Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

No more q-tips! No more alcohol! No more blowing in your cart! Did you know alcohol actually damages the carts? This is a much more effective, safe and long term way to restore the connection.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.

There are so many things in place that make browsing the internet difficult. From geographical walls to malicious software and spying — there's a lot to consider any time you do the most basic of functions online. VPN.asia: 10-Year Subscription is a VPN that can streamline your security process and make browsing the web so much easier, and right now, it's on sale for just $79.99.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

Up until April 2020, the iPhone XR was, for many new users, the first entrance into the world of Apple because it was the cheapest iPhone model since the original iPhone SE. Now, the second-generation iPhone SE has shown up at the same initial starting price as its predecessor, giving budget-friendly buyers another choice.

When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device?

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

The holidays are here. From the week of Thanksgiving until the end of the year, retailers will be offering massive discounts on your favorite items. So if you're looking for smartphone accessories, this is the time to buy. From Walmart to Best Buy, there are deals everywhere on a host of items.

As Microsoft continues to bask in the glow of its HoloLens 2 unveiling and begins ramping up the hype to launch, Nreal and Vuzix are carving out their own niches in the AR hardware landscape.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

While Apple has moved on from Touch ID to Face ID in newer iPhone models, there are still plenty of iPhones with fingerprint sensors — in fact, Apple's second-generation iPhone SE is the first new Touch ID iPhone in three years. With Touch ID, you can register up to five fingerprints, but it doesn't stop there. Using a little-known trick, you can sneak another five fingerprints in there for a total of ten.

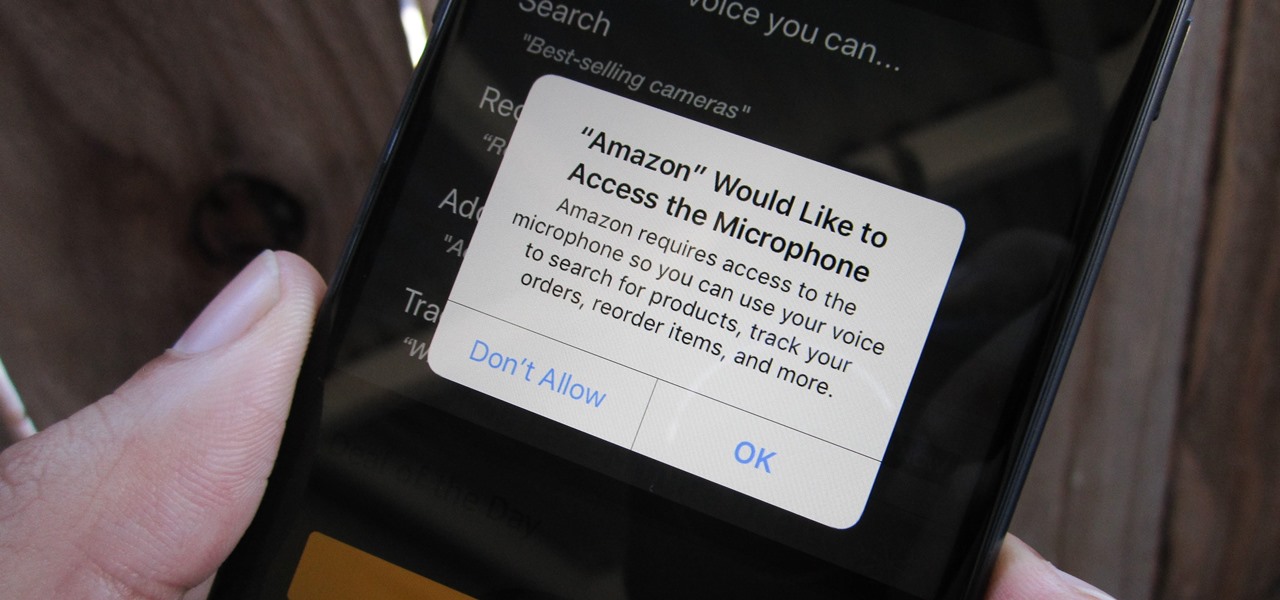
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

As great as passcode and biometric security features like Face ID are for preventing unwanted access, they aren't needed 100% of the time. When you're at home with a locked door between you and anyone you wouldn't trust with your phone, they really only serve to slow you down. Android has long had a solution for this, but a new Cydia tweak has now brought a similar solution to iPhones.

The last update to iOS 12 featured more emoji, Group FaceTime, eSIM functionality, real-time depth control for new iPhones, and a few other interesting tidbits and fixes. Now, in the latest for iPhones, iOS 12.1.1, Apple brought back a few things that were removed or made more difficult to access in previous updates, and it even has a few new features to offer, albeit small ones.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

Even with all the success HMD had with reviving the Nokia brand in 2017, it seems their second year is shaping up to be even better. Nokia has been steadily releasing sequels to last year's lineup, most with the new minimal bezel design language. The Nokia 7.1 is just their latest creation.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

When it comes to the sub-$250 price range, the new Nokia 5.1 might be the perfect phone. Of all the new models announced at Nokia's event in Moscow, the Nokia 5.1 offers the most with the least compromises. For a third of the cost of a flagship, you get a phone with a premium build, solid specs, and good battery life.

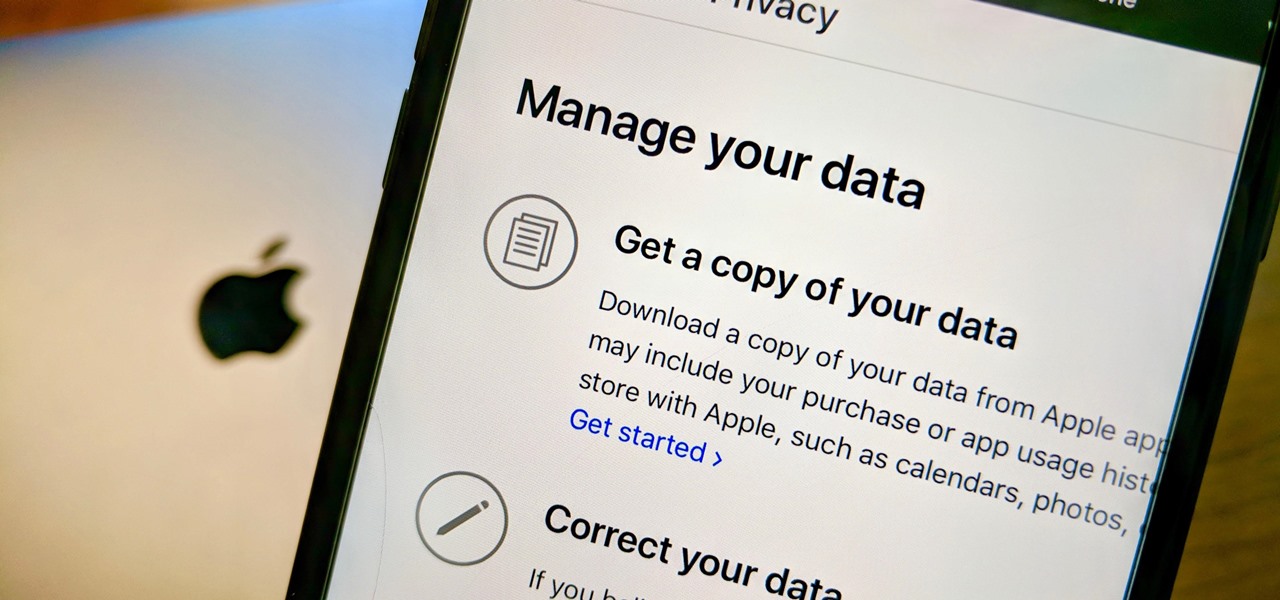
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

With Nokia's relaunch, the iconic company attempted to reimagine the budget phone market. The series of phones they introduced last year challenged the idea that good phones can't be cheap. This year, Nokia introduced the Nokia 7 Plus, a phone which offers perhaps the best balance of specs, software, and price.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

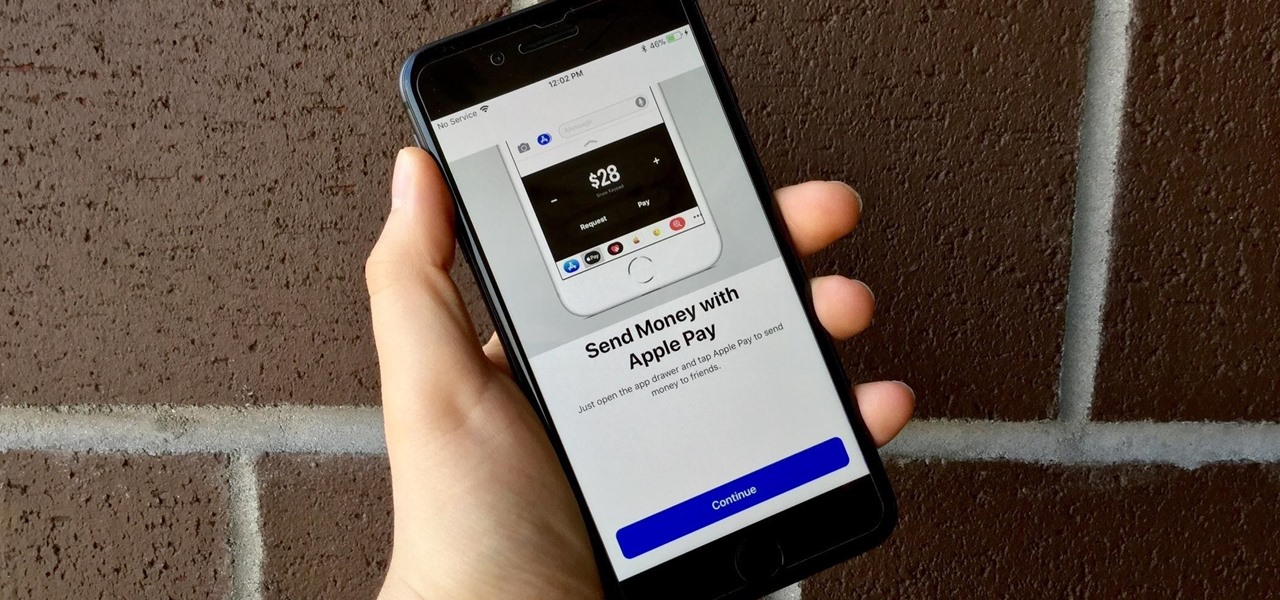
Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.