
How To: Make a Killer Bottle Opener from a .50 Caliber Bullet
In this article, I'll show you how you can make your very own bullet/shell bottle opener. All you need is a .50 caliber deactivated round and some workshop tools!


In this article, I'll show you how you can make your very own bullet/shell bottle opener. All you need is a .50 caliber deactivated round and some workshop tools!

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

In photography, using filters over lenses is a common practice and provides a great way to set the mood or to create an artistic image. The only problem is that they can be quite costly and there currently aren't many available for cell phones specifially. Fortunately, there is a simple solution to this, and all you need are everyday objects that can be found around the house. If you're a purist and don't want to rely on filters provided by camera apps, this is a great way to experiment with ...

The holidays are here and all of us here at Phone Snap hope you're spending them under a nice warm roof with some yummy food and great company! For this week's Phone Snap challenge, we want you to utilize your cell phone to capture some holiday spirit. Whether it be the gifts under the tree, stockings hanging over the fireplace, Christmas lights outside, or everybody gathered together wearing their favorite holiday sweaters—we'd love for you to share with us!

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

I've previously mentioned how saving browser passwords is a bad idea, but I never went into much detail as to why. Passwords that are saved in your browser can be carved out and stolen very easily. In fact, even passwords you save for instant messaging and Wi-Fi are vulnerable. Windows is very inefficient with the way it stores passwords—it doesn't store them in key-vaults, nor does it encrypt them. You're left with passwords residing in memory and filespace that's unencrypted.

Now we're getting to the kids who actually know what's going on. You're more likely to get enthusiasm and dare I say focus from grade school and middle school kids. Here's the lowdown:

You're sitting in your favorite café enjoying a hot cup of joe, then you open up your laptop or turn on your tablet computer to get to work, but as always you get sidetracked and head straight for Facebook. Someone just tagged you in a photo, so you check it out, then you see it out of the corner of your eye—your Facebook picture digitally displayed on the wall in a nice, neat digital photo frame.

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...

Designer Andrew Clifford Capener has made an alternative to the classic Scrabble board that celebrates the expression of typeface. It isn't in production yet, but Capener's set would offer tiles in a variety of different fonts:

Health, safety and security are three main issues which determine if your cruise is a successful vacation.

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

Willow Smith has what it takes to be a star, just like her parents, Will and Jada Smith, and her brother, Jaden Smith. But this Smith, at the tender age of 9, is quickly becoming a pop superstar and preteen trendsetter, thanks to her music video "Whip My Hair".

Would you rather live far up in the trees? Or deep underwater? A Nevada family of scuba divers have built the ultimate childhood getaway: the Needham family's "Bubble Room" is an underwater fort that sits at the bottom of a lake in the Sierras. The room is an air-filled pocket, made with vinyl and anchored down by an octagonal framework of metal pipe.

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

It's no secret that Jimmy Kimmel is a SCRABBLE man. He hosted and won the SCRABBLE 60th Anniversary Celebrity Doubles Tournament (SCRABBLE Under the Stars), and for the last couple of years, featured the National School SCRABBLE Champs on his late night show "Jimmy Kimmel Live!".

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a mouse.

Fishtail braids can be a little tricky, but the look is worth the effort. Divide the hair into two sections. In order for the hairstyle to look neat from the

The seated hammer curl using resistance bands is used to target primarily the biceps, however because the wrist remains perpendicular to the ground rather than parallel, the forearm also gets a workout.

The seated row with resistance tubing is a great back exercise. The largest muscle in the back is scientifically known as the latissimus dorsi. You might see it referred to as the "lats" or "wings." The lats are used any time you pull something. For example, when you open a fridge or a car door, you are primarily using your lat muscles.

This exercise is a convenient alternative to the traditional barbell row. The main target is the upper back, or scientifically, the latissimus dorsi. The "lat" muscles function to pull things. So whenever you open a door, your lat muscles are allowing the movement to take place.

If you are ready to take your ab workouts to the next level, this exercise is for you! The plate crunch can be used as a progression to the traditional workout ball crunch. The range of motion is virtually the same. However, a bar plate is placed behind the head to increase difficulty.

The seated chest press can be done from any chair with a seat back. This exercise is great for shaping and strengthening the chest muscles. The chest is scientifically named the pectoralis. This muscle is used any time you push a chair up to the table, shut a car door, or push a shopping cart. There are two muscles that make up the pectoralis. They are the pectoralis major and minor. The pectoralis major is always the prime mover during chest exercises.

The use of heavy duty resistance bands (also referred to as "Powerlifting Bands") as a strength training aid has become increasingly popular over recent years. The bands are used for accommodating resistance; a technique that involves creating maximal tension throughout a full range of motion.

The seated leg extension is used to isolate the quadriceps muscles. The quadriceps muscles are located on the front of the thighs. As you might have guessed, there are four muscles that make up the quadriceps. Each muscle works in unison to extend the knee. In everyday life, the "quads" are used when you jump, walk, sit, kick, or stand.

If you are trying to work the hips and butt, this exercise is for you! The side kick mainly targets the gluteus muscles. Any movement away from the center of the body is known as "abduction."

The outer thigh lift is a great way to work the butt. Whenever leg abduction (movement away from the midline of the body) takes place, the gluteus muscles are involved. Instructions for the outer thigh lift are as follows:

The use of chains as a strength training aid has become increasingly popular over recent years. Chains are used for accommodating resistance; a technique that involves creating maximal tension throughout a full range of motion.

The rush to secure face masks and hand sanitizers in March left many Americans concerned for their safety. With an expected second wave this fall, consider stocking up on PPE now.

The race to the driverless finish line just got more challenging as Apple seems to have joined the pack. Friday, the global superpower secured a permit from the California Department of Motor Vehicles that allows them to test autonomous cars in the state.

Encryption is on everyone's mind these days, from the FBI's battles in court with Apple to WhatsApp's recent announcement of end-to-end encryption for their one billion users. Now you can add Signal, whistleblower Edward Snowden's favorite messaging app, back to that whirlwind discussion. Created by Open Whisper Systems, Signal is an encrypted messenger app that allows you to send text, images, video, and audio messages without the fear of prying eyes. They already have an Android and iOS app...
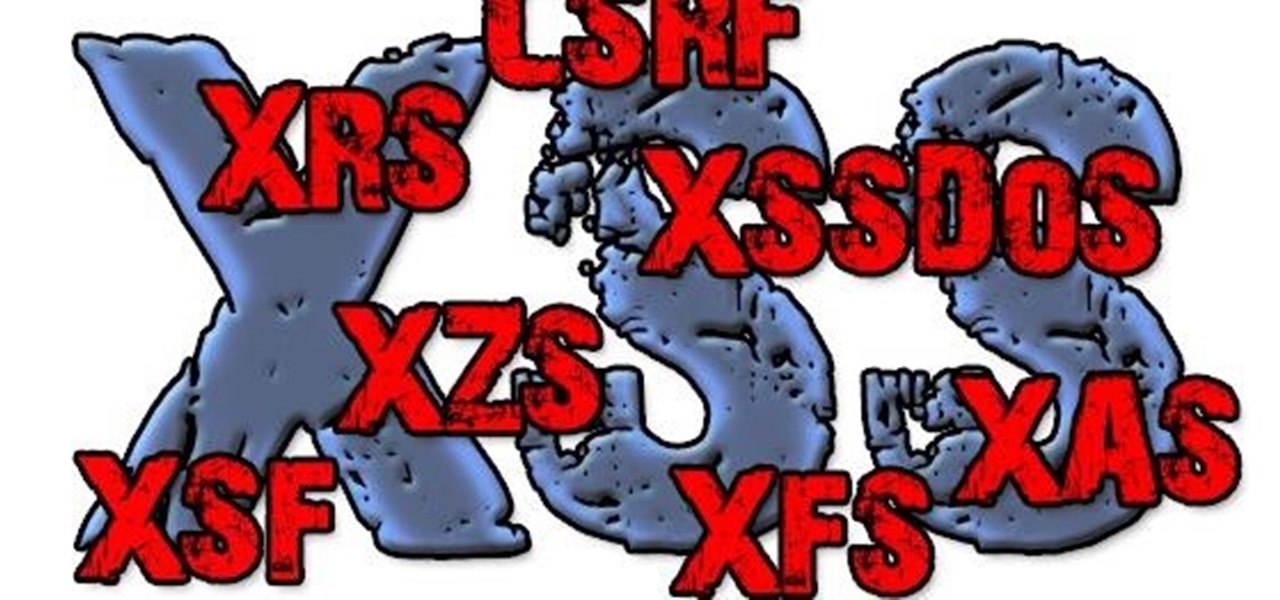
BeEF is an XSS-exploiting framework that lets you "hook" or gain control of victim web browsers. In this part of XSS exploitation, we will be working on finding an XSS-vulnerable website. We can simply do this by Google Dorking.
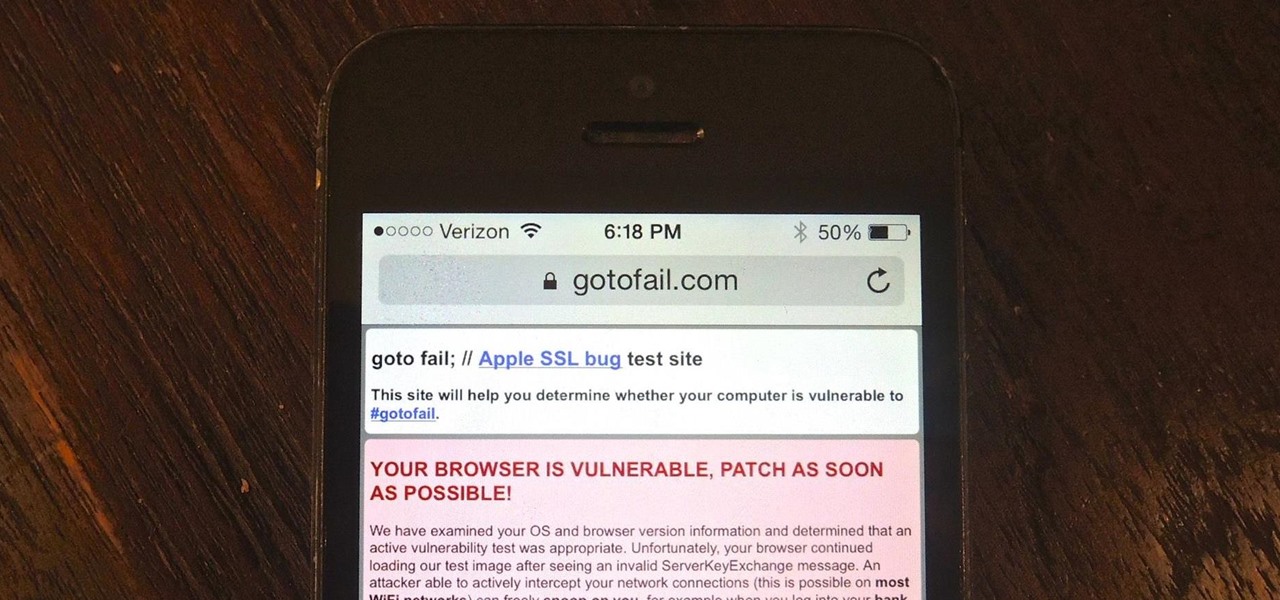
Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions.
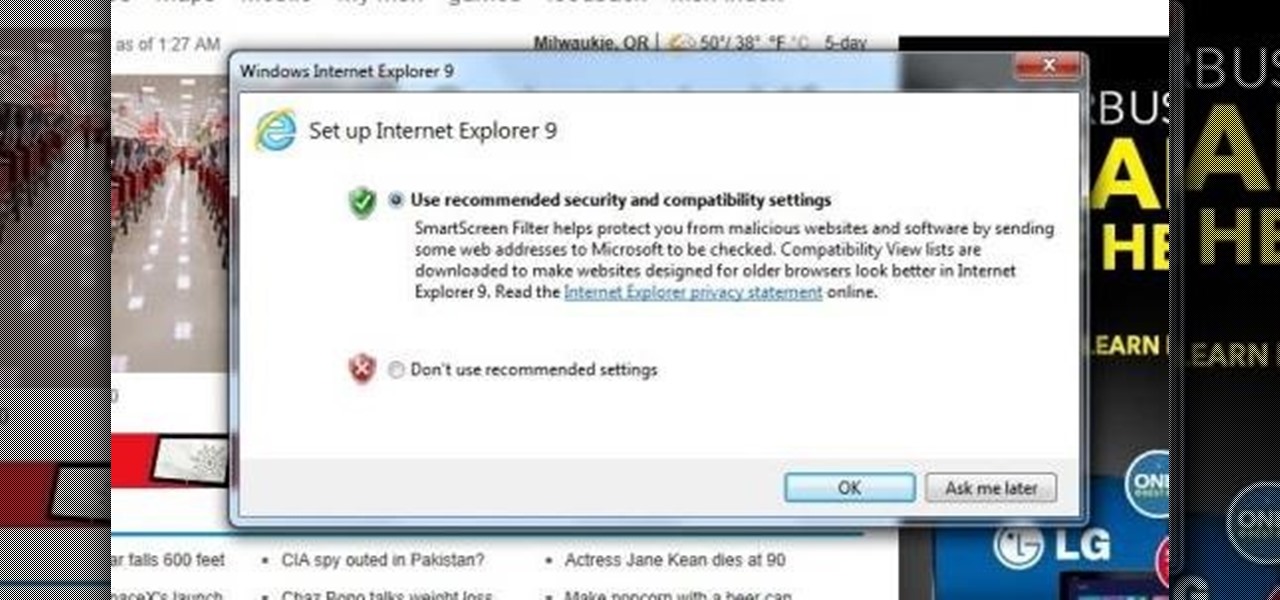
After you've updated Windows 7. Internet Explorer 9 is automatically installed. This is just a two step process of knowing it's been upgraded, and is ready to run and get you on the web.

When downloading any application on an Android device, you will always be prompted by the following... Whether it's Angry Birds, Shazaam, or Chrome, every application will ask for permissions. If you try and deny these permissions, it won't install, leaving you with no other option but to accept. So what can you do?

Along with the release of the new iPhone 5, Apple has introduced EarPods, which now replace the soon-to-be-defunct EarBuds. For three years, Apple has been testing the EarPods with users to try and find the most secure fitting, best sounding headphones for that price range. Loose Fit?
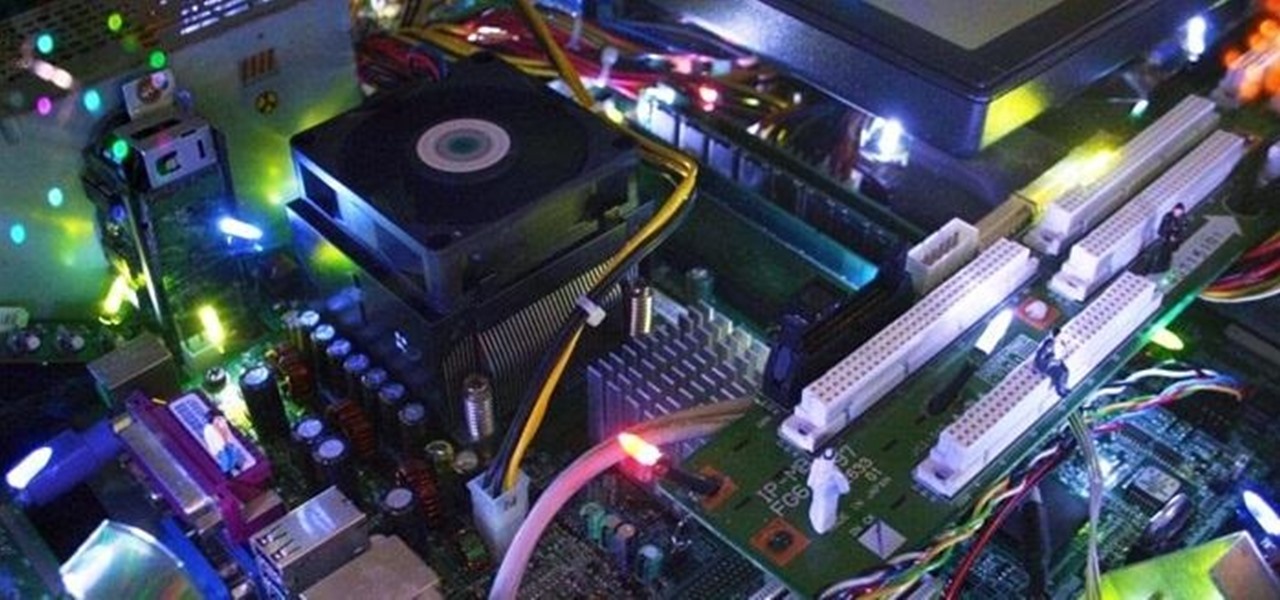
I have an interest in using recycled materials in sculptures, particularly circuit boards and other wasted electronic and mechanical components with which I put together sprawling cities lit with fairy lights. These cityscapes can conjure an image of a parallel society built from what we throw away. Utopian or dystopian, the ‘Electri-Cities’ remain a feast for the eyes and the mind. What makes them particularly intriguing is the population of tiny model railway people—they bring a host of nev...

Rain can make for an amazing photograph, but it can do disastrous things to your equipment. This super simple DIY cover from Purple Summit Photography will keep out the rain so you can capture beautiful shots no matter the weather, and it's made using things you probably have lying around. Photo by Jon Shave

Hotly contested video. The question remains, is the science behind the potato fire bonafide or bogus? We have yet to try it over here at WonderHowTo, and the comments thus far haven't indicated a solid verdict. Try it out and let us know! Is this a hoax? Or can you truly start a fire with a potato, salt and toothpaste?

Get out of your everyday ponytail rut and try something new. Here our hair expert shows you how to do a sleek, chic ponytail that is perfect for a night out. Texture