With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

This video will show you how to secure your GoPro camera to your motocross, Snowmobile, Motorcycle, Skiing helmet so that it will not loosen up and fall off.

This video will explain how to safely weight down and secure a basket ball hoop with a water filled base that has a hole in it.

Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Millions of laptop batteries have been recalled because of the risk of FIRE. Get some tips from CNET to learn how to keep your laptop battery safe and secure. First, make sure your battery hasn't already been recalled. Second, don't leave the laptop constantly charging because it heats it up. One way to save your battery is to remove it completely when you plug in directly. Third, treat the battery as fragile. And finally, four, avoid buying knockoff batteries.

If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

If you've spent a ton of money on your newest smartphone, you will want to make sure it's secure. In this tutorial from the experts at PCWorld, learn exactly how to activate safety mechanisms on your Android. With these options you can set a complicated passcode (so that anyone who does find your phone won't be able to access your files) and you can also set up a locator. By using the location app, you can text your phone from anywhere else and set off a search alarm so you will be able to fi...

This video tutorial shows you how to use a long wrap product to dress yourself while creating a secure carrier for your baby. The long wrap is brought forward from back to front and round your belly button, criss-crossed over your back and brought forward and criss-crossed once more, then tied. The two criss-crosses (in the shape of an X) help hold the babies legs, as the pass through the criss-crosses and support the baby. You should then try to bring the fabric down as far as possible to su...

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

If you want to transfer files to or from your iPhone at ease, check out this video on how to SSH / SFTP into your iPhone. SSH (Secure Shell) and SFTP (Secure File Transfer Protocol) all can be used to safely transfer files to your iPhone!

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

In this video, we learn how to install dry acoustic flooring with Fermacell. To start, you will level the floor and apply compound if you need. Next, you will lay the Fermacell around the room on top of the leveling compound. Push the flooring tightly together so there are no spaces in between them. You may need to cut the flooring to make sure it's the correct shape for the wall. After this, apply flooring adhesive to the seams to make sure they are secure as they are laid down. After this, ...

In this video, we learn how to use secure online passwords. There are a ton of things to consider when creating a password. A weak password is something that someone can easily guess. If you are using a birthday, common dictionary word, child's name, or something common then you are at risk. Your password should combine letters and numbers, and be at least eight characters long. It should also be completely random and have upper and lower case letters. You can use a password assistant if you ...

The way to wear hijab shown in this demonstration with a simple wrap around the head, securing the hijab with bobby pins at the back of the neck. The ends of the hijab are pulled forward to the chest. Then a thin scarf in a contrasting color can be wrapped around and tied at the nape of the neck as well. A portion of the hijab is pulled forward over it and pinned over the ear. Then one of the ends is pulled under the chin to the opposite ear and pinned to the head. The other end is wrapped ar...

Several Tanzanian girls demonstrate how to tie a kanga (an African sarong). The first method is to wrap the kanga around the waist and tuck the end in at the waist to secure. The second method is to wrap the kanga into a cylinder to use it as a base for carrying a parcel on the head. Another way to wear the kanga is to wrap it around the neck like a shawl or wrapped under an armpit and tied over the shoulder for a fancier look. To wear the kanga as a scarf, fold it into quarters the long way,...

To create an apostolic or pentecostal hairstyle, start with a poof in the front of the hair. It can be ratted behind for stability. Use two bobby pins to secure the back corner of the poof. Squirt the hair with hairspray before moving on. Then create a low ponytail in the back of the hair, pulling the top up and out slightly while forming the ponytail so it creates another poof in the back of the head. Spray the ponytail with hairspray then smooth out the hair on the top of the ponytail. Wrap...

This video illustrate us how to make a light bulb oil lamp. Here are the following steps; Step 1: Take all the things required that is bulb, socks,adhesive tape,scissors,kerosene, rim with a hole in the center.

In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...

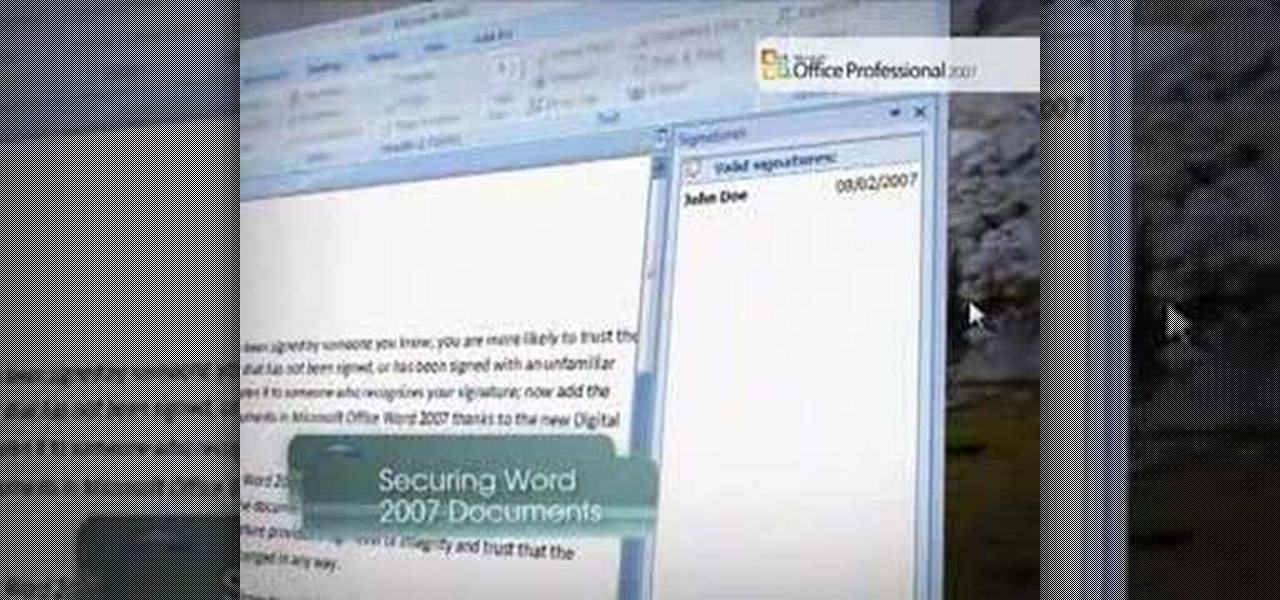
Securing Microsoft Office Word 2007 documents with Digital Signatures - When you receive a document that has been signed by someone you know, you are more likely to trust the contents than those of a document that has not been signed, or has been signed with an unfamiliar signature. Signing a document validates it to someone who recognizes your signature, now add the same degree of integrity to your documents in Microsoft Office Word 2007 thanks to the new Digital Signatures feature. For more...

This half-hour episode of Hak5 covers several topics: Using a DSLR camera to create HD footage, building your own Google TV, unlocking & copying locked files with Lock Hunter, using PicPick for screen capture, using WinDirStat for analyzing & cleaning your hard drive, setting up a secure FTP server with Ubuntu Server, and secretly copying data from USB drives with USB Dumper.

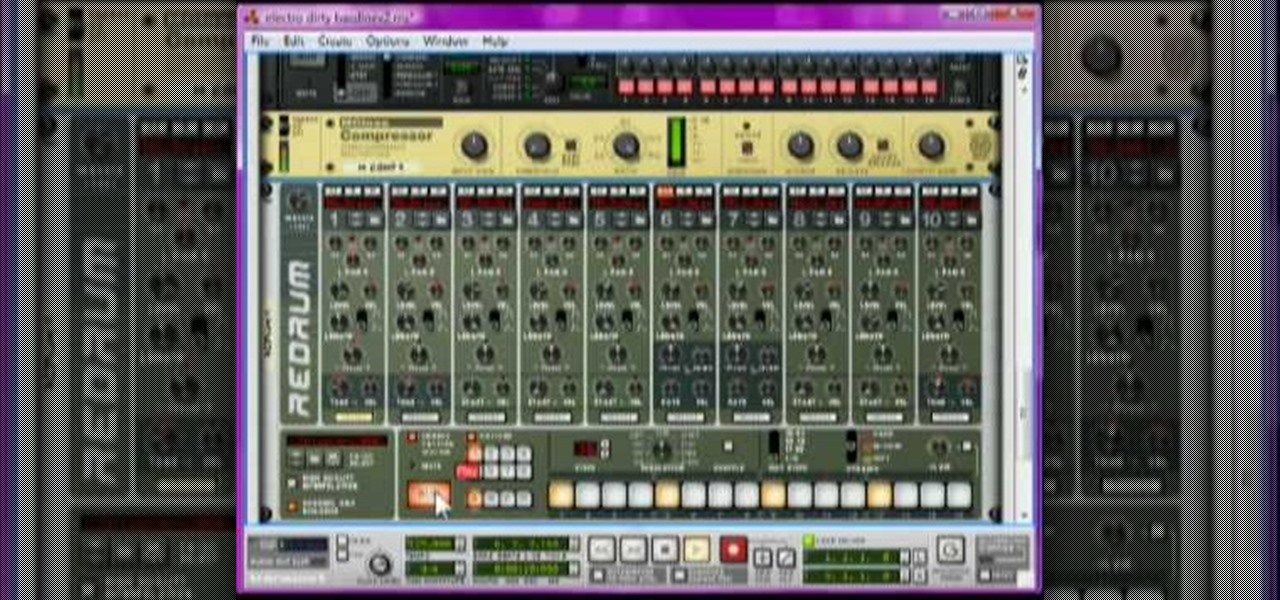
Justice might not have produced any new material in a while, but their place in electronic music history is already secured due to their filthy electro-house beats that have become ubiquitous in the years since they first broke out. Watch this video to learn how to make a dirty electro bass synth line like theirs in Reason 4.

One of the new areas that you can access in Dwarf Fortress 2010 is Hell itself. This video will show you how to get there and what to do when you do.

This video will show you how to build and use hospitals to take care of your dwarves in Dwarf Fortress 2010. It also discusses what happens when you abandon and then reclaim your fortress.

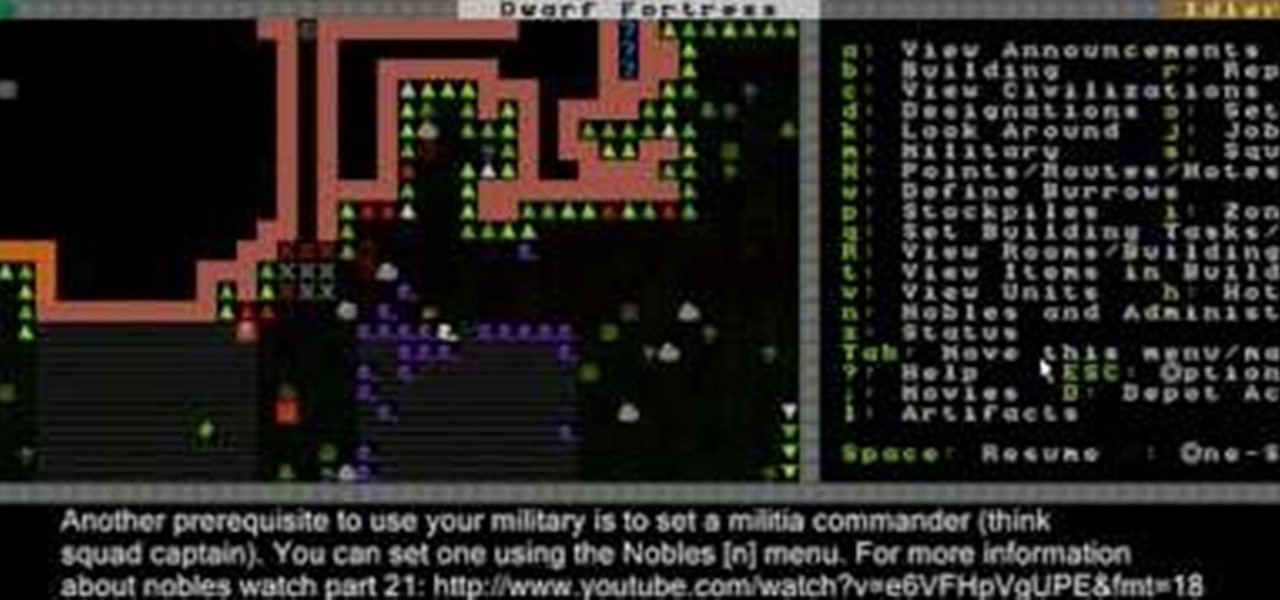
In this video, you'll learn about the basics of using your military to defend your fortress, in this case against a dinosaur attack, in Dwarf Fortress.

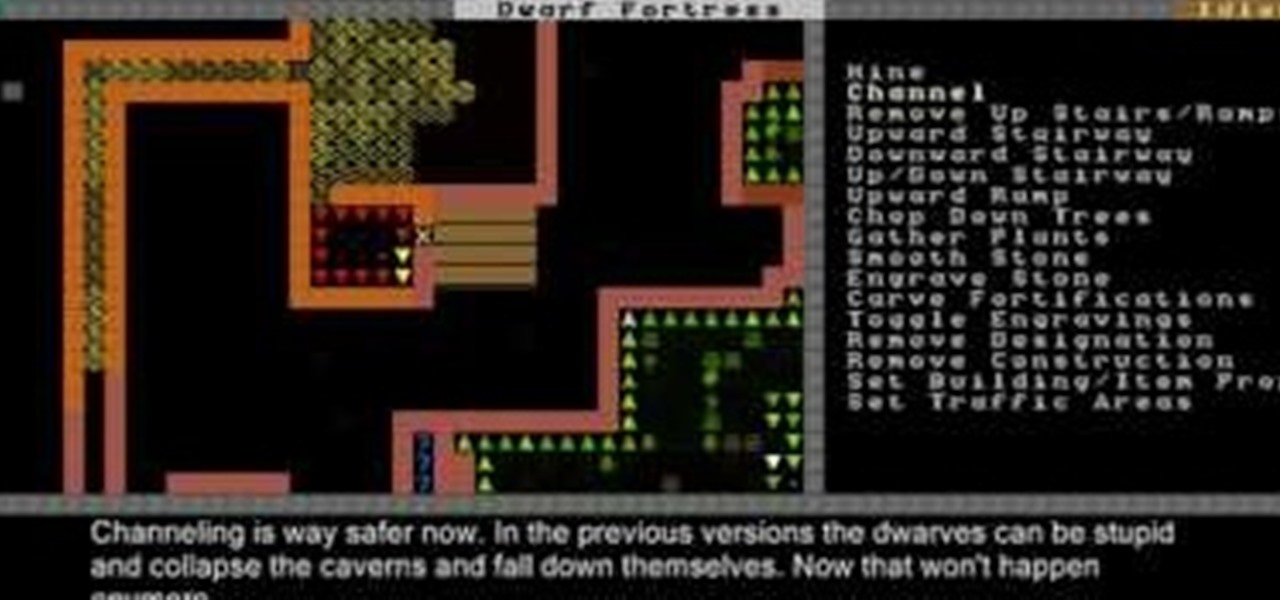
This Dwarf Fortress 2010 video will show you how to design a basic, effective fort, and also explain how channeling and farming work.

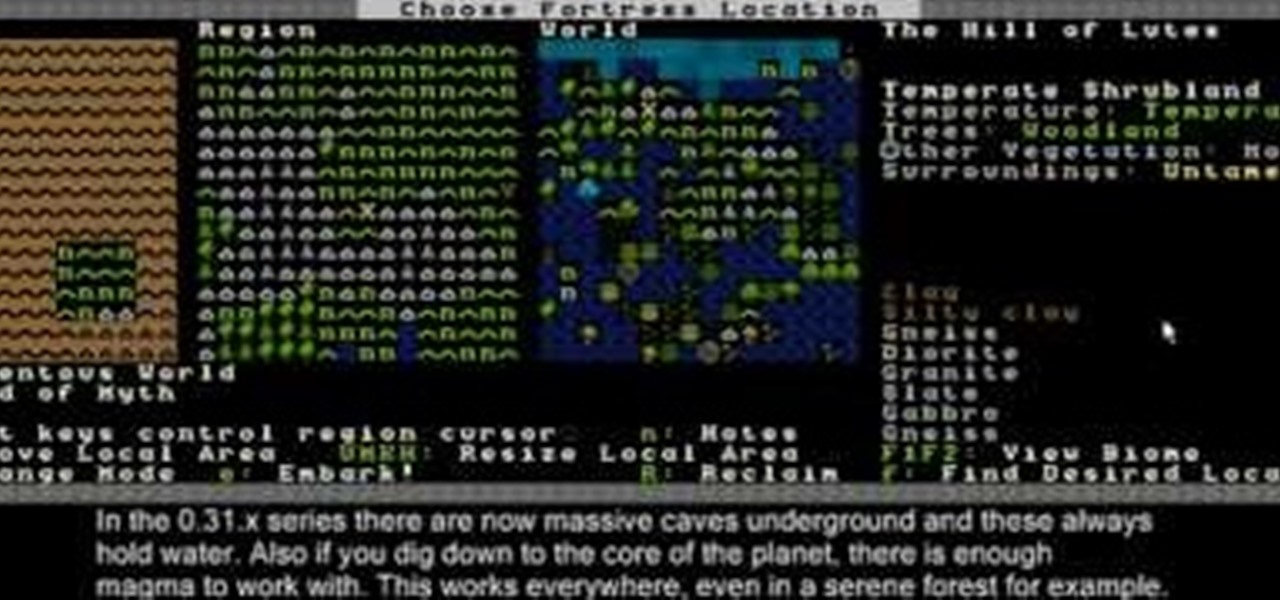
The release of Dwarf Fortress 2010 introduced many great changes to Dwarf Fortress, and this video will bring you up to speed on them. It also covers the beginning of a game, including preparing your dwarves, choosing a fortress site, and getting into caves.

This video will give you an overview of a successful endgame fortress from Dwarf Fortress, giving you tips on achieving a similarly successful fortress throughout.

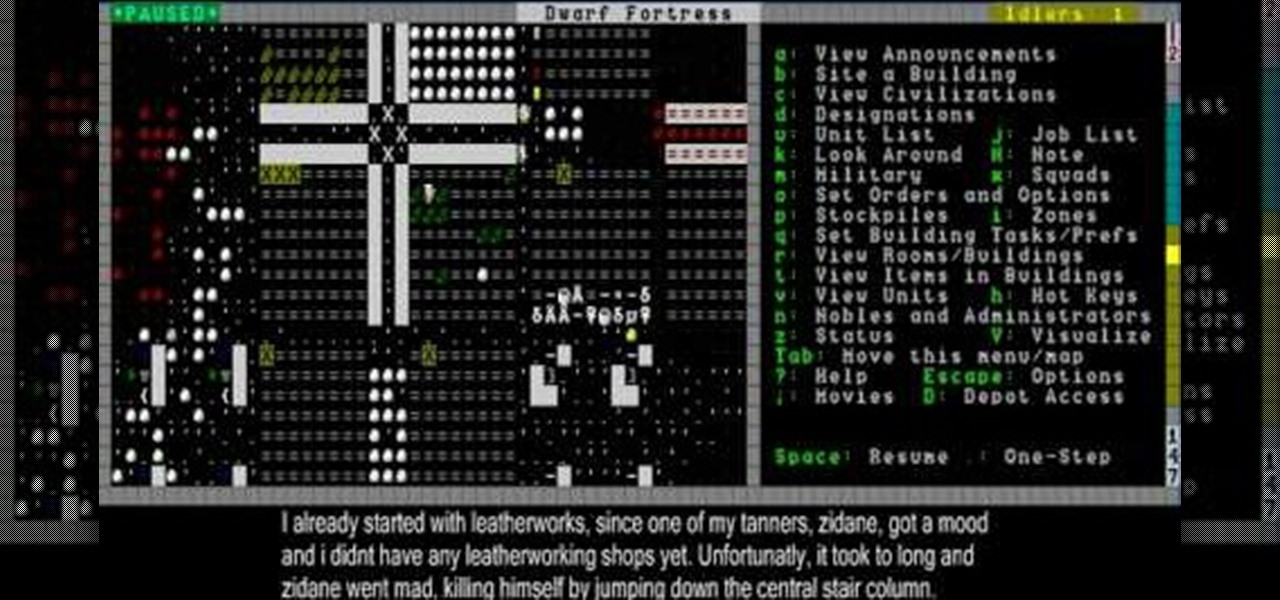
In this video you will see the results of the creator's preivous attempts to use a cave-in to trap demons in their peculiar chamber, then learn how the Justice and Economy systems work in Dwarf Fortress.

The best way to deal with demons in Dwarf Fortress in to seal them in their peculiar chamber by creating a cave-in above it. This video will show you how to do just that.

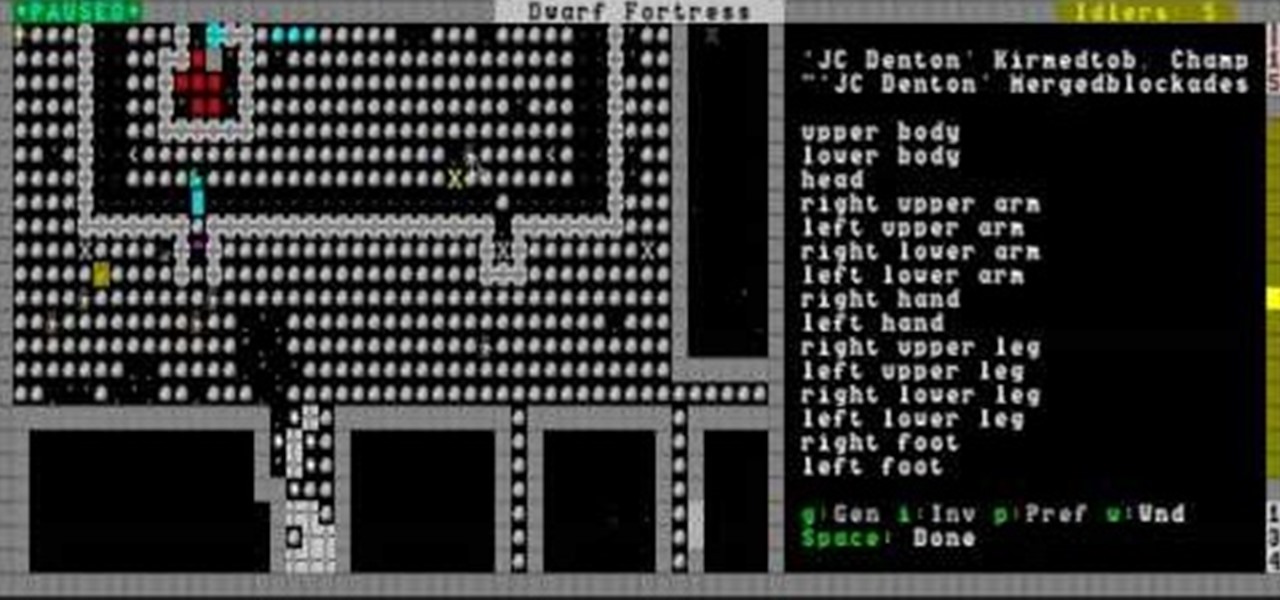
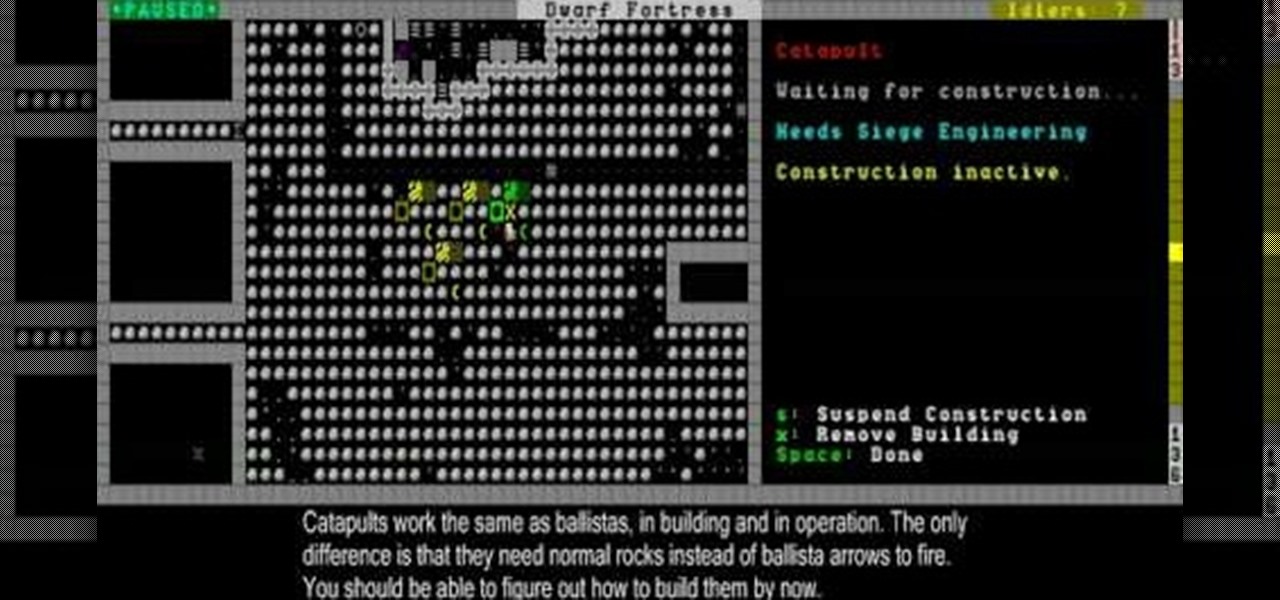
This video will show you how to make and use siege weapons and disarm enemies in Dwarf Fortress. It also includes an arena battle at the end for kicks.

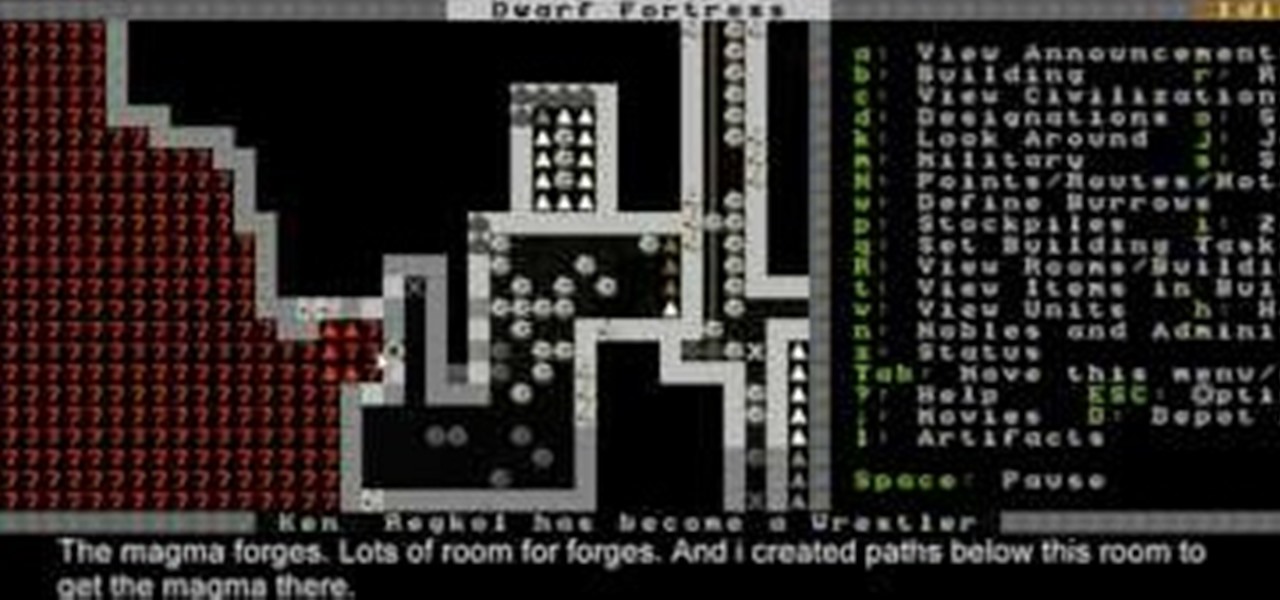
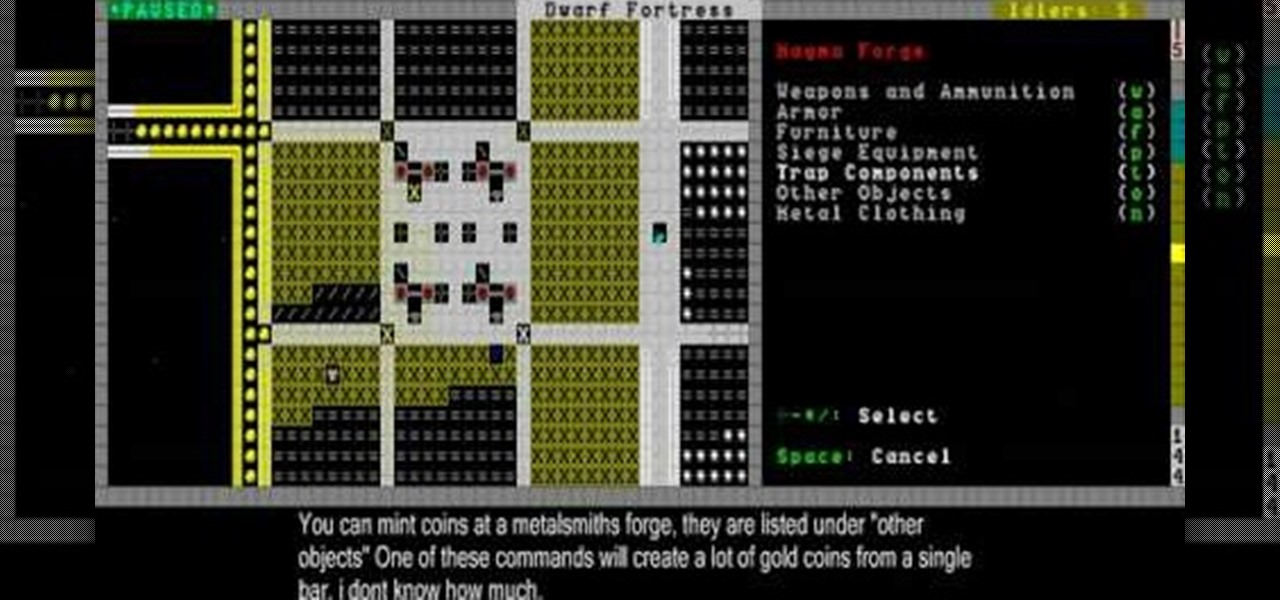
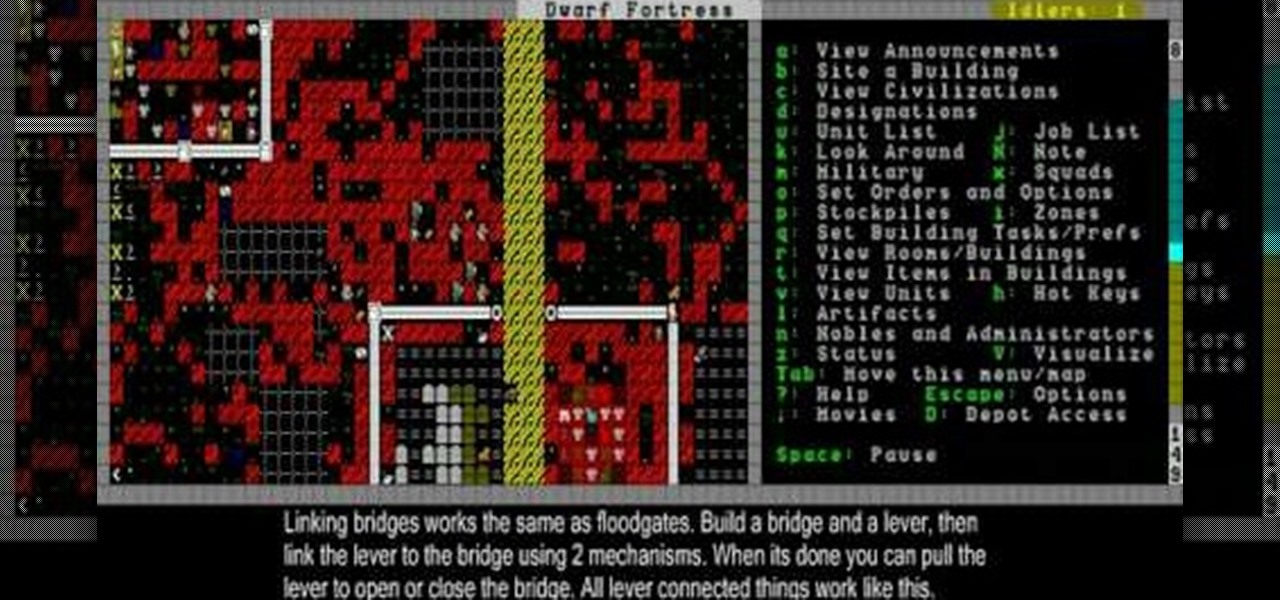
Magma is valuable but dangerous stuff in Dwarf Fortress, and this video will teach you still more about how to handle it. It also covers how to build bridges, floodgates, and levers that will link up and create effective dwarven infrastructure.

Water and magma can both destroy even a sturdy dwarf fortress very quickly. This video is all about liquid safety, teaching you how to channel water and magma using u-tubes and other tools without flooding your fortress and killing your dwarves.

This video starts with a new Dwarf Fortress fortress, and will show you how to deal with underground rivers and magma pipes.

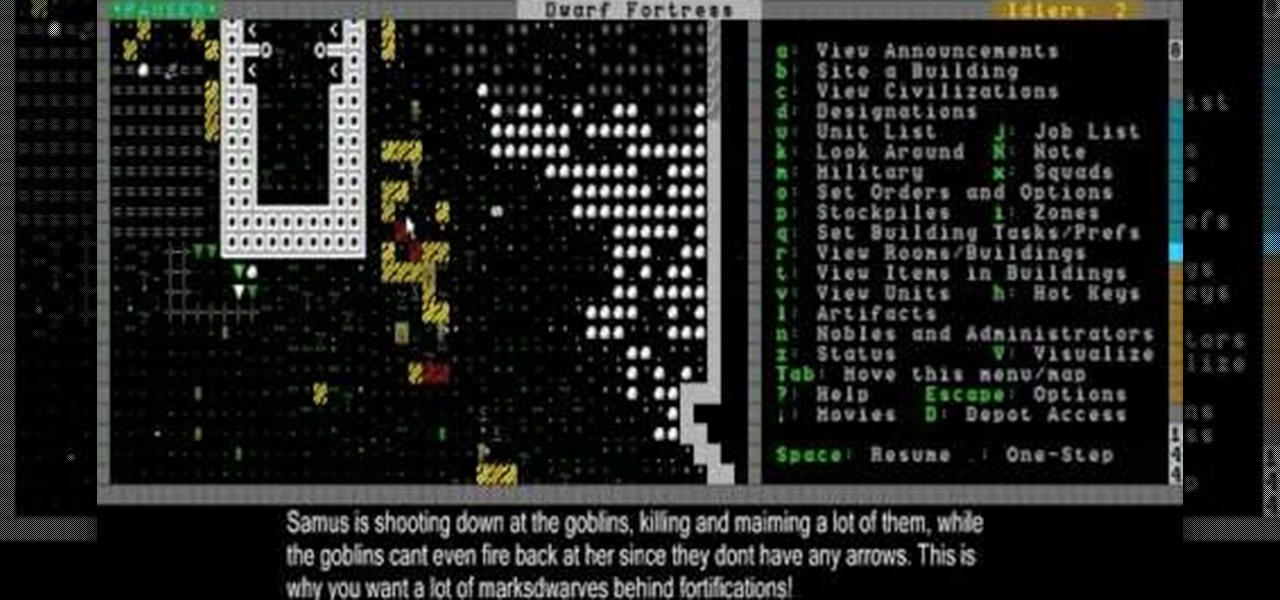
At this point in the game, Dwarf Fortress is starting to get serious. This video will show you how to defend against a goblin ambush and deal with graveyards and coffins, the resting places of your dead dwarves.