Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Apple officially unveiled the long-awaited iPhone X, its tenth-anniversary edition iPhone, on September 12. With preorder and release dates just around the corner, you'll want to brush up on all things iPhone X to make sure you get your hands on one as soon as possible. After all, preorders start Friday, October 27.
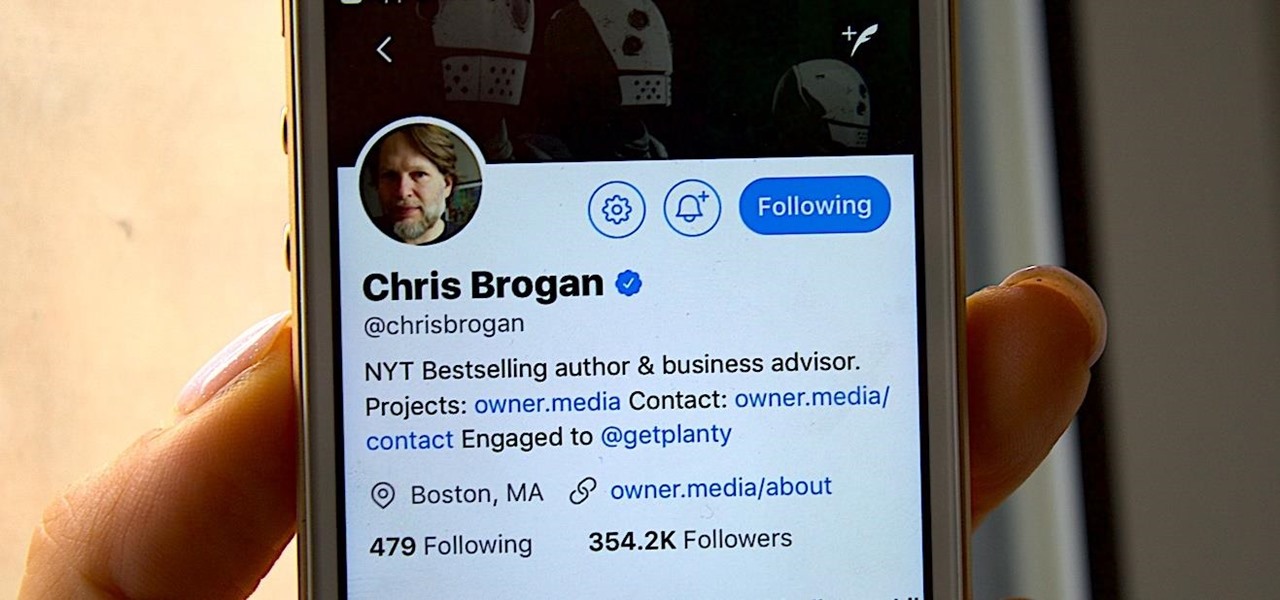
Chris Brogan is no stranger to using multiple social media platforms all from the comfort of his phone. In fact, not only does he have over 350,000 followers on Twitter, but he's also an avid YouTuber, Instagrammer, podcaster, and blogger.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Whether your palate runs to domestic or imported, a piece of cheese can be a real treat for the senses. Its smell, taste, and texture are all parts of its appeal. A big part of what makes that savory wonderfulness comes from the microbes in and on the cheese. Thanks to a team of researchers dedicated to studying those microbes, we have a better understanding of their importance to cheese and us.

Just like your gastrointestinal tract, and the soil we walk on — a dust storm has a collection of bacteria, fungi, and viruses all its own called a "dust microbiome."

There's no debating that the Galaxy S8 and S8+ are top contenders for the most beautifully designed handsets of 2017, but the same can't be said for their TouchWiz interface, which has been met with lukewarm reception at best.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

In my days as a hardware tech, I often came across motivated do-it-yourselfers who watched a video or two on how to repair a phone and thought that they'd give it a go. More often than not, they failed miserably and damaged their phones (and wallets) even more in the process.

Starbucks last big hit was definitely their Vanilla Sweet Cream Cold Brew, which became a permanent menu item—not just a summer fling—on May 31, 2016. It's the perfect blend of 20-hour cold brew and vanilla sweet cream; The result not only tastes great, but the cream makes is visually mesmerizing as it floats down through the brew.

If you've ever played the game of Would You Rather, you've probably been given the ultimatum between eating insects or doing something else that sounds absurd, like licking a cactus. I'm advising you to always choose the insects, and here's why:

Samsung's Note series is directly responsible for some of the biggest innovations in smartphones. As the first "phablet," it sparked the current craze for bigger screens, and the S Pen stylus has been mimicked numerous times. Even the curved display made famous by the Galaxy S6 edge made its debut on the Note 4, so this is the one smartphone line you want to keep track of if you like to stay on the bleeding edge.

The world of augmented reality has seen a myriad of different products, from sensor-laden smartphones to robust holographic headsets, but Google Glass's failures nearly killed the middle ground.

Fast food is a guilty pleasure in which we all indulge. When you're short on time and long on hunger, being able to whiz through the drive-thru or run 'in and out' of a fast food joint can be a real lifesaver.

Make delicious candy for Easter from the comfort of your kitchen with copycat versions of your favorite classics: Marshmallow Peeps, Cadbury Creme Eggs, Reese's Peanut Butter eggs, Almond Joy bars, and chocolate bunnies. The best part is that you get your sugar fix without the preservatives.

If you think that "pawpaw" is just an affectionate name for your grandfather or a cute way of talking about your cat's feet, you're missing out on one of the most interesting fruits out there.

Whatever you want to call it for now—Android Nutella, Android Nougat, or Android 7.0—the upcoming "N" release of Android will surely bring in tons of new features and functionality. We know it will be named after a dessert, and we know that Google uses an alphabetical naming system, so something starting with "N" is next in line after Android 6.0 Marshmallow.

If you've spent any time at all recently on social media, then you've probably seen pictures of fairy bread. This magical creation comes to us courtesy of Australia, so we have yet another thing to thank those clever folks Down Under for... along with shrimp on the barbie, Vegemite (the Aussie cousin of Marmite), and Hugh Jackman.

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

One of the hottest trends in the food world right now is "spiralized" vegetables. I will confess that I am a bit suspicious of any diet or food fad that eliminates an entire food group for anything other than physician-ordered health reasons, but something really good has followed in the wake of the Atkins/paleo/gluten-free movements.

Tonic water, seltzer water, club soda, and mineral water: these 4 types of "bubbly water" are often, erroneously, used interchangeably. But the truth is that each possesses unique qualities and uses that set them apart from each other.

Fall is a time of change. The leaves change color, the weather changes from warm to cool, and we change our clocks to fall back an hour. This last change means that many of us will get home from work in pitch-black darkness; for me, the early onset of night makes me less interested in cooking dinner and more interested in getting in my sweats, throwing leftovers in the microwave, and binge-watching The Affair.

While most of your iPhone's features are intuitive or well-covered across the web, there are some features hidden deep within iOS that you probably never even knew about. (These could also apply to an iPad or iPod touch.)

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

What is gluten, why do some people think it is pure culinary evil, and why are there more and more products devoted to being free of this mysterious substance? Here's what one person thinks: What Is Gluten Really?

For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step processing getting the breakthrough desktop operating system running on the latest greatest hardware.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Many of us in the Steampunk community have pets that we love and cherish, myself included, and we want those pets to share our joy of Steampunk. In reality, they couldn't care less, but for some reason we still love to dress them up. Their reactions usually range from bemused acceptance to temper tantrums, but the awwwws we get from onlookers usually makes it worthwhile.

There's something special about Laika Inc.'s Paranorman... Hey! Did you love Coraline? Are you interested at all in stop-motion animation? Well, watch this feature on Laika Inc.’s new film, Paranorman.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Every year, Apple releases new wallpapers for its iPhone and iPad software updates, and that's exactly what happened with the iOS 18 and iPadOS 18 updates released on Sept. 16. But you don't need iOS 18 or iPadOS 18 to enjoy Apple's new backgrounds — you can download and use them on any device, whether a smartphone, tablet, computer, or something else.

Android has a new security feature that every Android smartphone user needs to start using — even you. It won't change how you use your phone, but it will make life harder for nearby thieves.

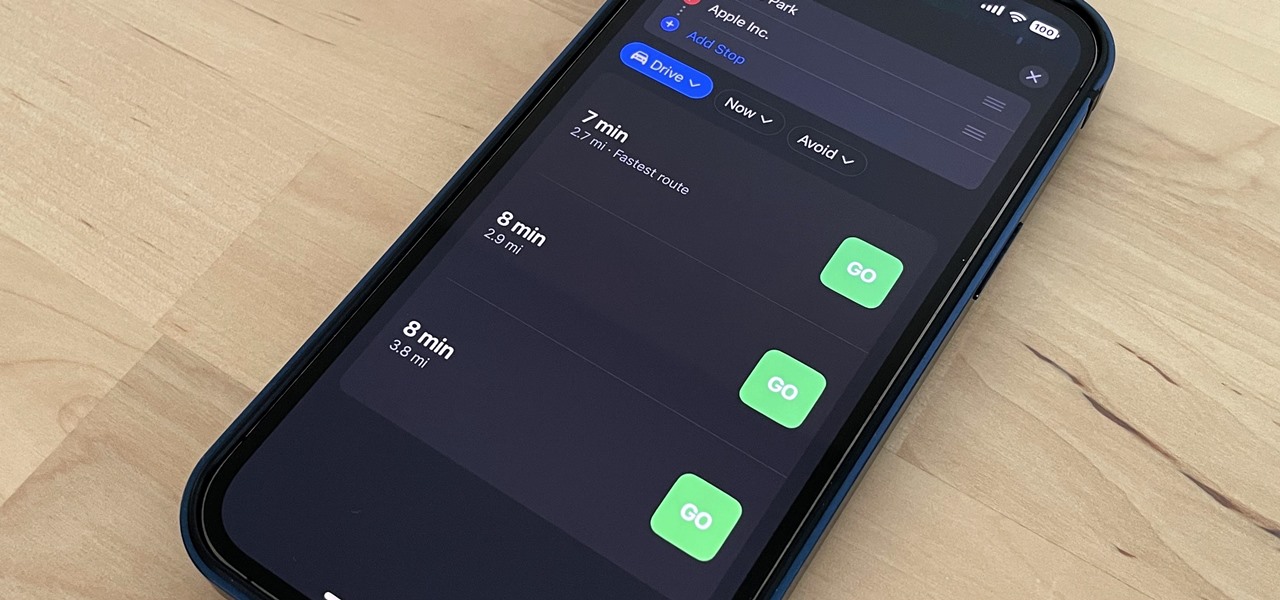
Apple removed the option to quickly change between miles and kilometers when using Apple Maps on iOS 16, but it's not entirely gone — it's just not as easy to find.

There are many ways to access the Google Assistant on your phone, but Android 12 adds another one for Google Pixel models that may be the best way yet.

From Time Machine to Cartoon 3D Style, Snapchat has strung together a run of viral AR Lenses as consistently as Beyoncé drops hits songs.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

You won't have to ask Santa for holiday-themed augmented reality experiences, because practically any social and shopping app that offers AR effects has them available now.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.