If you have children who are still your dependents and have been living in your household for at least half of the year, and have their own social security number, you can actually get a major tax credit with a simple worksheet. In this video you will learn the requirements for the tax credit and also how to fill out the worksheet and calculate your credit.

In this clip, you'll learn how to crack a WEP or WPA key on a GNU/Linux computer with GRIM WEPA. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.
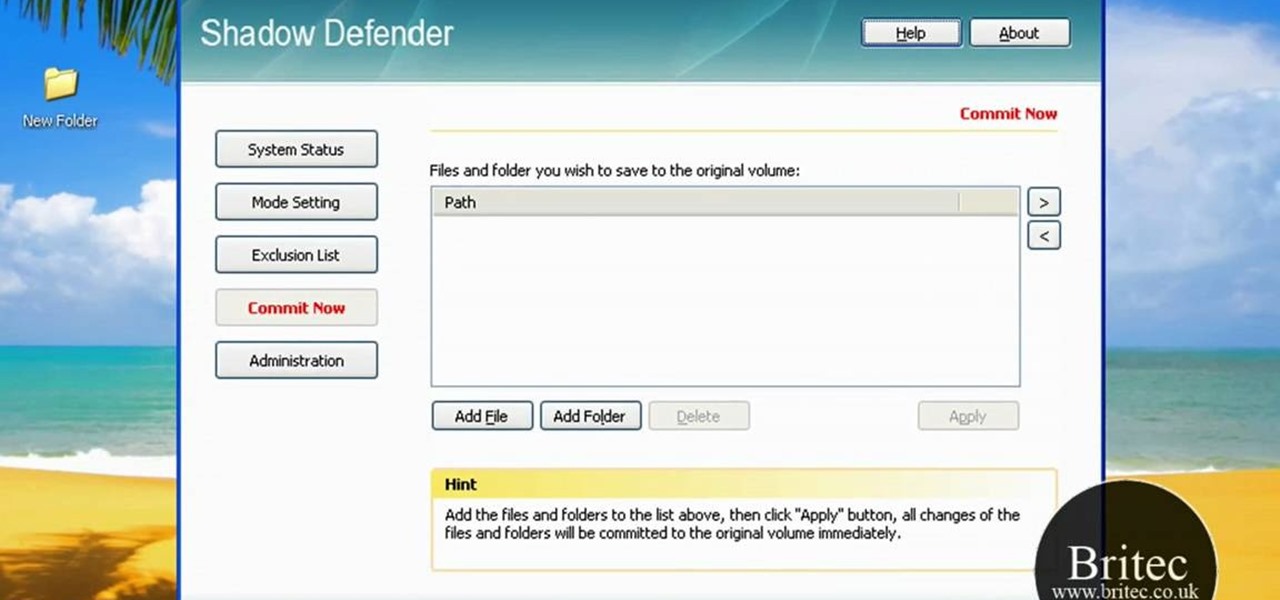
Looking for a security solution for your Microsoft Windows PC? With Shadow Defender, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under ten minutes. For more information, including step-by-step instructions on how to get started using Shadow Defender to protect your own desktop computer or laptop, take a look.
hether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 52.5th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about macro security. For more information on how to use macros safely, watch this free video guide.

Take a folder and organize documents based on the actions required. Actions:
What do you do with a password protected WinRAR archive? You hack it - naturally. And how do you hack it? First, download RAR Password Recovery v1.1 RC17 then follow along with this video to crack almost any WinRAR password. So much for security.

In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on an Oracle database. To see how to pop a shell from within Oracle or even perform a port scan from the database itself, watch this hacking how-to.

AccessDiver is a website security scanner. It incorporates a set of powerful features that will help you to find and organize vulnerabilities and weaknesses in your own site. This video tutorial presents a guide to its use. For more information, as well as to get started using AccessDiver for yourself, watch this video tutorial.

In this video tutorial, a CEH-certified Ethical Hacker will teach you how to exploit the old netbios remote IPC$ share while also demonstrating the beginning stages of a successful network security audit. For more

Did you know that field templates can be applied two different ways? And that the two "edit" buttons on the main interface tie directly into how these field templates are used? This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite discusses these topics and how to control such permissions through security roles.

There is a security flaw with any Apple iPhone running firmware version 2.0.2. This flaw potentially gives a person access to your email account and contacts when you have your iPhone locked. This video demonstrates a simple, but impermanent, fix for stopping others from accessing your private information. To protect your own Apple iPhone, watch this tutorial.

Dogs naturally want to have a den, so a crate gives him his own space. Puppies will get security and comfort from a crate. Because a dog will not want to go to the bathroom where they sleep, they won't make a mess in their crate, making it useful for housebreaking a dog. Watch this video pet care tutorial and learn how to crate train a dog.

In this how-to, Gary Rosenzweig of MacMost.com takes a look at best practices for making and storing passwords. You should have a different password for every account, for example, use secure passwords and store them in using a security utility. Learn how to store your passwords securely with this tutorial.

I explain how to view and control your computer from your iPhone/iPod Touch. This works over Edge and Wifi connection, but obviously the better your connection the faster it will go. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

This tutorial gives you a basic overview of how to build a Parabolic WiFi Booster that will increase you router's range as well as narrow the signal path for added security.

Professor of RVing, Jim Twamley talks about lock security and shows you how to replace an RV entry lock.

How to get around your school or home's computer security to view restricted webpages.

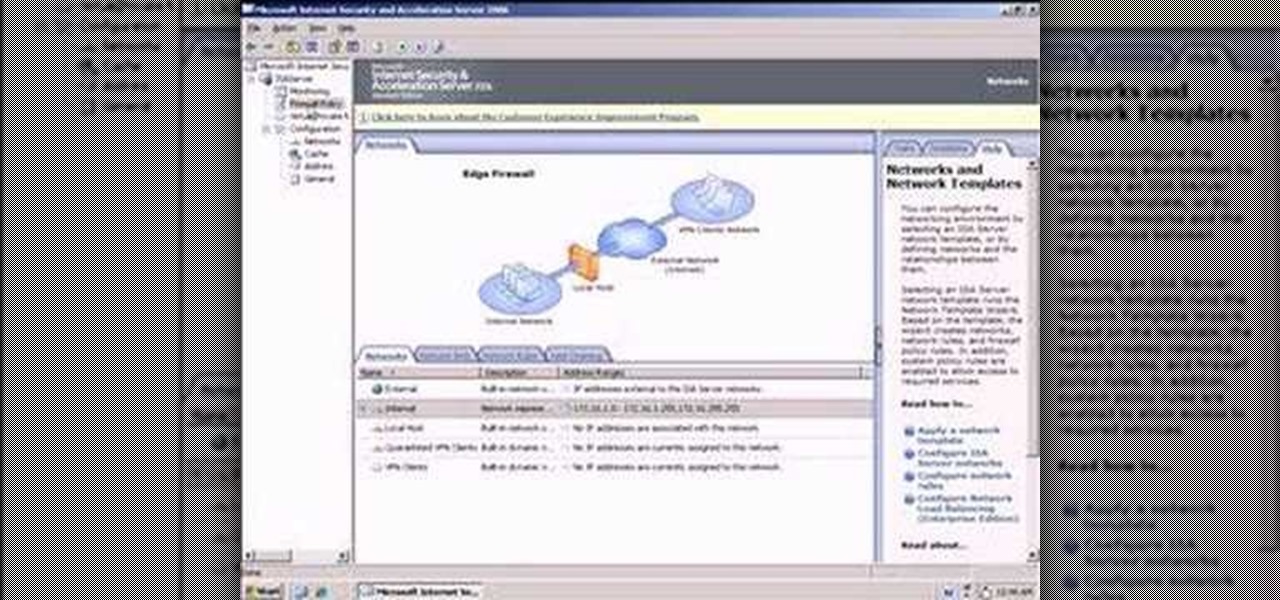
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

This Video demonstrates how to install multi channel (4,8,16) power supply for security camera and CCTV installation.

Watch this video to learn how to make a radio controlled camera rig that can tilt and pan like an expensive security camera. This is an amazing tool for movie making! Stick to your budget.

First of all you have to check the breast collar which is attached and hanged to the saddle. You have to maintain safety by not ducking under the horse neck. It is better for you to go around and do your job. Keep your head away from the horse head while attaching a collar. Ask your handler to hold the horse for you. Now pick your breast collar up and reach around the horse. Don’t duck under the horse head, but bring the collar belt to your side and then attach it to the ring on the saddle. N...

Before you go out to protest, understand what you are facing. Sometimes these demonstrations become infected with looters and rioters, which could mean interaction with law enforcement and potentially arrest. And if your phone is on you, it can be used as a tool against you.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

Ever since the iPhone X, Face ID has been the standard way to unlock your iPhone. For the most part, it works remarkably well and adds a layer of security that Touch ID can't match. That said, the tech isn't perfect. If you're finding that Face ID isn't working for you, there might be an iOS setting to blame.

One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it.

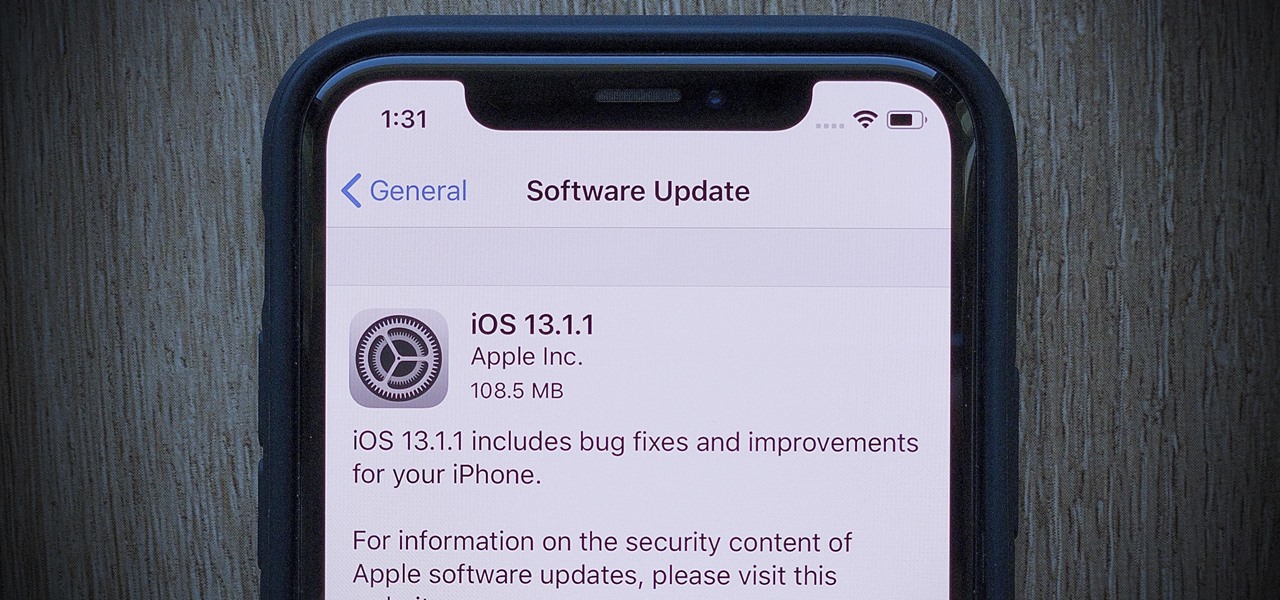
Is Apple trying to set a record for the highest number of updates within a two-week period? You wouldn't be blamed for thinking so. Just eight days ago, Apple publicly released iOS 13.0 for all compatible iPhones. Then, just five days later, Apple seeded iOS 13.1 with 22 new features to boot. Now, just three days into 13.1's tenure, Apple has released yet another update, iOS 13.1.1.

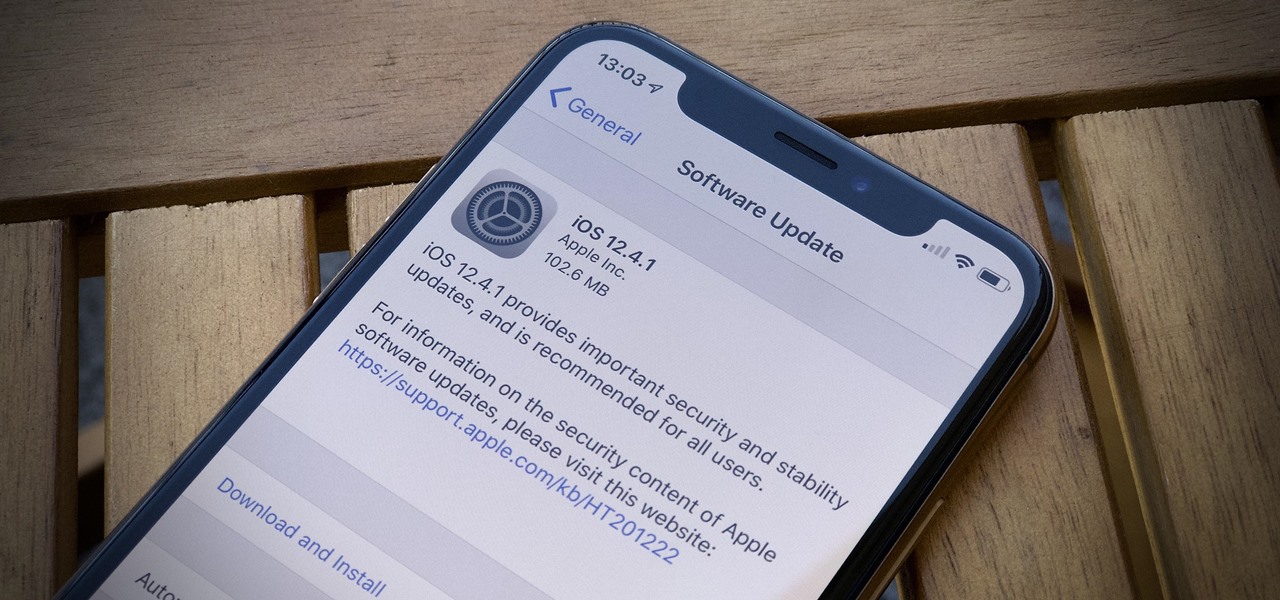
While all eyes might be on the next beta release for iOS 13, Apple is still pumping out updates for iOS 12. The company released iOS 12.4.1, the first update since iOS 12.4, on Aug. 26. The latest update includes a patch for the jailbreak vulnerability recently discovered in 12.4. One month later, on Sept. 26, iOS 12.4.2 came out for older iPhone models.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

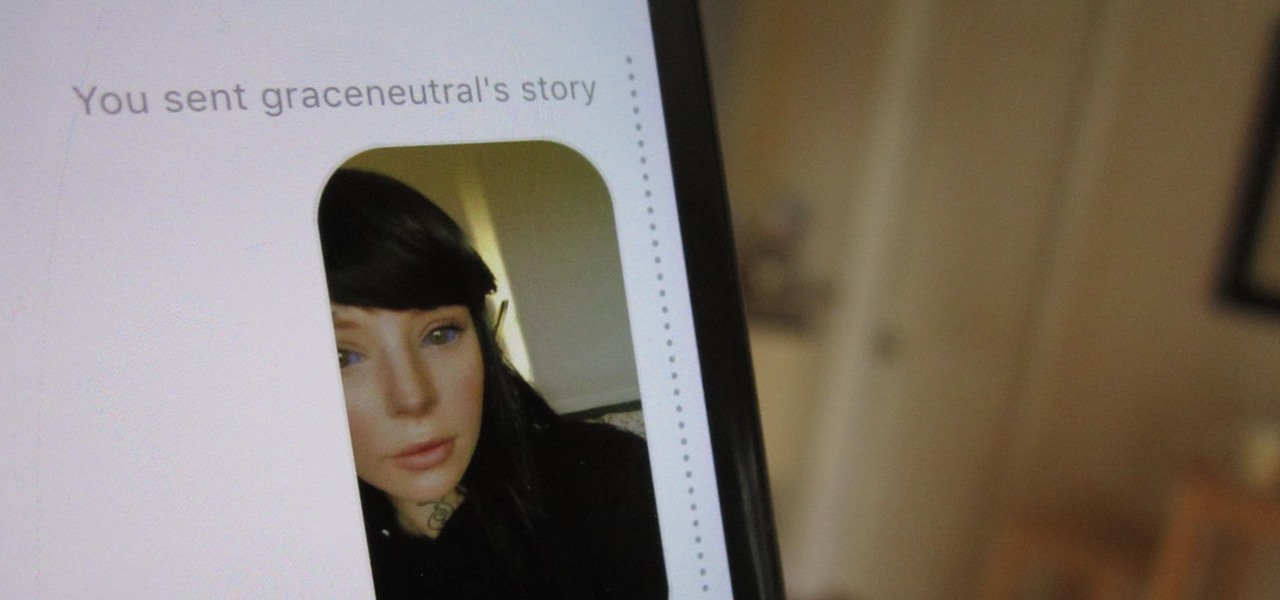
Instagram introduced a new feature in September 2018 that lets you share other users' Stories via Instagram Direct, the app's private messaging tool for solo and group messages. Problem is, it works both ways, so whenever you add to your ephemeral Story, everybody that sees it can share it directly with anyone else.

Get ready for more software testing. Just two days after the official release of iOS 12.1, Apple seeded public software testers iOS 12.1.1 — one day after developers received the update. While the rest of the iOS world is just getting to know all of the cool, new 12.1 features, testers are now sinking their teeth into what the next iteration of iOS has to offer.

While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Your email is just that — yours. You shouldn't have to worry about other people gaining access to it on your iPhone. Fortunately, Outlook agrees, and has included a way for you to protect your messages with one of two keys no one possesses but you — your face or fingerprint.

T-Mobile has just pushed out a new update to the Samsung Galaxy Note 8, bringing the build number to N950USQU2BQLA. Here's what to expect.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

A four-digit passcode is what protects your iPhone, and the sensitive material within it, from strangers or nosey friends. Four digits are the only thing preventing someone from snooping through your pictures and posting them online for the public to see, and that's if you even have passcode security enabled.