It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Your email is just that — yours. You shouldn't have to worry about other people gaining access to it on your iPhone. Fortunately, Outlook agrees, and has included a way for you to protect your messages with one of two keys no one possesses but you — your face or fingerprint.

T-Mobile has just pushed out a new update to the Samsung Galaxy Note 8, bringing the build number to N950USQU2BQLA. Here's what to expect.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

Locking individual apps on your Android device gives you an added layer of security by safeguarding app data from unwanted attention. I personally prefer using an app locker over a standard lock screen because my kids play with my phone, and they've completely disabled it after inputting the wrong PIN. So app lockers give me the right balance between giving my children access to my device, and the security of locking down my data from would-be intruders.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

A four-digit passcode is what protects your iPhone, and the sensitive material within it, from strangers or nosey friends. Four digits are the only thing preventing someone from snooping through your pictures and posting them online for the public to see, and that's if you even have passcode security enabled.

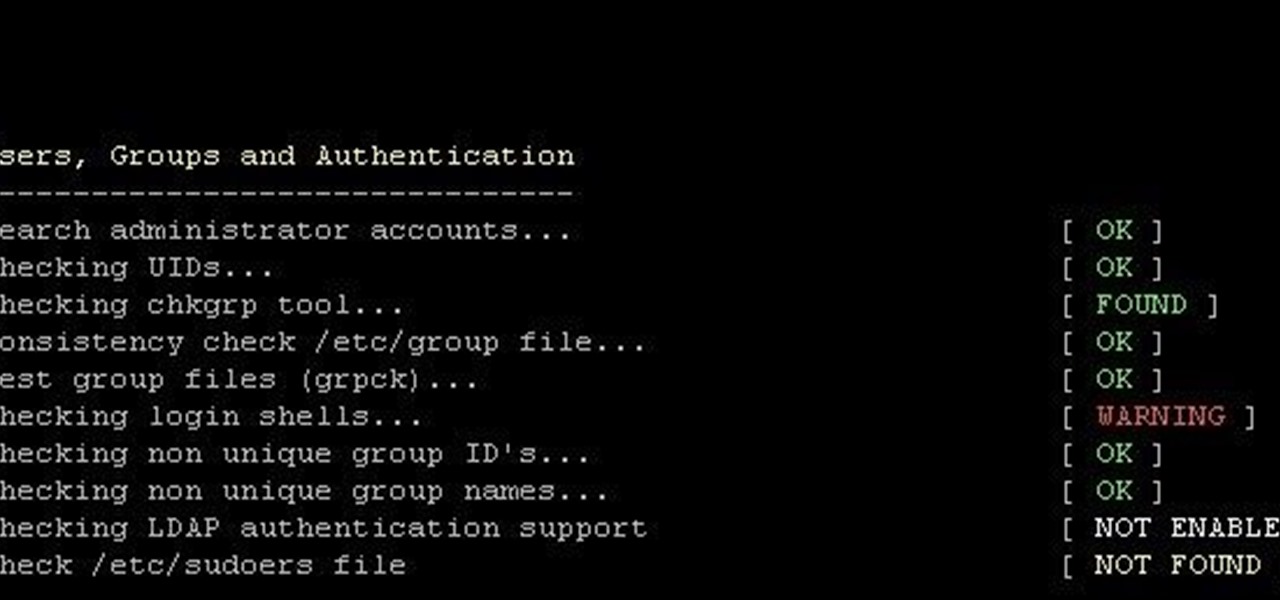
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

Locking up your iPhone with a passcode prevents mischievous friends from looking at your pics and emails, and makes it harder for thieves to access your data before you get around to wiping it. For even more security, there's the password option, which gives you more than just 4 lonely digits.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

David Blaine has made millions off his magic tricks and mind-bending illusions, so why shouldn't we get in on the action, too? Well, your Samsung Galaxy S3 can do all kinds of things, but magic isn't one of them...yet.

Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much attention is due to several, well-known features like Google Talk, Project Butter and expandable notifications.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

The one man Sam Fisher trusts, Victor Coste, has some information for him. To find out the intelligence, Sam has agreed to meet in person. Find out what the important intel is in this walkthrough for the Washington Monument (Mission 5), and where that lead Sam next.

Take a trip into the past as Sam Fisher gets captured by terrorists in the Iraq War. Instead of playing as Sam, you'll be playing the part of Victor Coste — the only man Sam trusts. Find out how Coste saved Fisher's life in this walkthrough for the Diwaniya, Iraq (Mission 4). What happens that day in Diwaniyah? Find out.

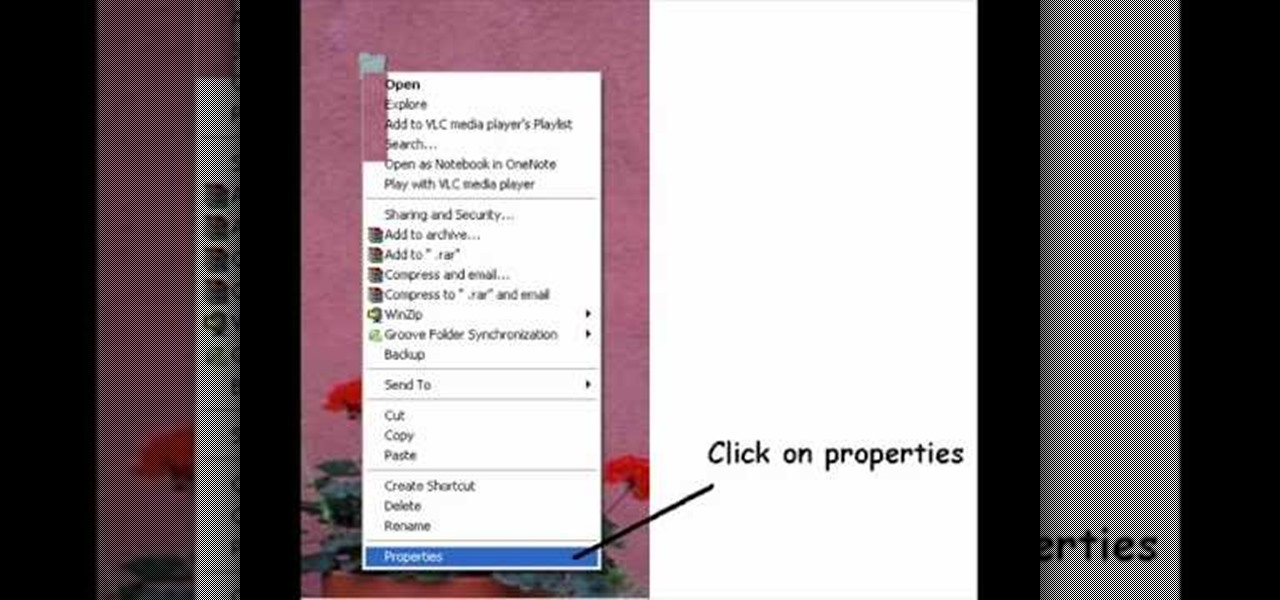
Take your desktop security to a whole new level by making your folders invisible! This video shows how you can make a folder icon disappear, so that the folder will hide in plain sight on your desktop. Use invisible folders to trick your friends!

If you're paranoid about the security on your web-browsing activities, fear not. This Firefox add-on, called HTTPS Everywhere, was created by the Electronic Frontier Foundation (EFF) to help you protect you from curious sites. Installing this add-on will make most websites default to the more secure version.

In this clip, you'll learn how to get started using SkyRecon's Stormshield. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over four minutes. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll learn how to use the VSN plug-in to encrypt email in Microsoft Outlook. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

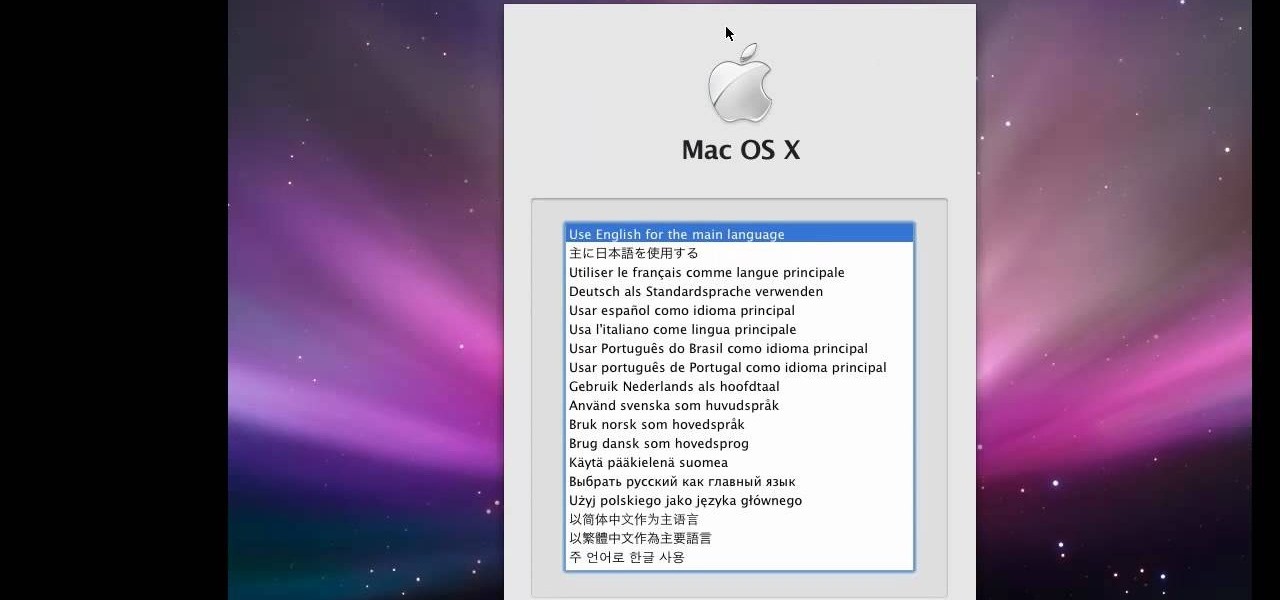
This video tutorial from knif3r2 shows how to install and run Mac OS Leopard on PC using Virtual Machine.

Greasemonkey is a Firefox add-on which works as a script manager for the collection of scripts available on the userscripts.org website. It can be used to manipulate the view and functionality of websites which has a user script. Greasemonkey only works in Firefox and not on any other web browser.

Make light saber glow effects in lsmakerThe author found freeware that helps create light sabers. The freeware is not as good as adobe after effects, but it will serve the purpose. Download the software from the website http://www.lsmaker.uw.hulpage.php?main=lsmaker.html. Extract the folder. Open lsmaker.exe. Save the extracted file to the desktop. Select import. Add either picture or video file. Change the saber color to red. Click ok. The blade needs to be white. In the dialog box change pi...

Not a great lock picker? Well, get some help figuring out how to break into padlocks and high security locks -- check out this video tutorial on how to open locks with comb picks. Comb picks are one of the best ways to hack into these common everyday padlocks. It's not a foolproof way to pick locks, but it's great when it works.

The spy camera shown in this how-to video has a 60 foot cable, and is full color and has audio. This spy cam can be used as a security device, or to feed paranoid delusions or stalking urges. Watch this video tutorial and learn how to set up an X10 spy camera.