
How To: Make a soda bottle submarine
Do you want to create your own underwater adventure? Then let the A-TV science squad show you how to make the coolest underwater vessle around. You'll be the captain of your own submarine in no time!


Do you want to create your own underwater adventure? Then let the A-TV science squad show you how to make the coolest underwater vessle around. You'll be the captain of your own submarine in no time!

Want a race car that never needs any gas? Then learn how to build your very own magnetic boxcar. With the magnificent magnetic force on your side your car will be cruising in no time!

In this article, I'll show you how to build a coil gun. A coil gun is a device that fires magnetic projectiles at high velocities, using electricity. Coil guns require no explosive propellant, therefor can be fired an infinite amount of time, providing that there is ammunition and available electricity.

Dual booting Ubuntu 10.10 Maverick Meerkat and Windows 7 is fairly easy. If you don't believe me, just read on!

Levers are the only toggleable way to provide a steady source of power to your redstone circuits, but they're ugly and they stick out like a sore thumb. Just look at this:

Here's another Null Byte on hacking our Skyrim game saves. Some of the rarer items in Skyrim are really fun to play with. However, seeing as they are rare, you will probably not see all of the best weapons in the game. Null Byte doesn't take too kindly to games that don't give us the rarest items when we please. Let's beat this game into submission by hacking our game save files via hex editing.

Iowa firefighter Pete Lilja has modded the software of a Canon powershot to record images of Earth, from as high as 85,000 feet!

A local butcher, who knows their customers by name!?! What a concept! This Hillhurst hot spot is planted smack dab in the sweet spot of Los Feliz. What I had been dreaming of for years, ended up walking distance from my home a few months ago, and the place couldn't be finer! McCall's is a husband and wife run meat and fish shop, where they are happy to help meal plan and recipe swap. The pair, Nathan McCall and Karen Yoo both have training from some of the finest restaurants around (Sona, Da...

If you rely on WhatsApp as your messaging go-to, you're probably all too familiar with the default background in chats. While its distinctive look definitely sets it apart from other messaging apps, you're free to swap it out for something more appealing.
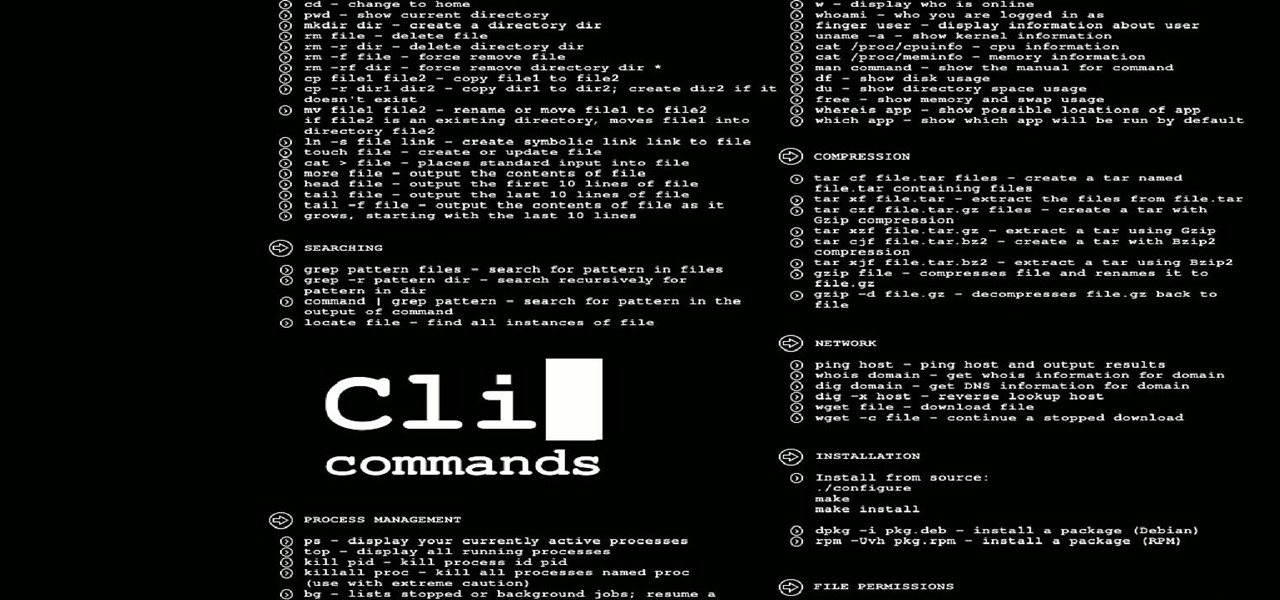
Hello everyone on null byte this is my first tutorial This Tutorial Is on Useful Lesser Known Commands on Linux
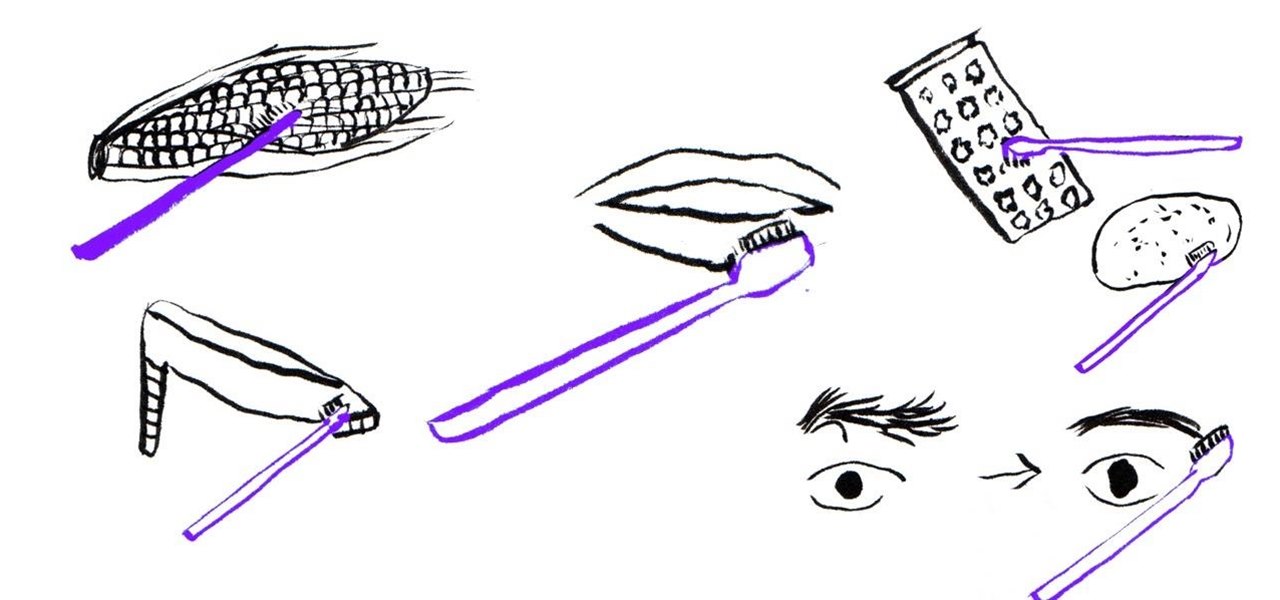
We all know to should swap out our toothbrushes one every three to four months, but did you know your used Toothbrush still has a number of handy uses once its time in your bathroom is done? You can use an old toothbrush indefinitely to remove silk from corn, exfoliate your lips, tame your unruly eyebrows or clean your cheese grater before sticking it in the dishwasher.

Record stealthily, in the dark. This hack is simple and will turn any LED flashlight into an infrared night vision light you can use with any video camera.

The internet is something most people rely on, so when you buy a used laptop without a wireless card or yours needs to be replaced, it's easier to do it yourself. Having someone else do it can cost more than you think, so here's an easy way if you own a Dell Inspiron E1505.

Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as this list from the Wall Street Journal of the fifty most common passwords gleaned from the 2010 Gawker hack. If your password is on one of those lists, you need to change it. Right now.

Guitar pedals add character to your playing. However, musicians still say that certain pedals by themselves don’t live up to its promise of a perfect sound. Therefore, instead of replacing your guitar pedals with new and expensive ones, you can modify your pedals using different DIY kits available online and at local music stores.

In this article, I'll show you how to make a high-powered, long-range, air-powered rocket gun. This launcher is based on a sprinkler valve, a modified propane tank, and a few other components. Though not hard to make, this device is VERY dangerous! The rocket can seriously harm, if not kill any living thing it's shot at. Here's a video of it in action, quite an accurate shot by my friend Chris... Parts
Rockets are lots of fun when you are launching them. However, finding them can be an arduous if not maddening task. Fancy space rockets have lots of tracking equipment to make touchdowns as simple as pie. Today, we look at embedding LEDs into your hobby rocket for easy night flight fun!

Are you the expert hacker we're looking for? Do you have a great idea for an article on Null Byte? Do you have a passion to write, and more importantly... teach?

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.
Game design is sedentary work. Generally its practitioners do their work with their butts planted securely in front of a computer in an office (be it home or away) as their muscles and verbal skills atrophy. Even game journalists are prone to this condition. Not so with Colin and Sarah Northway (pictured below), the husband and wife team behind NORTHWAY Games. Not only do they make really cool indie games, but they do it with just a laptop while traveling the world meeting indie developers of...

By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe".

If you already have your basic keyboard shortcuts under control—we're talking classics here, Control-C (copy for PC) or Command-C (copy for Mac)—it's time to load up your memory bank. There are endless shortcuts available (truly endless—since you can customize them yourself), but you don't need to memorize them all, only those you expect to use most. Below, two cheat sheets for upping your keyboard maneuvering status from "basic" to "intermediate" for both Mac and PC users.

Mass Effect 2 may have been around for a whole year... but not on the PlayStation 3. And last Tuesday, January 18th, PS3 gamers finally got their hands on a copy of the critically acclaimed RPG. Actually, this is the first time any Mass Effect game has been available on the PS3, making this a historical event for BioWare.

Find a mates, dads, mums, brother or sister car size tyre to your car or someone eles' When they go to bed take their keys.

Welcome to part three in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.

Before jumping right into becoming the next James Neely or Moose Peterson, you're going to have get situated with your new digital SLR. No matter if you purchased the Canon EOS 5D Mark II body and lens separately or together, you've got everything you need to get started except the CompactFlash (CF) card. If you plan on shooting in RAW or capturing HD video, I suggest getting an 8GB or larger CF card. If you can afford it, maybe even opt for a high-speed UDMA card.

Finally, summer is just around the corner! And while there are delicious fruits and vegetables available nearly every season, summer yields some of the very best picks. Equip yourself with one or more of the tools below before your next trip to the farmers market.

Nope, this isn't a flash game version of SCRABBLE. There's already one of those (and a multitude of imitations) for the Apple iPhone, iPod, and Facebook. This is an electronic game, and it's not a "handheld" game like the SCRABBLE Pocket Pogo Touch Screen Game (pictured right). It's an entirely new way to play everybody's favorite word game, and it's called SCRABBLE Flash (BOGGLE Flash outside of the U.S. and Canada).

There is a lot of mystery and voodoo surrounding blues guitar these days. With the common opinion claiming that in order to play the blues you have to really feel the music and respond with your playing. While this is certainly the case when improvising, I would argue that a good knowledge and understanding of the basic principles of blues guitar can provide even the beginner guitarist with a great sounding set of licks to impress friends and family.

Spring has sprung, which means it's time to plant all those delicious vegetables and lucrative cash crops. If you are like me, every year you meticulously plan every aspect of your garden before dutifully neglecting it all summer. I decided enough was enough and built this simple automatic watering system.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

How is it that we use Firefox tremendously and yet not care for its needs? You might have noticed Firefox sometimes tends to slow and not respond often. You might have installed countless add-on in Firefox to enhance your using experience, to get the most out of your Firefox use these Hacks. The about:config page contains all most all of the tweaks and enhancements available for Firefox to day.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

You're currently playing a heated game of Scrabble or Words with Friends. The game is close, too close for comfort. But you're not sweating because you're confident. You play a huge word that puts you in the lead, but then when your letter tiles are drawn...

Facebook's new Timeline feature has been rolling out gradually since its unveiling in September, but yesterday it finally became available to Facebookers everywhere. It's even available on your mobile device, too. Those who want to upgrade to the radical new profile design can do so by simple logging into their Facebook account and visiting the About Timeline page on Facebook.

Grand Theft Auto 3 was the biggest video game of the last decade, by far, introducing open-world adventure games to consoles, a genre that now rivals shooters and sports games for market dominance. A huge map, decentralized narrative, and myriad of interlocking quests and objectives that happen in a flexible order all became hallmarks of the "new" genre, along with the ability to shape the morality and reputation of your character. And most importantly, all of the quests and stories are compl...

You get a skateboarder ( Bam maybe? ) to think that he is going to do a huge skateboard jump onto a mat ( doesn't have to be a mat ). When you show him to jump and go through the landing plans, you show him the mat as well. When he goes back in to get ready, you swap the mat for a poo filled container!