When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.
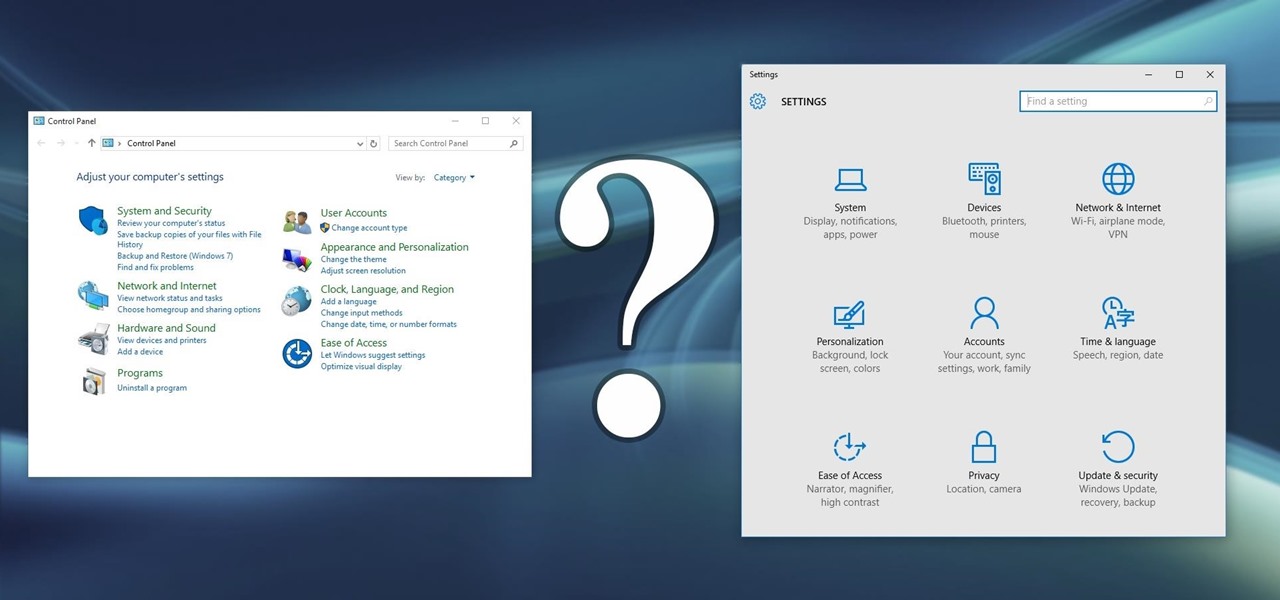
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

The Galaxy S6 Edge comes with a useful feature called Information stream that allows you to view quick tidbits of info with a quick back-and-forth swipe on the edge of your display while the screen is off. Apparently, Samsung left the door open for third-party plugins to use this feature, and now we're starting to see an influx of useful additions.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

Aside from being able to change the wallpaper and add shortcuts, the Galaxy S4's lock screen doesn't offer much in the department of personalization. The lock screen is efficient and practical, but it's also a little bland.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.

Do you think that Avril Lavigne has nothing on you when it comes to belting it out on the mic? Then you probably prefer karaoke versions of songs to the real ones so you can hone your vocal chops to your favorite tunes.

In this video we learn how to tie a half Windsor knot. First, bring the tie around your neck and position the small side by your belt. Next, bring the big side over the little side, then bring it underneath the little side. After this, take the big side through the gap on the right side only. Take the big side back over the top of the little side and bring the big side through the gap once again. During this, make a little hole with your right hand and tuck the big side into this hole. Push t...

If there's one thing we learned from high school show choir, it's that trying to scream out songs like your favorite pop artists will eventually ruin your voice and even scar your vocal chords so you'll never be able to sing well again. In fact, lots of famous pop musicians have had to get throat surgery later in life to correct all the damage they did to their vocal chords when they were younger.

In this video tutorial viewers learn how to wear the National Working Uniform. This uniform has a strict policy and all must follow the uniform rules. The basic components of the uniform are: an eight point cap, blue cotton undershirt, shirt, trousers, belt with closed-faced buckle, black boot socks, blousing straps, black 9" steel-toed leather boots, embroider rank insignia and service & name tapes. This video is very detailed and clearly explains all the uniform expectations. This video wil...

High waists and poofy balloon skirts are both two of the hottest fashion trends this season, seen on stars like Lauren Conrad and Jessica Simpson (yes, of the famous "Mom jean" snafu).

With the weather getting colder and colder this winter season, you may need to update your winter clothing with some new, warm sweaters. If the weather is just a little too chilly for your taste, then layer yourself up with this fashion tip. See how to make a lux short-sleeved sweater in this video from GiannyL.

Acid reflux can be painful and irritating, and did you know that toddlers can be affected by it too?

In a tool shed there are two gentlemen discussing how handy a well organized tool shed or tool box is. One man starts to say that he has come up with a easy and in expensive way to keep hand tools organized. Find a old simple nail apron and draw some lines down the pouch. This lines will later turn into places to put tools so it is a good idea to think ahead about what tools you will end up using and adjust the size accordingly. Next, snitch up those lines that you have drawn. Finish up by pu...

Agnes from My BF Closet takes us through a few ways to use your boyfriend's ties to compliment your own wardrobe. A trendy and young look for women, a necktie may be just the right accent and bit of flair for you. Agnes teaches us first, using herself as a model, how to tie and wear the tie in its traditional form, around your neck. Moving on, and with a great sense of humor, she shows us, in a montage, various other uses. As a belt, for instance. And as a headband. With this video, Agnes sho...

Transforming your school uniform to express your individuality can be done very easily with a creative mind. One thing you can do to dress up a pair of pants and a plain tee is to wear different scarfs and belts. Feel free to mix and match. You can even try them with a cute vest or a jacket. Another way that you can mix things up is to change your shoes; you can get a variety of interesting colors or patterns. Also, changing your totes to something cute and different can make you stand out.

Try out this science experiment... watch this video tutorial to learn how to experiment with a Van de Graaff generator. This is purely educational, and demonstrates different techniques in using the Van de Graaff generator.

Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...

Don't fret too much if your watermark is barely noticeable when you're finished with this project - the less obvious it is, the better a job you've done. Watermarkers are present in many types of paper, especially the monetary kind. If you hold up a ten dollar bill you'll see a watermark of Thomas Jefferson's face on the right, proving the bill is real.

Use Microsoft Windows 7? Miss the old Ctrl-Alt-Delete log-in prompt? It's easy to restore. So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete overview of the restoration process in just over a minute's time. For more information, and to get started restoring this useful security feature on your own Windows 7 PC, watch this free video tutorial.

If you move around a lot, you may notice that you can't play the same DVDs from country to country. The world is separated into different regions, and not all movies will play in all places. There are ways around this security measure, however, if you follow this tutorial.

Webcartoonist shows us how to draw cartoon pirates. Begin with crown of the hat (based on Long John Silver from "Treasure Island"). Start with half-moon shape. The pirate carried a parrot on his shoulder. Begin the parrot's comb, eyes, & head about level with the brim of the pirate's hat. Directly under brim of hat, near center, draw pirate's eyes & nose. Beginning from side opposite the parrot, fill in pirate's facial features. Draw pirate's coat. Add pirate's sleeve, with cuffs & ornamentat...

The PhotoshopUniverse team effectively teaches a method of adding a watermark to an image, as a security feature to make it harder to copy or steal. Instructions are simple and easy to follow, using as an example a photo of two girls that one might have in his or her family album. Using Photoshop, the text that will become the watermark is added, rotated and patterned across the entire image. To finalize the watermark, the opacity is edited to a desired value so that it does not interfere wit...

This video shows you how to make a security device out of a door bell. The concept is that most thefts happen when people are away from home. To make sure of this the thief rings the door bell to make sure that nobody is home, if nobody answers then they will break in. A lot of people have dogs and alarm systems which will scare off the thieves, but this alarm system combines both. To make this devise you have to buy a speaker system that connects to your door bell. When the door bell rings i...

Check out this RESIDENT EVIL 5 Chapter 2: Gigante walkthrough from Machinima.com The behemoth from RE4 returns with some new tricks up his sleeve.