One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

One of the hardest, most intimidating parts of making your own Steampunk guns from scratch is the wooden stock of the gun. To be fair, it's probably the hardest part. It requires the most artistry, and is the easiest to mess up.

Access your computer's BIOS settings

This video will show you how to disable secure virtual memory in Mac OS X. From the top left of your screen click on the apple icon. Click on system preferences from the pull down menu. Click on the security icon. Click on the image of the closed lock from the bottom left of the window so that you can change make changes.

Get a new perspective on computing with an HP Tablet PC. HP's Tablet PCs are well-equipped personal notebooks, with a significant twist. The display turns around one hundred and eighty degrees, transforming your notebook into a flat tablet touchscreen PC.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

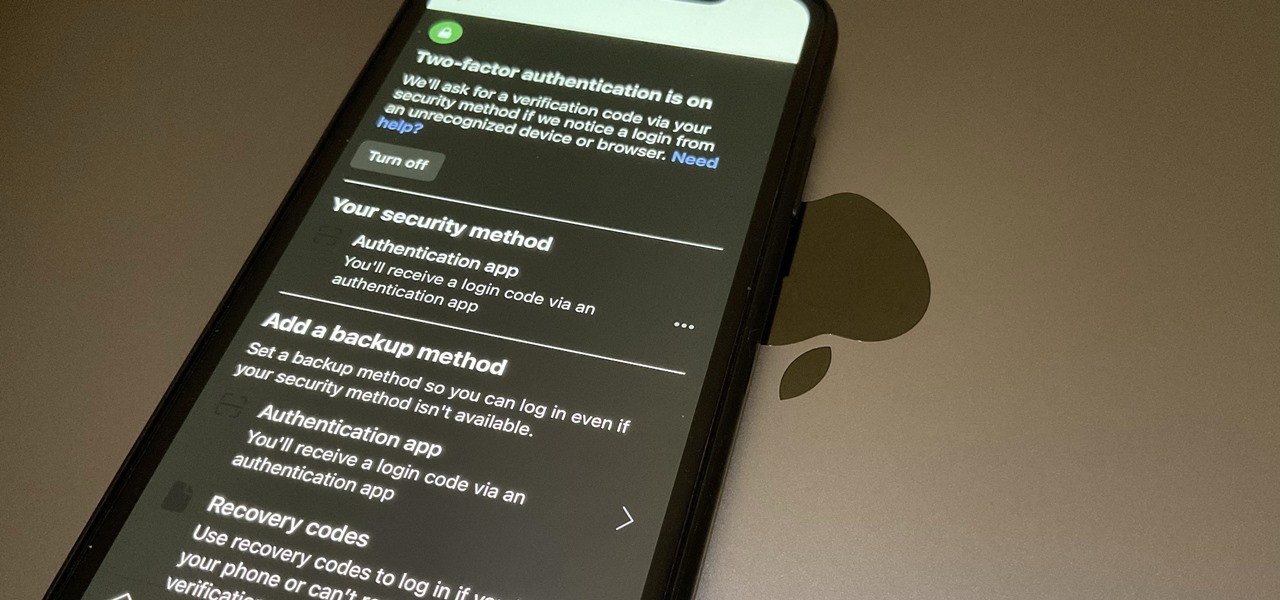
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

Amazon really wants to make itself at home in your home. Like, everywhere in your home, from your doorstep to your kitchen, your kids' rooms, and everywhere in between.

The emergence of Microsoft's HoloLens 2 as a cutting-edge US Army tool has focused a spotlight on the marriage between augmented reality and the military.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

Apple released the newest update for iPhone, iOS 14.5.1, today, Monday, May 3. The update (build number 18E212) is the first since iOS 14.5, which Apple made available one week earlier on Monday, April 26.

Apple just rolled out the of iOS 14.5 to developers and beta testers, and one of the headlining features is the ability to keep your iPhone unlocked when your Apple Watch is nearby. As these things tend to go, Android has actually had this same feature for years, though it isn't quite as polished.

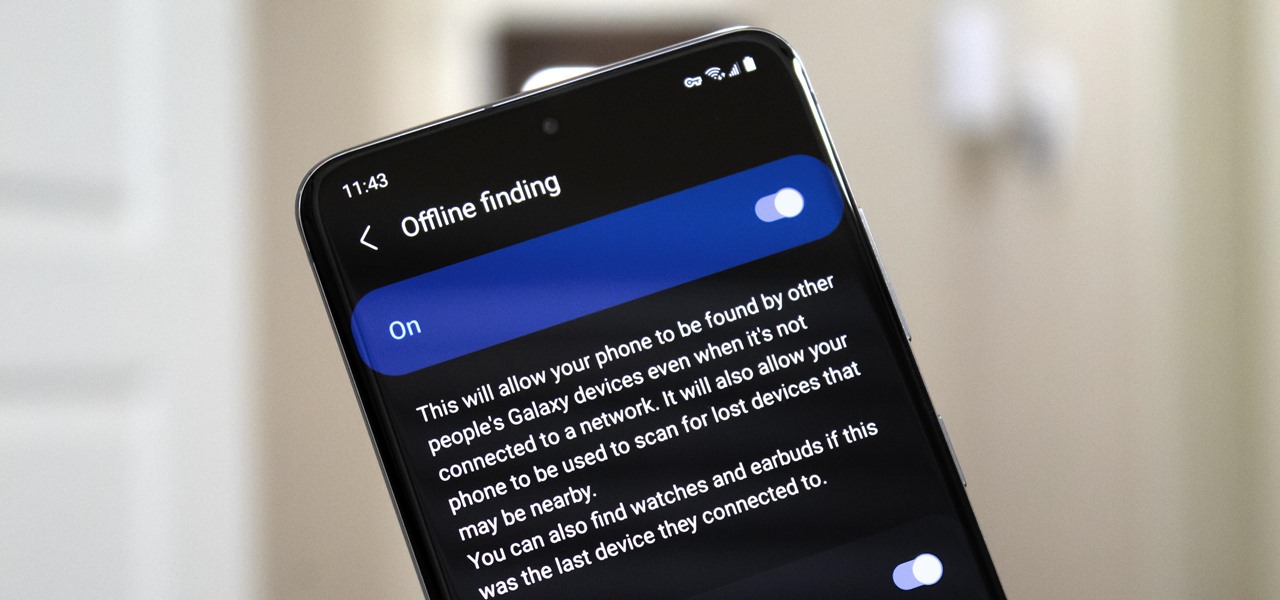
Nowadays, even the dumbest thieves know that the first thing you should do after you steal a phone is turn on airplane mode. Not only does this make it harder for police to track the phone through cell tower triangulation, but it also disables security features the person you stole it from may have implemented — for instance, Samsung's Find My Mobile service.

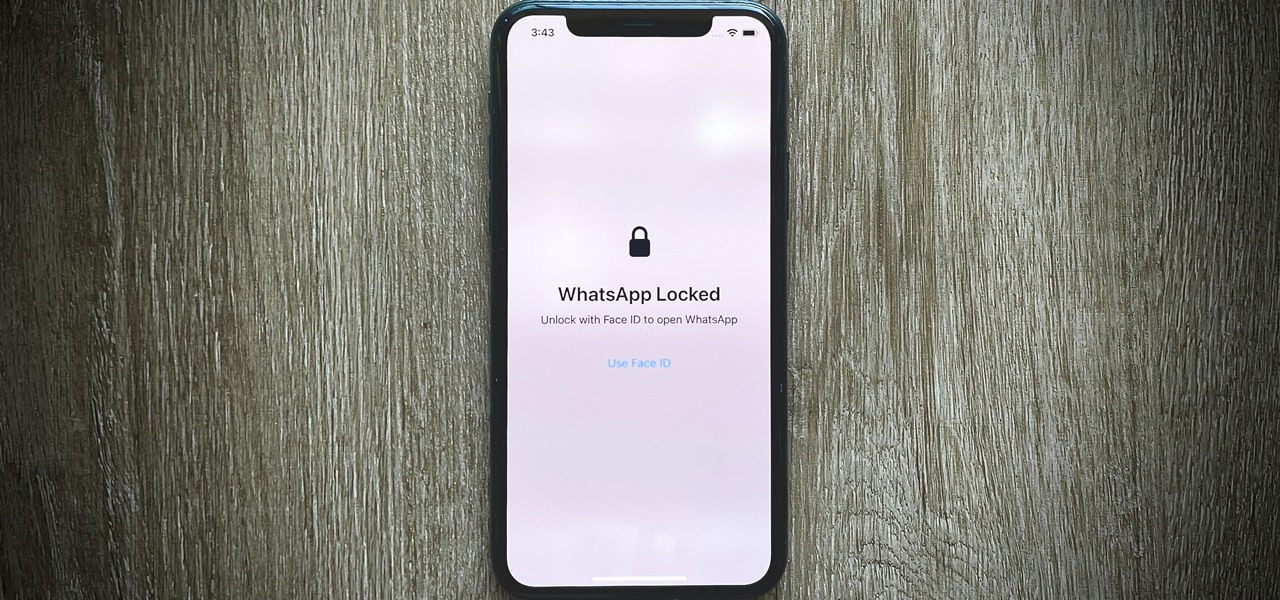
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

In the tech world, our data is always under attack. When you download and install a new app, it can be difficult to know what information the app is actually accessing. Thankfully, a new emphasis on privacy in iOS 14 changes the game, exposing more of what your apps want access to — and even changing some behavior along the way.

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.

Apple just released iOS 13.5 for iPhone developers today, Monday, May 18. This GM (golden master) update comes 12 days after the release of iOS 13.5 dev beta 4, which introduced updated COVID-19 exposure notification logging settings and the ability to share your Medical ID with first responders when placing an emergency call.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

Apple has their regular iPhone 11, then two higher-end "Pro" models. Samsung went the other way — they have the Galaxy S20 and S20+, then there's the S20 Ultra. But one thing these smartphone lines do have in common is the base model flagship. How do they compare?

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

It's a good sign for any emerging technology when one of the leaders of an industry adopts it. So when Mastercard, a brand so recognizable that it dropped its name from its logo at CES last year, decides to develop a mobile augmented reality app, the moment is a milestone for the AR industry.

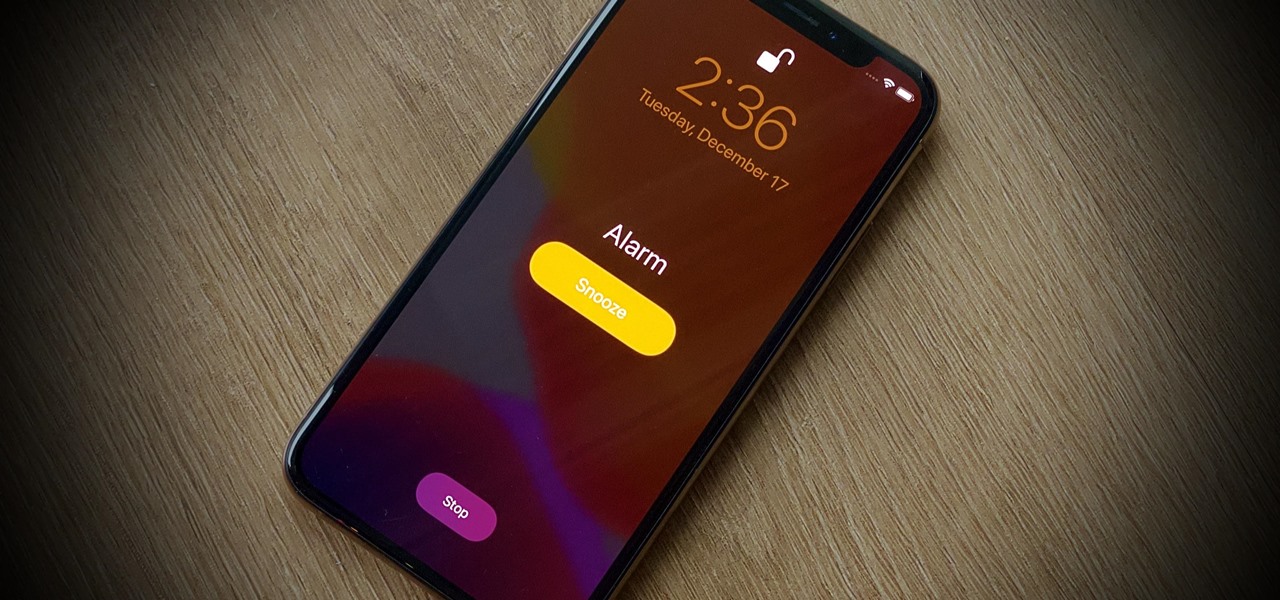
It happens to almost everyone. You wake up one morning, check your phone, and realize your alarm never went off. Now you're late to start the day, and you spend every night onward paranoid it'll happen again. But if you have an iPhone, there are two things you can check to make sure the alarm always goes off on schedule.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Smartglasses from Apple have become the holy grail of augmented reality, and 2020 has been the rumored time horizon for the product's arrival for the past two years. The latest analyst report sheds more light on its potential debut next year.

There have been enough music artists releasing Snapchat AR experiences over the past week to fill a small festival. Count them with me: Bruno Mars. Gucci Mane. Kodak Black. Missy Elliot. Imagine Dragons. Panic! At the Disco.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

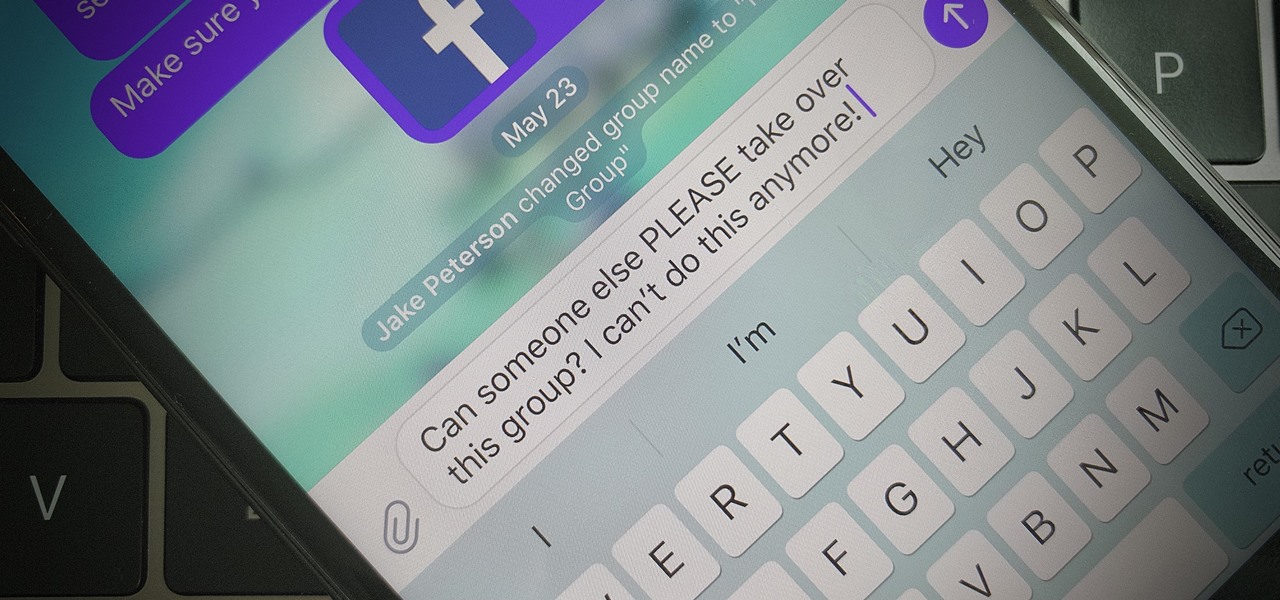
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?

WhatsApp, the popular messaging app owned by Facebook, has several important privacy and security-related features, including end-to-end encryption, screen lock, read receipts, and two-step verification. If you're an avid WhatsApp user, you'll be happy to know there are more privacy features you might not know, such as hiding your profile photo from other users.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

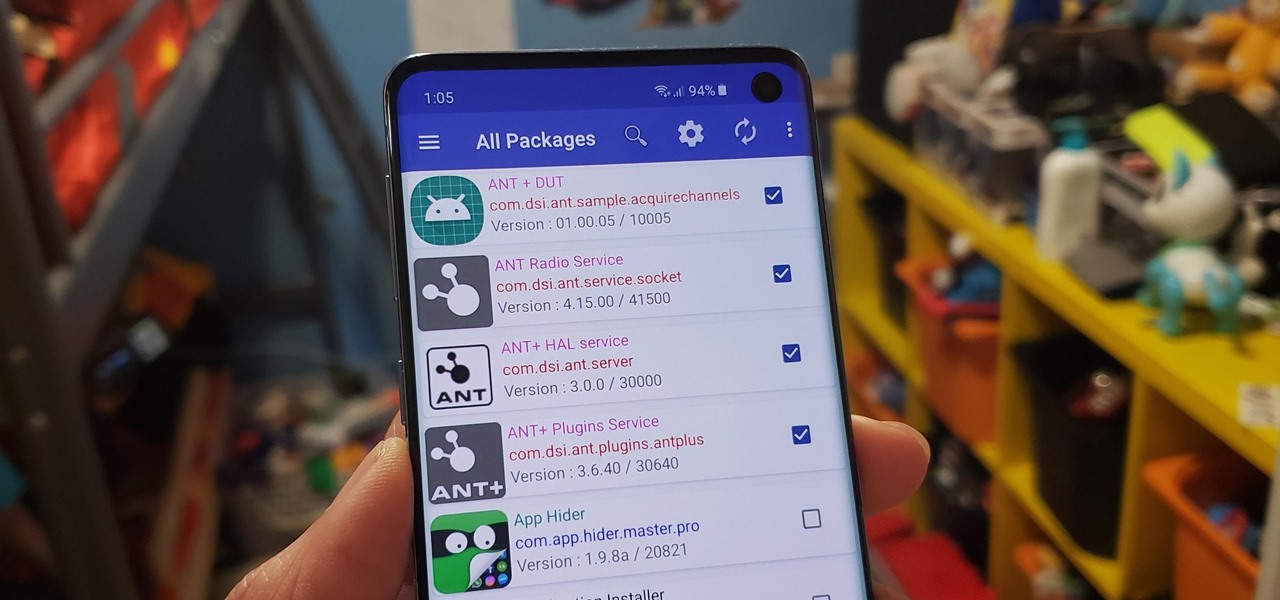
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.