Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to session hijack with a pineapple.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to boot Windows from a USB flash key.
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to configure Cisco and iptables firewalls with a utility.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to packet sniff networks with the fundamentals.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to break down IP and TCP header with Wireshark.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn any Windows application into a service.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to organize your desktop with Microsoft Scalable Fabrics.

Instead of pushing, pulling, and cursing, why not fix that door that sticks? You Will Need

Beat the Level 2-3 Boss in Resident Evil 5 via this walkthrough and gameplay. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Check out this video tutorial to see how to construct an alarm system, that's based on the principle of motion detectors, which work by touch. It's very useful to catch unpleasant visitors red-handed. So make sure your chocolate bar never gets snagged again, catch the bandits with a motion detector alarm! Or just keep you kids away from the birthday present closet where peeping is not allowed.

This is a tutorial that shows you how to view and control your computer screen from your iPhone/iPod Touch. But this method is for people who have a jailbroken iPhone/iPod Touch. This works on Edge and Wifi. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

See how to make an X10 wireless security camera into a nice helmet cam on the cheap in this three-part video. All it takes is an X10 camera, ten bucks in parts, and two hours of your time.

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.

Danny Lipford demonstrates how to wear a tool belt to provide easy access to your tools. A tool belt is handy because you can keep your materials like nails and screws, in addition to tools, right at your fingertips. A nail apron is lightweight but can slide down because it has thin strings. To solve this problem, loop the nail apron strings around your belt loop. When you put the string around the hammer holder, loop it around a second time to securely keep the hammer in place. A tool belt t...

This unique craft project adds flare to your wardrobe, and it makes excellent gifts. Our expert, Kristine Mueller, shows you everything you need to know to paint on a leather belt. Learn the paint to use, and how to select the right belt.

In this do-it-yourself video series, learn how to use a belt sander. This power tool allows you to complete large woodworking projects in minutes instead of hours, saving you the back-breaking effort of smoothing out large areas of rough wood by hand. Our expert will give you easy-to-follow shop safety tips, as well as how to care for and maintain your sander, how to operate the trigger system, and what types of wood to use.

In this online video series learn from expert professional mechanic Nathan McCullough who graduated from Nashville Auto-Diesel College with a Grade Point Average of 3.5 and received their craftsmanship award and honor seal. Learn important automotive Serpentine belt topics including: what is a Serpentine belt, locating the Serpentine belt, replacing the Serpentine belt, when to check the Serpentine belt, types of wear to look for, Jacking Screw Tensioner, Serpentine belt removal, checking the...

Put together semi casual outfits for dinner dates

Sadly we are not all size 00 runway models who fit into sample sizes made by designers for the catwalk and for their ateliers. But then again, who wants to be a dull, faceless clothing hanger?

In this how-to video, you will learn how to dry a simple version of Shy Guy from Mario Brothers. You can use a pen or pencil on paper, or even software such as Illustrator or Photoshop. First, start off by making a circle. This will be the face of the character. Draw in the two elongated ovals for the eyes and shade in with black. Next, draw a small black circle for the mouth. Now, draw the hood and robe of the character. The arms and feet are next. Draw the belt and buckle of the character a...

Here is a fun afternoon project that will add a little fare to your dogs wardrobe. Instead of buying your next dog collar, try making one out of an old belt. Some say dogs look like their owners and now they can dress like them too.

Want to mix and scratch like a professional DJ? To be a good DJ you need to understand the concepts of mixing tracks, adding cool effects, and of course you need a good sense of rhythm to line up the beats. This how to video explains how you can set up the American Audio TT-Record Turntable. This is a Belt Drive turntable that can record your vinyl with a press of a button. All you need to do is plug in your memory stick and off you go. This unit does not need to be used as a direct drive sin...

While most iOS updates will only improve the experience on your iPhone, some can cause more havoc than good. If an update unexpectedly breaks or degrades certain functions on your iPhone, you may be able to roll it back to the previous software.

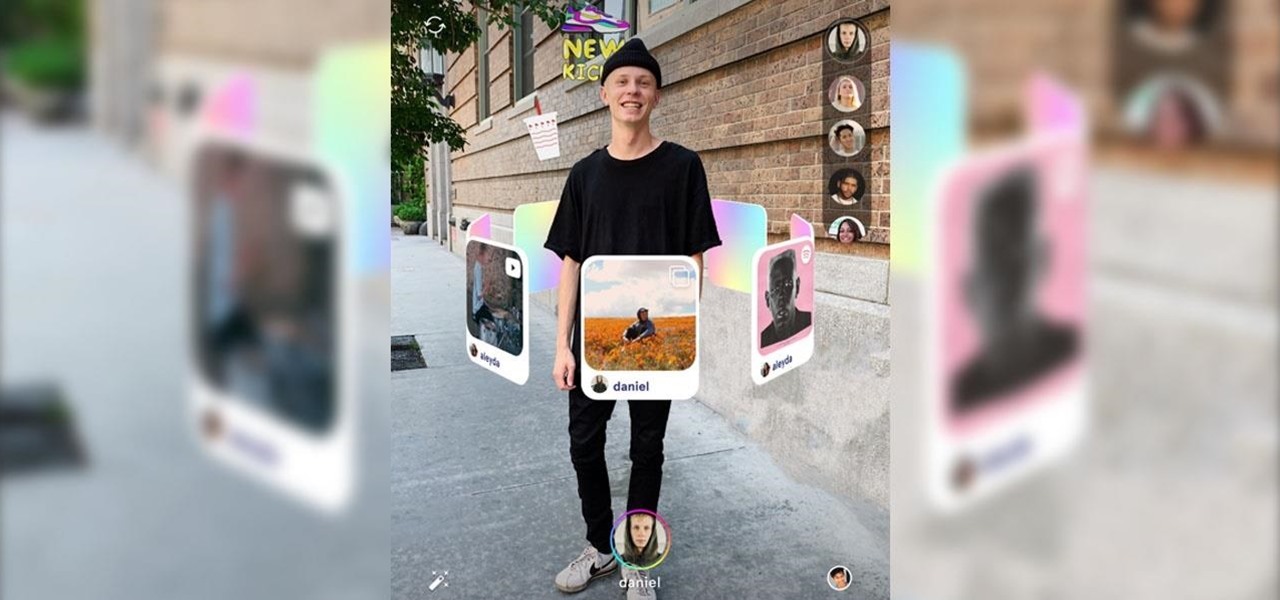
In a world full of augmented reality camera effects apps, one app is going in a more social direction.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

This simple but cool leather ring you can make in 5 minutes. Video: .

Gravity can be a real pain when you are trying to finish a project and your supplies wind up on the ground.

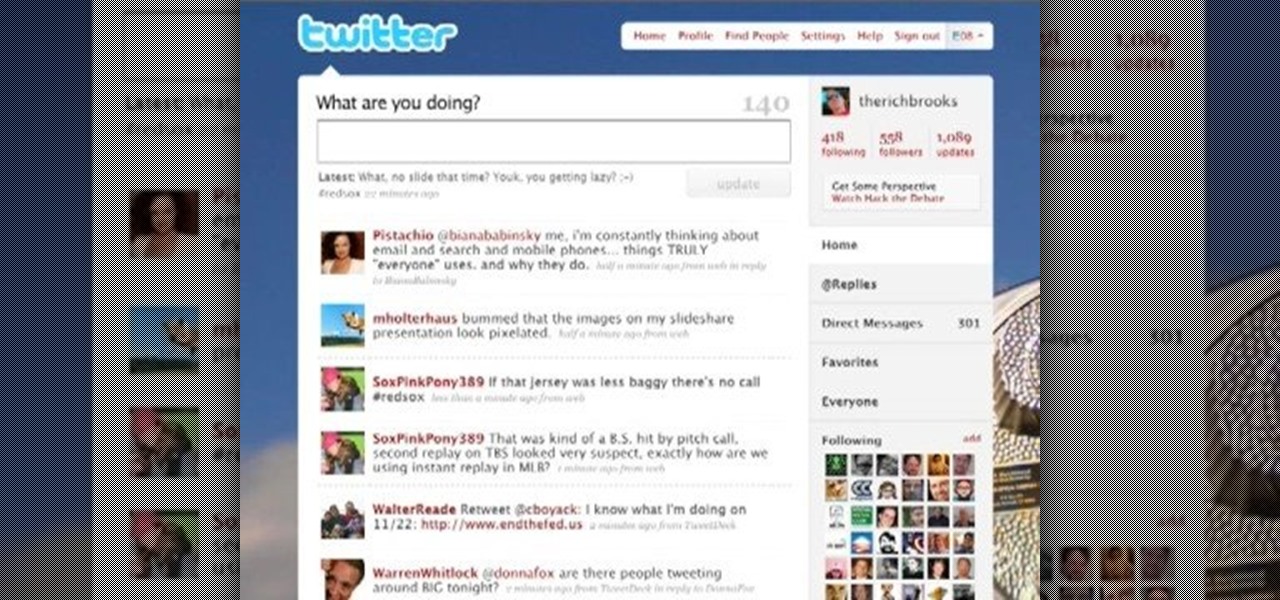
In this tutorial, we learn how to sign up and set up a Twitter account. Twitter is a social networking site where you have 140 characters to tell your friends how you are feeling, what you are doing, or talk to them! You can follow people and other people can follow you. You can choose who follows you, which will create and strengthen online relationships. You can even get business referrals from this! Just by getting yourself out there, this is a great tool. To sign up, you will simply go to...

In this tutorial, we learn how to remove pop up screens when Avira Antivirus updates. First, locate the installation folder for Avira, this should be in your computer programs. After this, locate the file "avnotify.exe". Next, right click this and go to the preferences option. Now, go to security, then edit, then click on the system option. Click "deny" on all the boxes in the bottom section, then save these. Now, the next time your Avira updates, you will not get a pop up box that tells you ...

Tired of your PC pestering you to check this or fix that? Are you sick of all those pop-up balloons? Well, Windows 7 now has a feature called Action Center, and it lets you decide which alerts you see and which ones you don’t. See it in action!

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

You have an online store ready to go… almost. You still have to deal with getting the perfect shopping cart to go along with your e-store. Matt Winn from Volusion walks you through what to consider when choosing a shopping cart software for your online store. From what type of software exists in the market, to the required features, to security levels (PCI certification), to the type of support you may need.