One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.
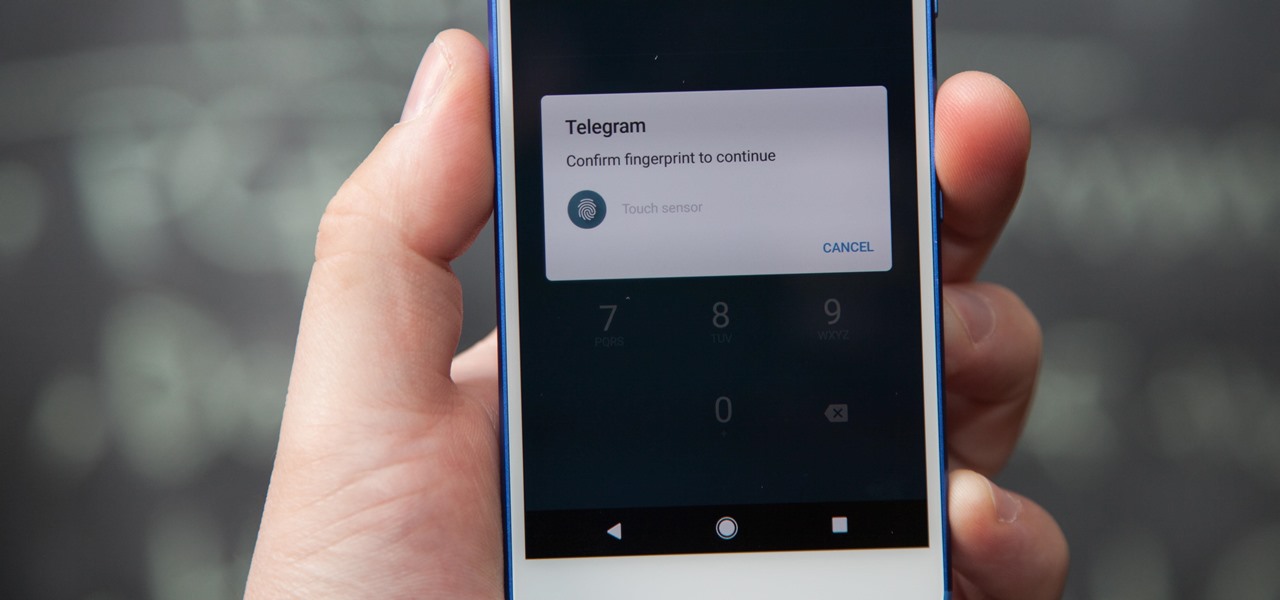
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

This is my first ever clothing haul video and I was so very excited about creating this video for sammydress - you might have heard of this company , who sent me this stuff for review purposes, hence the title "How to Wear the Same Top and Belt in Different Ways and Samydress Haul +Review "

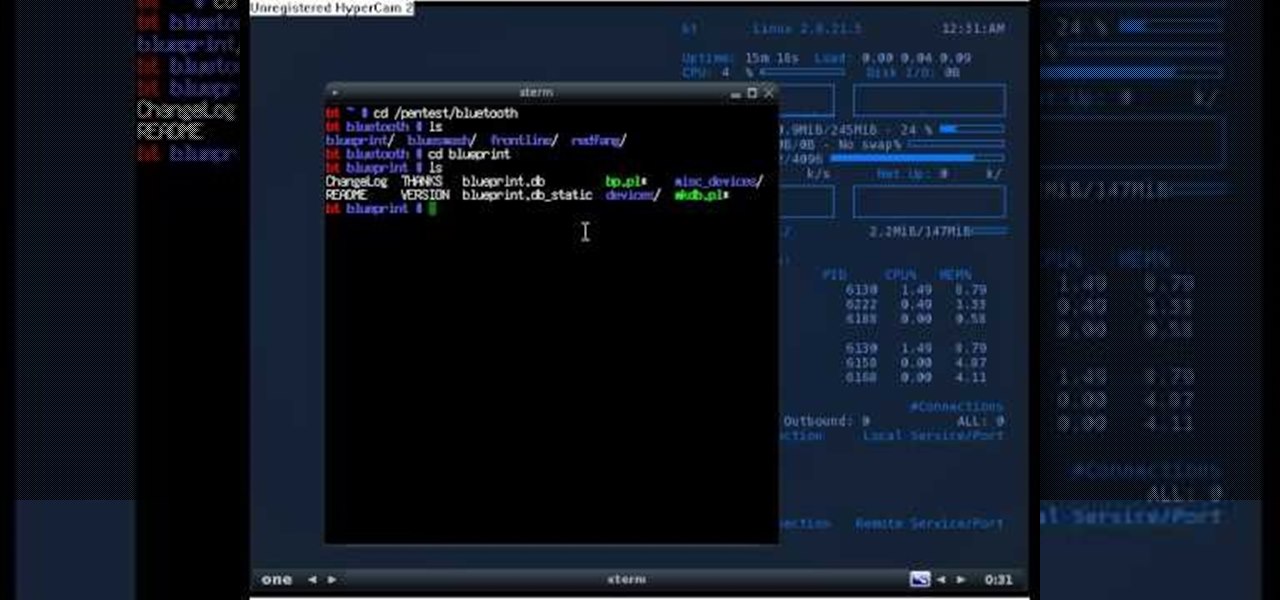
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

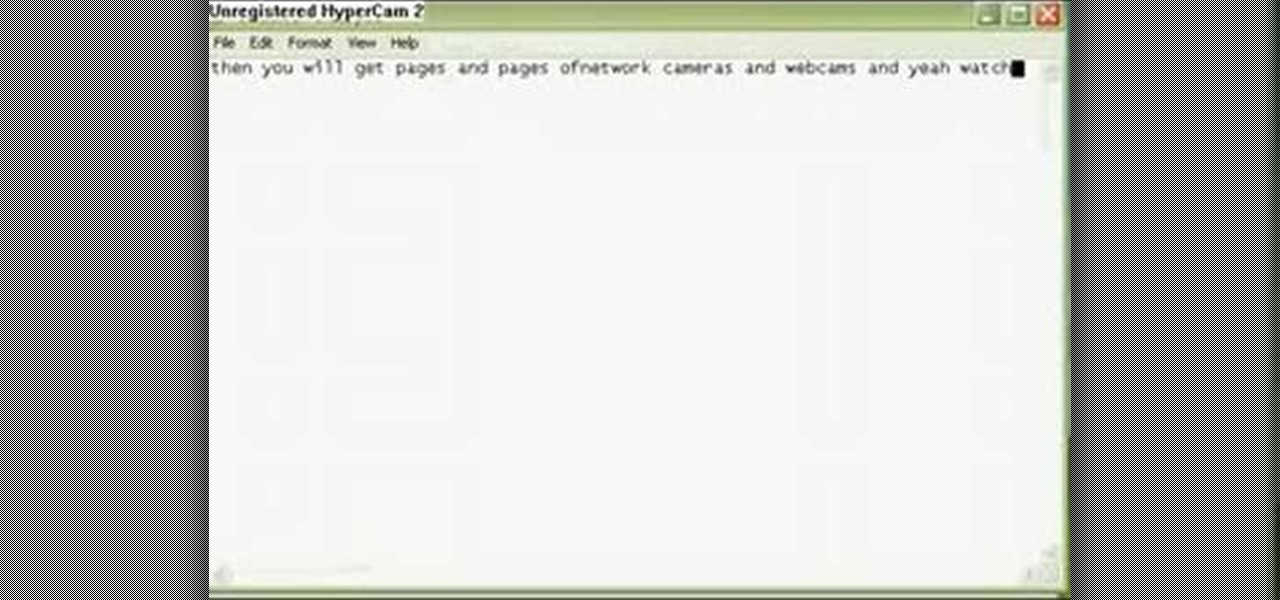
This tutorial will let you hack into a wide selection of web cams and online security cameras. The hack is actually quite easy, and is best done with a browser like Mozilla Firefox. Navigate to Google in your browser, and then type in "inurl:viewerframe?mode+refresh". This piece of code will open up a list of active webcams. Then just surf through your choices and watch whatever you want. You can even change the camera angle and zoom in and out of the picture!

Security is tighter than ever in U.S. airports. From the recent instigation of the hotly debated full-body scans and pat-downs to the TSA limiting every ounce of body lotion you bring, it's hard to make it through the security gates without some major airport hate.

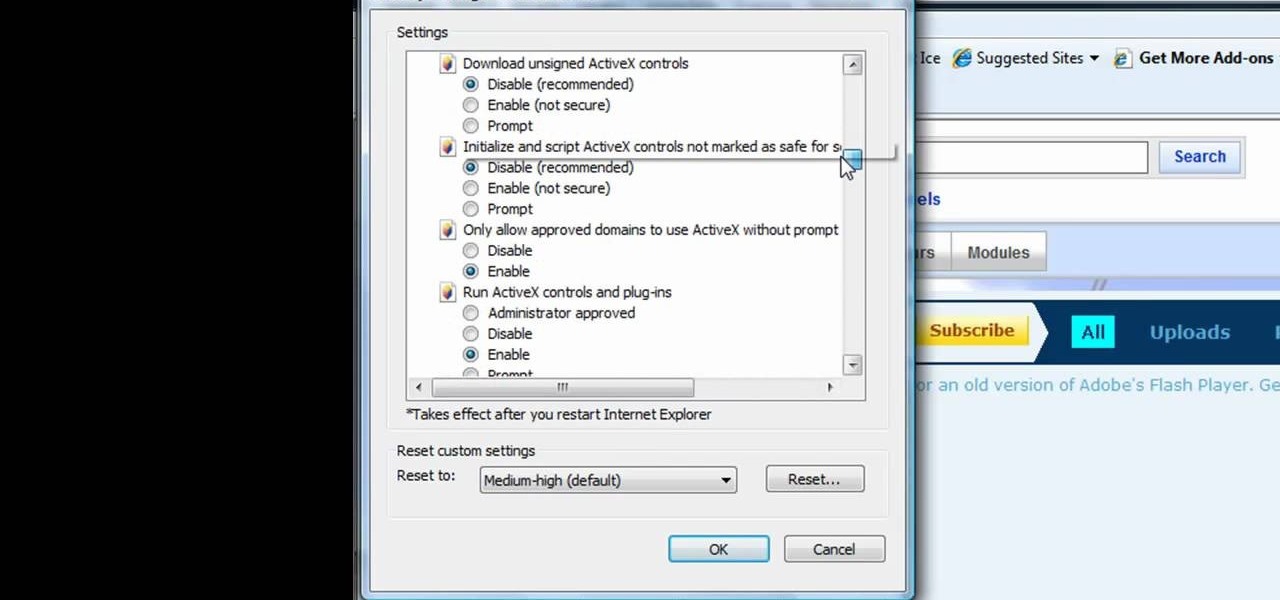
This tutorial shows us how to enable JavaScript in Internet Explorer. First, go to the top right of IE and click "tools". Then, click "internet options" and then go to the security tab. From here, select your security level that you want by clicking "custom level". Scroll down to the bottom and find the tab that says "active scripting" and make sure it's enabled. Click on "ok", then refresh the page that you are on. Now you should be able to watch videos and use anything that uses JavaScript ...

The difference between an amateur piece of jewelry and a professional one often lies in the details. Almost anyone can link chains together into a necklace and add small floral baubles, but the professional will take care to make sure the baubles are attached almost imperceptibly and the closure blends in with the rest of the necklace and also won't budge.

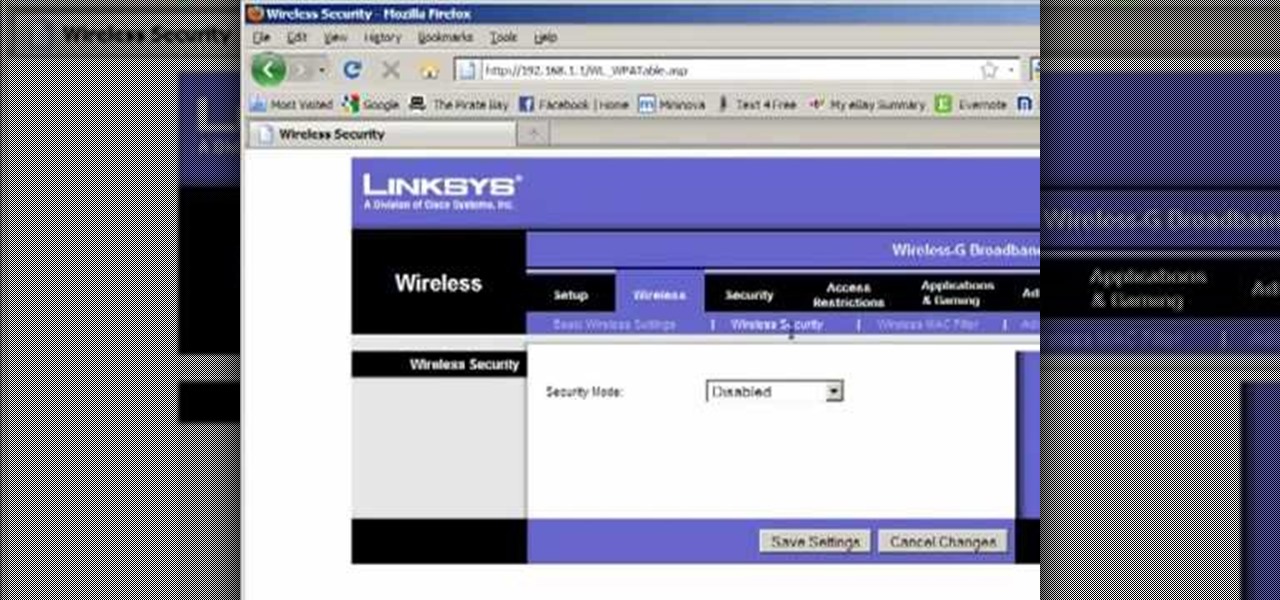
Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

Llewyn demonstrates how to configure your router for Wifi. Access the router by opening up your internet browser and typing in your router's IP address. That will bring up the router configuration page. Now, click on the wireless tab. You can set the wireless network mode to accommodate your computers. As a precaution, set the mode to mixed for greater flexibility. Set your wireless SSD broadcast to enable which will enable your wireless card to actually see the webpage and the internet. You ...

This video shows the method of getting past blocked sites and opening them using proxy servers. The method shown is useful when the sites are blocked using another site. In this case it is 'www.lightspeedsystems.com'. It can be done using proxy servers. In the case shown it is 'treesniff.com'. The URL is typed and we choose the option of 'Continue to this website'. Press 'No' for the security information. After this the page of the proxy server is displayed. Type the name of the website you w...

In this video TIAT shows you how to make a rescue belt. Begin by making a basic knot in the center, holding that knot on the top of your ring finger and between your thumb begin making loops. To create these loops extend the strand to the right side of the knot straight out parallel to your thumb, with your right hand curl the yarn first up, than forward, than back down forming a circle that you slid over your thumb. Take the tail of the cord and pull it snug. Repeat these circular loops unti...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to program a USB development board for cheap.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

In this video tutorial, you'll find a step-by-step guide to how a n00b hacker (like you?) can get usernames and passwords easily through one of the security flaws of the Ethernet ADSL router. More than half of Internet users never change their default password which makes this "hack" easy. Take your time to read the text on the slide. For more, and to get started testing the security of your own Ethernet ADSL router, watch this hacking how-to.

Notice: This is probably not new to many people. This *IS* new for some people however, and meant for them! Post interesting cameras you find.

A killswitch is exactly what you think it is: A switch that kills an operation in an emergency situation when the operation can't be shut down in the usual manner. It shuts your operation no matter what the consequences.

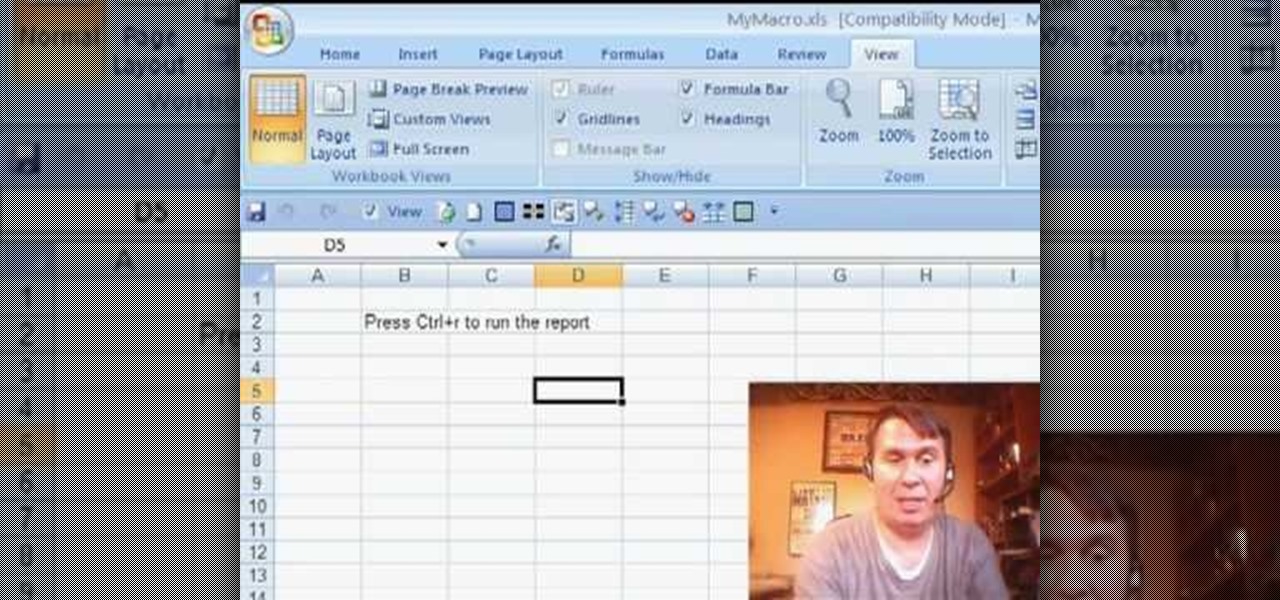
Some times when you upgrade your Microsoft Excel software to Excel 2007 your old macros may stop working. Some times this may be due to the settings and by enabling the macros you can get your old macros to work. Macros are turn off by default in Excel 2007. You can turn this on from the macro security settings. But the settings option is it self completely hidden. You cannot find it in any of the tabs present on the top of the program. Even the macros option present in the view tab has no se...

Got only a teensy amount of time before that Halloween bash and no costume in sight? Then check out this Halloween costume tutorial to learn how to quickly sew together a Greek goddess costume.

Check out this tutorial for some awesome techniques for the latest edition from Fight Night Round 4. In this clip, master some counter punch skills and it might mean the difference between holding the belt and holding your teeth.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Keep your possessions safe from thieves with these tips. You Will Need

Burglary is common, but is also quite preventable with these tactics. You Will Need

You don't need to don a garter belt and balconet push up bra to feel like a sexy, burlesque vixen. As not everyone can pile on the silk and red lipstick like Christina Aguilera, this cheeky nail look may just be the next best thing.

If you've ever wanted to make a homemade collection of karaoke songs or belt out your own version of Britney Spears over her own song, then this video might come in handy. Learn how to remove vocals from a stereo recording in Reason/Record with help from Reason expert, James Bernard.

This video shows how to tie a scarf three different ways. The first way to tie a scarf involves a square silk or chiffon scarf. Fold it and wrap it around your neck, then tie it to one side. This is like an ascot tie. The second way to tie a scarf requires a long scarf. Tie it around your waist like a belt, with the ends dangling down your side. This creates a scarf belt. Finally, choose a shorter scarf. Tie it around your head with the tie in the back. You can tie it over your hair. Or you c...

In this video Chuck Cook shows how to correct the push shot posture. He demonstrates that the correct posture for the shoulder should go down and out toward the ball which drives the club head around back to the left. To obtain this posture, stand with the feet shoulder width apart, the back should be straight up. Take the club handle and stick the end into your belt buckle with club head sticking straight out. Next extend the arms straight out keeping the club at the level of your belt buckl...

Richpin's Auto Care shows you how to replace the cam over seal on a GM 3.1L V6 engine. Once the vehicle is raised and is safely supported by jackstands, you'll be taken through the first step which involves removing the serpentine belt from the engine. After the belt is removed, the video shows you how to remove the splash shield in the wheel next to the engine, using the proper tool. Next you'll be removing the crank pulley using a pulley remover, allowing you to get access to remove the sea...

Learn how to tie a Heaving Line or Franciscan Monk's Knot - a practical and decorative knot used to add weight to the end of a heaving line, or to finish a Monk's belt rope ends. This is a fine knot for camping, climbing, sailing or Boy Scout training.