiers around the bottle of wine. Cover each tier with tissue paper before adding the next one. Wrap each tier in blankets. Top off the cake with a can of formula wrapped in a decorate blanket. At this poi...

Have some files you don’t want anyone to see? Or maybe it’s just been a while since you’ve emptied your trash bin. The trash bin function is not a permanent delete but you can erase files off your Mac with this tutorial.

They say it is always darkest before the dawn. If that's the case, then perhaps there's a light ahead for Magic Leap after more unfavorable news in the form of executive departures.

On Sunday, Microsoft did what everyone expected the company to do by unveiling the long awaited HoloLens 2.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.
This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

Materials: Scrap fabric, elastic thread, cardboard, scissors, cellophane tape, and other bits and bobs ie feathers, buttons

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

Need to secure your track to the road bed for your model railroad? Well, this video tutorial will show you how to do it, not to mention show you how to weather your flex track.

Looking a for a secure and secretive entryway to your Minecraft base? Check out this video to learn a great design that uses pistons to make a trap door. With this trap door you can control who gets into your base, and who gets sent to the lava pit.

Concerned about unwanted eyes setting upon the information in your Android phone? This video will show you how to turn on the screen lock feature of your Android smartphone. Keep the information on your Android device to yourself with a lock screen.

Check out this Minecraft building guide to learn how to build a machine gun that can fire 25 arrows a second. If you need to secure your home from mobs, or you just want to have an awesome machine gun, watch this video.
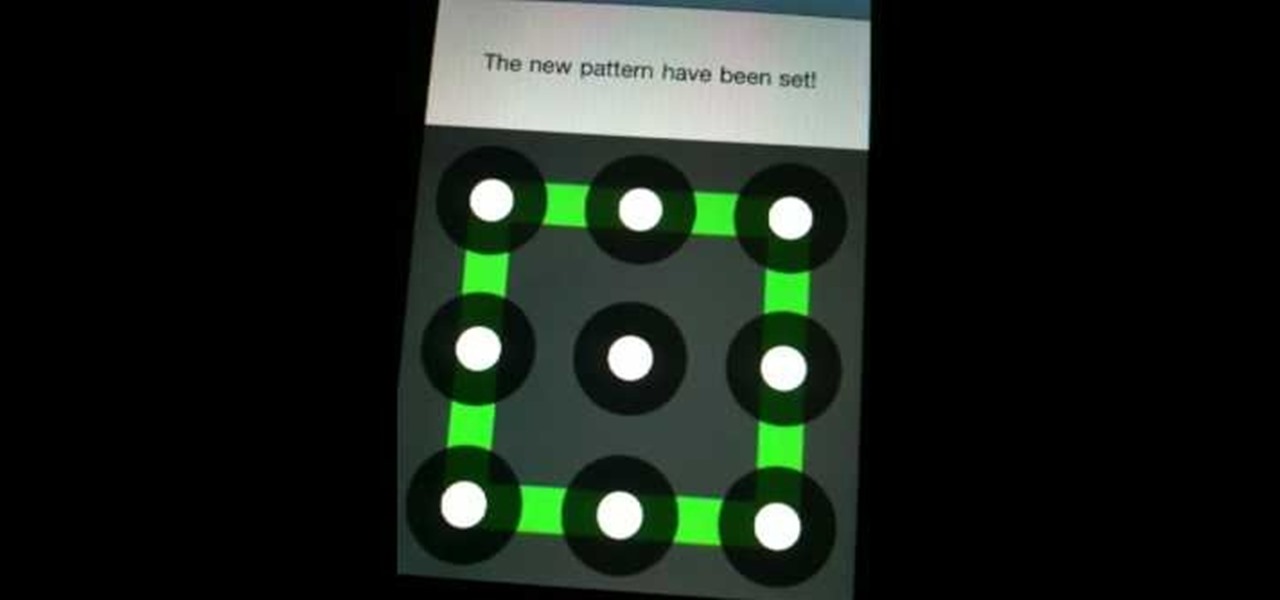
iPhone and Android both have a lot of great features. Enjoy the best of both worlds when you install Android lock on your iPhone. This is a great way to secure your iPhone. Use Android lock to get an extra layer of security.
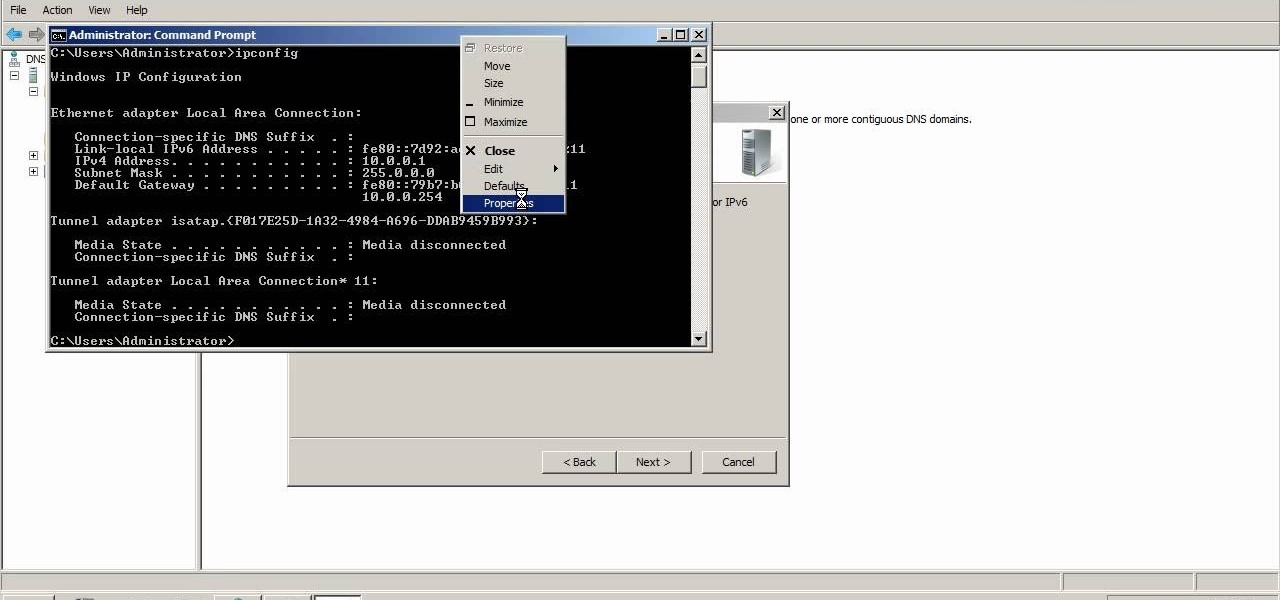
A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.

First, make sure that your image is hosted on a secure place online (such as your own Photobucket account). Then go to ImageMaps.com and use this free site to create your own image map that can now be added to your website.

This strategy guide is specifically for those who want to become better players at the multiplayer mode in Call of Duty: Black Ops on the map Kino Der Toten. Perfect for those who prefer one on one or two on two games.

Adding a SIM card to your Samsung Galaxy Tab is easy! If you have this new Android tablet and are looking to see how to install the SIM card, this video will clearly show you how it's done. Simply remove the slot's cover, insert the SIM card, making sure it's secure and snug, and then closing the cover. That's it!