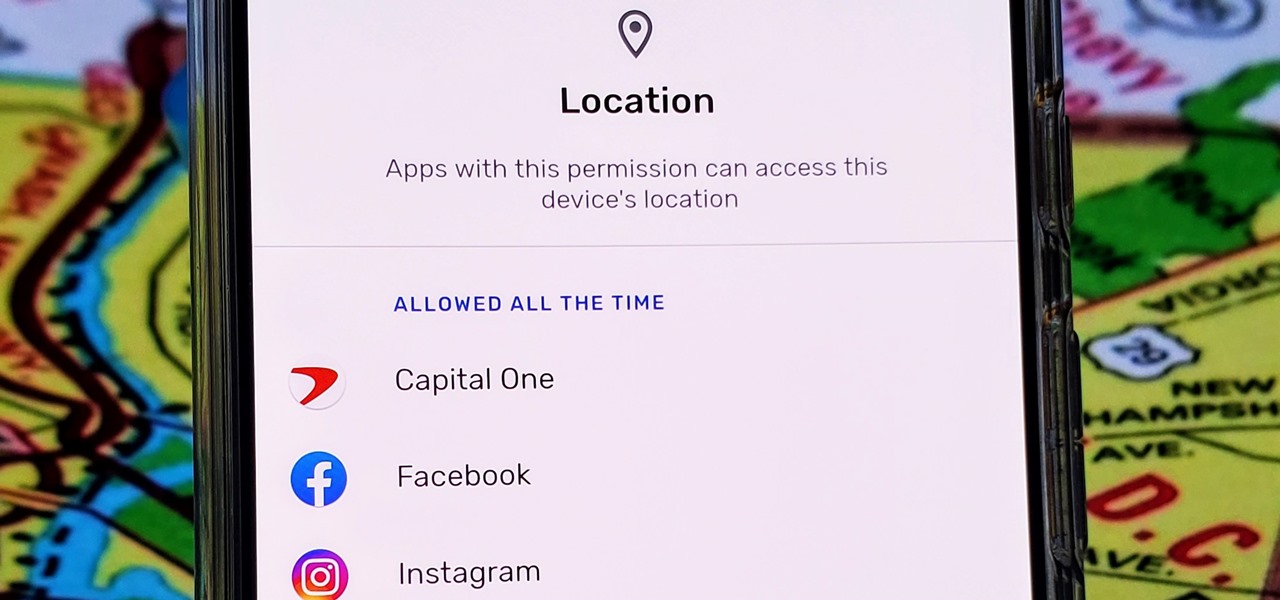
With Android 10, there are now three options when an app asks to access your location: Allow, Deny, and Allow While In Use. That last one prevents apps from seeing your location unless you're actively using them, and it's the default now. But when you first update, most of your apps will still be allowed to access your location in the background — at least, until you do something about it.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.
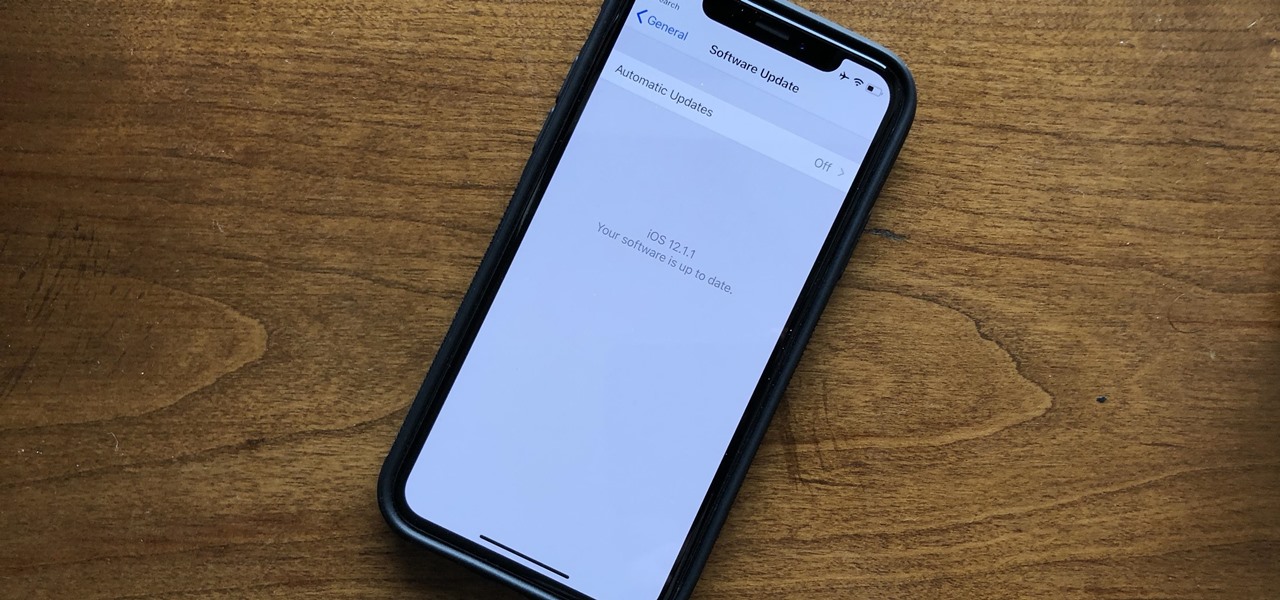
Apple released the latest update for iPhones, iOS 12.1.1, on Wednesday, Dec. 5. It introduces a few new features to iOS 12 as a whole. The software has been in beta testing since Halloween of this year, spending just over one month in the hands of beta testers.
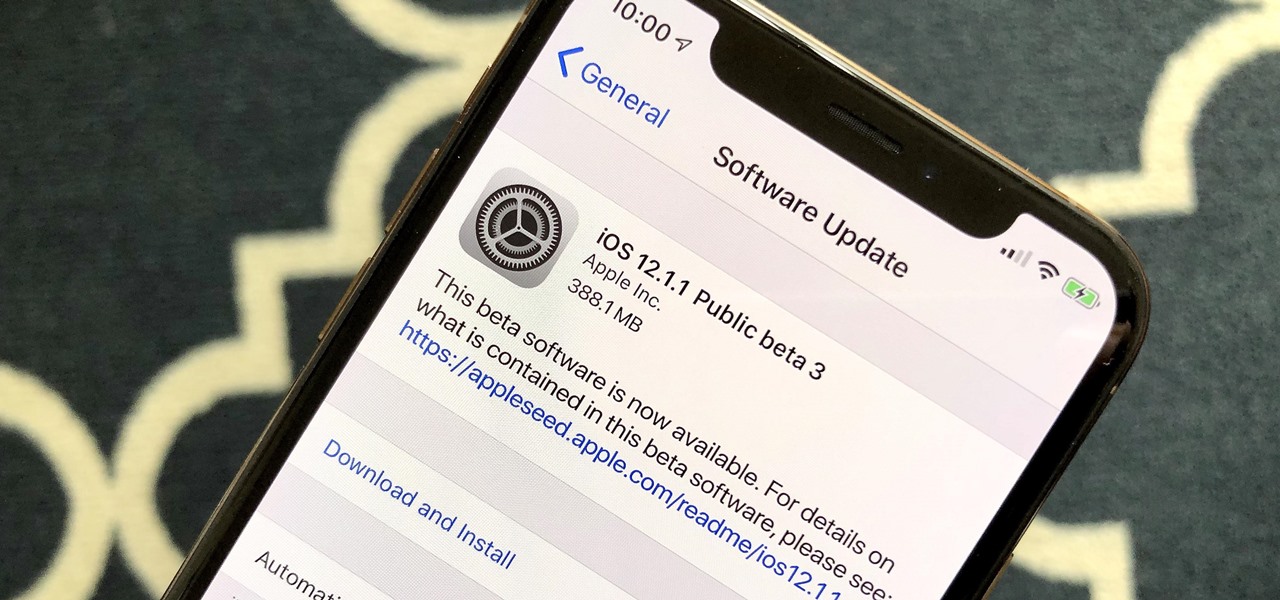
It seems Apple will keep with recent tradition — the third iOS 12.1.1 public beta released to software testers Thursday, Nov. 15, just hours after the 10 a.m. PDT (1 p.m. EDT) release of dev beta 3. Apple likes to take a short time after a developer release to ensure the beta is good enough to release as a whole, as seen with the entire iOS 12 dev beta 7 debacle.
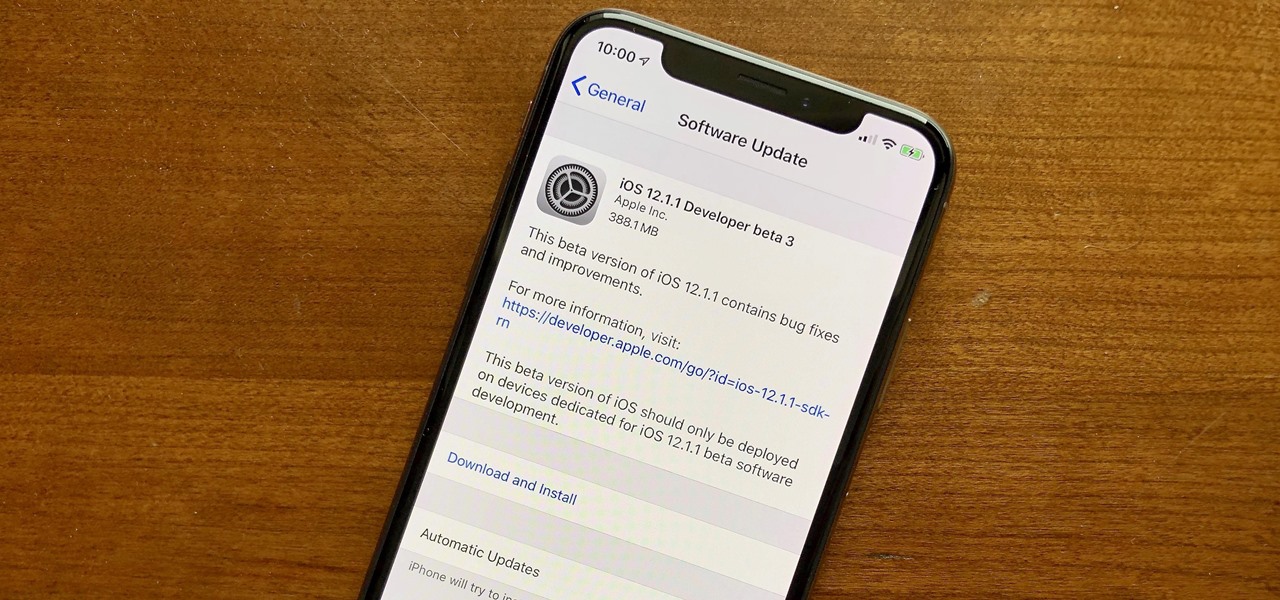
Apple released the third beta for iOS 12.1.1 on Thursday, Nov. 15. This update is not much of a surprise, as it comes just a little over one week after the release of dev beta 2. As with that beta, we expect Apple to release the 12.1.1 public beta shortly, possibly as soon as this afternoon.
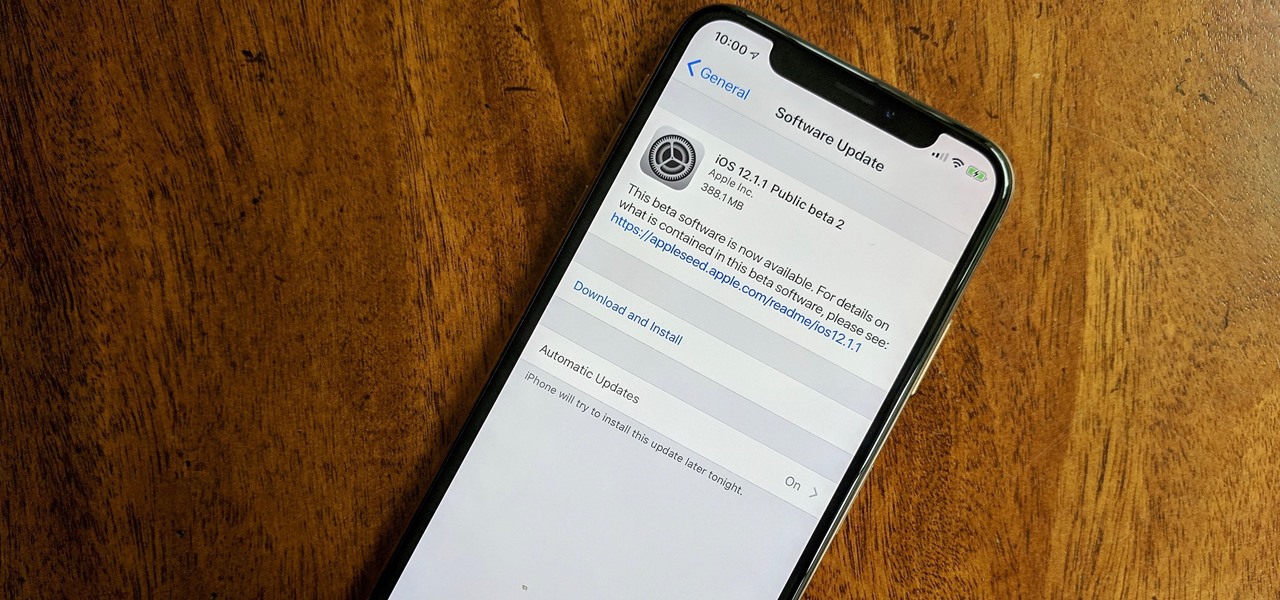
Registered iOS developers received their first taste of 12.1.1 dev beta 2 on Wednesday, Nov. 7, and public beta testers received the iOS 12.1.1 public beta 2 shortly thereafter.

Developers opened their iPhones on Wednesday, Nov. 7, to find an update to the iOS 12.1.1 beta. Apple seeded developers the first 12.1.1 beta on Halloween, marking one week between it and the second beta. It's a quick update turnaround but in line with trends as Apple typically waits at least a week in between beta releases.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Flying under the radar during Magic Leap's big week at the Game Developers Conference, the company settled a potentially ugly lawsuit with a former employee.

It's often the smallest details that determine your overall experience with a smartphone. Unlocking your device with a PIN is an example — and iPhones have had a leg up over Android thanks to their automatic unlocking. Thankfully, this era has finally come to an end with the arrival of the Galaxy S9.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

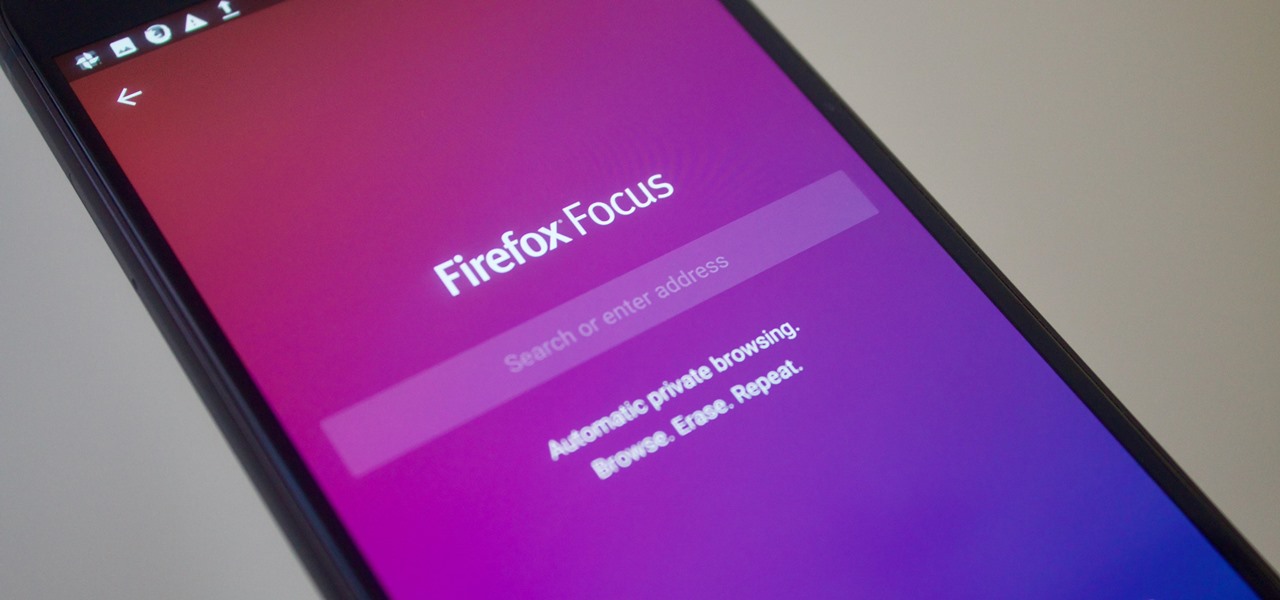
Firefox Focus is Mozilla's effort to make your internet experience a little more secure. Originally released in November 2016 for iOS, Focus blocks internet trackers, search history, anything that gets in the way of a clean, private browsing experience.

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

As we get closer to the release of the iPhone 7 this September, more and more details are emerging about the features the new smartphone could have. The well-regarded analyst Ming Chi-Kuo of KGI Securities, who has an uncanny ability to predict new Apple features, has reported another detail involving a dual-lens camera on the upcoming iPhone 7 Plus model.

Once you connect all of your devices to your Wi-Fi router at home, you'll never need that long, complicated Wi-Fi password ever again, right?

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Welcome back, my rookie hackers!

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

In addition to the fingerprint scanner, the Samsung Galaxy S6 has all of the basic lock screen options that other Android phones have: swipe, pattern, PIN, and password. There also just happens to be a secret sixth option called "Direction lock" that protects the device with a series of customizable directional swipes—only it's hidden in an unsuspecting settings menu.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

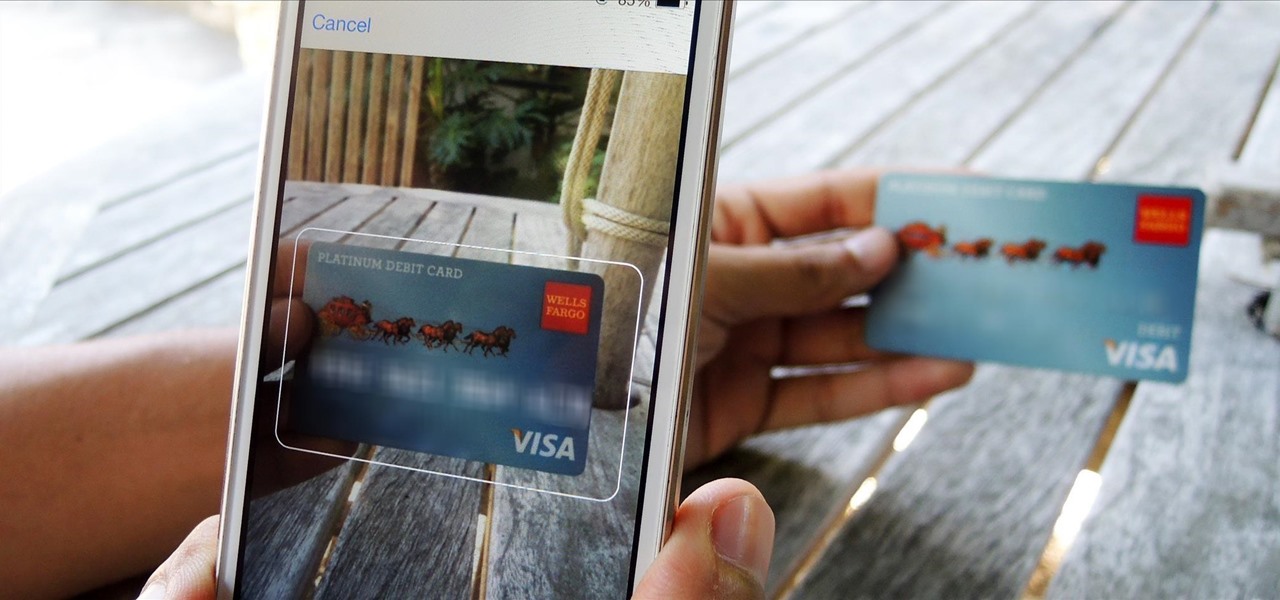
There's a feature that debuted in iOS 7 that lets you to save your credit or debit card information in Safari so that you can auto-fill text boxes when purchasing something online. Unfortunately, you still had to manually fill in your card info the first time, and if you wanted to disable the feature for security concerns, it was entirely useless.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

Update: June 2nd, 2014 Over the weekend, someone snuck in to Apple's presentation dry run, and grabbed a quick video of the new iPhone will look like.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

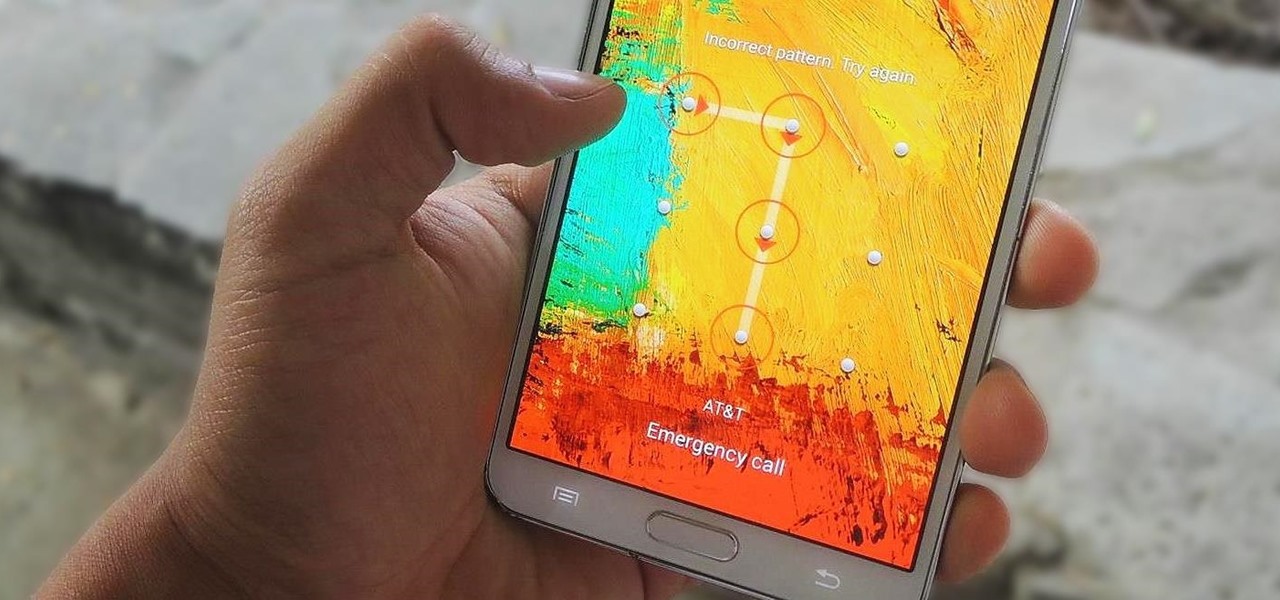
Lock screen security provides a means of safety when it comes to keeping others from breaking into our smartphones and snooping around on or stealing private information like documents, emails, photos, and videos.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

February may be the shortest month of the year, but for iOS softModders, there were plenty of apps and tweaks to fill up those days. Whether patching major security holes or just a tweak to make speed dialing more efficient, there was a plethora of great mods for our jailbroken iOS 7 devices. These are our favorites from the month.

There are countless mods and apps for Android devices that give them an iOS-style look, but maybe it's about time we take some notes from Android, especially when it comes to the iOS 7 lock screen.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"