When you decide its time to retire, you will most likely need to cash in your Social Security benefits. In this official two part tutorial, presented by the American Social Secuity Administration, learn exactly how to use their website and apply online. Applying online is very easy, and takes a lot less time than applying in person. By applying online for social security, you will bypass all of the long lines and waiting that usually happens in one of the offices. Plus, you won't ever have to...

Airport security lines are one of the biggest hassles involved in air travel. Navigating them quickly and successfully can be the difference between making your flight and not. This video offers some tips for how to get through security quickly, including buying airport-security-friendly luggage and packing said luggage in an easy-to-inspect way. Also, don't wrap any gift, as security may want to unwrap them!

Home security is as important as having a job. You have to protect your family and your valuables. If you can't afford a high tech security system, then maybe a fake security camera will do the trick. This security camera dud is also a cheap alternative for a film prop. Watch this video tutorial to learn how to build a fake cardboard security camera.

Airport security keeps getting stricter and more time-consuming. Shorten your time in the security line with these tips. Watch this video travel tutorial and learn how to get through airport security.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

This beauty video demonstrates how to do a MAC danger zone makeup look: red and black .

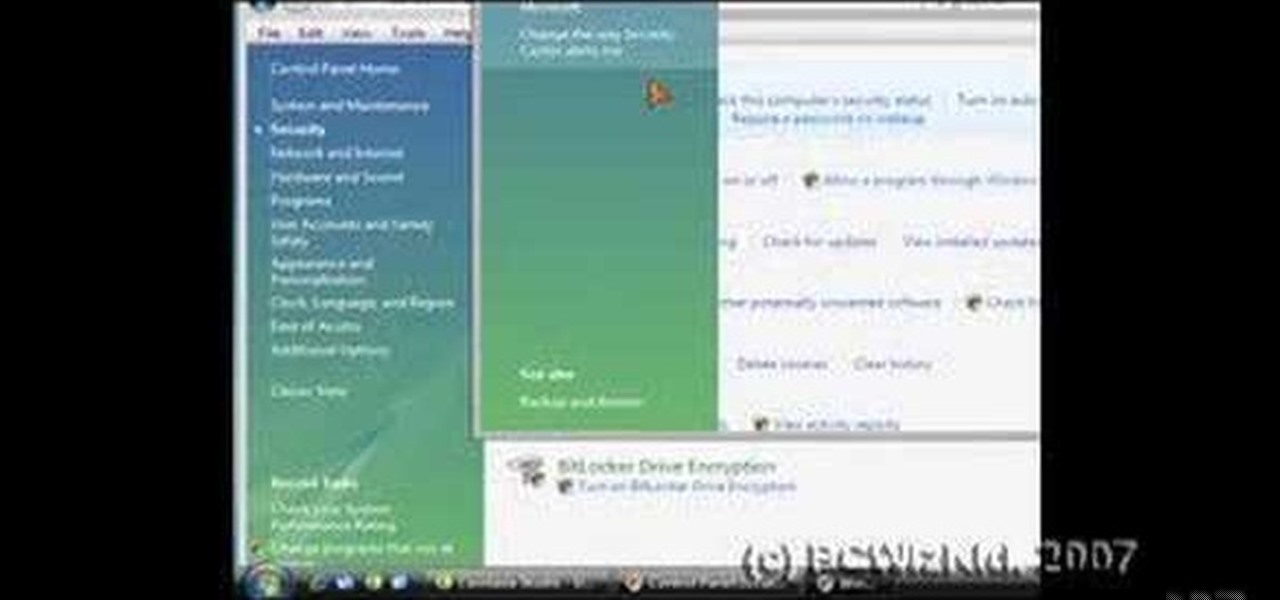
Windows Vista is jam-packed full of new security features, which could be a good thing, but they're just so obtrusive it's not really worth it. If you want to learn how to stop all of the annoying security alerts, this video will walk you through the process of disabling these security notifications in Windows Vista.

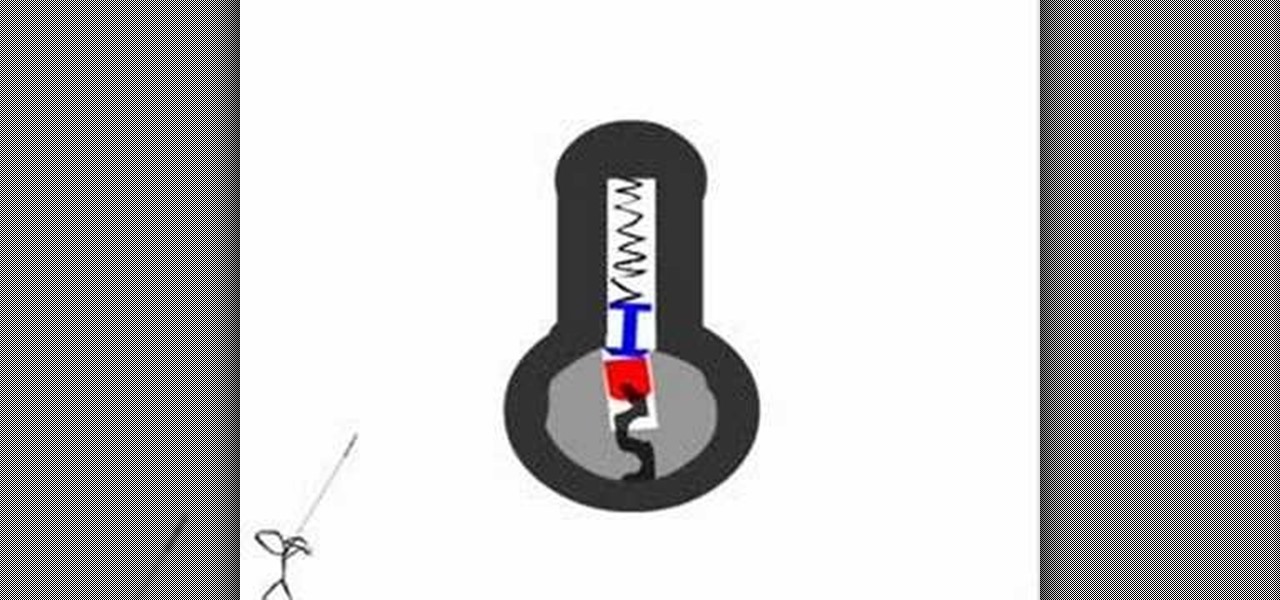
Lock picking can be difficult with some security features. This instructional video shows you what happens when you encounter them and what to do. Break into a lock when you've forgotten your keys, but please don't sneak in anywhere you don't belong. Watch this video lock-picking tutorial and learn how to detect security pins.

With the new screening protocols and their full body x-ray scanners, the TSA is taking constant criticism from unhappy travelers. Between the nude images the scanner produces and the awkward pat downs, air travel will never be the same. That's why it's important to make sure you're prepared for your flight and the TSA security checkpoints.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Installing security lights outside of your home can make for a great addition, but they also create new problems with regards to maintenance and cleaning. Having lights outside exposes them to all of the elements that mother nature can throw at them. This video will show not only how to install security lights, it will also show the proper measures to take so they will keep working with minimal maintenance and care.

This is a lock picking video which demonstrates how to pick a tumbler lock. Of course the only way to really open locks is to practice. But this is the basic info to picking locks. This lock picking tutorial also covers security pins and clear instructional animations to demonstrate. Learn how to pick a lock and use this video to understand lockpicking, security pins, skill tension, and bump keys. See all about how to pick a tumble lock & understand lock security pins.

In this clip, you'll learn how to quickly set a security pattern on an LG Droid Ally Google Android smartphone. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started setting up your own security secreen, watch this helpful video guide.

Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to configure the features in F5's FirePass v7 SSL VPN Endpoint Security. Peter Silva shows some of the new Endpoint Security features in the recent FirePass v7 release. Watch how to create policies, enforce host checks and other protective measures for your Remote Access deployments. For more information, and to get started configuring your own installation of FirePass v7, take a look.

If you live in a hurricane prone area, it is a good idea to protect your windows with security film. This video will teach you how to install hurricane security window film on your own and protect your home and assets.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to bypass security wafers when lock picking.

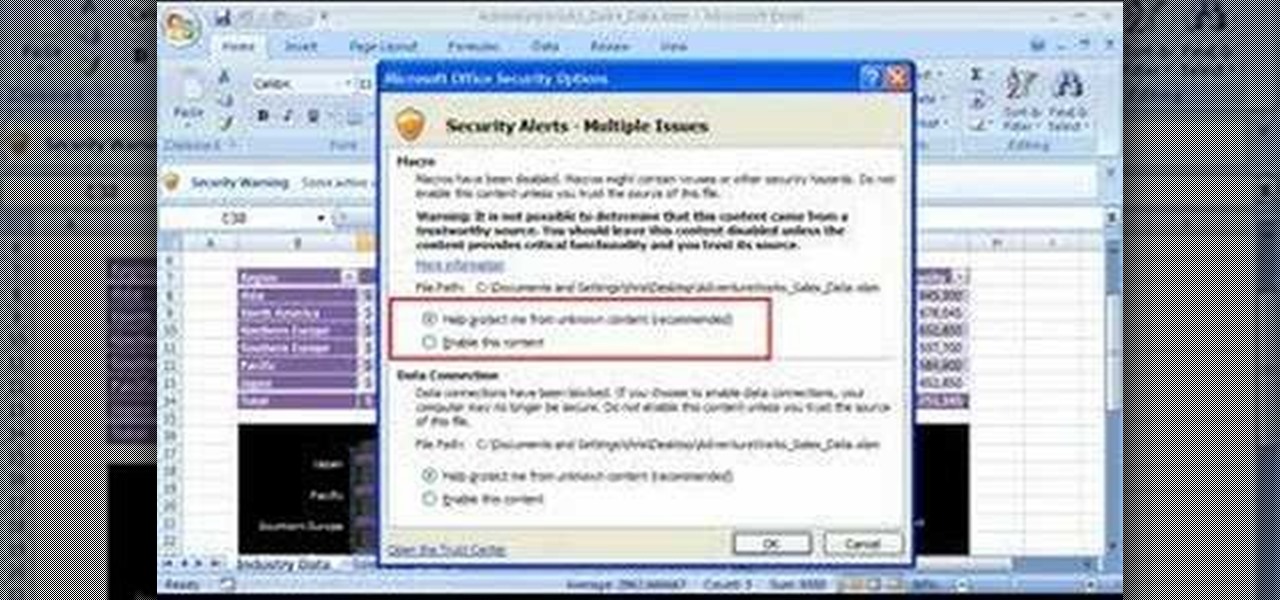
Not sure what to do when you get a security warning about a macro? What are macro security settings, the Trust Center, and Trusted Locations anyway? Watch this instructional video to learn how to enable macros and make informed security decisions that can help you keep your computer safer while you work in Microsoft Office Excel, Outlook, Word, Publisher, PowerPoint, and Visio 2007.

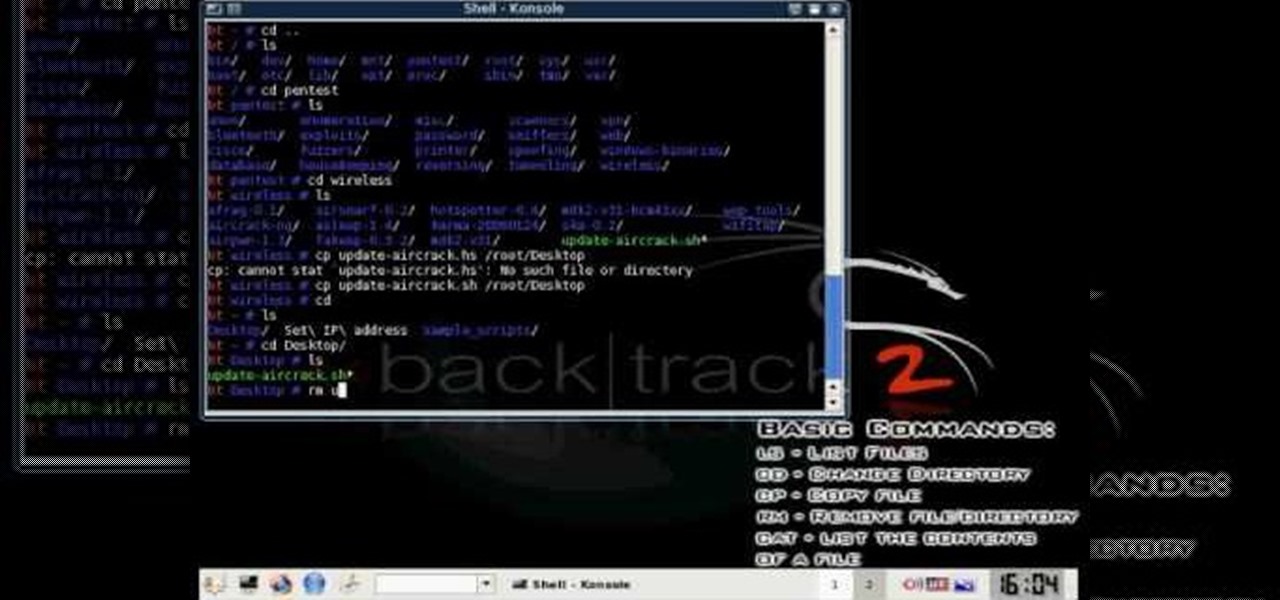
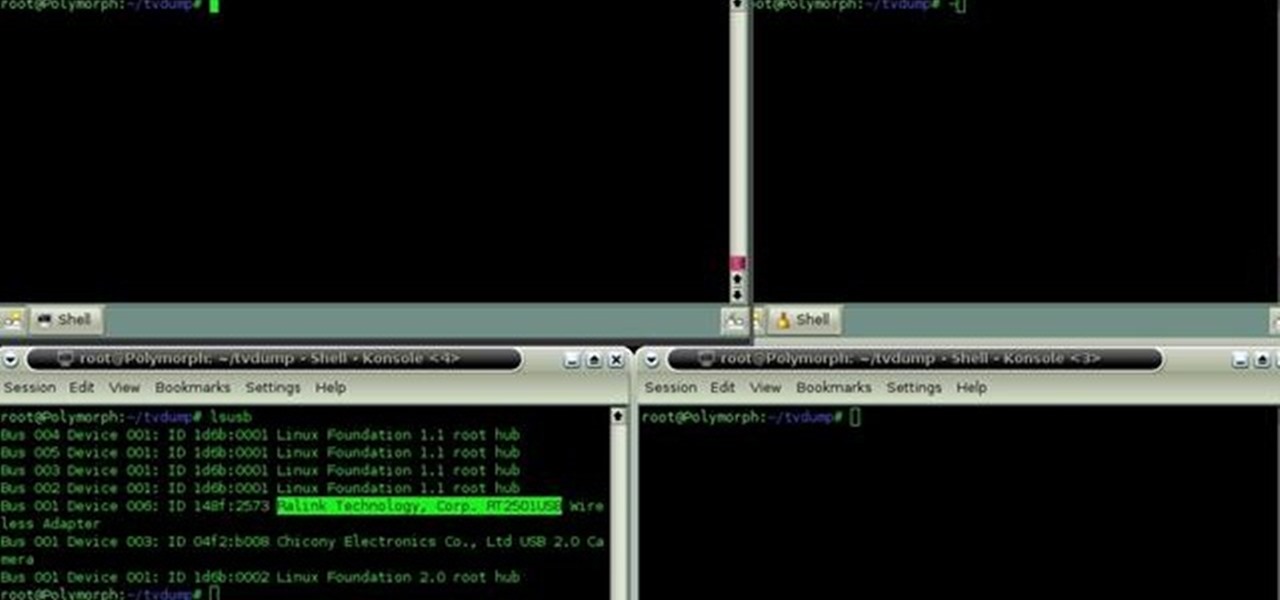
A basic tutorial from InfinityExists.com on using Backtrack - the Linux-based security software package. This tutorial covers: Where to get Backtrack 2, How to burn an .ISO file, How to boot Backtrack 2, How to login, and start the GUI interface. It also illustrates basic Linux commands, and how to set up your Network Interfaces.

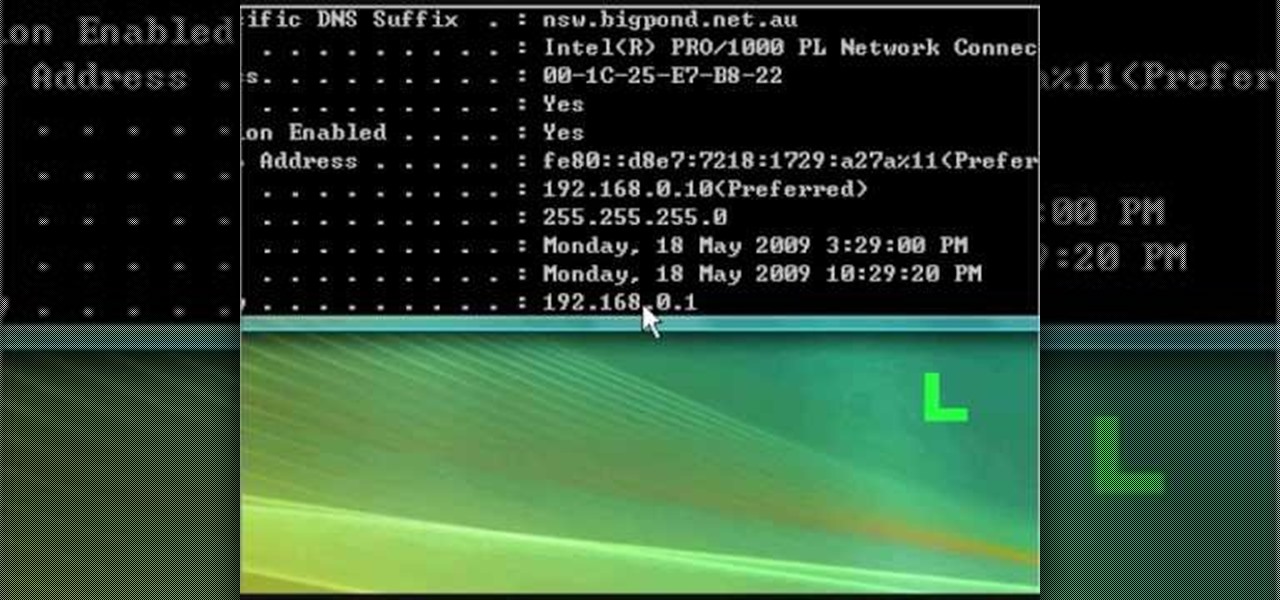
In this tutorial, we learn how to fix security mode for nds Wi-Fi. First, open the command prompt in Windows. Next, type in "ipconfig/all" in the black window that appears. After this, copy your default IP the screen just gave you, then type it into your address bar online. After this, you will be able to log into your security account and make default changes you prefer. Change different station accesses and any other security preferences you want to change. After this, you can change your p...

Having security setting on your web browser is a pretty important tool. It keeps you safe from potential hackers and makes sure you don't visit unsafe sites that could lead to a virus. But sometimes the security settings on a web browser can be a pain and the best choice would be to turn it off. So in this tutorial, you will learn how to easily change the security settings to INternet Explorer 8. So sit back and enjoy!

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

If you remember who Danger Mouse is, you may be considered old in some books. Danger Mouse was a secret agent has had an eye patch on his face and a weird looking partner. He would always face off against other animals like birds and snakes, but in the end would always save the day. So, if you're interested in going back through time, this tutorial will show you how. The video shows how you can draw Danger Mouse using some helpful tips. Good luck and enjoy!

A lot of commonly used household items are actually poison for your furry friends. In this clip, learn all about which items can pose a danger for your dog or cat. It's not only chemicals that are bad for your pets, innocent seeming items like fruit, veggies, chicken bones, chocolate, human medications and many other hidden dangers exist as well.

Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to pick a Brink's high security lock.

Have you ever been the victim of theft? It sucks. Why would these lazy scumbags rather steal from us than work hard like everybody else?

Video tutorial showing how to make your own solar-powered wireless security camera using an off-the-shelf solar panel and any wireless webcam. See creator site for more detailed graphics.

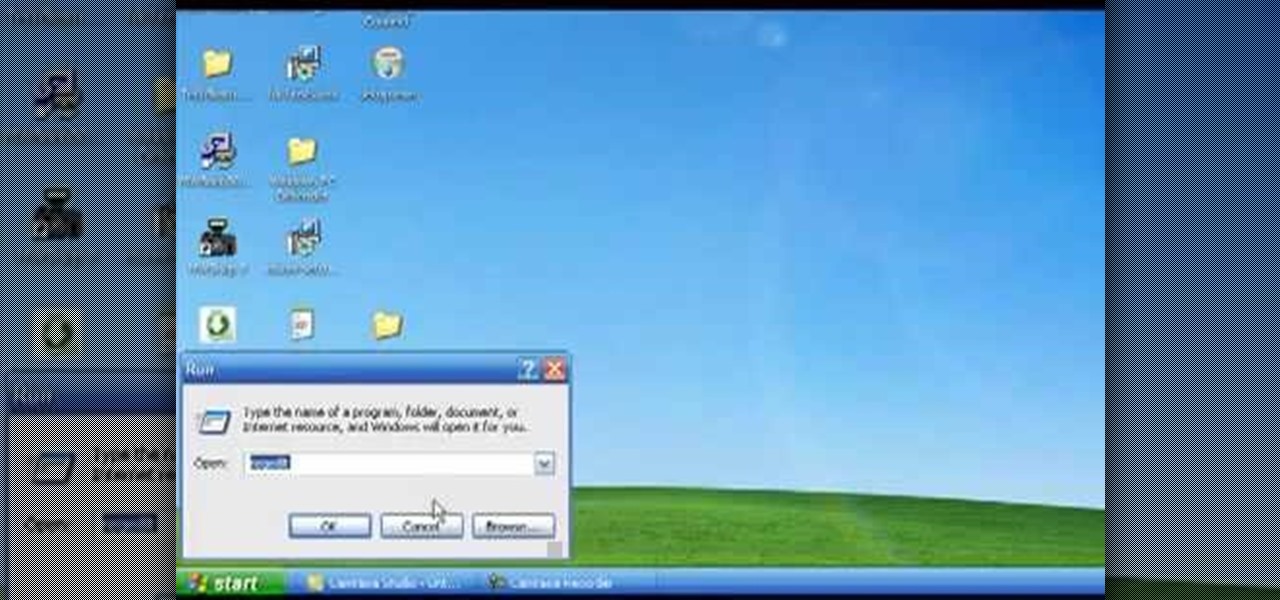
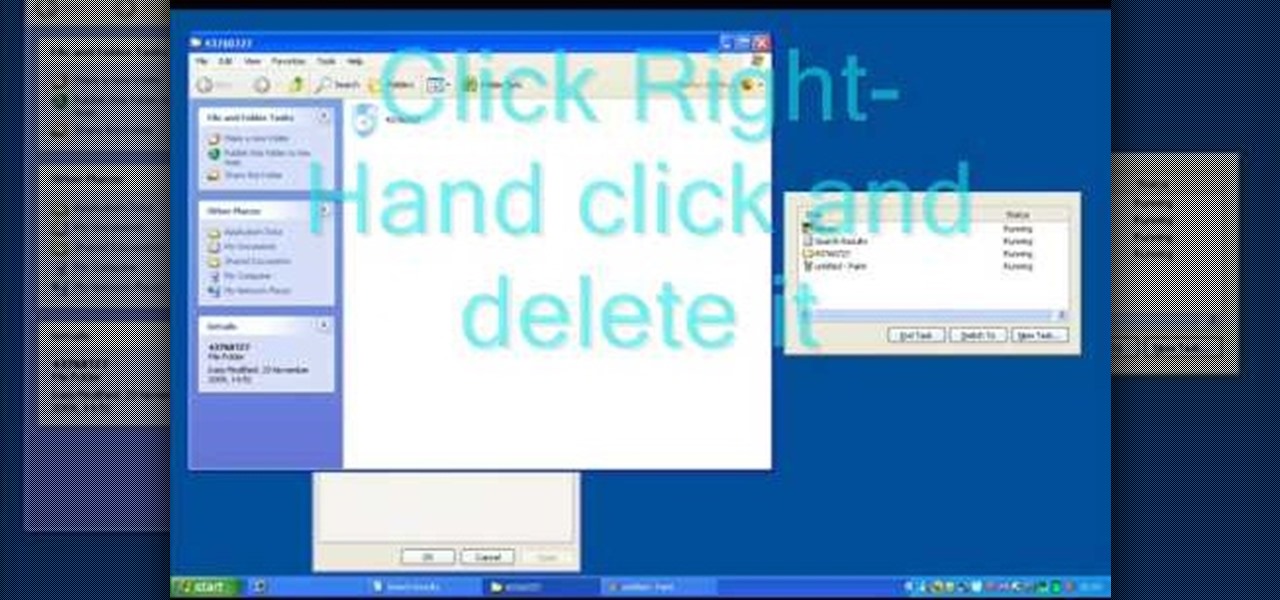
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

Today is the day before Thanksgiving. It's also the BIGGEST travel day in North America. Everyone is taking flights home to their family and friends for a nice Thanksgiving dinner. But this holiday will be one to remember thanks to the TSA.

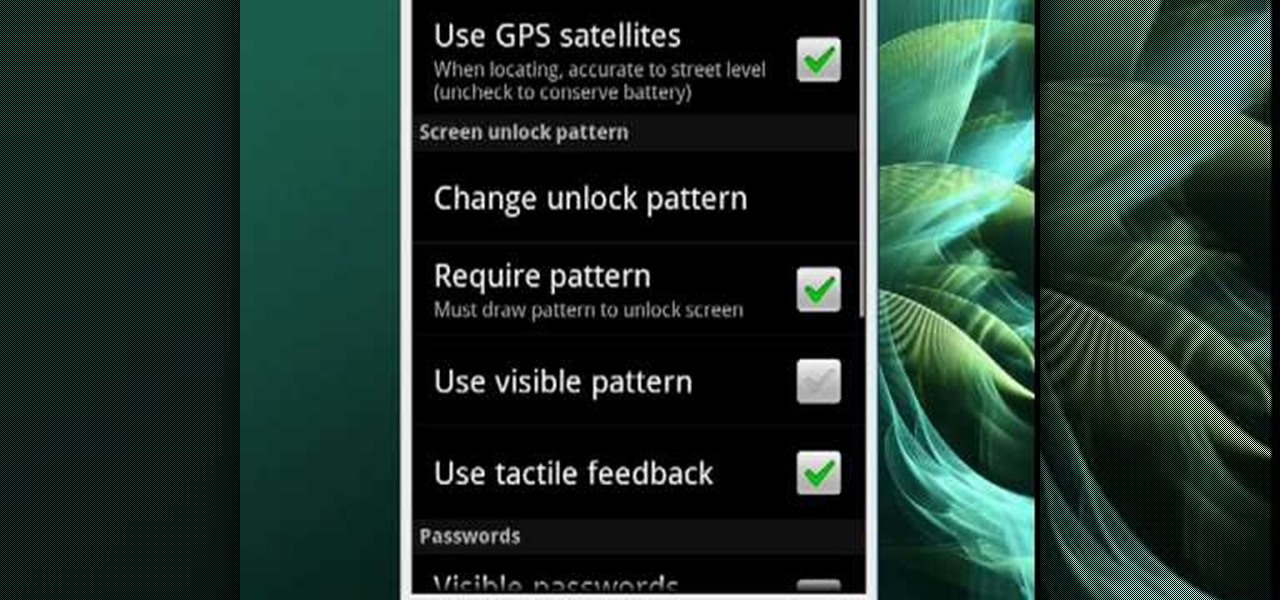
In this video tutorial, viewers learn how to change the lock pattern on an Android phone. The lock pattern allows minimum security on the phone to prevent other people from tampering with your mobile files. Begin by going into the Settings and click on Location & security. Under Screen unlock pattern, select Change unlock pattern. In order to change the unlock pattern, users will have to type in the current unlock pattern. Now type in the new unlock pattern and press Continue. Then retype the...

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Watch this video tutorial, and learn how to turn an ordinary inexpensive webcam into a hidden home security system, viewable anywhere in the world from your cell phone! With a cute and cuddly teddy bear and a cheap webcam, you can make the perfect homemade security camera, or just a camera to spy on your sister and her friends during sleepovers. Follow along with the steps in this how-to video and learn how to set up this spy system. Note: this video is NOT recommended for people who are perv...

By DevonLocks.Com - Security pins can be a pain. This video shows you how to bypass them. See our other video on how to spot them.

If you own the Galaxy S8, S8+, or Note 5, be on the lookout for a new security update. These Samsung devices are the latest to receive the December security update to patch issues from both Samsung and Android.

In this video, we learn how to remove Security Tool the simple way. Most ways will not remove this from your computer, but this way will. To start, you will need to restart your computer. After this, press ctrl+alt+del the moment Windows shows up. Then, go to the Task Manager and look through the programs that are open. When your security tool opens, press the same buttons to get the mouse free. Then close the security tool from the Task Manager. Now, go to your desktop and press on the icon ...

In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.