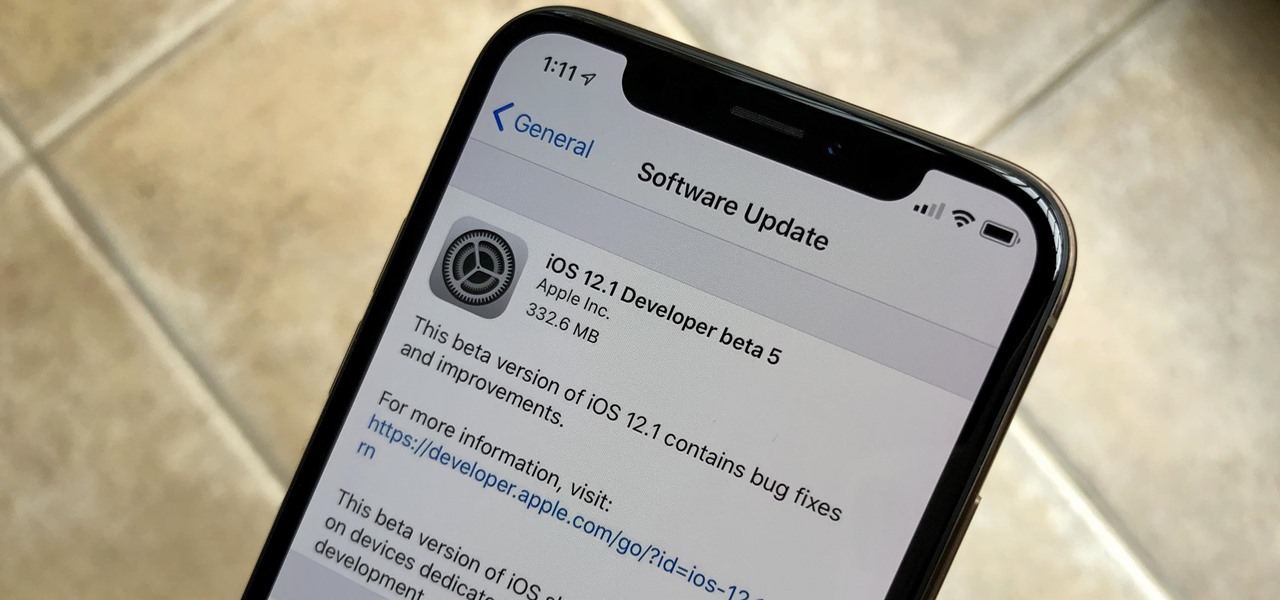
Check your Settings, software testers — Apple released the fifth iOS 12.1 beta on Monday, Oct. 22, just seven days after seeding the fourth beta to both developers and public testers alike. While this initial update is only for developers, we expect Apple to subsequently release the public beta within hours of this post.

The first White Hat Award for Technical Excellence tutorial contest ended last night at midnight! We had many excellent articles submitted, once again re-affirming what an incredible community we have here at Null Byte! We had quite a flurry of great articles in the last few days. Thanks to all of you who submitted such high quality material to our community. Your efforts are appreciated and you have the undying gratitude of our community. We will not forget your efforts. I'll be reading and ...
According to T-Mobile's website, an Android version bump is due out today. While details of specific changes are sparse, the support documentation for Nexus devices very clearly notes a release date of June 2nd for the software. Sprint may have jumped the gun with its own outing of a 4.4.3 update about a month ago, but all indications point towards today's date marking the beginning of a staged-rollout from Google.
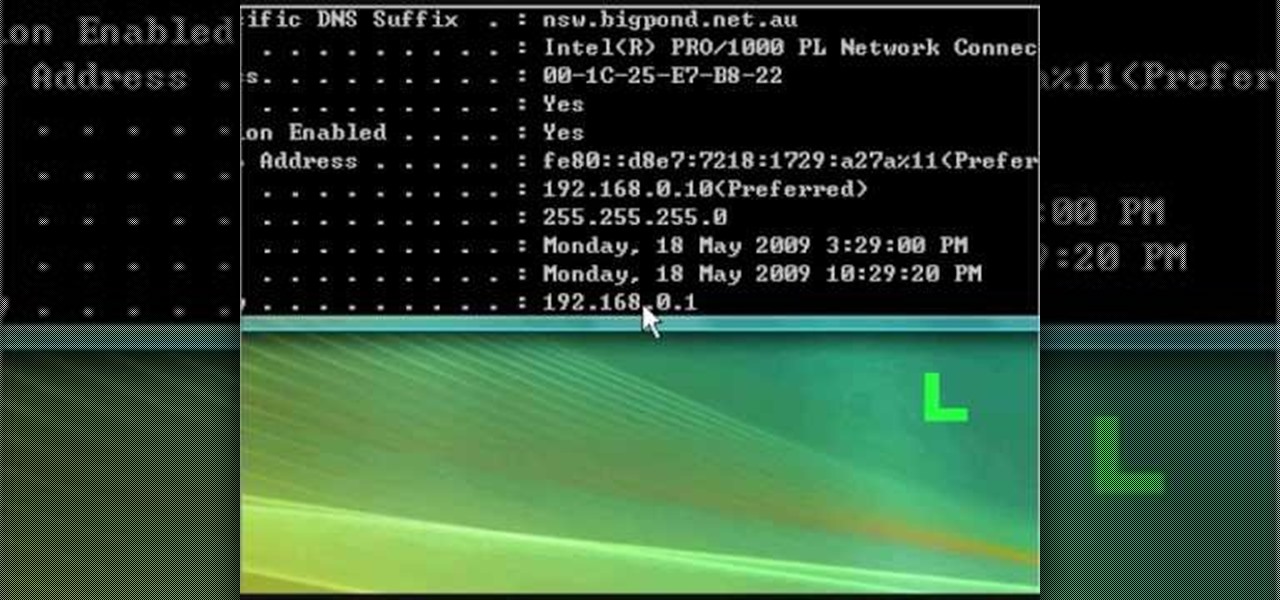
In this tutorial, we learn how to fix security mode for nds Wi-Fi. First, open the command prompt in Windows. Next, type in "ipconfig/all" in the black window that appears. After this, copy your default IP the screen just gave you, then type it into your address bar online. After this, you will be able to log into your security account and make default changes you prefer. Change different station accesses and any other security preferences you want to change. After this, you can change your p...
Having security setting on your web browser is a pretty important tool. It keeps you safe from potential hackers and makes sure you don't visit unsafe sites that could lead to a virus. But sometimes the security settings on a web browser can be a pain and the best choice would be to turn it off. So in this tutorial, you will learn how to easily change the security settings to INternet Explorer 8. So sit back and enjoy!

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

There's a strange grey area for "guerrilla filmmaking" on YouTube. Generally, someone shooting a video needs to get permission from the people in it to show their faces. But on YouTube, that "rule" is more of a suggestion (and sometimes not even that).

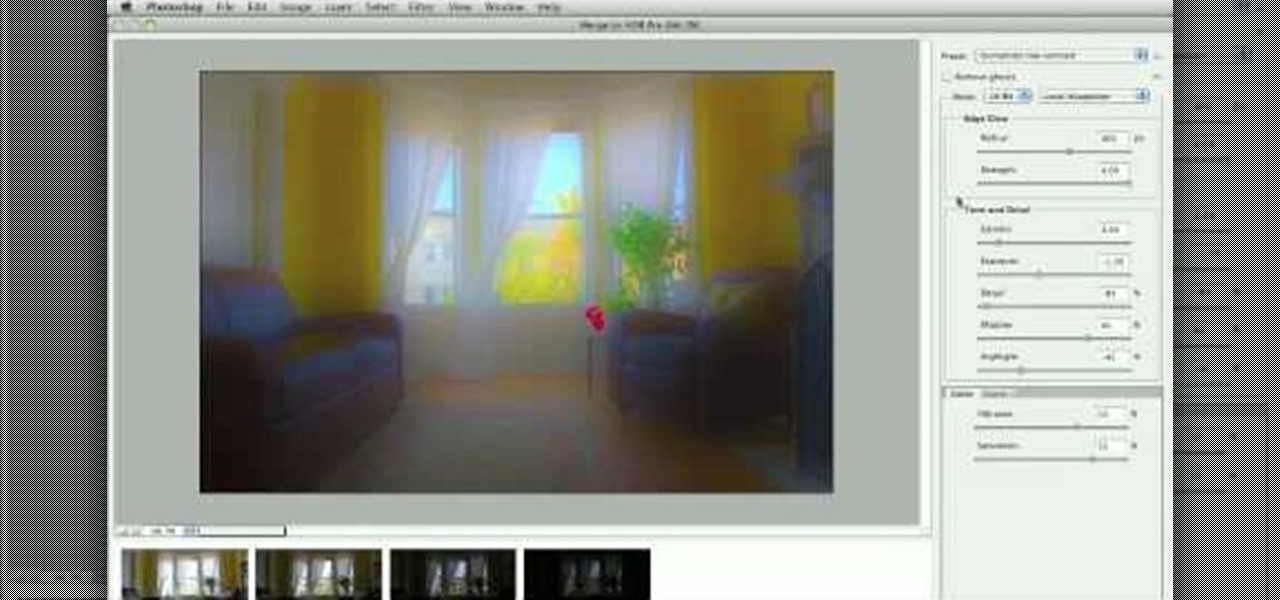
With Adobe Photoshop CS5, it's easier than ever to work with HDR or high dynamic-range images. This video tutorial presents an overview of some of the bigger enhancements. Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial. For more information, and to get started taking advantage of Photoshop...

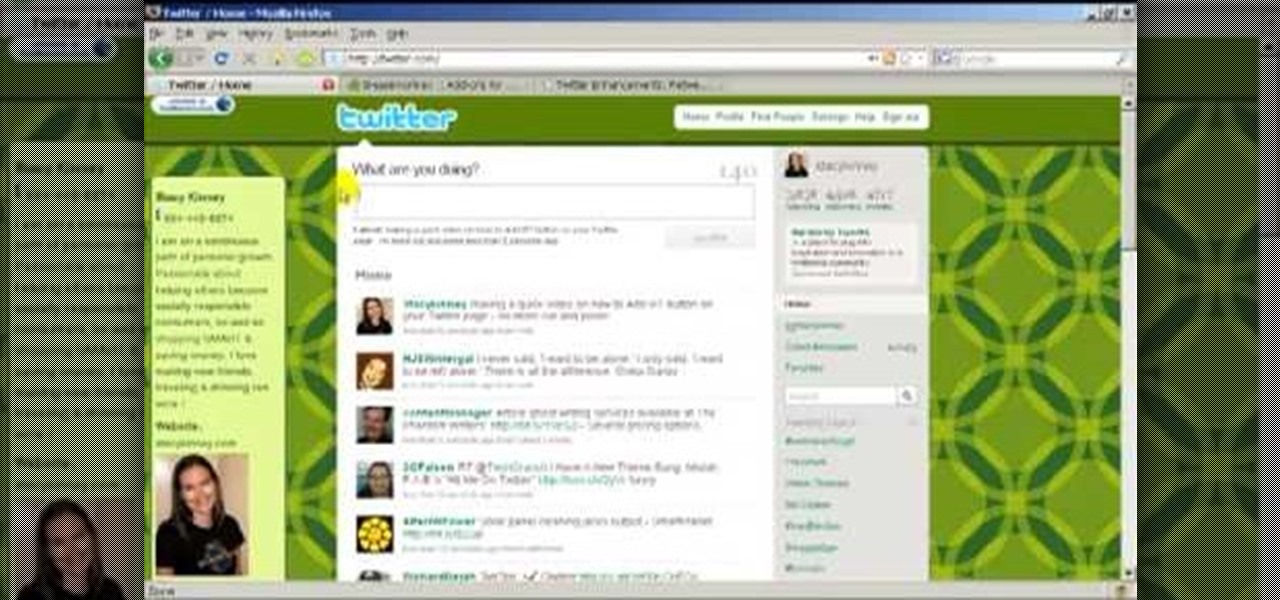
In this how to video, you will learn how to add a re-tweet button on to your Twitter page. Normally to re-tweet, you will have to copy and paste the tweet and type in RT before the message. If you download the Firefox plug-in for re-tweeting, you just have to press a re-tweet button next to the tweet. To do this, go to the Firefox add-ons and download grease monkey. You will next have to download Twitter enhancement. Once you do this, you will see the buttons next to the tweets. You now are a...

Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

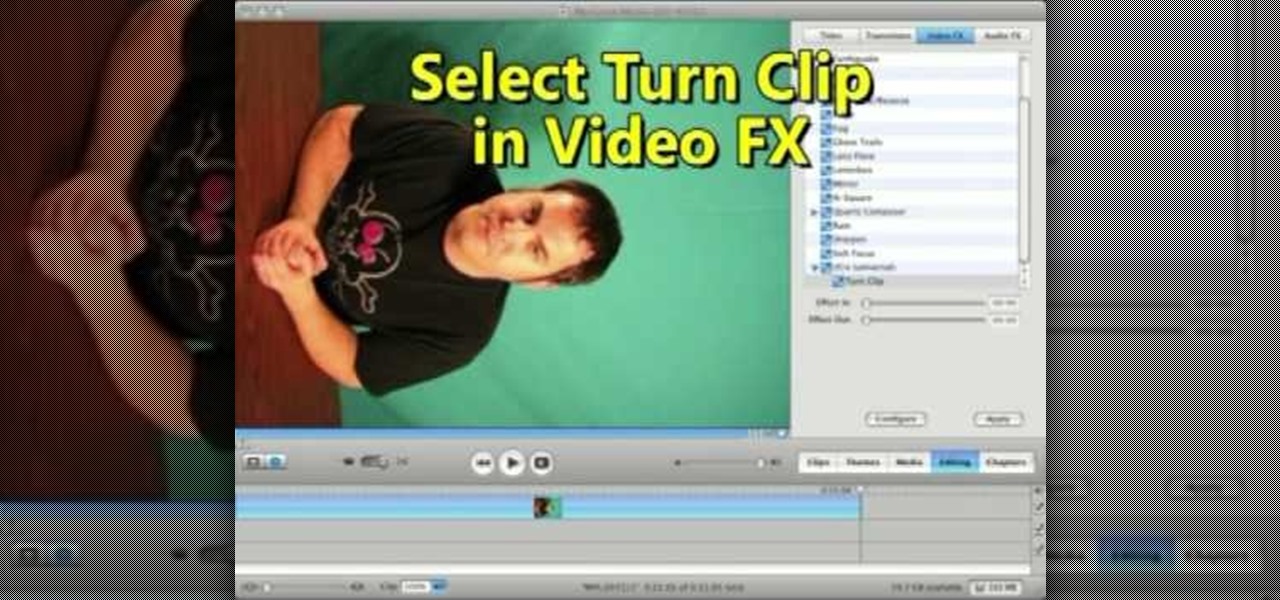
This video shows us the method to rotate a video clip using iMovie HD. Go to iMoviePlugins and download Turn Clip from it. Also make sure you have iMovie HD installed. Now add the video clip to the timeline. Go to the editing tab and choose Video FX and CFX enhancements. Choose Turn Clip from the resulting window. Now set the rotation angle. This can be configured to 90 degrees or 180 degrees. Click on 'Apply' and the software will render the rotation on the timeline. When everything is done,...

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to pick a Brink's high security lock.

Have you ever been the victim of theft? It sucks. Why would these lazy scumbags rather steal from us than work hard like everybody else?

Video tutorial showing how to make your own solar-powered wireless security camera using an off-the-shelf solar panel and any wireless webcam. See creator site for more detailed graphics.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

In this video, we learn how to enhance the audio in your Camtasia Studio 5 videos. First, set your video to 640x480 and then choose the option to zoom yourself. Now, click the zoom in button to zoom in on the time line with your audio. Then, right click the audio and go to "audio enhancement". Once here, click the first option under background noise removal, then click the remove background noise button. Now, when you play back your audio, you will hear a huge difference in what you just play...

In this video tutorial, viewers learn how to use the noise removal tool in Camtasia Studio. Begin by uploading the audio track into the time line. Then select and highlight the region that contains the noise. Now click on Edit and select Audio Enhancements. Under Background noise removal, users are able to select to automatically or manually remove the noise. Once selected, simply click on the Remove Noise button. Users also have the option to adjust the sensitivity. This video will benefit t...

Looking for an easy way to polish your digital images in Photoshop? Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial.

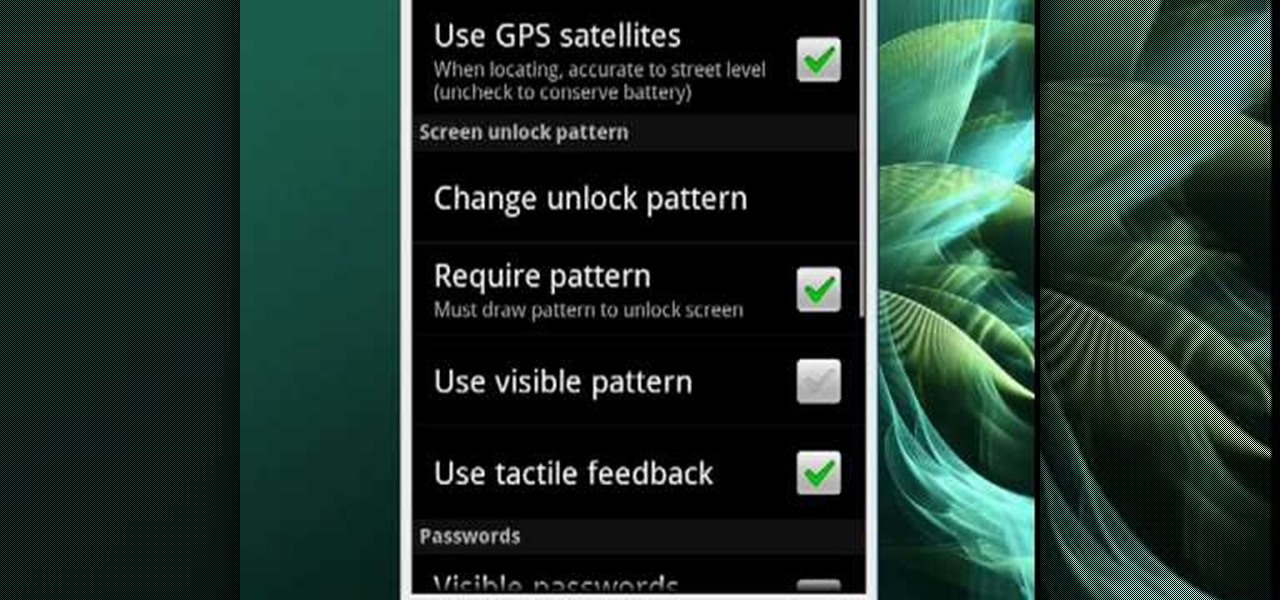
In this video tutorial, viewers learn how to change the lock pattern on an Android phone. The lock pattern allows minimum security on the phone to prevent other people from tampering with your mobile files. Begin by going into the Settings and click on Location & security. Under Screen unlock pattern, select Change unlock pattern. In order to change the unlock pattern, users will have to type in the current unlock pattern. Now type in the new unlock pattern and press Continue. Then retype the...

Learn how to touch up images in Photoshop and bring out the true potential of your art. Using subtle strokes of image enhancement you can redefine the effect that shadows have on your images and use them to bring out the aspects of the photos that you want to highlight. Similarly you can hide those nasty imperfections with ease as shown in this tutorial. Never again let your images befall an embarrassing fate. You too can produce professional quality work with minimal effort and time on your ...

Microsoft Word 2010 prevails with new advancements. New options such as Backstage view allows the user to work efficiently and utilize new abilities when managing documents. It succeeds with new abilities that will allow the user to complete tasks quicker than before. Working with the newly enhanced ribbon allows the user to navigate with an easy, more personal customized environment. Now with more options and commands at your fingertips, it is evidently shown that Microsoft is gifting users ...

Go beyond the traditional 3D workflow to an immersive creative experience with the software Modo, created by Luxology. Modo is the next evolution of 3D modeling, painting and rendering for Mac and PC. Modo includes 3D sculpting tools, animation and network rendering, and advanced features such as n-gons and edge weighting.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Watch this video tutorial, and learn how to turn an ordinary inexpensive webcam into a hidden home security system, viewable anywhere in the world from your cell phone! With a cute and cuddly teddy bear and a cheap webcam, you can make the perfect homemade security camera, or just a camera to spy on your sister and her friends during sleepovers. Follow along with the steps in this how-to video and learn how to set up this spy system. Note: this video is NOT recommended for people who are perv...

By DevonLocks.Com - Security pins can be a pain. This video shows you how to bypass them. See our other video on how to spot them.

In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

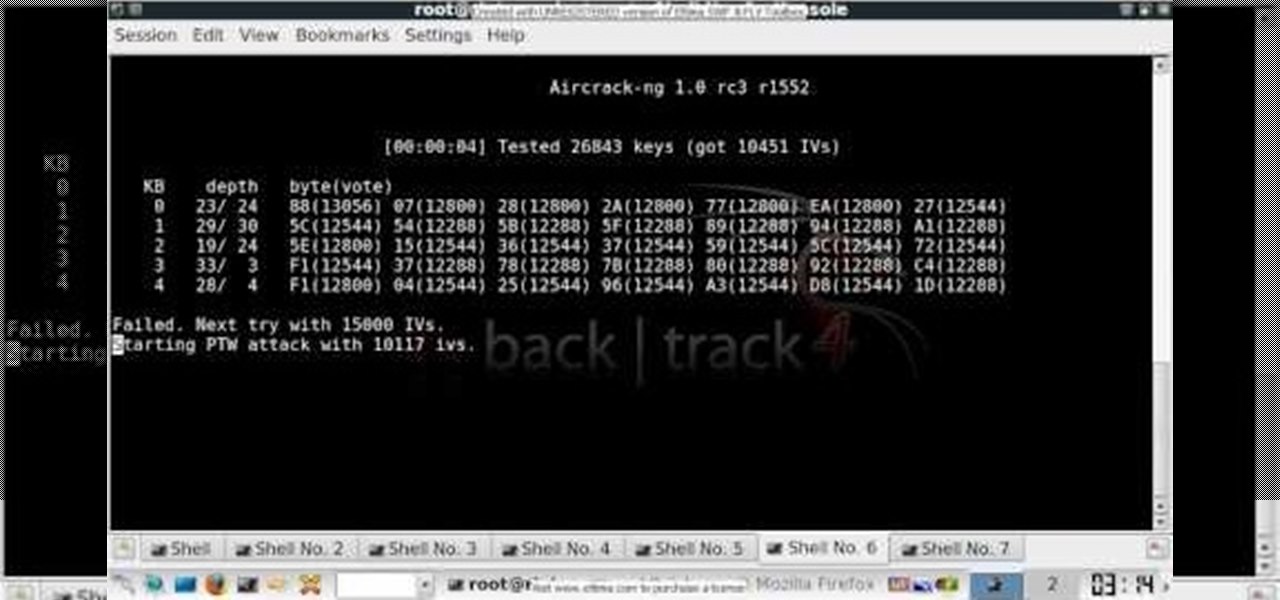
In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Wish there were a way to turn your webcam into a bonafide security camera? Well, there is! And it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over two minutes. For more information, including step-by-step instructions, take a look.

In this tutorial, we learn how to change your body features with makeup. To enhance the cleavage, you can purchase a product called Beautiful Breasts. You will first take the matte color and start to define where the breasts and cleavage are. Make the angles natural and make sure the makeup is blended so it's undetectable. Apply shimmer to the collar bone and shoulders to give a glow as well. The products work for any size and any shape and will give you extra enhancement. There is also a pro...

In this video tutorial, viewers learn how to make a PowerPoint video. This task is easy, simple and fast to do. Begin by creating the PowerPoint presentation and save it as a Graphics Integrated format. Then open the Windows Movie Maker program and click on Pictures under the Import menu. Select the presentation and click on Import. Now edit the video clips in the time line by adding transitions, effects, music and other enhancements. When finished, publish the video. This video will benefit ...

Need some help figuring out how to disable potentially annoying popup security notifications in Microsoft Windows 7? This video tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

In this Microsoft Windows 7 users guide, you'll learn how to take advantage of the operating system's new Applocker security feature. It's easy! So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in about a minute and a half. For more information, including complete, step-by-step instructions, take a look.

In this how-to video you'll learn all the tricks and tips to getting yourself through airport security quickly and easily, even if you have electronic gadgets. Some companies produce travel gear that the TSA will let pass through without having to remove your laptop or electronics. Timesaver! Watch this video and you'll soon be cruising through the "Expert Traveller" line.

It seems that almost every multiplayer map in Gears of War 2 has a secret glitch-based way of getting underneath it. This video is a tutorial on how to do just one of these glitches. It will show you how to get under the Security multiplayer map using a barrier breaker glitch.

In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...