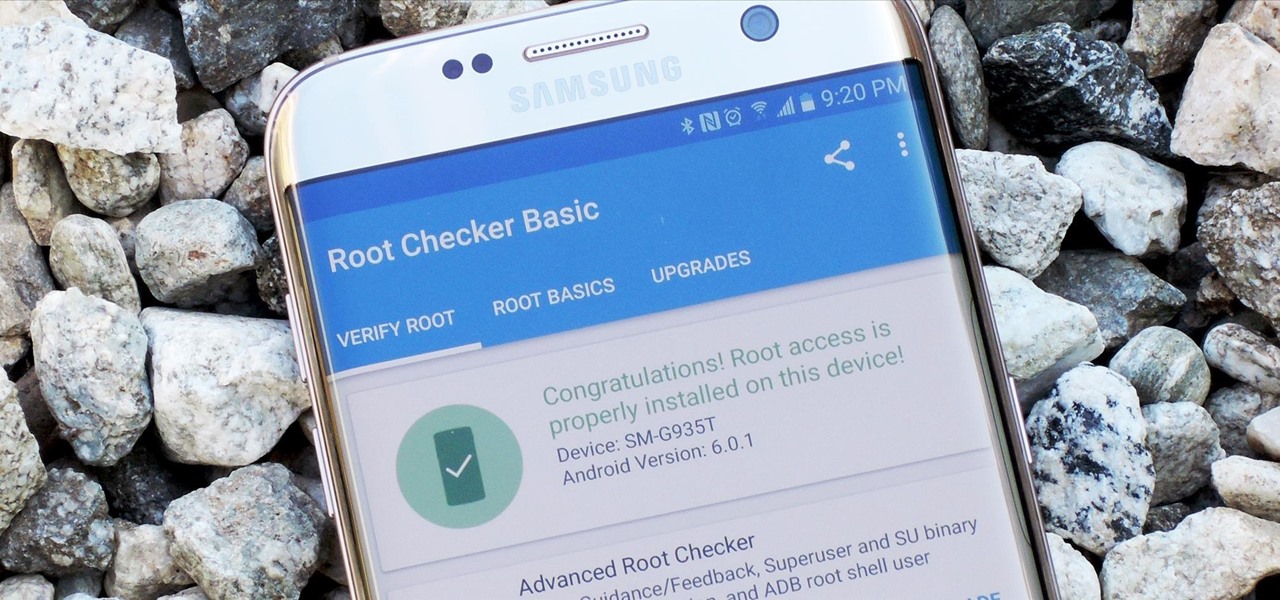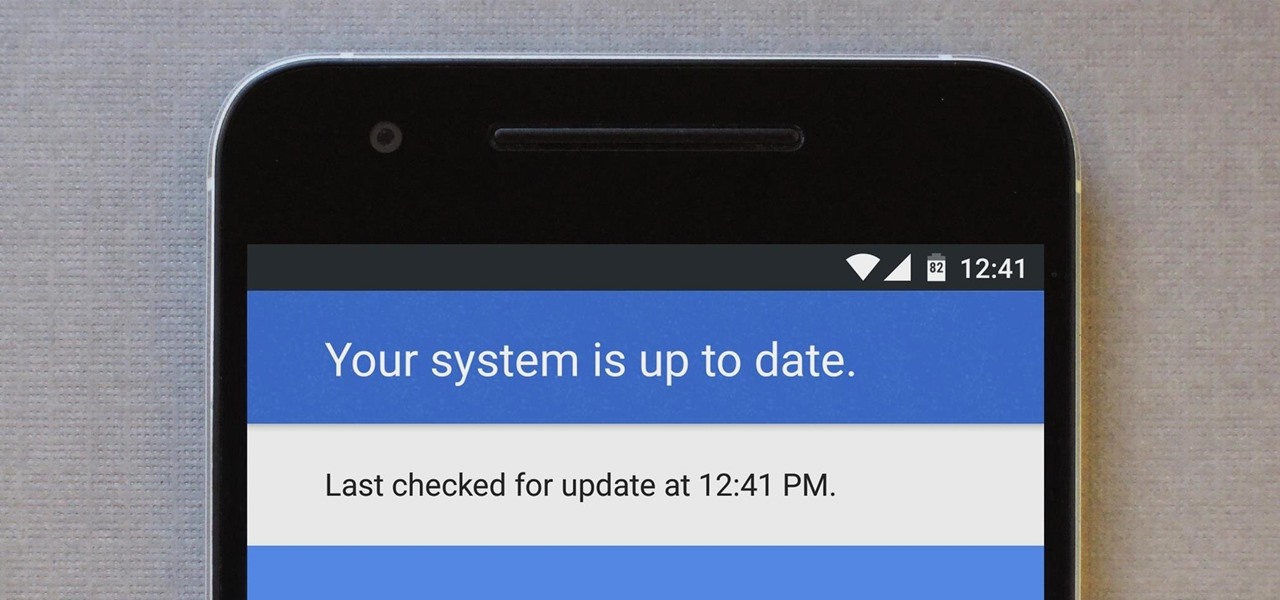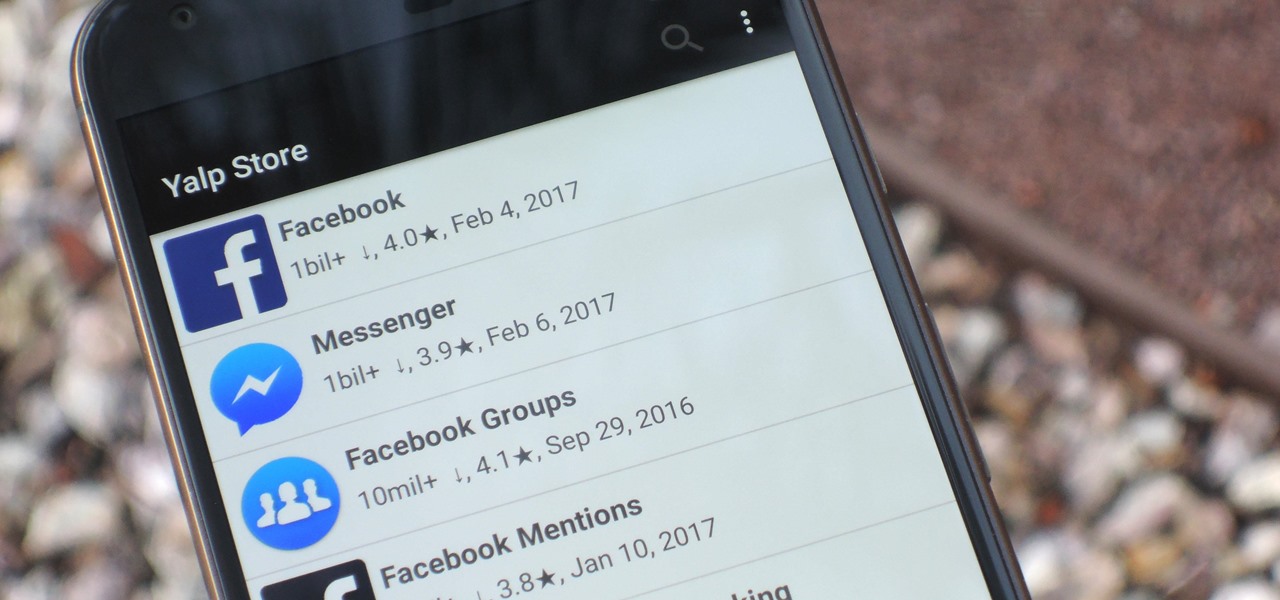
Android is Google's project, so of course you can see the search giant's fingerprints all over the operating system. Aside from the obvious user-facing apps, there's Google Cloud Messaging, Google Connectivity Services, and the much-maligned Google Play Services running in the background, to name a few.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Avian flu is making the news again with new human cases in China reported in January. What does "avian flu" mean to you—and how dangerous is it?

It's become a routine for many of us to ring in the New Year with pledges to finally get our budgets and finances under control. Unfortunately, it's also quite difficult to to keep those promises. Some of us will just dive into our resolutions and wing it as we move forward, which usually ends in failure. But even for those of us who plan carefully, obstacles along the way can spell doom for New Year's resolutions.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader is absolutely pointless, as having it locked will not hinder normal device usage, which is kinda true.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

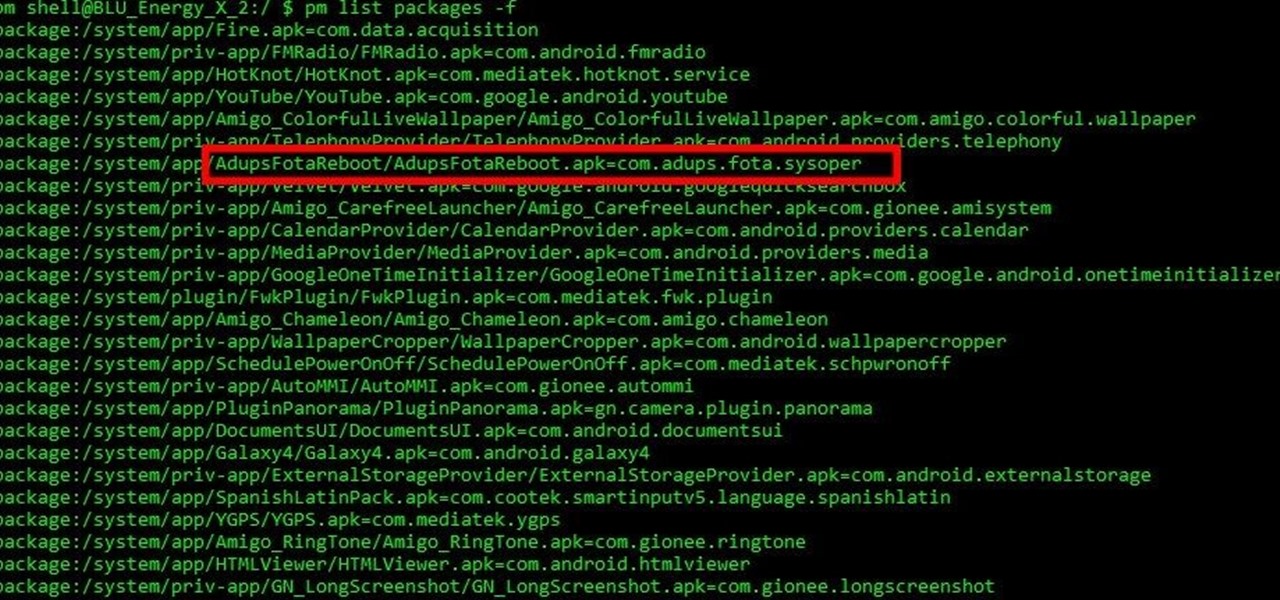
Mobile security researchers at Kryptowire recently uncovered spyware preinstalled on hundreds of thousands of Android smartphones by FOTA provider Adups which was gathering personally identifiable information (PII) such as call logs, app usage data, and even the full contents of text messages and sending these to a third-party server—all without the users' knowledge.

In this first part of my series on getting started with Windows Holographic, we are going to cover everything you need to get set up for developing HoloLens apps. There are many pieces coming together to make one single application, but once you get used to them all, you won't even notice. Now there are different approaches you can take to make applications for HoloLens, but this way is simply the fastest.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

There were some new hurdles to clear, and then there were a few more, but legendary root developer Chainfire has created a fully-functional root method for Google's Pixel and Pixel XL flagships. Like past devices, this method relies on the SuperSU ZIP, but now, there's an additional file that needs to be flashed in order to bypass issues with Android Verified Boot (AVB).

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

While it hasn't gotten as much attention as iOS 10, Apple's big 10.12 update to their Mac operating system is finally out for all to enjoy—and you can download it for free from the Mac App Store right now.

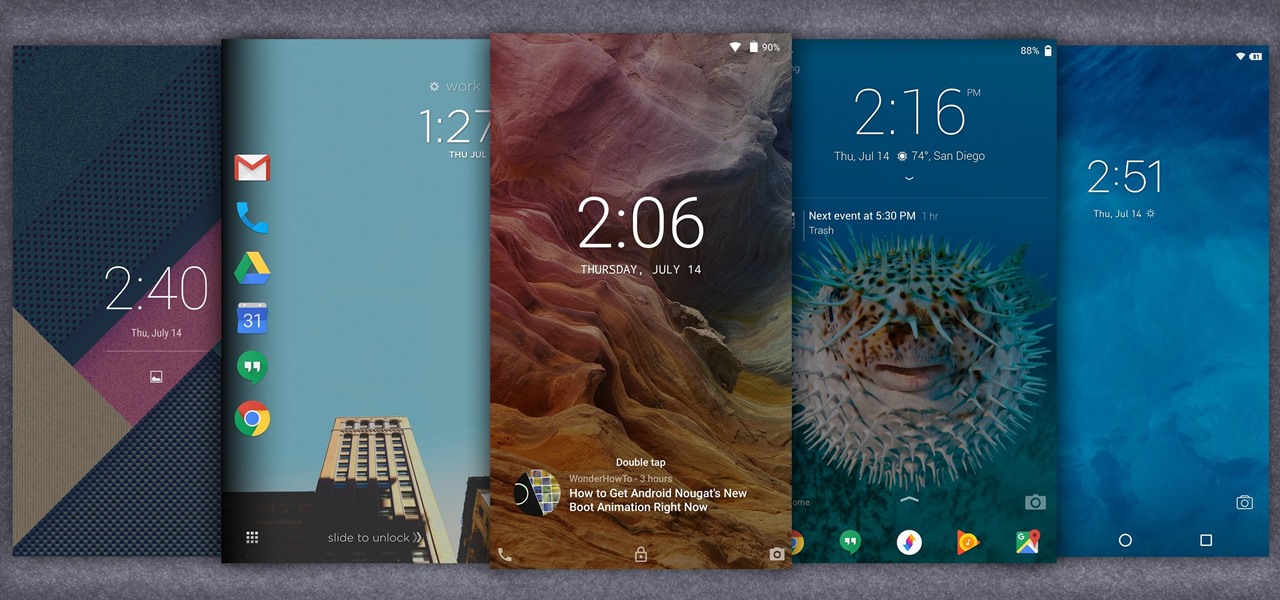
When it comes to customization, you just can't beat Android. Not only can you replace your home screen, switch your default apps, and apply icon packs, but you can even replace your entire lock screen by installing a simple app. Considering that the lock screen is the first interface you encounter when you pick up your phone, that last one might even be the biggest change you can make without root access.

If you want free Poké Balls and eggs when playing Pokémon GO, you can find them at PokéStops in variation locations around your city, which are marked with towering blue icons on your map. Once you're at Level 5, they'll also grant you Potions and Revives to help you in your battles against other trainers, so they're definitely something you should be visiting whenever you can.

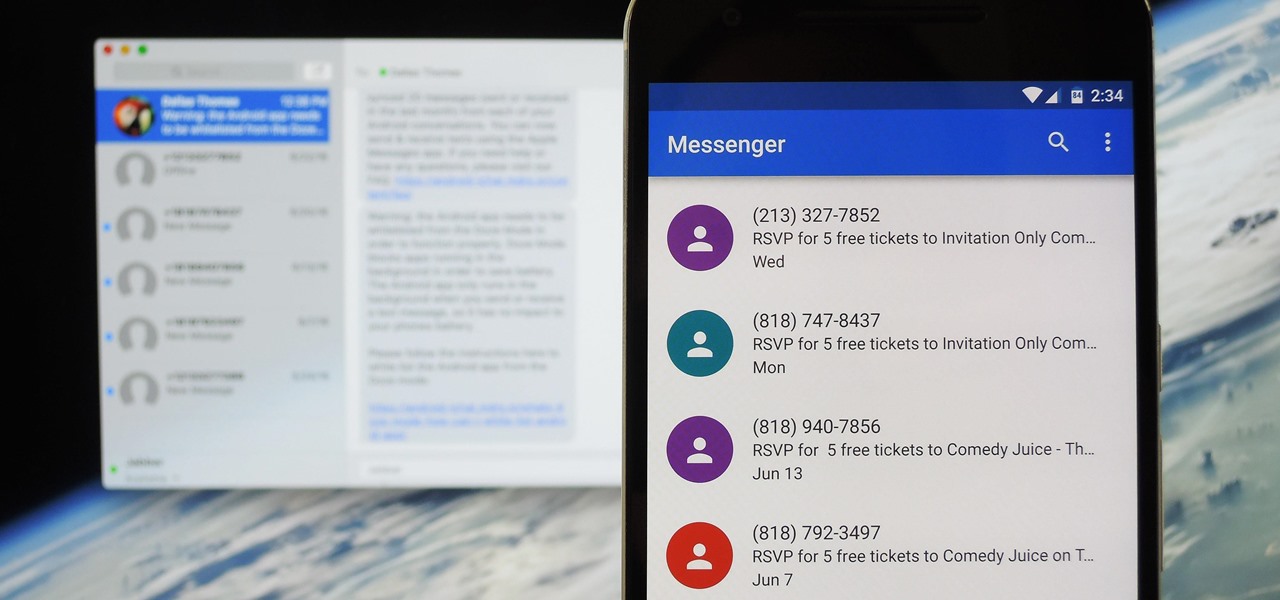
Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

I've been an Android user almost as long as the operating system has existed, so when I received my first iPhone in April, I felt like I was in a foreign land. Sure, it runs most of the apps I'm used to, and the phone itself feels about the same in my hand as any similarly-sized device, but everything else is just different.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Virtual reality is all the rage these days, especially with devices like the Oculus Rift, Gear VR, and HTC Vive hitting shelves lately. But before any of those fancy, expensive headsets ever made it to the market, Google came up with a thrifty and inventive substitute in the form of Google Cardboard.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Sometimes the best way to hide things is in plain sight. Whether you're trying to sneak some medication past security at a concert with a zero-tolerance policy, or you're just worried that maybe Omar comin', YouTuber MrGear has a clever way to put your mind at ease.

Samsung's 2016 flagship devices are some of the most beautiful, powerful smartphones ever made. And amazingly enough, thanks to legendary root developer Chainfire, the Samsung Galaxy S7 and Galaxy S7 edge are about to get even more powerful.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

On the list of problems with Android, manufacturer tinkering ranks near the top. Slow or nonexistent updates, poor performance, excessive bloatware apps—all of these things can be attributed to manufacturer skins like TouchWiz or Sense, and none of them are issues with unmodified, Vanilla Android devices like the Nexus series.

If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard dongle (receiver).

For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

Microsoft did a wonderful thing in 2015: for the first time, it was offering a free upgrade to Windows 10 for all current Windows 7 and 8.1 users. And, if you were lucky, the upgrade process was relatively simple and painless. There were, however, some questions after the everything was said and done.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

If you're reading articles in bed or scrolling through Facebook before trying to fall asleep, you'll spend much less time on your iPhone before drifting off into slumber as long as you're using the right display mode.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

After seeing the title of this post from me, you might be thinking, "Why did The Joker made another post on a topic on which we already have a nice sticky post?"

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.