When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.
Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to pick a Brink's high security lock.

Have you ever been the victim of theft? It sucks. Why would these lazy scumbags rather steal from us than work hard like everybody else?

Video tutorial showing how to make your own solar-powered wireless security camera using an off-the-shelf solar panel and any wireless webcam. See creator site for more detailed graphics.
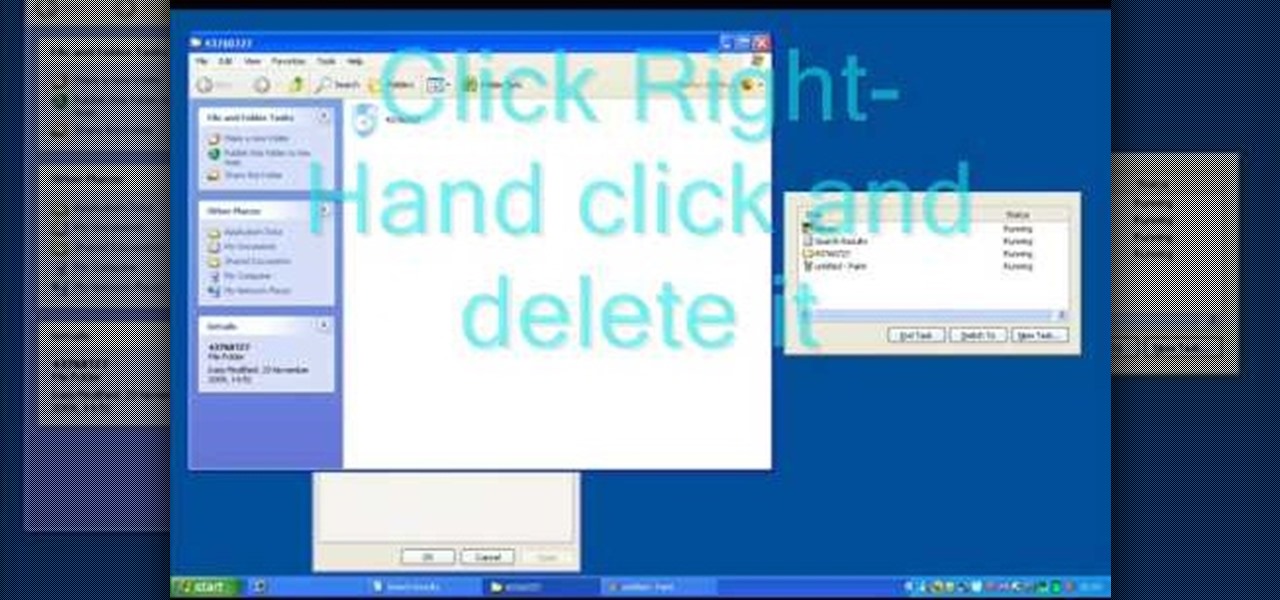
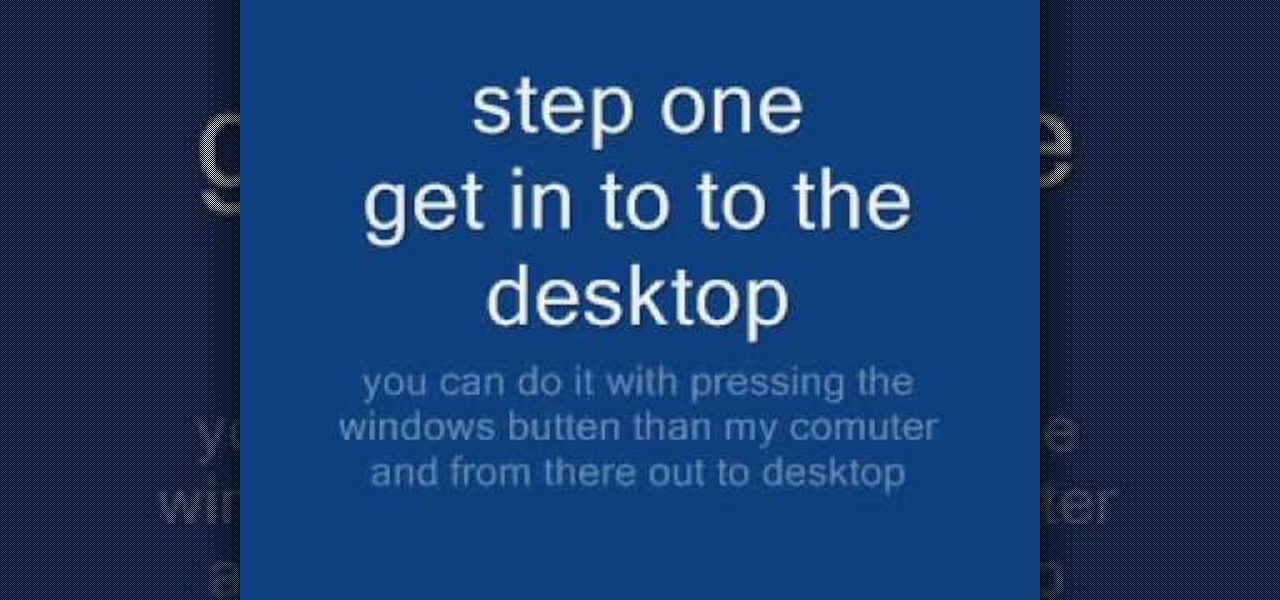
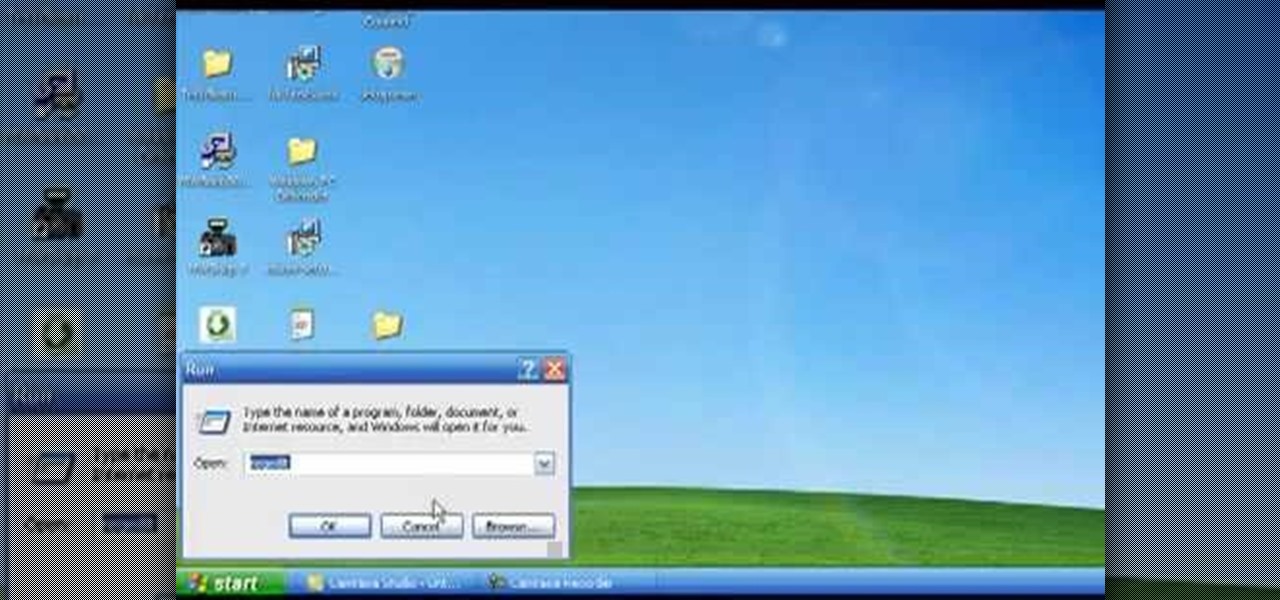
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

If you own the Galaxy S8, S8+, or Note 5, be on the lookout for a new security update. These Samsung devices are the latest to receive the December security update to patch issues from both Samsung and Android.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

Today is the day before Thanksgiving. It's also the BIGGEST travel day in North America. Everyone is taking flights home to their family and friends for a nice Thanksgiving dinner. But this holiday will be one to remember thanks to the TSA.

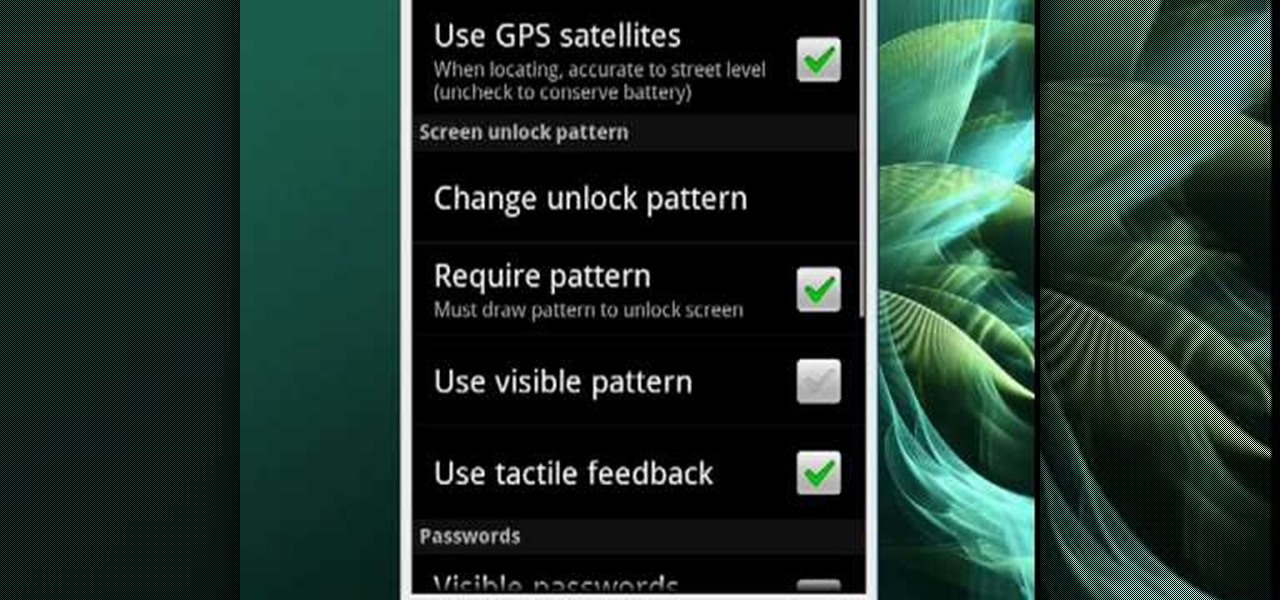
In this video tutorial, viewers learn how to change the lock pattern on an Android phone. The lock pattern allows minimum security on the phone to prevent other people from tampering with your mobile files. Begin by going into the Settings and click on Location & security. Under Screen unlock pattern, select Change unlock pattern. In order to change the unlock pattern, users will have to type in the current unlock pattern. Now type in the new unlock pattern and press Continue. Then retype the...

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Watch this video tutorial, and learn how to turn an ordinary inexpensive webcam into a hidden home security system, viewable anywhere in the world from your cell phone! With a cute and cuddly teddy bear and a cheap webcam, you can make the perfect homemade security camera, or just a camera to spy on your sister and her friends during sleepovers. Follow along with the steps in this how-to video and learn how to set up this spy system. Note: this video is NOT recommended for people who are perv...

By DevonLocks.Com - Security pins can be a pain. This video shows you how to bypass them. See our other video on how to spot them.

Samsung just began rolling out the Oreo Beta 2 to registered users of the Galaxy S8 and S8+. The update's changelog promises the inclusion of the October 2017 security patch. Unfortunately, after downloading the update, we've noticed this is not the case. Omission of the more recent security patch is notable in that it leaves devices vulnerable to several known exploits, such as KRACK.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

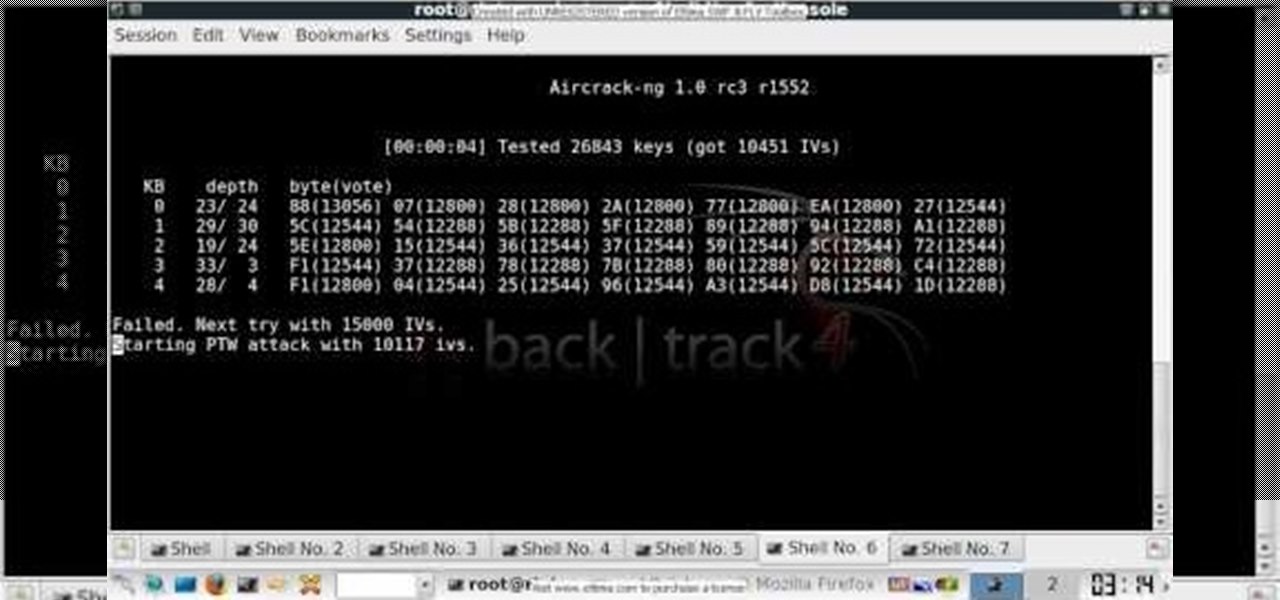
In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Wish there were a way to turn your webcam into a bonafide security camera? Well, there is! And it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over two minutes. For more information, including step-by-step instructions, take a look.

Need some help figuring out how to disable potentially annoying popup security notifications in Microsoft Windows 7? This video tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

In this Microsoft Windows 7 users guide, you'll learn how to take advantage of the operating system's new Applocker security feature. It's easy! So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in about a minute and a half. For more information, including complete, step-by-step instructions, take a look.

In this how-to video you'll learn all the tricks and tips to getting yourself through airport security quickly and easily, even if you have electronic gadgets. Some companies produce travel gear that the TSA will let pass through without having to remove your laptop or electronics. Timesaver! Watch this video and you'll soon be cruising through the "Expert Traveller" line.

It seems that almost every multiplayer map in Gears of War 2 has a secret glitch-based way of getting underneath it. This video is a tutorial on how to do just one of these glitches. It will show you how to get under the Security multiplayer map using a barrier breaker glitch.

In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

In this video you will learn how to Get ESET Nod32 or Smart Security forever. First make sure you have the trial for ESET Nod32or Smart Security. To do this go into the description of the video, download that file and put in the trial username and password. The downloaded file its called ESET Box4Ever.Before you extract the file open your ESET window and press F5.Uncheck self defense and restart computer. After you restarted the computer extract the files from ESET Box4Ever and run the file, ...

Enchiladas are a Mexican staple that can be made with chicken, beef, or cheese. This easy recipe makes a tasty and satisfying meal.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.

Got a mystery to solve? Somebody’s been making off with your stuff, and you don’t have a clue who it is, do you? Here’s your chance to catch them in the act. In this how to video you will learn to make a DIY laser security system.

Learn how you can protect your home in a pretty radical and fun way by transforming two cheap household items into a stealth hi-tech, anti-burglar, security system! Literally to hot for any bad guy to handle!

This is a Google Tech Talk from March, 26 2008. Timothee Cour - Research Scientist lectures. Movies and TV are a rich source of highly diverse and complex video of people, objects, actions and locales "in the wild". Harvesting automatically labeled sequences of actions from video would enable creation of large-scale and highly-varied datasets. To enable such collection, we focus on the task of recovering scene structure in movies and TV series for object/person tracking and action retrieval. ...

In this video you will see how to access network security cameras through google search engine easily!

In this video, we learn how to remove Security Tool the simple way. Most ways will not remove this from your computer, but this way will. To start, you will need to restart your computer. After this, press ctrl+alt+del the moment Windows shows up. Then, go to the Task Manager and look through the programs that are open. When your security tool opens, press the same buttons to get the mouse free. Then close the security tool from the Task Manager. Now, go to your desktop and press on the icon ...

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.