Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.
There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

There's nothing more inherently awesome than looking up into the stars and wondering WTF is really out there. Outer space is one of those rare items that a Google search cannot provide all of the answers for.

After everyone updated their shiny Apple devices to iOS 6 a few months ago, they were shocked to find that their beloved YouTube app was missing. As it turned out, Apple decided to kick YouTube off their list of pre-installed stock apps. The new YouTube app (found in the iTunes App Store) is definitely better than the native one from iOS 5, but it's lacking a direct upload to YouTube option. Sure, you could upload videos from your iPhone's Camera Roll, but the options are limited as to what y...

Tired of the Instagram wave? If you're sick of having to view the world through low-contrast and sepia-toned filters, there's a way to get them back to how they're supposed to look, and it's called Normalize, which undoes the magic filtering that Instagram and similar photo filter apps provide. The process of un-Instagramming your (or anyone else's) photos with Normalize is perhaps easier than Instagramming them in the first place. All you need to do is copy and paste them into the app and wa...

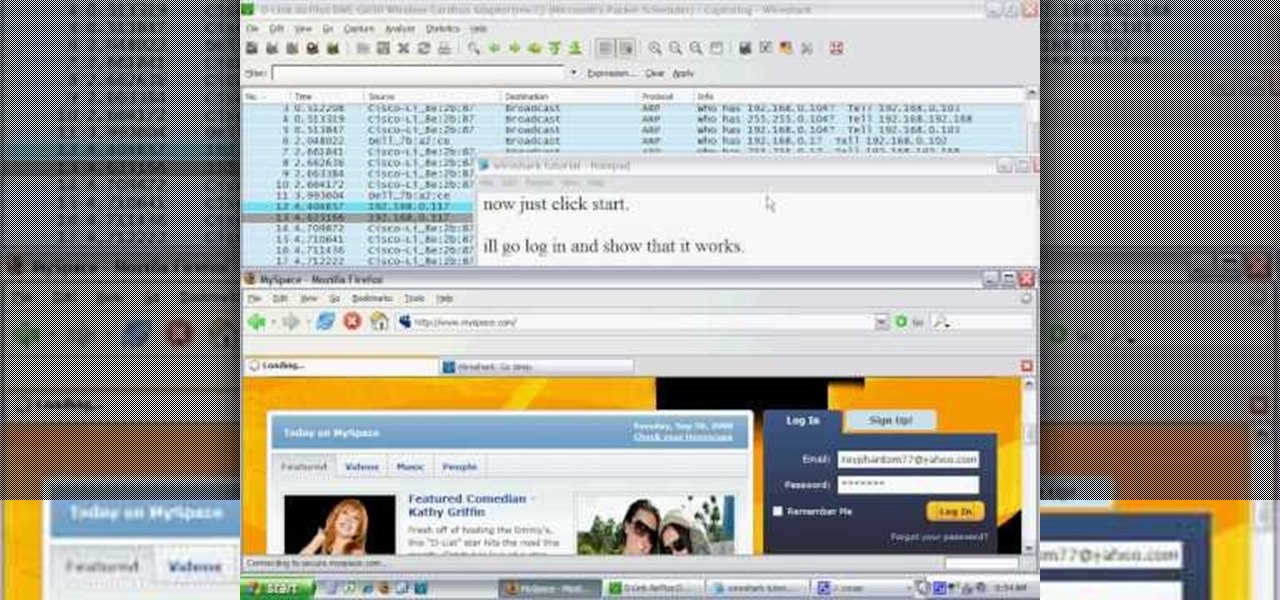
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only doing it to test a network's security, or for your own educational purposes. Check out the video, follow the steps and see how secure network is. Hack, hack, hack!

If you've recently upgraded you doorknob to an elegant Schlage Plymouth Handleset, then it's time to match your front entry locks and install a new electronic high-security Schlage Plymouth Keyless Entry Deadbolt. This keypad is great if you never want to lock your bottom handleset (or doorknob). Watch this step-by-step installation video to see how it's done! You'll need a phillips head screwdriver or electric drill. To see how to install the matching handleset, click here.

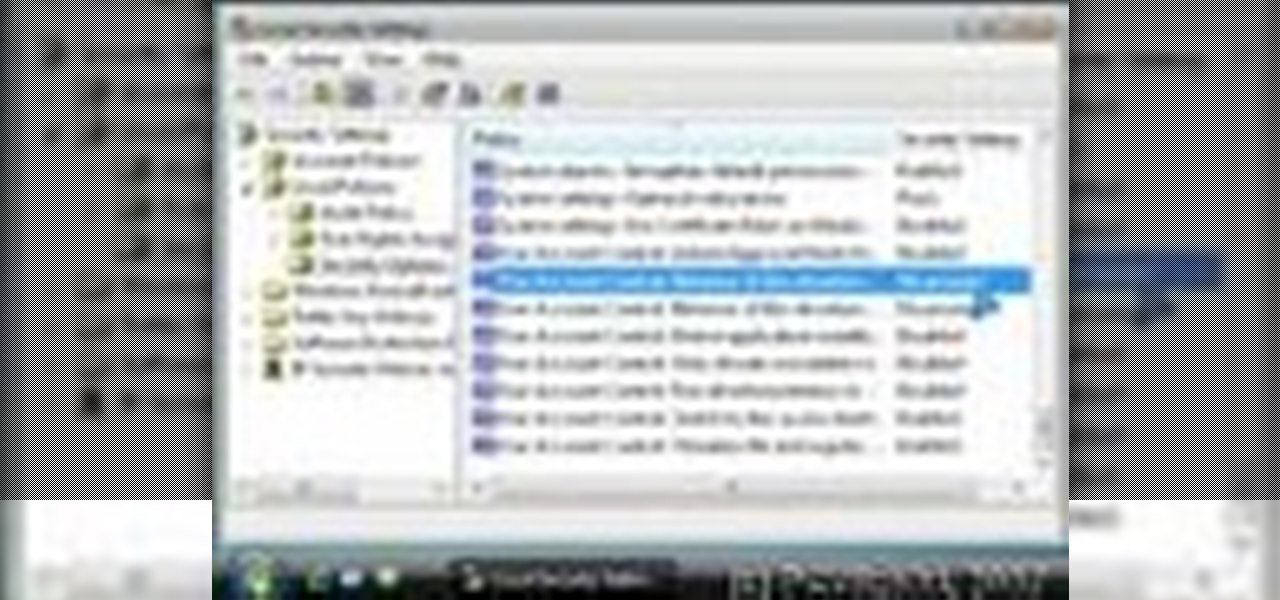
Why is Windows always asking you for permission before you do anything? Since when does Windows control your computer, and not you? Those user account control popups can be so frustrating, especially when it comes to simple tasks.

In this video, we learn how to protect your privacy while using Twitter. Your personal information can get stolen in an instant with the internet. With Twitter, when you are doing updates showing where you are and what you are doing, someone could try to find you and potentially create harm to you. To help you avoid situations like this, you need to go to the security settings of your Twitter account. When you go here, you can change the account so that it only allows people you want to follo...

In this tutorial, we learn how to use the notepad to get by school internet blocks. First, open up Notepad on your computer, then type in "<html>" "<body>", "iframe src=http://www.youtube.com", then "height=100%", then "width =100%". To finishe, type in "<iframe>>/body><html>". Save this as hack.html as all files. After this, open up your browser, then you should be able to go to the website that you wanted to go to! This is a great way to get around the security settings that your school has...

In this video tutorial, viewers learn how to test their system performance. Begin by clicking on the Start menu and select Control Panel. Then click on System and Security, and select "Check the Windows Experience Index" under System. Now click on "Rate this computer". The system will then begin to run some tests. This will take about 1-2 minutes. The Windows Experience Index assesses key system components on a scale of 1.0 to 7.9. This video will benefit those viewers who use a Windows 7 com...

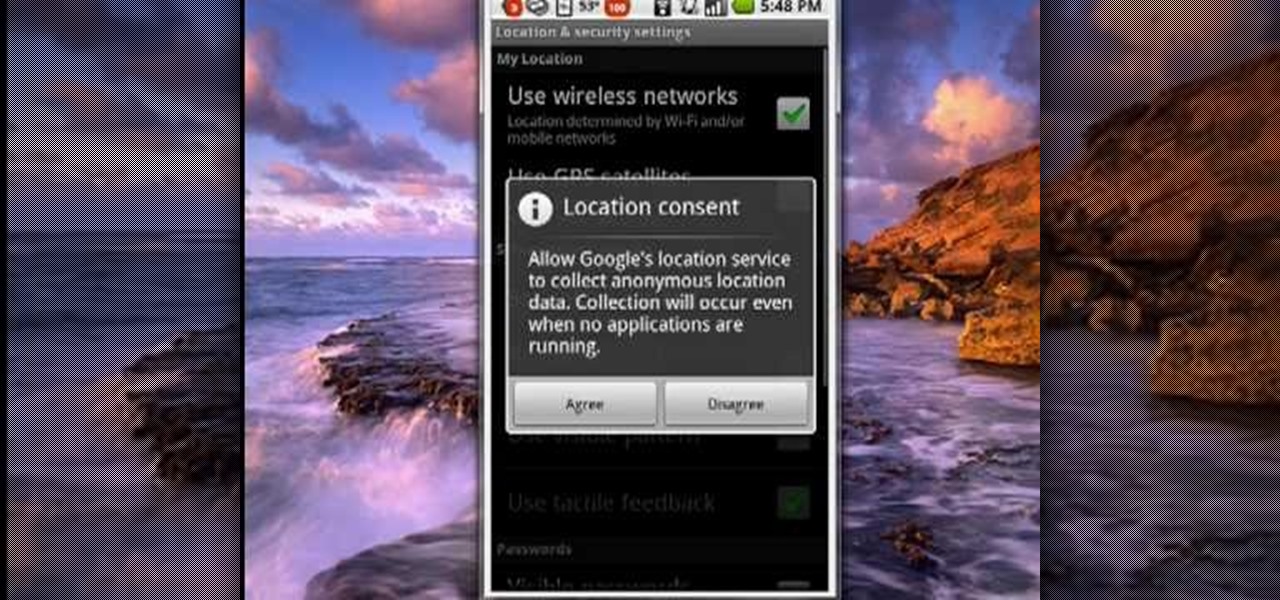
Many applications, especially those found in the Android Market are more effective when they know your physical location; like an app that's going to find the nearest gas station, restaurant or ATM. One of the salient advantages of a Google Android smartphone over, say, an Apple iPhone, is the inherent extendibility of the open-source Android mobile OS. There are a seemingly infinite number of settings to tweak and advanced features to discover and use. This free video tutorial, in particular...

Fashion designer Cate Adair demonstrates dressing with a sarong for Modern Mom. She also discusses how to buy or extend a sarong when the one you find isn’t long enough. One important consideration for beginners is finding a sarong that can wrap around the body twice for security. One way she wraps is to simply wrap under the armpits twice and tie a flower or ornament with the corner. Another way is to put the full sarong on from the front, wrap each end backward and then over the shoulders...

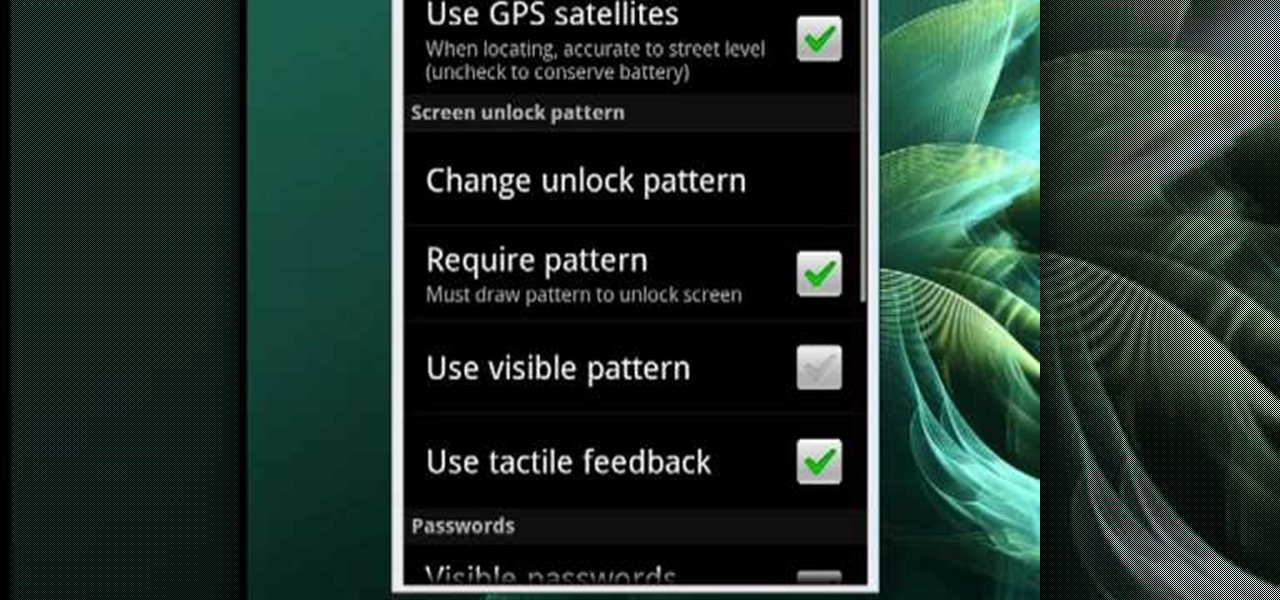
In this video, Mike Callahan shows us how to make our unlock pattern visible on an Android phone. First, unlock your phone and go to the home screen. Then, go to 'settings, location & security". After this, click the button that says "use visible pattern" so that the check mark and button are both gray instead of green. To test this, tap back on the home screen and lock your phone. Now, when you draw in your pattern you will be able to see it on the screen. This way you can see the pattern as...

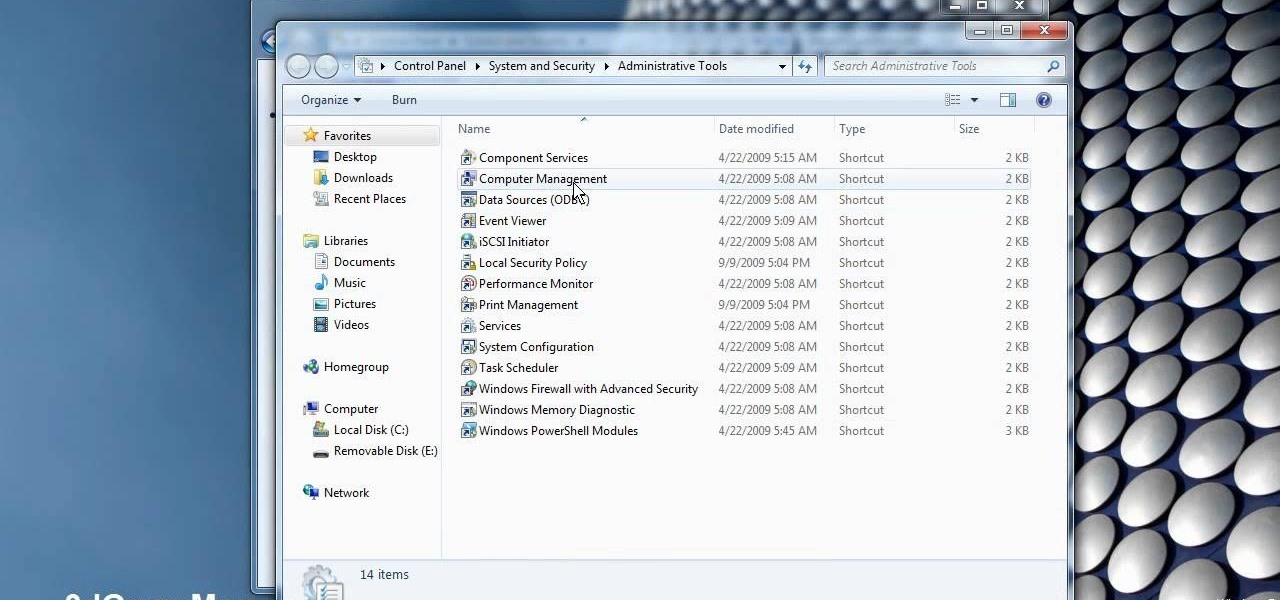
This video demonstrates how to change a drive letter to a certain drive in your Windows 7 computer. On you Windows 7 computer, go to Start > Control Panel. In the Control Panel, select System and Security then open the Administrative Tools. Look for and open the Computer Management tool. On the left side pane of the Computer Management window, select Disk Management. Look for and right click on the drive you want the drive letter changed. Select 'Drive Letter and Paths...'. Click change and s...

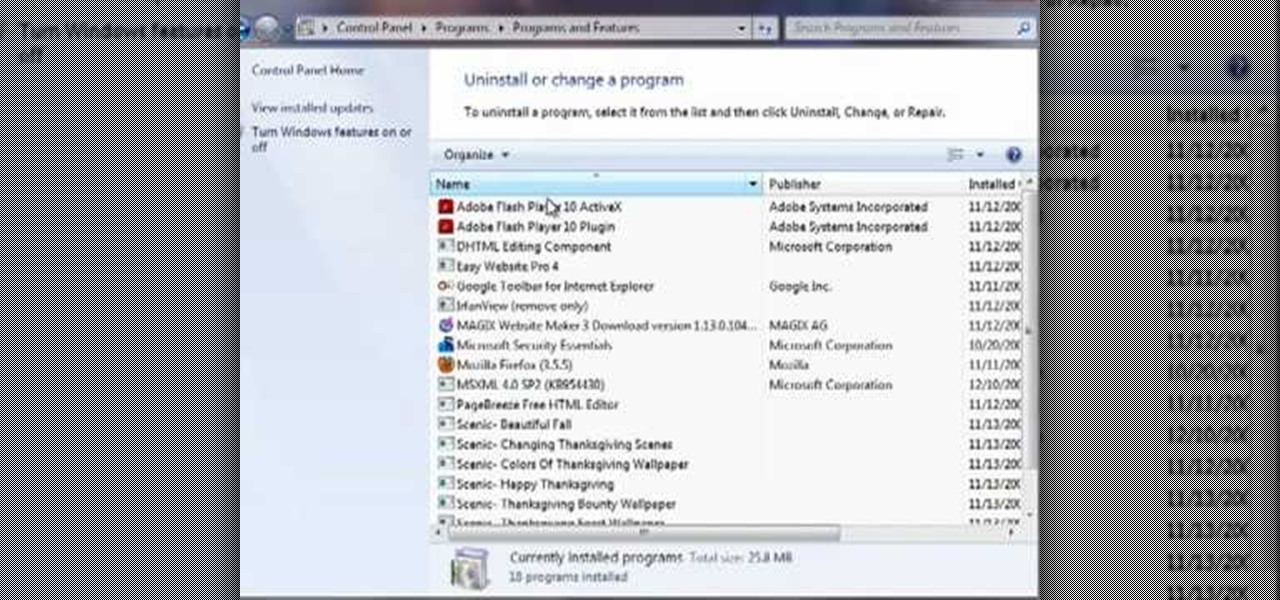
This video by Butterscotch shows viewers how to uninstall a program in Windows 7. To begin, click on the start button at the bottom-left of the screen. Click 'Control Panel' in the boxes that pop up. Click 'System and Security'. On the left side of the window, there will be a link marked 'Programs'. Click on it. Click 'Uninstall a program' beneath the 'Programs and Features' heading. Highlight the program you want to uninstall, then click the 'Uninstall/Change' button near the top of the wind...

The video shows us how to use a proxy to bypass the Internet Filters. Most of the times in our schools and colleges most of the websites including the social networking ones will be blocked for security reasons and makes us unable to log into those websites. In such cases even the ones from the YouTube, several videos will be blocked. So in this video, we will be shown how to bypass those filters and log into those sites. Firstly go to the website Proxapp and over there you will be asked the ...

RAID, or Redundant Array of Independent Disks, lets you divide and replicate data among multiple hard disk drives for information storage security. This video tutorial demonstrates how to install Ubuntu in a RAID 0 array. Before starting, you'll need at least 2 hard drives and an Ubuntu alternate installation CD. RAID 0, or striped disks, let's you install an operating system, such as Ubuntu, on a partition, while using others for data storage, as illustrated in this instructional segment.

In this video you will learn how to update your version of Windows 7 and how to check the system settings for automatic updates. In order to do this you need to go in the Start Menu and then in the Control Panel. Then you need to click System and Security. The next step is to click Windows Update. A new window will pop-up and you will see two types of updates: Important Updates and Optional Updates. To install them just click on the blue link and then check the boxes. To check for updates you...

In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...

Check out this Mahalo video walkthrough of Marshlands in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

If you're an avid programmer or developer, your time is likely spent creating apps and perhaps the occasional website. And while these go-to coding endeavors are exciting and occasionally lucrative, more and more coding pros are turning to careers in cybersecurity and ethical hacking — thanks to the high pay, flexibility, and unparalleled opportunities.

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

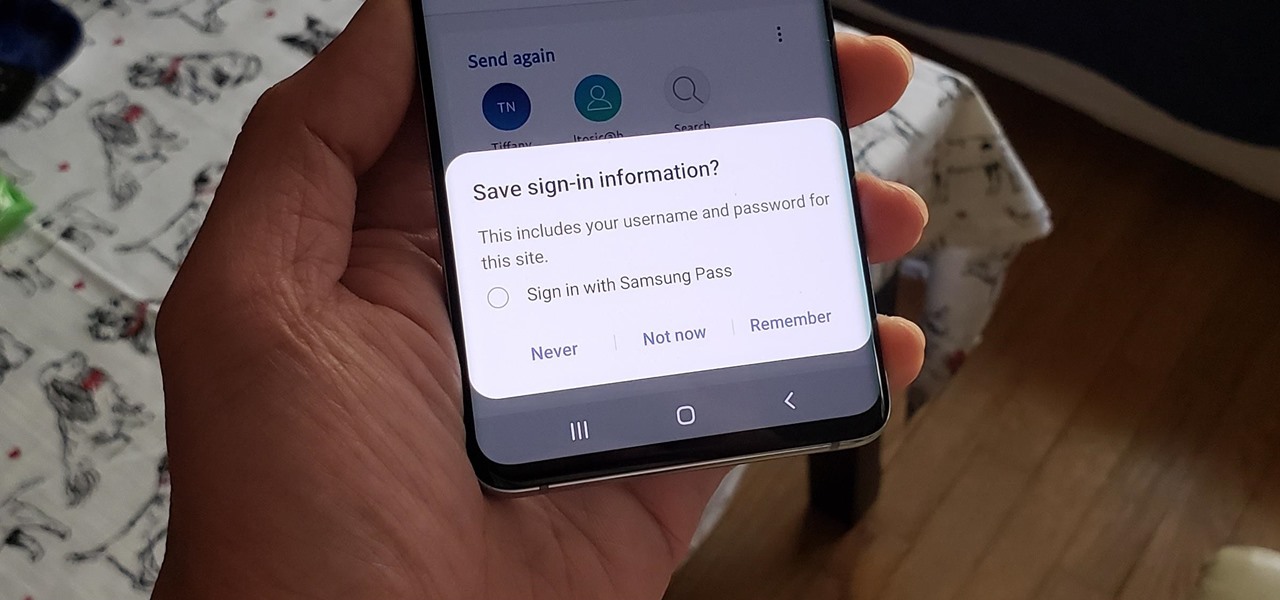
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

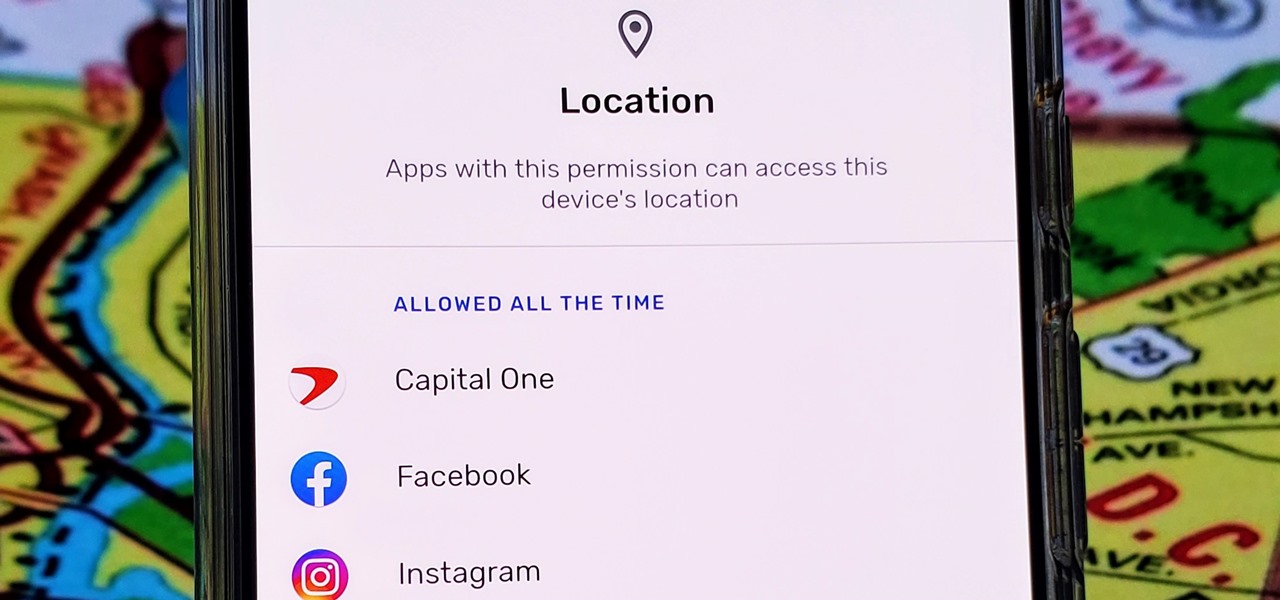
With Android 10, there are now three options when an app asks to access your location: Allow, Deny, and Allow While In Use. That last one prevents apps from seeing your location unless you're actively using them, and it's the default now. But when you first update, most of your apps will still be allowed to access your location in the background — at least, until you do something about it.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

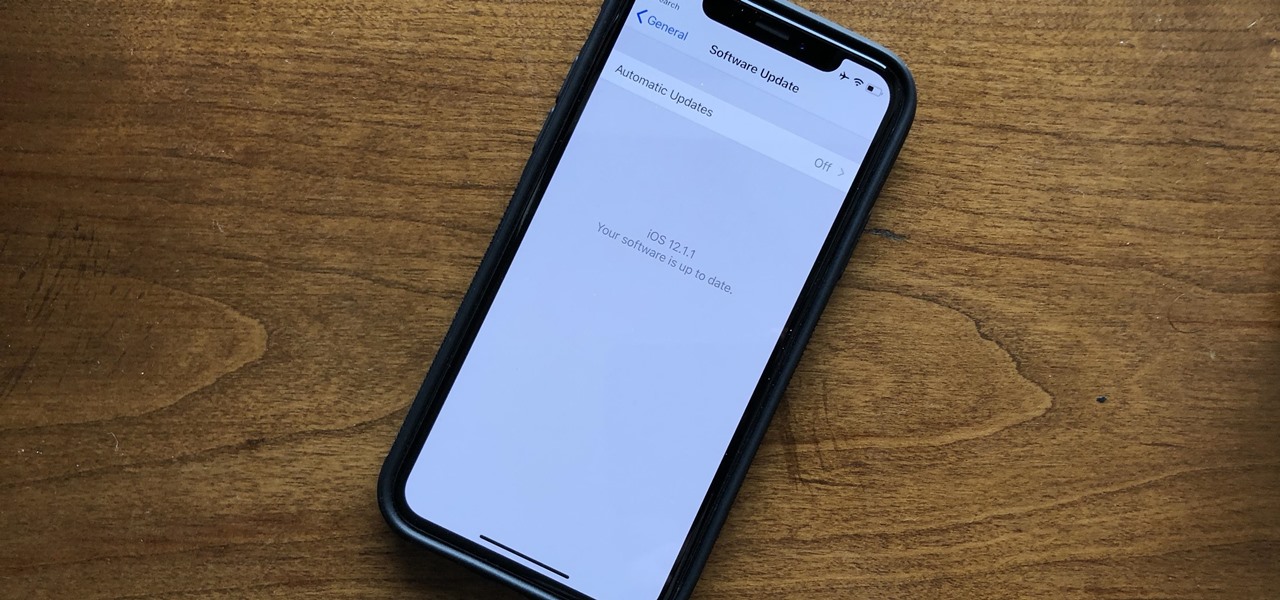
Apple released the latest update for iPhones, iOS 12.1.1, on Wednesday, Dec. 5. It introduces a few new features to iOS 12 as a whole. The software has been in beta testing since Halloween of this year, spending just over one month in the hands of beta testers.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.