Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.
OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.

The enterprise sector is where the money is for augmented reality at the moment, and remote assistance apps are the go-to app for many enterprise customers. We took a look at the leading apps and platforms from this category, from the top contenders to the underdogs with unique features.
The OnePlus 7 Pro is truly the best phone that the company has ever created to date — it's even one of the hottest phones around regardless of OEM. It offers an awesome display with minimal bezels, a smooth 90-hertz refresh rate, a pop-up selfie camera, and the best triple camera system in a OnePlus phone so far. It can truly compete with other flagship phones while keeping the cost down.

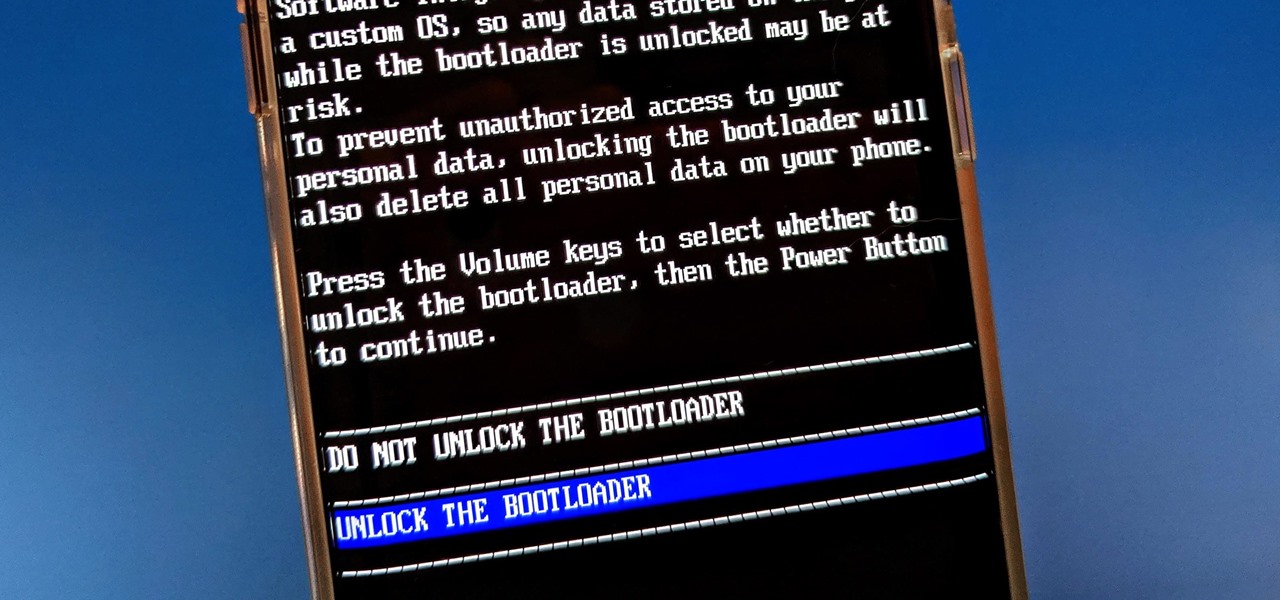
The first thing you'll always have to do before getting your customization game on with most phones is to unlock the bootloader. Doing so opens the true potential of the device, allowing you to root, install TWRP, Magisk, custom ROMs, and other mods. No matter your wants or needs, there's no way around it — the bootloader must be unlocked to modify the system.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Apple released iOS 12.3, the latest version iOS 12 for iPhone, on May 13. Great features to know about include Apple TV Channels such as HBO and Showtime that you can subscribe to in the TV app, support for audio, image, and video streaming to AirPlay 2-enabled TVs, and the ability to use Apple Pay to pay for content and subscriptions inside Apple's own apps.

The hugely successful S10 series of flagships may be a tough act to follow, but Samsung has proven that it's up to the task with the Galaxy Note 10. The latest phablet bearing the Note name is the first of its line to come with an even larger variant, and boasts an eye-pleasing design with impressive performance to boot.

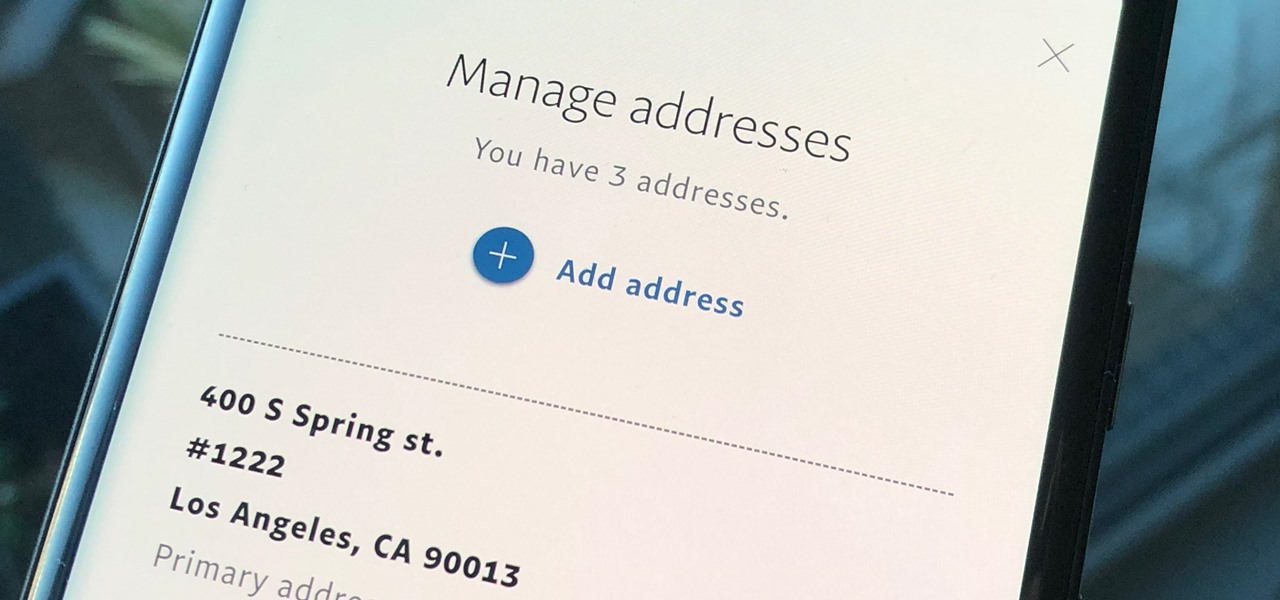
Whenever you move into a new home, whether that's a house or apartment, changing addresses on all your online accounts is one of the most monotonous tasks that needs to be done. It's even more tedious when you have to update both shipping and billing addresses. But it's necessary, and if you regularly use PayPal, it'll be one of the first places you'll want to update.

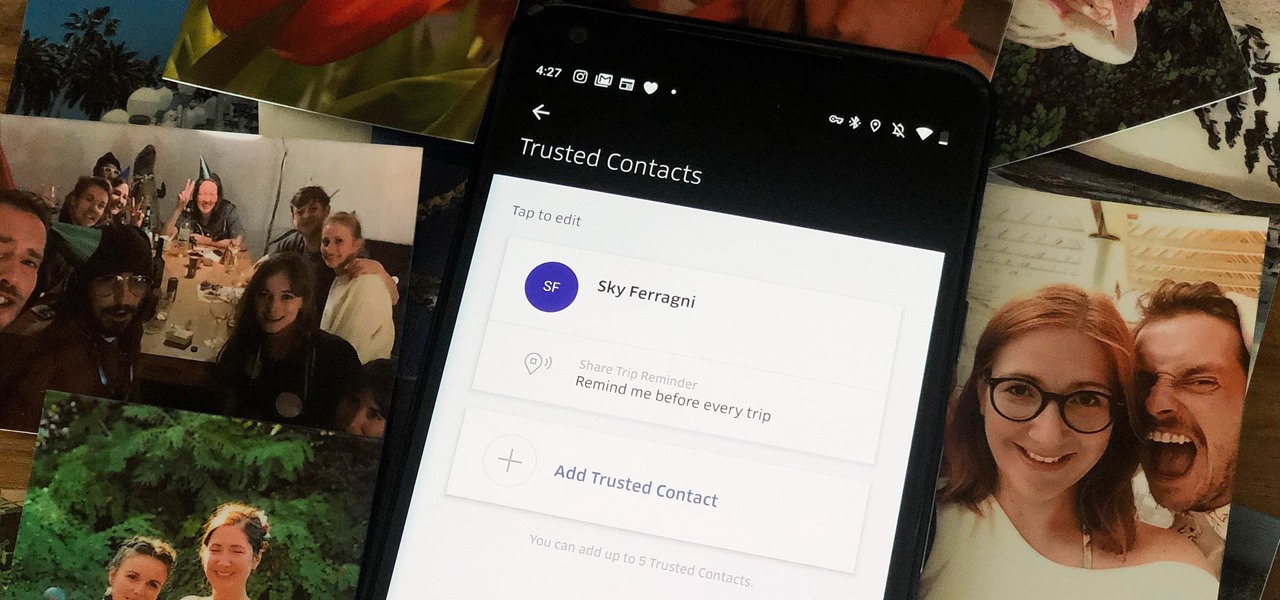
When you're riding in an Uber, on your way to meet family or friends, they may want to know where you are exactly to see how long until your arrival. On the other side of the coin, there may be times when you want to tell family or friends where you and your Uber car are without them asking, like when you're in a dangerous situation. Uber makes this easy, as long as you set it up first.

When someone sends you a funny video, image, tweet, what have you, often the first thing you want to do is share it with someone else. Instead of copying the link and jumping over to another chat to do so, WhatsApp makes it easy to share content right from the thread you received it in, via the forward feature.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

New updates are always exciting, even more so when Google's behind the wheel. Yes, Android 10 "Q" is here, at least in beta form, ready for software testers to dive in and explore all the new changes. Among those changes, however, lie some issues. We won't sugarcoat it — there are some annoying things baked into Android 10.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

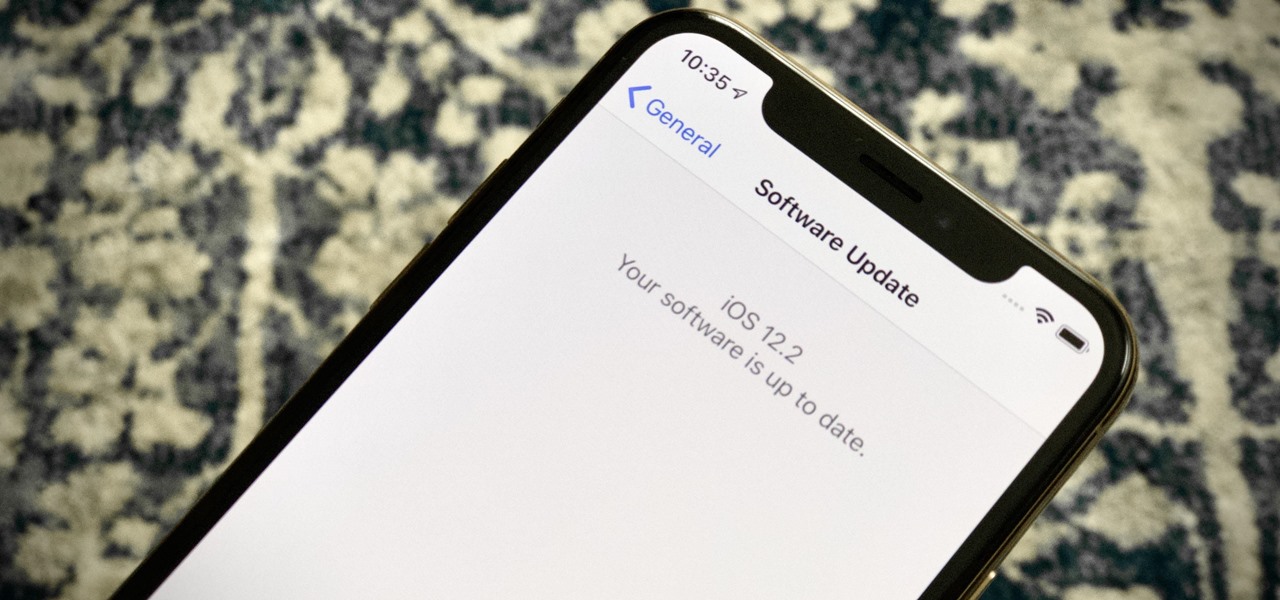
Public beta testers are in for a treat today. While Apple is extremely inconsistent with the release schedules for the developer and public betas, the company has once again released both versions of iOS 12.2 beta 5 today, March 11. If you're a public tester, you now get to experience all of iOS 12.2's new additions for yourself, instead of needing to read about them for up to 24 hours in advance.

If you're an iOS app developer, your Monday just got better; Apple just released iOS 12.2 developer beta 5 to your Software Updates today, March 11. This fifth beta includes a number of small UI changes and tweaks, and likely some degree of under-the-hood improvements and bug fixes.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

In 2019, Sony is mixing up its design, attempting to stand out among the sea of familiarity. Instead of emulating Samsung with punch hole cameras, they decided to target a rare section of the market, content consumers. There's the Xperia 1 for those who want the best, and the Xperia 10 and 10 Plus for the budget crowd.

Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.

Once again, LG is mixing up its launch. Instead of the announcing the latest entry in G series later in the year, the LG G8 ThinQ was announced at Mobile World Congress 2019, shortly after Samsung's Galaxy S10 event. And instead of trying to match what other OEMs are doing, LG is once again trying to be different.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

On the surface, Instagram is pretty intuitive, so you might think that you already know everything there is to know about using it on your iPhone or Android phone. But this photo and video-sharing app is constantly adding new features, some of which don't make the press releases. Even if you're an Instagram guru, chances are you've missed one of these hidden goodies.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

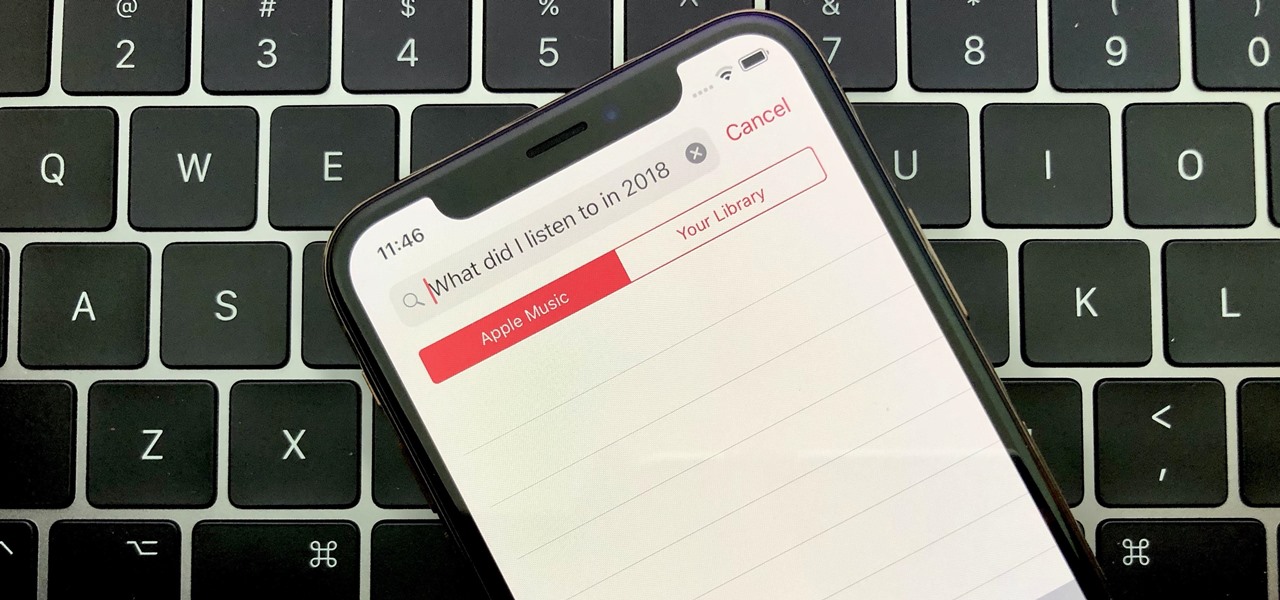
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

Investors continue to bet on augmented reality, both for short-term returns and long-term plays. This week, Niantic reportedly picked up another round of funding from Samsung and others, based on the success of PokémonGO and the prospects for future revenue. Likewise, investors see value in WaveOptics, whose waveguide displays could make consumer smaller AR smartglasses possible within the next year.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

The North remembers...that smartglasses are the future! Game of Thrones jokes aside, the smartglasses startup opened its doors, and we visited its Brooklyn store to get our hands the consumer-focused Focals smartglasses.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

This week, inside sources divulged details of how Apple nearly acquired Leap Motion, twice. Otherwise, companies offering or working on augmented reality technology had more successes than failures to talk about.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

In the battle for best stock Android flagships, there are really only two choices: Google Pixel phones and OnePlus phones. Although the latter isn't true stock Android, it is impressively close and usually paired with more impressive hardware than the Pixel lineup. The latest is the OnePlus 6T, which will be a bit controversial for fans this year.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

There's more to recording calls than just protecting yourself against liability or an angry ex — oftentimes, this feature is the perfect tool to save momentous calls like breaking news of your recent engagement to loved ones. And with the prevalence of video calls, you can even capture memorable video chats such as your mom's first glimpse of your newborn on your mobile, courtesy of Skype.

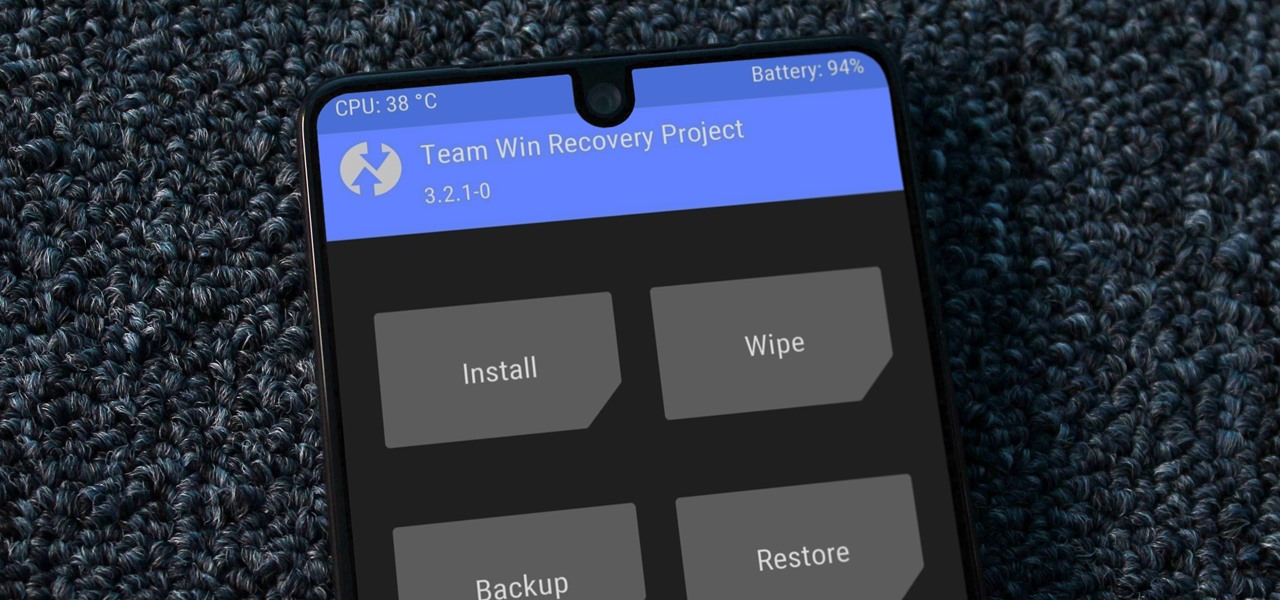
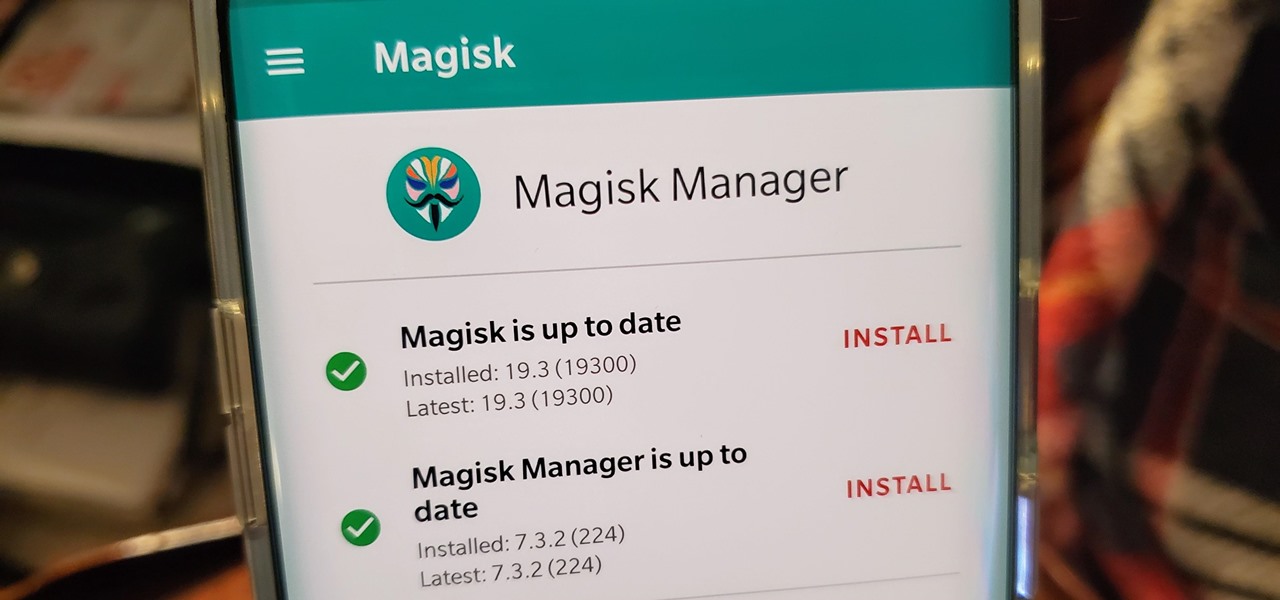
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.