Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

There are many impressive features on a Samsung Galaxy Note 2, but just like any other smartphone on the market, the most used one is the camera. How many times did you take a picture today? Or admire all the selfies in your gallery? Or upload a video to Instagram, Vine, or Snapchat?

Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

There was recently a case that came to national attention where a gentleman was arrested at an airport for having a watch that looked like a bomb, among other things. As it came out, the watch was, in fact, not a bomb, and the man was just an artist who was probably trying to make a statement of some sort. Well, that message was lost amongst the hail of people shouting that either he had been stupid for bringing that watch on the plane and so deserved to be arrested, or that it's a free count...

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Your closet is an area that holds important things such as keys, glasses, clothes and shoes. However, for some reason, it's always messy. Why is this? I know my closet is messy because I don’t have a lot of time to sit down and organize every little thing in there. I have never really even given much thought into organizing it.

Adding a peephole to your front door is a cheap and simple way to improve home security. This how to video shows you what to consider and how to install a peephole.

How to Hide IP from Hackers. Hide your IP address to get more security. Hotspot Shield (free) change your IP address and your location. To see the changes visit http://www.ip-adress.com/ before and after running program.

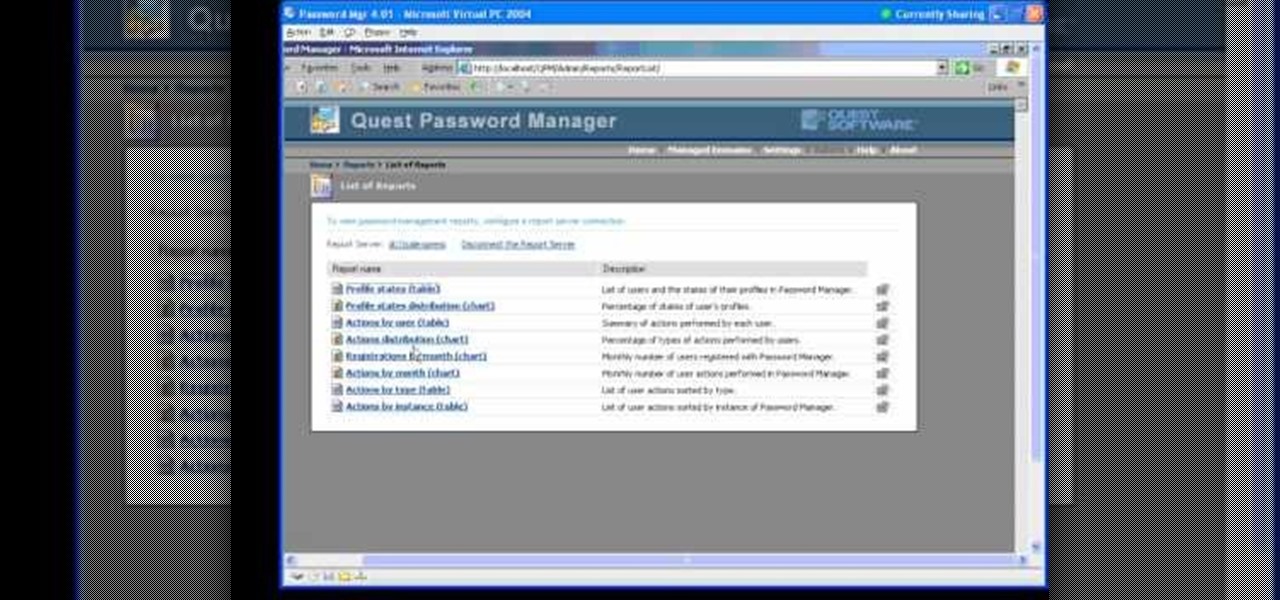
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

Watch as Karen's password is retrieved - both by hypnosis and with the help of technology. Plus, learn how to improve your password security.

Too many people just drive their cars for a few years and then replace them. When treated right, cars can keep on running for decades. You may not be able to keep your car running forever, but you can definitely extend its life.

Ronald Gotlin holds five black belts, including a 6th degree black belt in Tomiki Ryu Aikido, and is Past President and Founding Member of the International Aikido Alliance. This series of videos shows beginner moves in aikido.

Back in the '80s, I was just a kid with a LEGO hobby. I remember building castles and floating boats, spaceships and monster trucks, even a working LEGO train powered by battery, lights and all.

Android has a new security feature that every Android smartphone user needs to start using — even you. It won't change how you use your phone, but it will make life harder for nearby thieves.

Attackers may have actively exploited a new WebKit vulnerability on iOS and iPadOS, but Apple just released a patch to secure your iPhone and iPad from attacks.

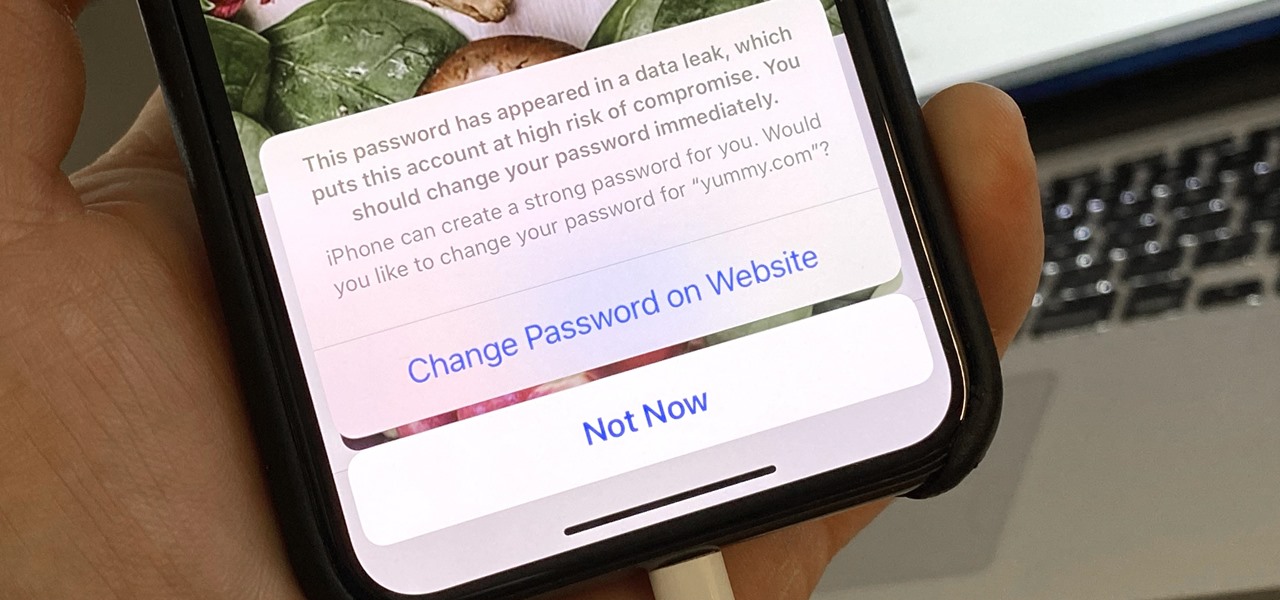
Everything lives online these days, so it's not uncommon to have hundreds of credentials for different accounts on apps and websites. That's why a password manager is a must, and your iPhone has one built right into iOS that you can start using today. In iOS 14, it's gotten even more useful since it can now monitor your passwords regularly to see if any match leaked password lists online.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

Although Facebook has some questionable privacy and security practices, you'll find it still offers you ways to protect the information that's important to you. One of those ways is locking Messenger behind biometric authentication protocols such as Face ID and Touch ID, ensuring that no one else can access your private chats.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding education to get the skills you need to thrive.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

The automatic software update setting on your iPhone is nice, but you may not always want to install new iOS versions blindly. New updates could contain bugs and vulnerabilities, and your favorite features may even disappear. With the auto-update option turned off, you can manually download and install updates, but there are also hidden options to be more specific about how you want to do it.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

With No Time to Die, the 25th installment in the James Bond saga, arriving in April and Black Widow, the first solo film for the Marvel Cinematic Universe's own secret agent, following a month later, what better way to get in the espionage mood than some augmented reality spy gaming?

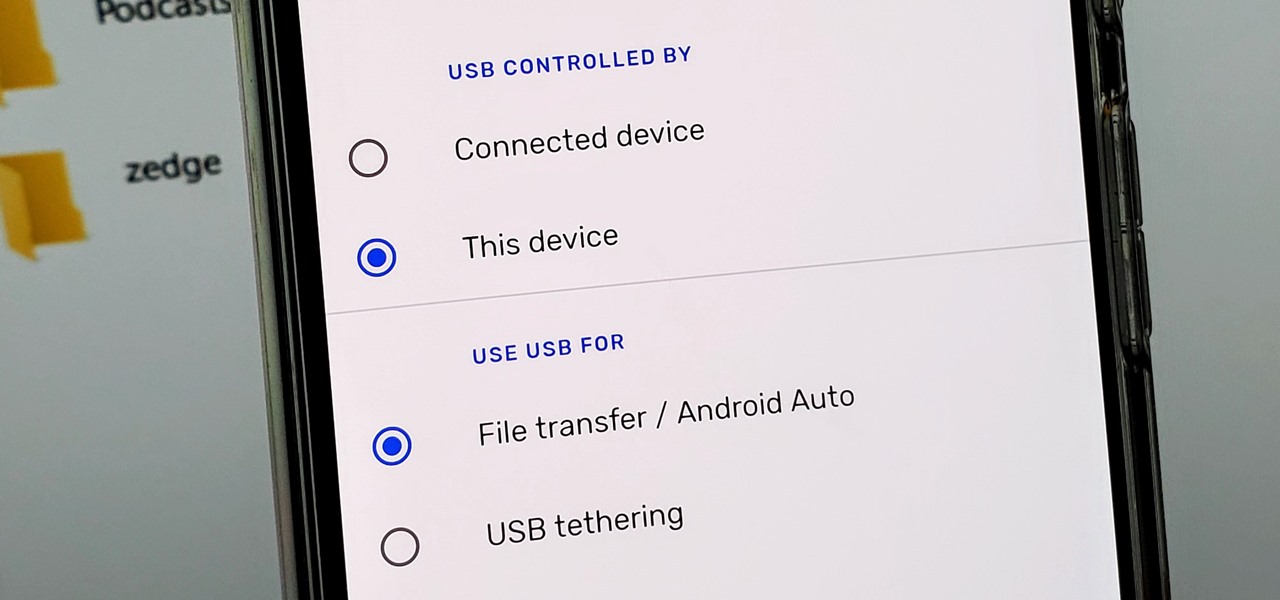
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

Estimates say that there are roughly 441 million Apple Pay users in the world, but with almost a billion active iPhones in the world, some of you have yet to jump on board the digital payment method. But once you're ready — or if you just need a refresher — adding your debit and credit cards to Apple Wallet is simple.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

We might never truly know all of the colors behind old and classic black-and-white photos, but thanks to technology, we can get a pretty accurate colorization. Although Photoshop is a popular way to colorize these images, you can now use your iPhone, along with a nifty shortcut, to transform and give new life to vintage photos.

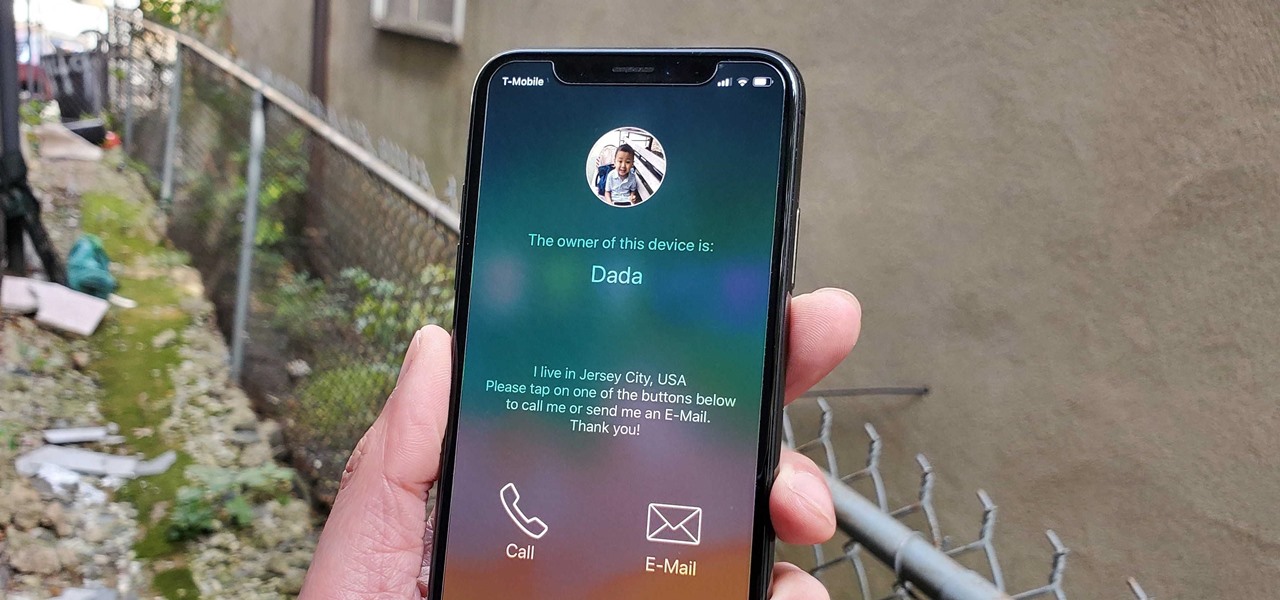
The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.

When you sign up to be a public tester for Apple's iOS, you get early access to features most users won't see for months. But you aren't the first — developers get priority when it comes to beta releases, made clear when they received 13.2 beta 3 while public testers were still on beta 2. Well, we public testers finally caught up, after Apple released iOS 13.2 public beta 3 Wednesday, Oct. 16.