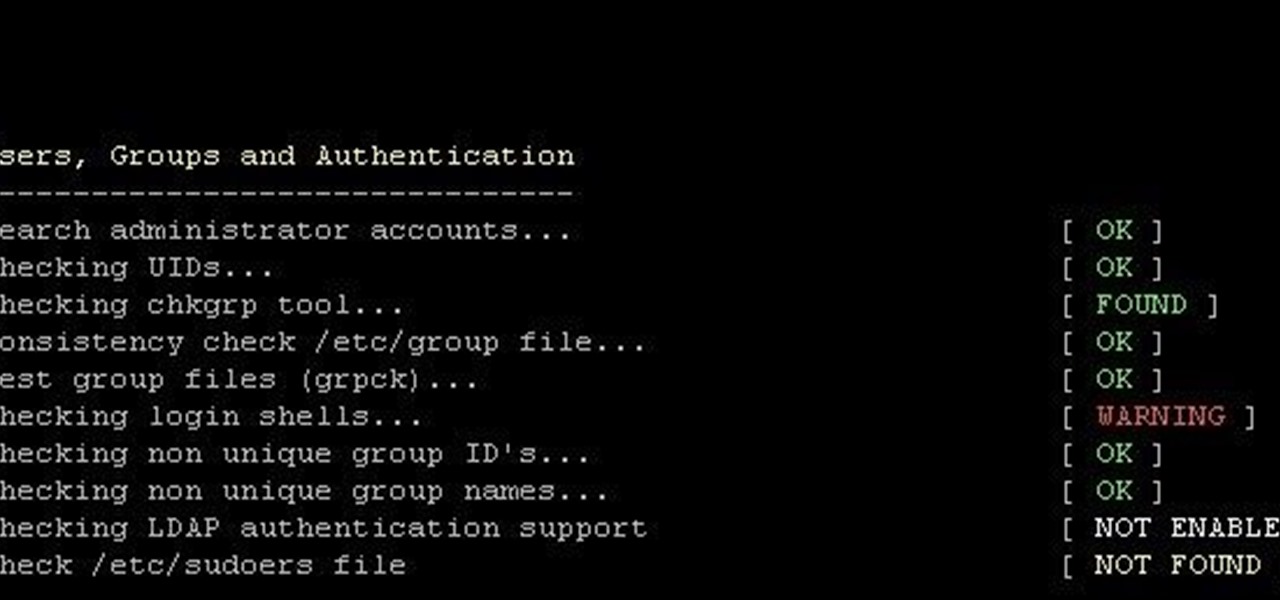
How To: Find Your Computer's Vulnerability Using Lynis
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started


This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Locking up your iPhone with a passcode prevents mischievous friends from looking at your pics and emails, and makes it harder for thieves to access your data before you get around to wiping it. For even more security, there's the password option, which gives you more than just 4 lonely digits.

Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much attention is due to several, well-known features like Google Talk, Project Butter and expandable notifications.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Tired of always having to ask tall folks to help you get stuff down from the top shelf? In this tutorial from Make Magazine, Kipkay teaches you how to build your own stilts. But while these stilts will make you taller, we don't suggest wearing them on the basketball court.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

For many people the home treadmill is a daily ritual of taking care of the body, and that's great. Why not take care of the treadmill just as well? Watch this video to learn how to lubricate your treadmill belt and how much that can improve the performance of your treadmill.

Turn those boring blue jeans and that drab white shirt into a fashionable ensemble with a few accessories. Watch and learn how to spice up your outfit with layered shirts, belts, fashion scarves and boots. There's nothing to giving an outfit a little more zest.

Comfortable doesn't have to mean frumpy. Learn how to make the most of your go-to jeans, T-shirts, and belts by watching this video.

Need a last-minute costume for Halloween or a party? Well yee-haw, pard'ner, you can slap together a cowboy outfit in no time. Watch this how-to video to learn how put a cowboy costume with items you have around the house. All you need for your costume is: jeans, flannel shirt, cowboy boots, belt with buckle, bandana, cowboy hat, and a few other things.

If you're too shy to get up in front of strangers and belt out your best version of Hit Me Baby One More Time, then you can always share the moment with some close friends at home. Get ready to rock and roll, karaoke style.

Grab a strap, necktie or belt to do this shoulder stretch. Remember your Ujjayi breathing and be sexy.

Eric Arceneaux shows you how to belt those vocals and get rid of your nasal sound for singing better.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.
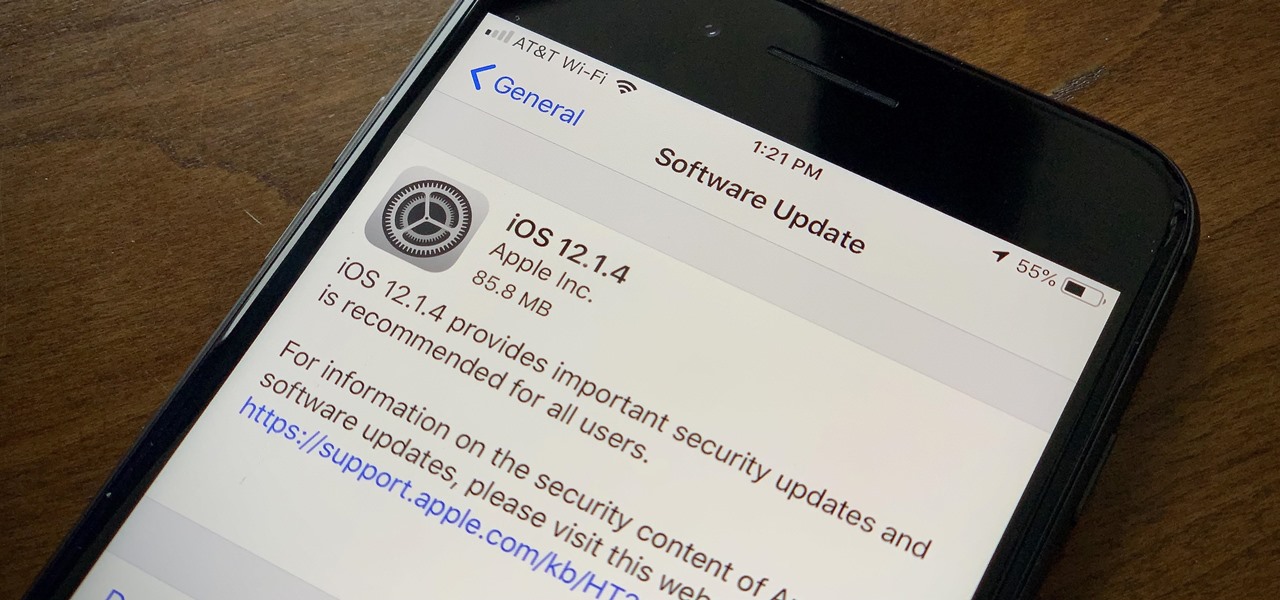
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.
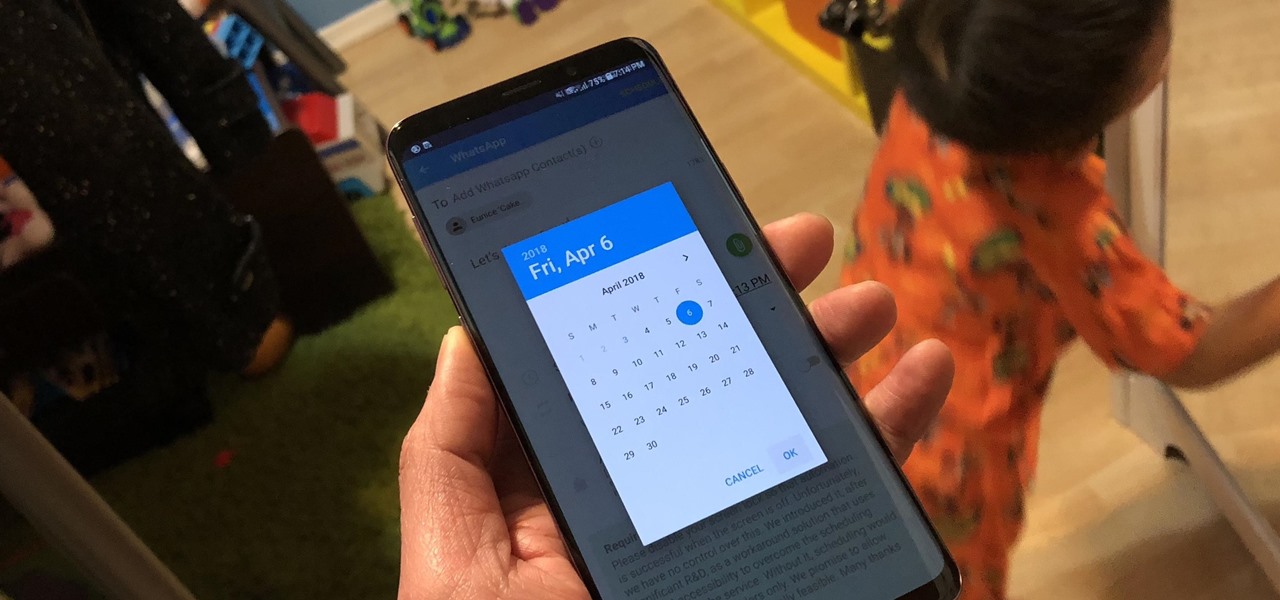
Great ideas often strike at random times, but messaging friends and loved ones at an inopportune hour not only risks their wrath, but also increases the chances of your message not being paid proper attention to. Thankfully, there's an app that lets you create and post WhatsApp messages at the time you wish for maximum effect.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

Locking individual apps on your Android device gives you an added layer of security by safeguarding app data from unwanted attention. I personally prefer using an app locker over a standard lock screen because my kids play with my phone, and they've completely disabled it after inputting the wrong PIN. So app lockers give me the right balance between giving my children access to my device, and the security of locking down my data from would-be intruders.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

This Tutorial shows how to make an easy wavy macrame bracelets. For the most interesting appearance you can also add beads. With this style you can also make a belt, just take bigger cords and make it longer :)

How to make a Nice Macrame bracelet with rhombus and small beads. (Video Tutorial) In this style you can even make a belt.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

How to Braid with SEVEN strands - DOUBLE BRAID Tutorial. This braid can be used for making hairdo, belt, bracelet, etc..

Square knot variations with eight strings. This is easy to make and looks good. You only need to know a square knot. With this macrame pattern you can make: belt, band, bracelet, strap for guitar or bag

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

So this is a great beginner's knot. This Square Knot pattern is made by switching the fillers and working cords. I recommend you use two colors to get the best results. It's important to leave enough space between the knots so you can see the crisscrossed cords clearly. This knot can be used to make a simple belt or other items can also be made with this knot.

Reversed Half Hitches, Larks Head Sennits or chains (can be made in several different ways) They can be used as bracelets, belts, or just for decoration. Very easy to make, can be used as a Survival bracelet or Friendship bracelet. Good for beginners :)

in this Zipper bracelet is used Half Hitch knot or oldest name - Basket Stitch. They can be used as part of plant hangers, or to make belts, bracelets, and other items. This is very easy to make (: can be used as a friendship bracelet and good for beginners :)