In this video tutorial, viewers learn how to replace a key on a Samsung notebook keyboard. This task is very fast, easy and simple to do. Begin by placing the small retainer clip into the small areas of the key. Make sure the retainer clip is aligned on top of the keyboard and is securely placed on. Then simply place the key over the retainer clip and press on it. Hold the bottom of the key with one finger and press down the key with another finger. to secure it in place. This video will bene...

This video describes the easy process of building a garden retaining wall. First you will need to map out your area for your wall with strings and dig your trench for your stones. You will be filling the trench with gravel to hold your stones in place. Make sure to pack to gravel securely into the ground. You should have a leveling tool to ensure your base is very level. After you make sure that first level is secure and in place you will stack your next level of stone. Once the homeowner has...

Alazzo Clothing demonstrates how to measure pant length. Measuring pant length is important when ordering clothing online or ordering custom made clothing to ensure a good fit. To measure the length of pants, place a tape measure at the top of the pants waist. Hold the tape securely and then bring it down to the bottom of the pants. You can also measure to one inch from the ground. When measuring pants length, be sure to follow the seam. Utilizing the pants waist to bottom of the pants method...

This video shows how to throw a sinker baseball pitch. The instructor begins by showing his two seam grip on the ball and notes then he does not use the strong thumb tactic while pitching. The instructor explains how he throws through the inside of the baseball which involved his hand rolling over mid way through the pitch. Another pitching technique the instructor shows is the cross finger throw which is when you hold the ball securely with only two fingers on the ball with the thumb only sl...

This video shows the viewer how to secure crimp beads using both crimping pliers and chain-nose pliers for the purpose of jewelry making. The video uses two millimeter crimp beads, beading wire, and both sets of pliers to demonstrate the technique. To crimp using the crimping pliers, the viewer will utilize both notches of the pliers to crimp the bead onto the wire. In order to crimp using the chain-nose pliers, one must simply flatten the bead onto the wire. Crimping is a good method to secu...

Christina of Bright ling Beads explains how to use a fold over crimp to finish an organza ribbon necklace. First, fold down the ribbon approximately an eighth of an inch. Then, fold it down over once again. Make perpendicular folds bringing each fold towards the middle and making the end of the ribbon as wide as the crimp bed. Lay the folded ribbon inside the crimp, leaving a small piece of the ribbon sticking out of the top. Use flat nose pliers to hold the tab of the crimp and hold the ribb...

CyclingSecrets will show you how to lubricate your bike chain. First, start with a good quality lubricant a good one will keep your chain clean. Hold the bottle securely and apply the lube while cycling the bike around. Keep cycling the pedal around for a while so you get the lube all worked in the gears so it gets worked in good. When you have run through enough times you just wipe of the chain and bike with the excess oil.

Learn the tricks to running a three-legged race – without ending up flat on your face! Step 1

Check out this video to learn a technique for attaching soft clay to soft clay. No scoring or slip is needed. By just applying firm pressure to get a good strong joint. The small clay coil is used to reinforce the joints, and the blending is to make sure both parts are joint securely. Finally give a little pull to the new piece of clay that was attached, to test how good the joints are. If it comes loose than you are not applying enough pressure in joining the two pieces together. Finally, if...

In some places, it's illegal to ride your bike at night without lights or reflectors, so if you plan on going for a joyride on your street bike, then you need to be prepared to share the road with vehicles and be seen. Appropriate gear and lighting are essential for safety when riding a bike at night.

If you have ever found yourself working on a car project at your home and ran out of fuses, this tutorial is for you. Instead of going out and paying around $30 to $40, make your very own. It's wasy and saves you time and money.

Making a jewelry organizer is a fun and easy project to do! Orielle Hopkins, the Money Smart Mom, gives tips on making a great organizer for a minimal amount of money. Make a trip to your local craft store and search for a bead organizer with enough compartments to store your jewelry. If you have a lot of jewelry you may need to buy more than one organizer. Select adhesive backed felt in your favorite color for your project. Measure each compartment in the bead organizer and cut squares of fe...

This video shows how to make a peasant blouse, using a T-shirt pattern from a previous video. Take the front of the T-shirt pattern and cut it out of your fabric. You will need two pieces the same, one for the front and one for the back of the blouse. Save the extra fabric from the neckline to add length to the sleeves. Place the two pieces right sides together and sew the side and shoulder seams.

By watching this video, you will learn how to create your own art journal. Begin by cutting pieces of heavy weight cardstock 5" by 8". After you have cut all your sheets, fold them in half. If you want a defined crease, you can use a bone folder. Next, poke small holes in the crease of each sheet. Start at the center and then poke one every inch above and below the center hole. Then using a regular running stitch, sew through each hole of a single sheet. Once you reach the bottom hole, bring ...

The first step in removing acrylic from nails is to cut nails down with clippers. Next file off gel sealer and seventy percent of acrylic with file or nail dimmer. The demonstrator then cut ten squares of foil, one for each nail. After the foil is completed cut cotton rounds into four pieces. You will only need two and a half cotton rounds. Using one hundred percent acetone saturate each cotton piece that you cut. Place saturated cotton pieces on each finger and then wrap securely with foil. ...

In this video, Meg will show you how to make your own wreaths. You’ll be creating two scenes on your wreaths : a woodland and an aromatic one. You’ll need 2 cardboard rings (one slightly smaller) cut in wreath forms, green moss, a hot glue gun, a knife, some pretty fabric, and a handful of old corks.

Preheat oven to 425. Place butter in 9 x 13 baking dish and place in oven as it preheats. Place chicken pieces in zip top bag. Add flour and shake to coat. When oven is warm, remove pan from oven and place the floured chicken in pan with the melted butter. Return to oven and cook for 30 minutes. Turn the chicken and continue cooking for 20 min. While the chicken bakes, chop onion. Saute' onion in a small skillet with a little olive oil. Chop mushrooms and add them to the onion. Saute' until t...

To make a paper gift box is one of the simplest projects that you can create on your own. In order to do this you need some materials: a Square of Paper, a Pencil, a Ruler & a Folding Bone. Take any size square of paper and draw two lines diagonally from corner to corner. This will form a large X, marking the center of the square. In turn, fold each corner into the center of the square. Firmly crease the fold. Fold the first corner to the line of the first fold made on the opposite side. Repe...

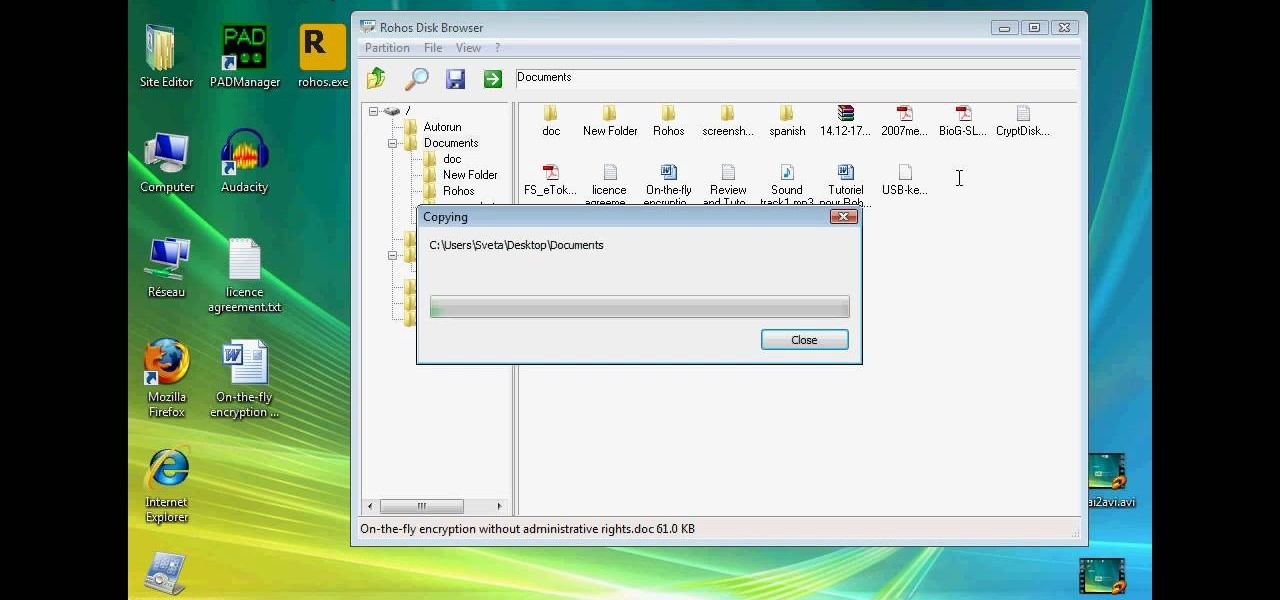
This technical video will show you all about the Rohos Mini Drive. See how you may work with an encrypted partition on a PC without admin rights using this free portable encryption solution. It securely protects your portable data on any USB device. Portable utility Rohos Disk Browser gives you opportunity to work with your sensitive data on a USB drive in the usual way on any PC (even at an internet cafe, where you don’t have admin rights).

Your sewing machine needs bobbin thread to create overlock stitches, so keep your machine going by learning to fill your bobbin.

Why justify the cost of buying a corsage from your local florist? Make an affordable corsage yourself that reflects your personal style.

Motorcycle fatalities are on the rise. Make sure you're doing all you can to protect yourself. Practice good motorcycle safety.

Spray the Styrofoam ball with a color that adheres to the scheme of the ribbon and ornaments. There will be white space when you make a Christmas ornament tree, and the color on the ball will help to conceal the space.

Stop guessing if you need to take your RV into a service center, answers are here in this tutorial video. Learn how to maintain the water heater on your RV.

When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier.

Want to securely delete information from a Microsoft Windows XP desktop PC or laptop? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Have some files you don’t want anyone to see? Or maybe it’s just been a while since you’ve emptied your trash bin. The trash bin function is not a permanent delete but you can erase files off your Mac with this tutorial.

This Scooby's Workshop video shows proper form of the incline dumbbell fly exercise for pecs. Fly type exercises have done far more for my pec development than the pushing type exercises. In doing flys, make sure that your arms do NOT go behind the plane of your body as this puts too much stress on the shoulder joint. If you don't have a incline bench, you can make one as I have done here by tying a 2x8 securely to a coffee table. This exercise is best done with a spotter for safety, if you m...

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Do you need to lock the door but don't have the keys? This may happen if you are sharing your keys with someone else, staying at a friend's house, or for a variety of other reasons. Check out this video for a sneaky way to secure that door tight without even sticking a key in the lock.

BD Quikheel Safety Lancet The BD Quikheel Lancet is a safety-engineered product designed for heel sticks on infants and premature babies. It features a sweeping surgical blade that permanently retracts after creating an incision. Additionally, it offers a tapered window providing the healthcare worker with the ability to accurately position the lancet.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

There may be many third-party file managers for Android to choose from, but until now, Google offered no proprietary option. Enter 'Files Go,' which, while initially anticipated for December, is now available for you to try.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...