How To: Some Terms a Hacker Must Know...
Welcome back Hackers\Newbies!

Welcome back Hackers\Newbies!
Apple's grand reveal of iOS 8 at WWDC in San Francisco is still a few days away, but that doesn't mean there isn't any speculation as to what features and enhancements might come packed in the new mobile operating system.

Knit blankets are comfortable and scream home and security, but they are expensive and making them is an arduous task. If you want to get started on a major knitting project, watch this video, and learn in general terms how to knit a blanket.
Take a look at this video and learn how to hack into a wireless Linksys router. This hack isn't applicable for all security enabled networks, only ones that use generic passwords.

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

The Thule Snug Tite hitch lock is for carrier to receiver security. This video shows you how it assembles first, then how the lock is applied to a bicycle rack.

This video demonstrates how to install or replace a dead bolt in your door. Having a dead bolt lock gives you a added sense of security, because it is more secure than just the lock on the door handle.

There's a lot of fighting to endure in the Xbox 360 game Bayonetta. In Chapter 1 - The Angel's Metropolis, it's your first real battle. Central Station Platform - Go to the far side of the platform and go through the security gates. The door on the far side of this hall is locked, but on one wall in the hallway you'll see a strange sphere. Walk up to it and start doing combos to open a door.
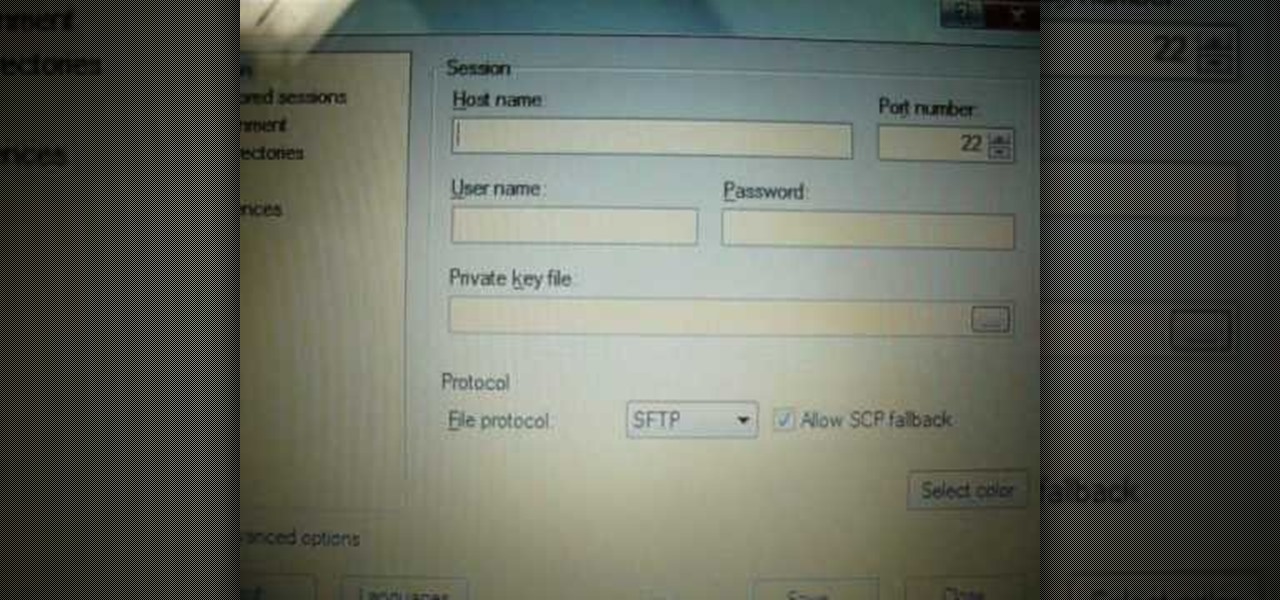
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...
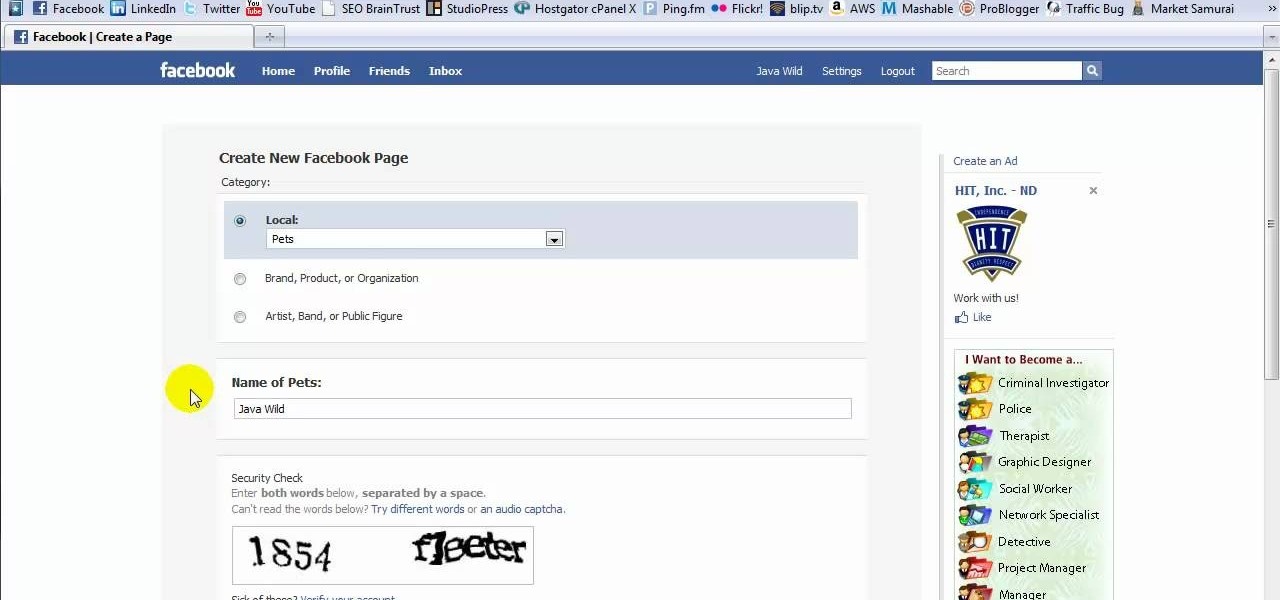
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

This video is a step by step guide for creating exposed teeth makeup . This is loosely based on the Harvey Dent character from Batman: the Dark Knight.

Reduce your chances of becoming the seatmate everyone hates by learning how to head off a screaming jag.

Research shows that color can have a powerful effect on our emotions. Start harnessing that power today. Watch this video to learn how to improve your life with chromotherapy.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

Adding a peephole to your front door is a cheap and simple way to improve home security. This how to video shows you what to consider and how to install a peephole.

How to Hide IP from Hackers. Hide your IP address to get more security. Hotspot Shield (free) change your IP address and your location. To see the changes visit http://www.ip-adress.com/ before and after running program.
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

Watch as Karen's password is retrieved - both by hypnosis and with the help of technology. Plus, learn how to improve your password security.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

Although Facebook has some questionable privacy and security practices, you'll find it still offers you ways to protect the information that's important to you. One of those ways is locking Messenger behind biometric authentication protocols such as Face ID and Touch ID, ensuring that no one else can access your private chats.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

Estimates say that there are roughly 441 million Apple Pay users in the world, but with almost a billion active iPhones in the world, some of you have yet to jump on board the digital payment method. But once you're ready — or if you just need a refresher — adding your debit and credit cards to Apple Wallet is simple.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

We might never truly know all of the colors behind old and classic black-and-white photos, but thanks to technology, we can get a pretty accurate colorization. Although Photoshop is a popular way to colorize these images, you can now use your iPhone, along with a nifty shortcut, to transform and give new life to vintage photos.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

When it comes to augmented reality (AR) on Android, you might be wondering how you can get those cool new games and apps on your unsupported phone. Google has an officially supported device list for its ARCore platform, which usually consists of the more modern devices. You won't find very many older devices on the list for a reason, but that doesn't mean your "old" phone can't use ARCore still.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.
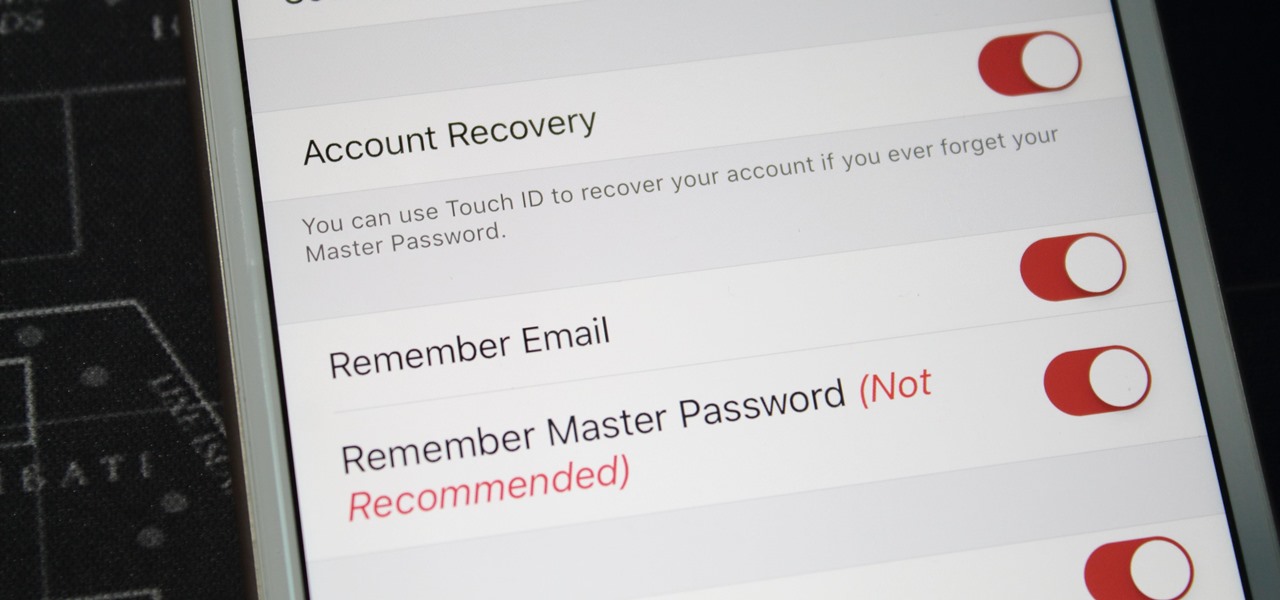
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

The hugely successful S10 series of flagships may be a tough act to follow, but Samsung has proven that it's up to the task with the Galaxy Note 10. The latest phablet bearing the Note name is the first of its line to come with an even larger variant, and boasts an eye-pleasing design with impressive performance to boot.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.
Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.