
TypoGuy Explaining Anonymity: Staying Hidden from the NSA
We all know them, and many of us despize them. And some might support them, regardless many have different opinions.


We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

What's up guys! It's time to discuss strings in more detail. Review

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

The Fire TV Stick, as well as the Fire TV, may be limited by Amazon's fight on piracy, but after a quick sideloading of Kodi, the floodgates are back open with the freedom to stream just about any video or song you want.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Ideas can be a fleeting thought, just like a shooting star that appears and disappears within a brief moment. So when you're inspired and have an awesome idea, it's important to jot it down as soon as possible, otherwise it may vanish from your memory for good.
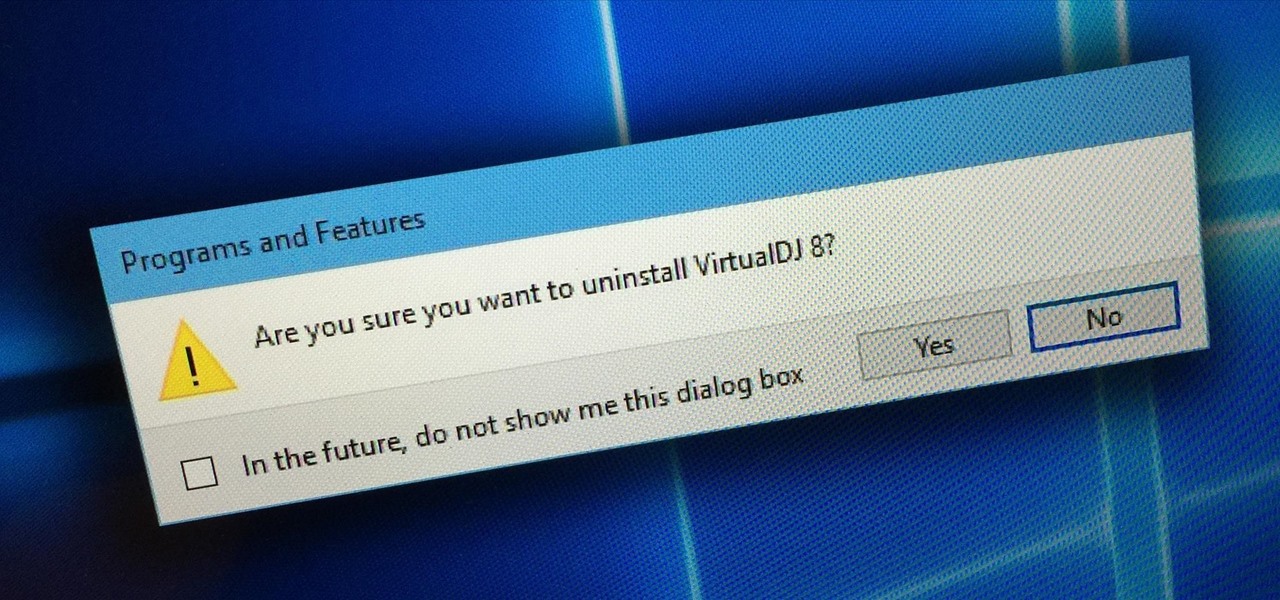
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.
The transition from Android KitKat to Lollipop was pretty drastic in the looks department. Google's new Material Design guidelines changed the way many parts of the UI function, like the notification drawer, status bar, and most notably, the lock screen.
Ah, the fabled dark mode. In the past, many users were delighted to find the existence of something called Royale Noir, a dark theme option that was available for Windows XP. Yet for reasons unknown, Microsoft had kept knowledge of Royale Noir a secret until some bright minds discovered its existence, and the rest is history.

When you go to the grocery store, chances are you're confronted with the usual piles of apples, berries, bananas, and melons. All well and good, right?

With iOS 8.4 and iTunes 12.2, we got our first look at Apple Music, Apple's new streaming subscription service. While it's a little late to the party, there is definitely an incentive for iOS and Mac OS X users to switch over from competitors due to its heavy integration with the Apple ecosystem.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Windows 10 is due to be released on July 29th, and the majority of existing Windows users should be eligible to upgrade to the newer version for free.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

The Samsung Galaxy S6 includes a pretty nifty feature known as "Gesture wake up," which lets users wave their hand over their locked display to wake it, making those periodic notification checks from the lock screen a lot more simple than having to press the power or home key every time.

After you have registered to this site,sign in then to start missions. Basic Missions

Nearly nine months after the release of the iPhone 6 and 6 Plus, we finally have some solid information on the "S" model of Apple's flagship device, slated for release this fall. Coming straight from Apple analyst Ming-Chi Kuo of KGI Securities (via AppleInsider), quite a few upgrades will be included in the next iPhone model.

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

Android's auto brightness feature was recently updated, and as of version 5.0, a new "Adaptive brightness" feature was added. This allows users to set a preferred overall brightness level, but still have the ambient light sensor adjust the backlight accordingly.

The wait is over. The Samsung Galaxy S6, arguably the best Android phone of this year, has just launched. There was already a lot of hype about this super phone—its looks, its specifications, and its other functions have been under the microscope for quite some time. It will not be a good idea that you take this phone in your hand and use it in the same fashion as you have been using your other phones in the past.
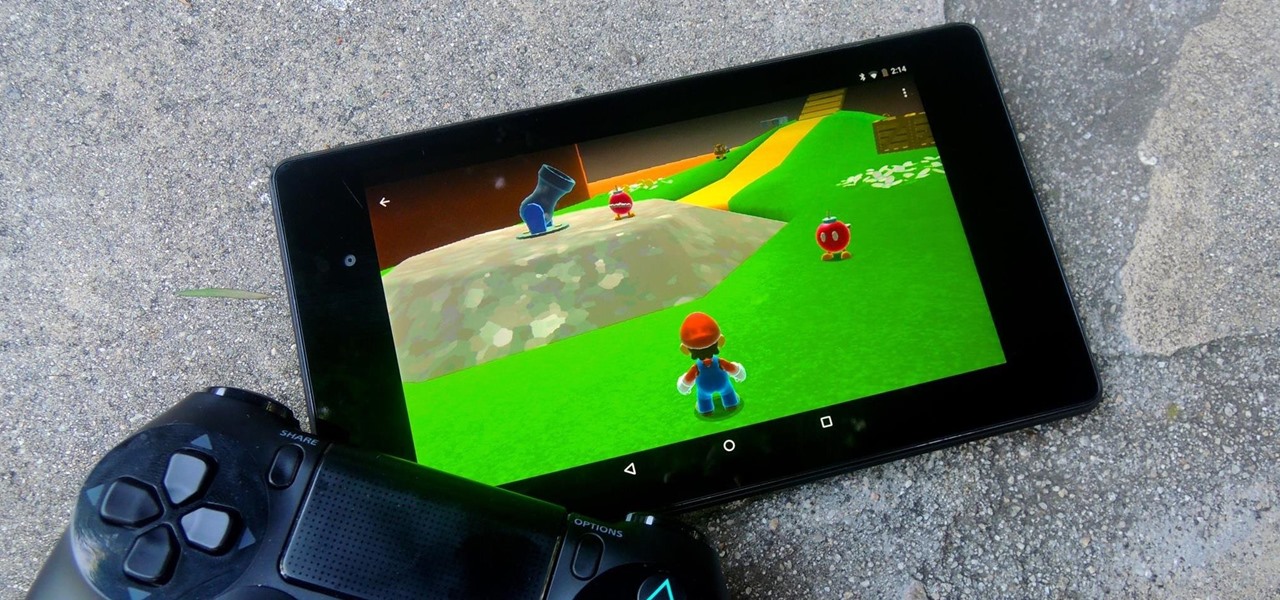
If you're jonesing to play some Super Mario Run on your Android phone, you might not be able to get your fix for some time—at least, until Nintendo figures out the best way to keep piracy down and security high. But if you can't wait for the first official appearance of Mario on Android, we've got the next best thing...

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

Welcome back, my budding hackers!