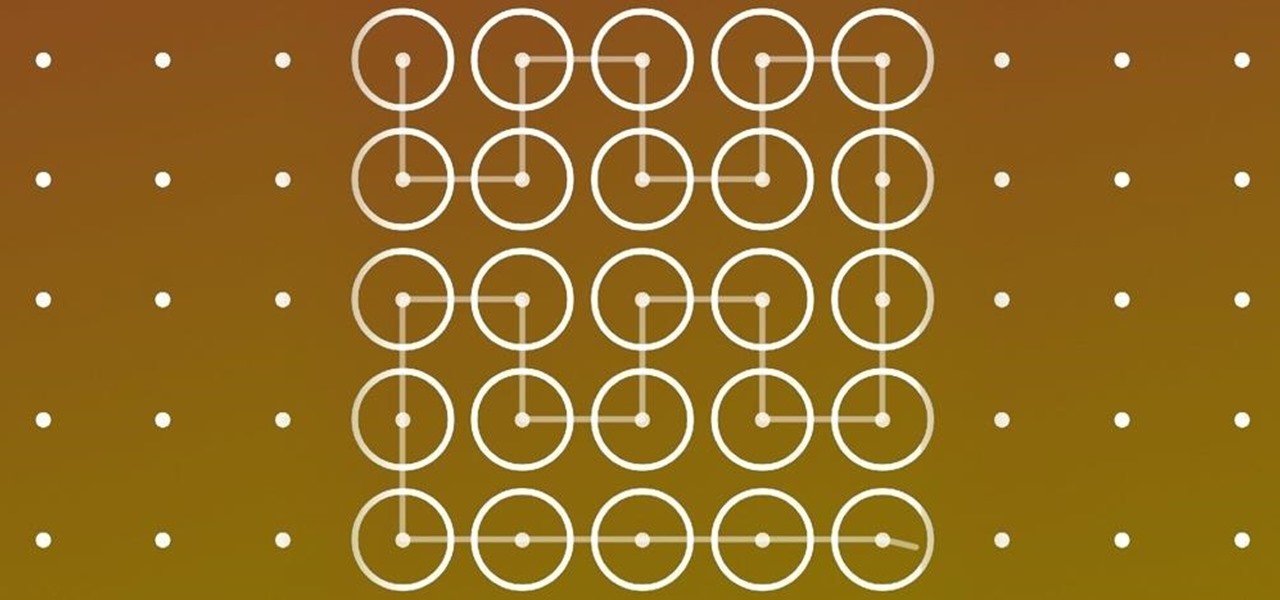
In this Microsoft Windows 7 users guide, you'll learn how to take advantage of the operating system's new Applocker security feature. It's easy! So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in about a minute and a half. For more information, including complete, step-by-step instructions, take a look.

In this how-to video you'll learn all the tricks and tips to getting yourself through airport security quickly and easily, even if you have electronic gadgets. Some companies produce travel gear that the TSA will let pass through without having to remove your laptop or electronics. Timesaver! Watch this video and you'll soon be cruising through the "Expert Traveller" line.

It seems that almost every multiplayer map in Gears of War 2 has a secret glitch-based way of getting underneath it. This video is a tutorial on how to do just one of these glitches. It will show you how to get under the Security multiplayer map using a barrier breaker glitch.

In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...
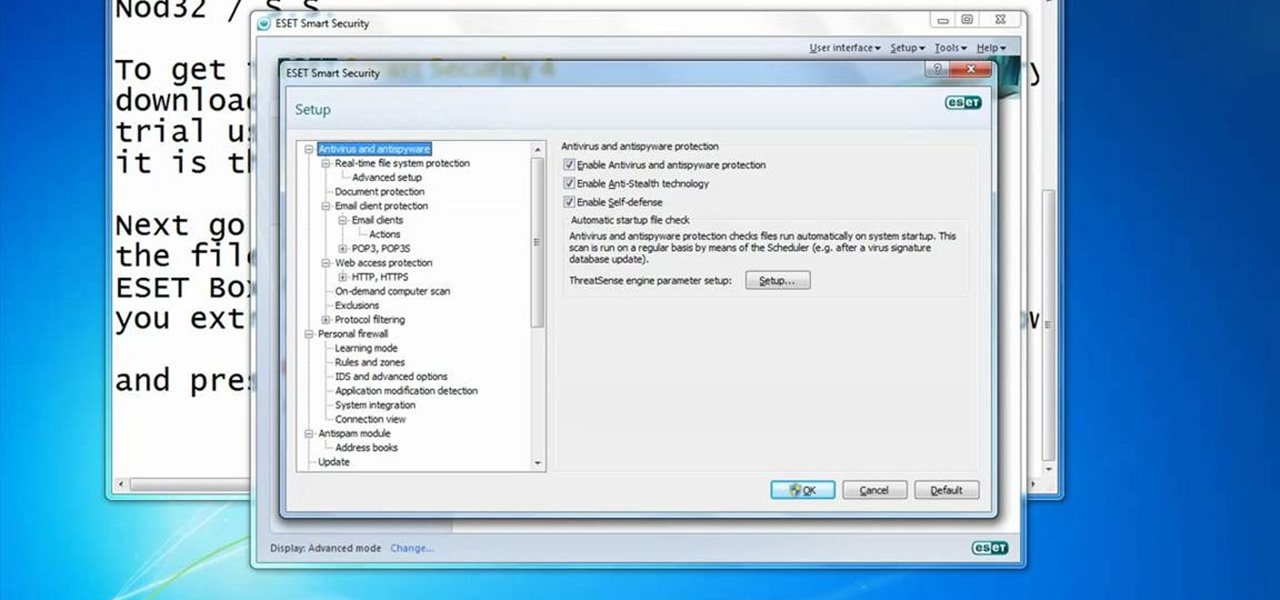
In this video you will learn how to Get ESET Nod32 or Smart Security forever. First make sure you have the trial for ESET Nod32or Smart Security. To do this go into the description of the video, download that file and put in the trial username and password. The downloaded file its called ESET Box4Ever.Before you extract the file open your ESET window and press F5.Uncheck self defense and restart computer. After you restarted the computer extract the files from ESET Box4Ever and run the file, ...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.

Got a mystery to solve? Somebody’s been making off with your stuff, and you don’t have a clue who it is, do you? Here’s your chance to catch them in the act. In this how to video you will learn to make a DIY laser security system.

Learn how you can protect your home in a pretty radical and fun way by transforming two cheap household items into a stealth hi-tech, anti-burglar, security system! Literally to hot for any bad guy to handle!

In this video you will see how to access network security cameras through google search engine easily!

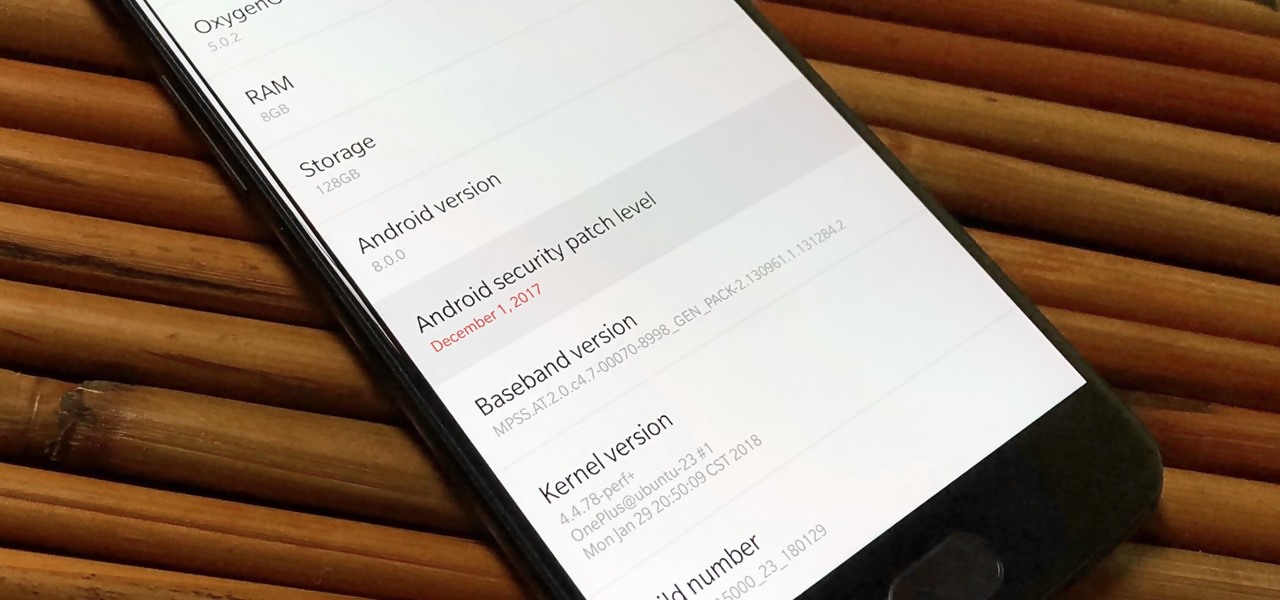
Samsung just began rolling out the Oreo Beta 2 to registered users of the Galaxy S8 and S8+. The update's changelog promises the inclusion of the October 2017 security patch. Unfortunately, after downloading the update, we've noticed this is not the case. Omission of the more recent security patch is notable in that it leaves devices vulnerable to several known exploits, such as KRACK.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

This video tutorial demonstrates how to draw a cartoon soldier or police officer. Begin with outline of an elongated face. Right above his nose, draw a small brim of his hat. Continue with the brim, adding the hat band and the top of the hat shaped somewhat like a bowl. In front of his face, draw his arm bent upward so his hand is appearing to salute. Add in shoulder patches. Next, draw his other arm bent in at his side. Add his belt buckle at the center of his waist. Now draw medals and acce...

If you're ever done a big race before, then you've probably had to deal with attaching a paper number to your chest with safety pins. In a triathlon, where you are going to have to change clothes multiple times, having to keep unpinning and repinning that number can cost you valuable time and effort. This video will show you how a race belt can simplify the process, making switching your numbers location a breeze, even across multiple outfits.

This is how you tie your belt for an aikido training. It is demonstrated by an aikido club member from Wimbledon, London, UK.

This video shows you how to tie a wide belt to accent many outfits.

Debra Hardy provides detailed instructions on how to make darling decorative Santa soy votive candles in this video. She first cuts the red felt into 6 3/4 inch by 2 inch strips for the Santa suit, wraps it around and adheres it to the bottom of the glass votive. Next, she secures a smaller strip of the white faux fur on top of the red felt also towards the bottom of the candle to create the bottom of Santa's jacket. Debra then instructs the viewer to cut a 6 3/4 inch by 1/4 inch black felt s...

Wearing a seat belt while in a car can save your life. Do you know how to adjust and properly use it? Learn how to drive safe and use seat belts properly (Ford DSFL). A professional driver explains how to fasten your seat belt properly.

As far as overall security updates are concerned, we all know that iOS reigns supreme over Android. But just how bad do Android devices fare against Apple in general? A recent report will have you second guessing some companies the next time you're in the market for a handset.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Samsung's 2016 line of smartphones has a new update, at least for the devices on AT&T. The update brings the Galaxy S7 to version G930AUCS4BQL1 and the Galaxy S7 Edge to version G935AUCS4BQL1. Here's what's on the table.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

This video will show you how to tighten a loose snow blower belt on a Toro snow blower. This would work on a Toro 624, 724 and 824. Also many other snow blowers that have a Briggs and Stratton engine.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.

Snapchat has had more than its fair share of security failures and mishaps. The photo-sharing company is looking to better address some of these security gaps by adding new features, and today its most recent addition is live: the Captcha. New users will be asked to verify their "humanness" by selecting the infamous Snapchat ghost out of a selection of images. The feature is supposed to help block hacker-made bots from creating fake accounts or accessing existing ones. But rather than using t...

In this video we will show you how to quiet a squeaky engine serpentine belt.

In this video we will show you how to install a new serpentine belt on your 96-06 Chevy Silverado or GMC Sierra.

This quick video will show you how to replace the engine serpentine belt idler pulley in your Ford F150, F250, or F350 pickup truck (1992-1996).

This quick video will show you how to change a loose serpentine belt tensioner in your Ford F150, F250, or F350 pickup truck (1992-1996).

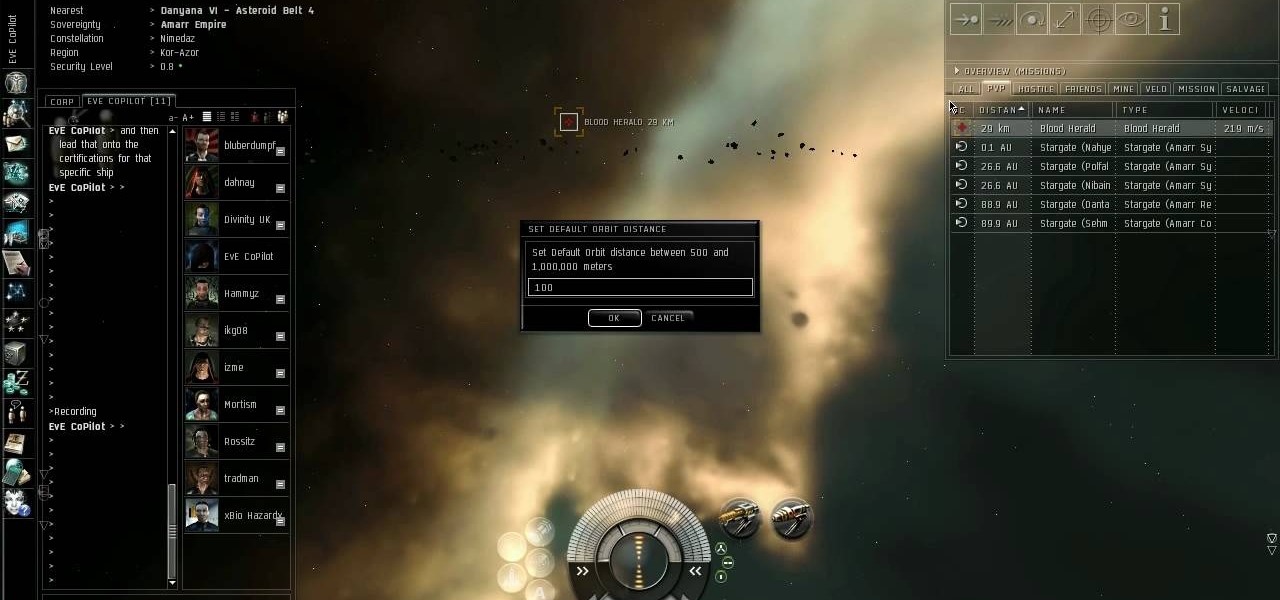
Quickly turn a profit during a combat mission by ratting - killing NPC enemies who spawn in asteroid belts. The difficulty of rats depends on how secure your system is - the lower security, the harder the rats are to kill. This tutorial shows you the best way, as a new player, to earn money by ratting.

All hail Caesar, it's costume time! OK, if you're a woman, or a girl and you're looking to make a cool toga costume, look no further as this video will show you what you need. Basically you'll want some white fabric, either cotton or satin or whatever you have in your sewing box. You'll need some rope, twine or ribbon to make the belt. Follow the steps to wrap the fabric and tuck it into a tube top to hold it, then use your belt to complete the girl toga costume. Toga! Toga! Toga!

The first way the she explained tying a scarf was "belting a pashmina." Which is taking a pashmina scarf, placing it around your neck and securing it under a belt that you fasten around your waist. The second method was "Be a wrap star." Get a really long scarf, tie it around your neck twice loosely, keeping it uneven and adding fullness to your neck. The third way was to "rethink your evening scarf," where she describes a bow scarf. You put the scarf around your neck and put one side over th...