It's not enough for me to just listen to a mindless EDM song that can be retooled as a torturing method for Guantanamo Bay. As an actual fan of music, I yearn for substance and depth. Artists like Morrissey, Kurt Cobain, and John Lennon impacted lives with not only their music, but the subject matter of their songs.

Google announced Android L to the masses at their I/O event, and with it they introduced their new "Heads Up" notification system. These notifications are part of the new Material Design UI and are sure to change the way we interact with notifications on our devices.
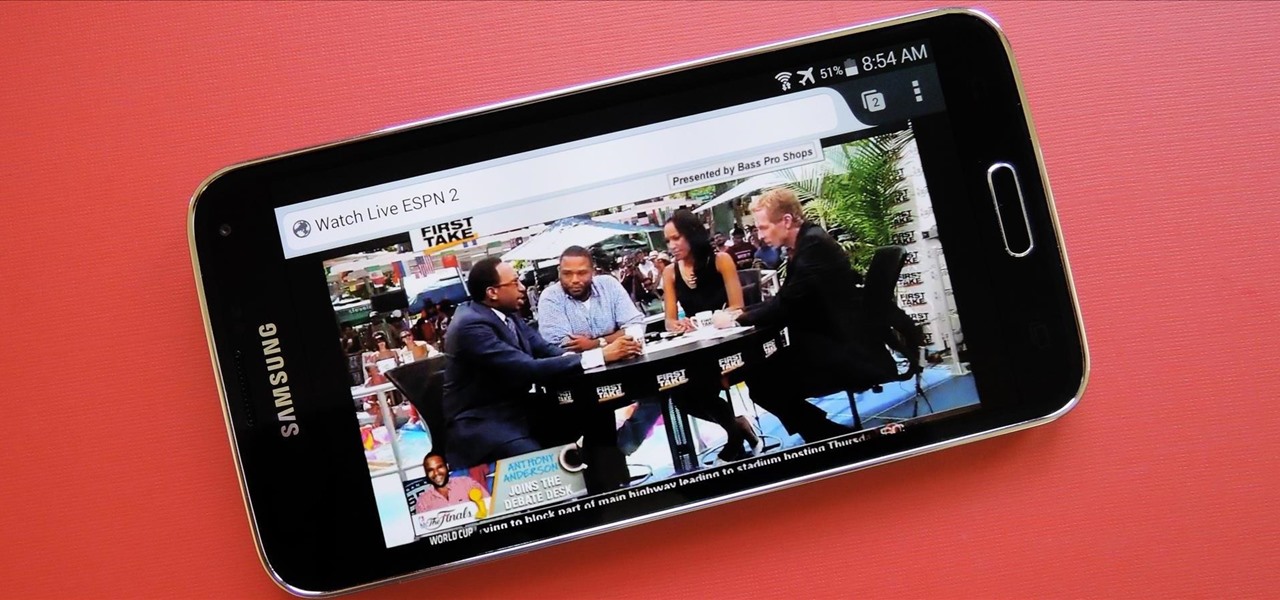
Over the course of the past few years, many websites have begun offering up a mobile-friendly HTML 5 version of their content. Videos that once required Adobe's Flash can now be played on any modern mobile web browser.
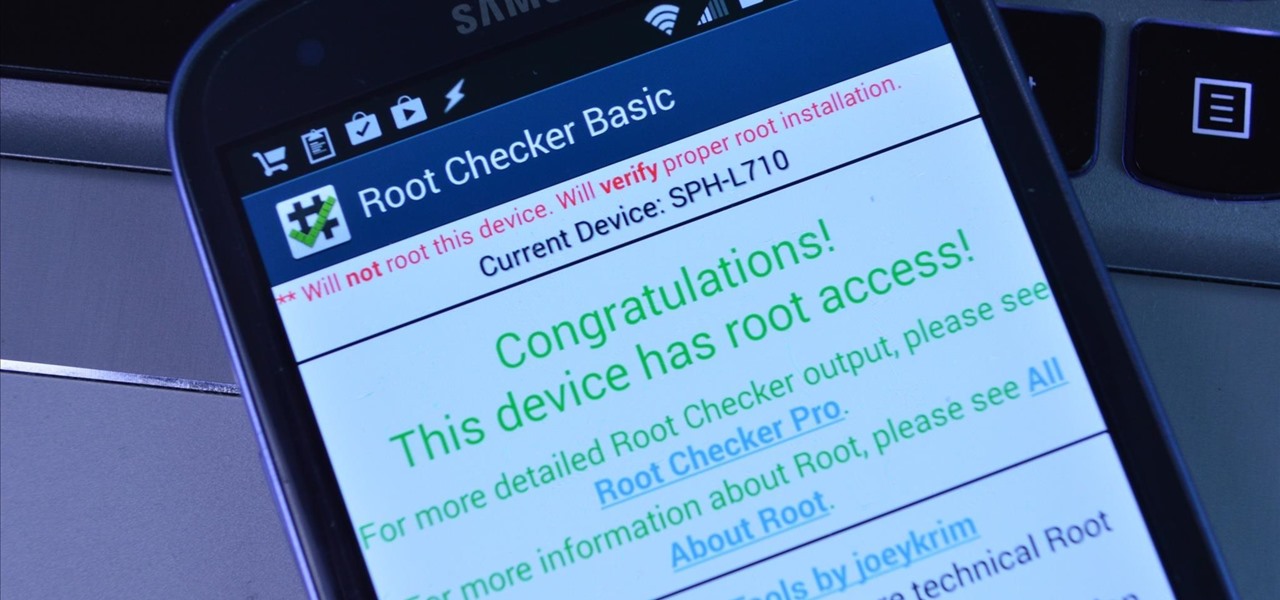
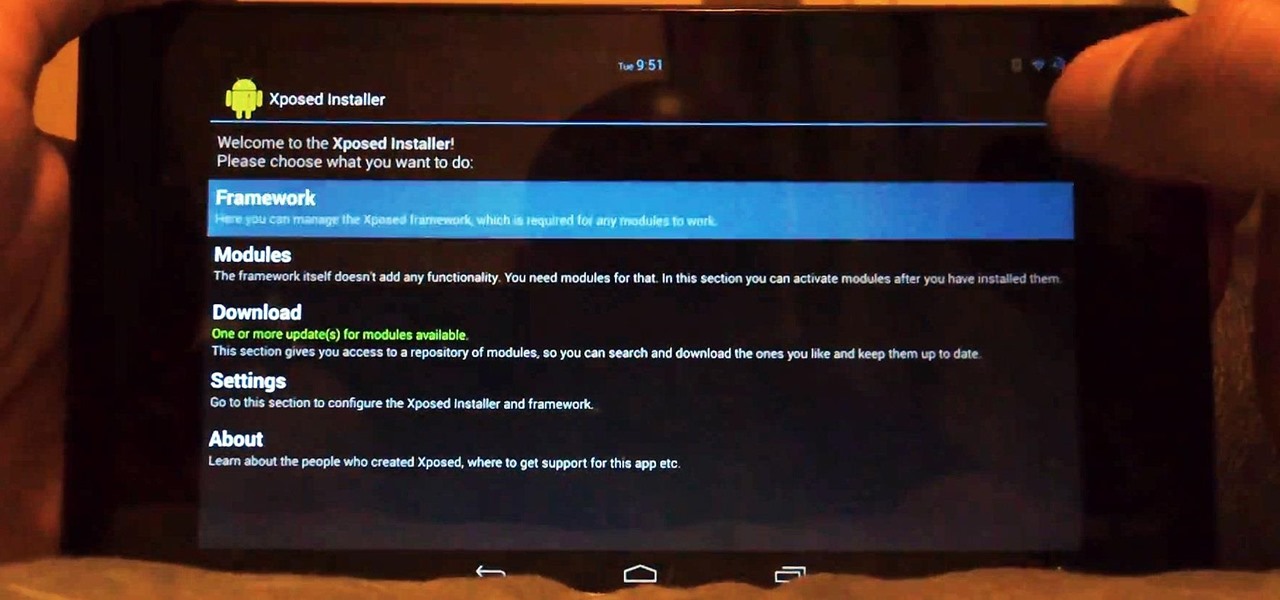
Now that all variants of the Galaxy S5 have finally been rooted, we can start exploring all of the tweaks and hacks that Superuser privileges open up to us.

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.
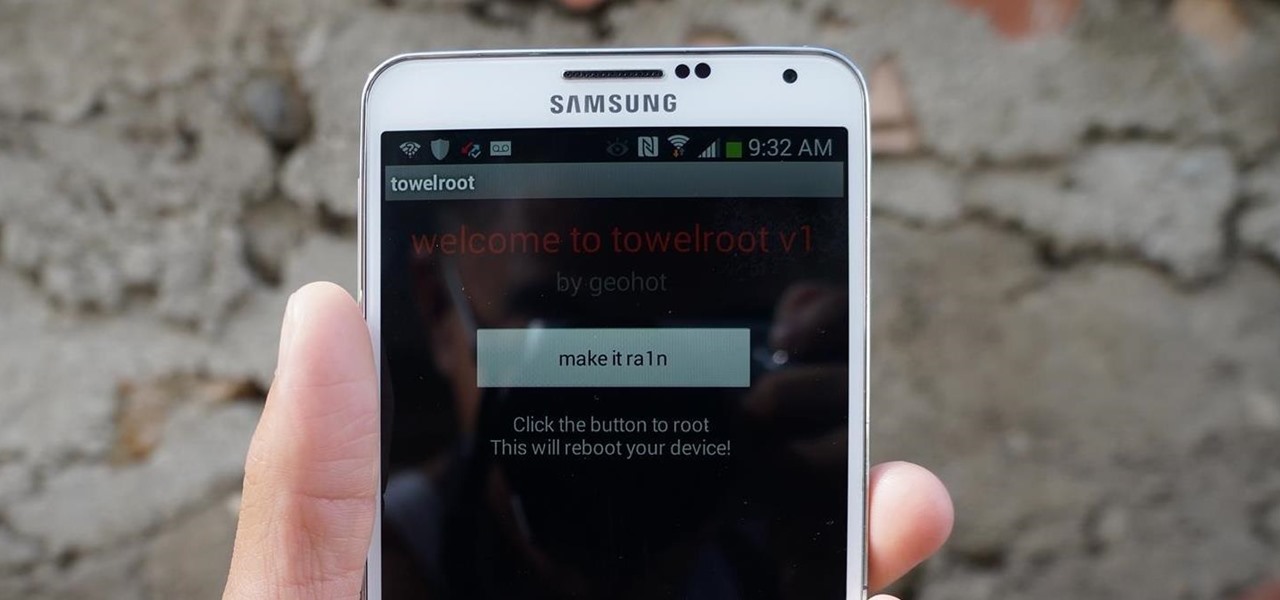
AT&T and Verizon customers, it's finally happened. After many long months of waiting, and a fairly significant bounty up for grabs, your Galaxy Note 3s can finally be rooted! Best of all, it may be the simplest method for achieving root we've ever encountered.

Rooting an Android device used to be a nightmarish labyrinth of .zip files and command prompts, confusing seasoned modding veterans and newbies alike. Thankfully, the process has gotten simpler over the years, with various "one-click" rooting tool kits surfacing and working for nearly every major Android flagship on the market.

Samsung's TouchWiz interface comes with tons of small features that can increase your productivity and user experience. From Mulit-Window Mode to Stress Level Monitoring, there are so many functions that some even go unnoticed.

While AT&T and Verizon may not have had a chance to screw Note 2 owners with unrootbale devices—mainly because they've screwed us over by not issuing KitKat updates—it's safe to say that they can in the future. And while Sprint and T-Mobile subscribers have been able to root, the various methods can make the process somewhat confusing, especially for first-timers.

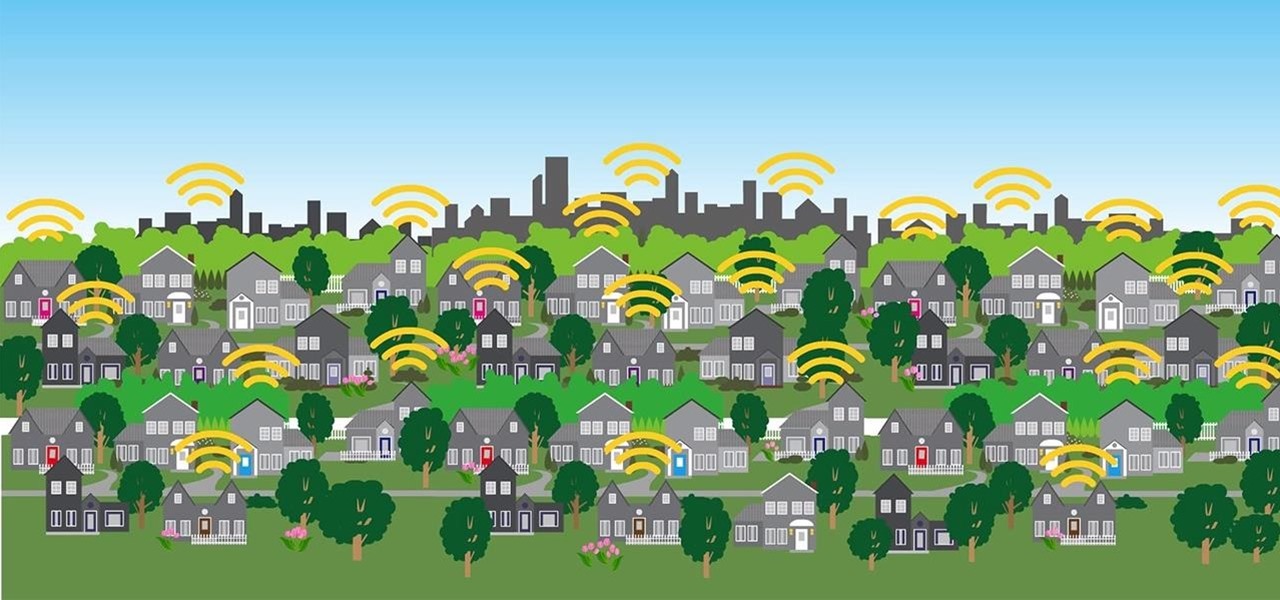
In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

Parents, grandparents, aunts and uncles, and even older siblings have all likely dealt with handing their smartphones over to young children. No matter if they want to play games or watch cartoons or record funny noises, you're handing over a very personal device to those who can mess up what they don't know.

As I begin my move across the country, I find myself dodging all kinds of Craigslist scams, particularly in the apartments and housing classifieds. Fortunately, I've discovered a little trick that will tip me off to a scam before I lose $1,000 in a fake security deposit.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

There are a lot of mods for your Nexus 7 when it comes to improving and streamlining its overall functionality. You could add custom swipe gestures, conserve battery power, and even run multiple apps at the same time.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

The "Knock Knock" features on LG's G2 phone have proven popular and useful enough to spawn various apps and mods cloning these abilities for other devices. Porting the "Knock On" feature to our Samsung Galaxy S3 isn't as easily doable, since developers would need to create a modded kernel, like they did for the HTC One. The "Knock Off" function, on the other hand, is a lot more manageable.

When it comes to blocking unwanted calls, your Android device comes stocked with a native blocking feature that allows you to reject certain phone numbers. That being said, the native blocking feature on the Samsung Galaxy Note 3 isn't the prettiest or the smartest, with its non-obvious setup and lack of features.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

While you may suck at Instagram, it's likely that you manage multiple Instagram accounts, whether strictly for personal use or for managing blog and business pages.

I love my status bar. Not only does it tell what time it is and how much battery juice is left, but it gives me cellular connection info, text alerts, and app update notifications. However, one thing is does not give me is customization. Since you're looking at it all the damn time, why not personalize it?

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

It was only a matter of time before the apps from the new Samsung Galaxy S5 leaked for everyone to download and install, and today we've got one that takes advantage of the IR blaster on your Galaxy Note 3.

Accessing notifications and quick settings from the lock screen just makes things move quicker and more efficiently, unless of course we're using a secure lock screen. It makes sense that if we have face, pattern, or pin security enabled, we may not want notifications accessible, but really, that should be something we decide for ourselves—and now we can.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Leaving your Wi-Fi radio "on" allows your smartphone to auto-connect to trusted wireless networks in lieu of using cellular data, but it also consumes battery power while it's constantly network hunting.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

I've said it before, but there are few things quite as annoying (or embarrassing) as having your smartphone go off at a time where it just shouldn't happen. Imagine a nice, intimate evening with your significant other; you dim the lights, snuggle up, and "this classic" comes on. Or, your phone goes off in a meeting, and your boss gives you that look.

Smartphone users these days can get bombarded with texts and emails every hour. Online retailers sending you coupons to get you to buy stuff. Girlfriends asking where you are. Service providers reminding you to pay your bills on time.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

If you're like me, then you were a little disappointed after updating your Nexus 7 to KitKat and realizing that not much has changed. The old Jelly Bean look still occupied your home screen, and there wasn't really anything noticeably new overall. All of that waiting and anticipation only to be left high and dry.

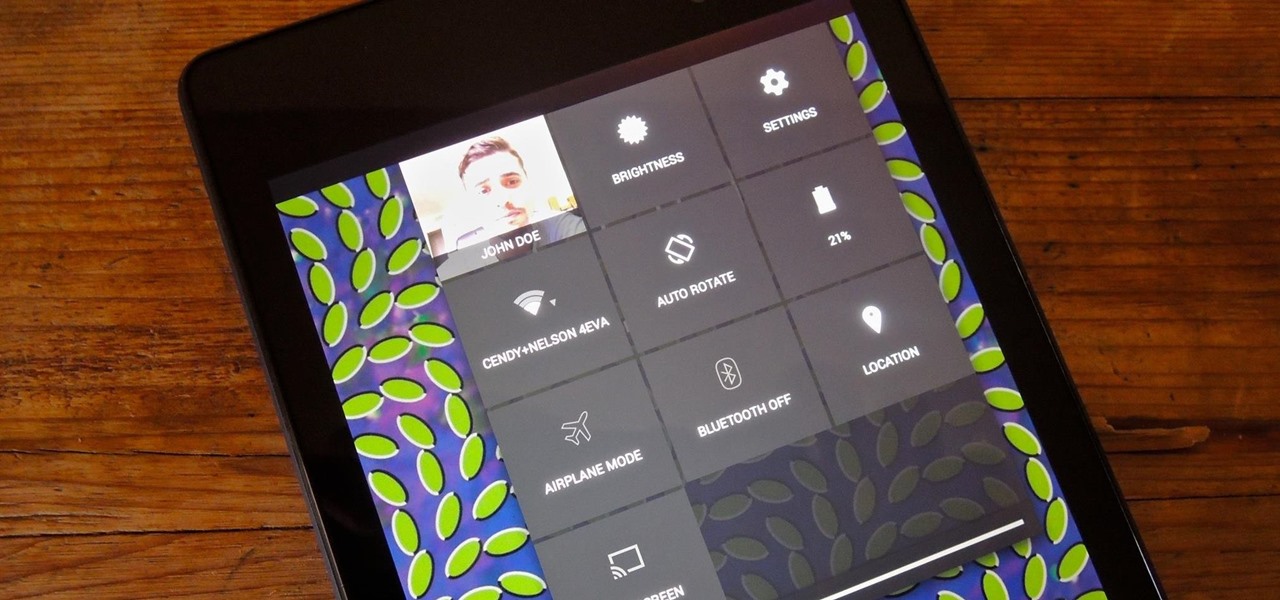
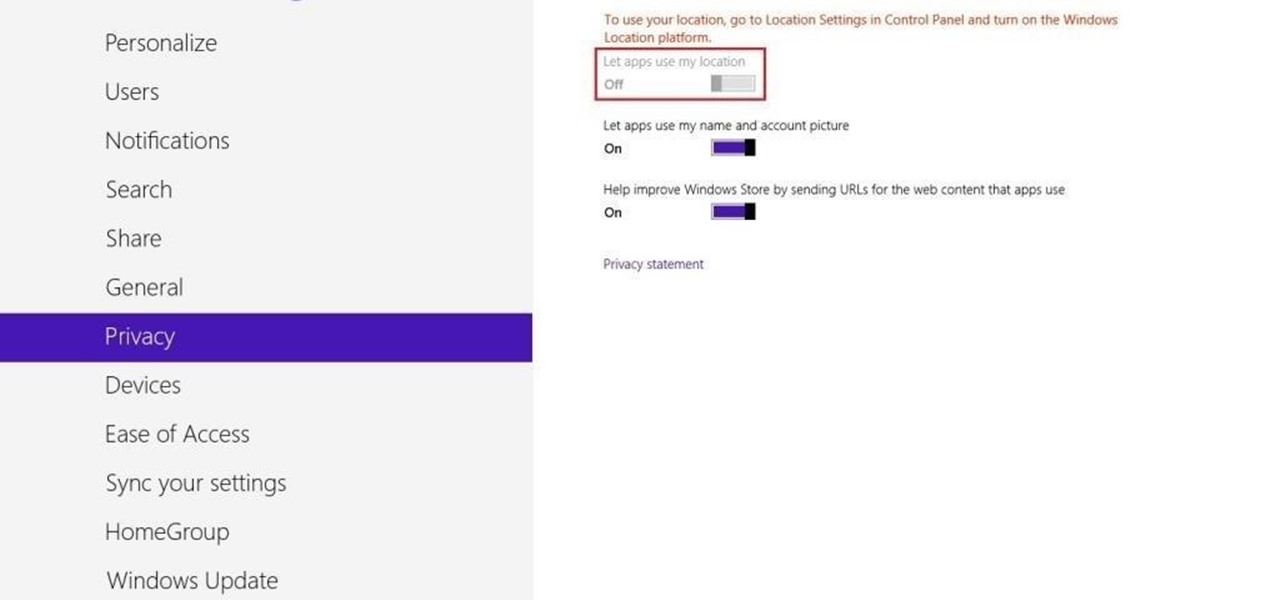
Not only does your mobile phone auto share your location. Now Windows 8 does the same thing. I'm going to show you the two (2) ways to disable that.

Keeping your Samsung Galaxy Note 2 clean and neat can become a hassle, especially if you're an app whore. As the amount of applications on your device goes up, so do your notifications, which will clog up your Status bar with icons alerting of recent news and tasks.

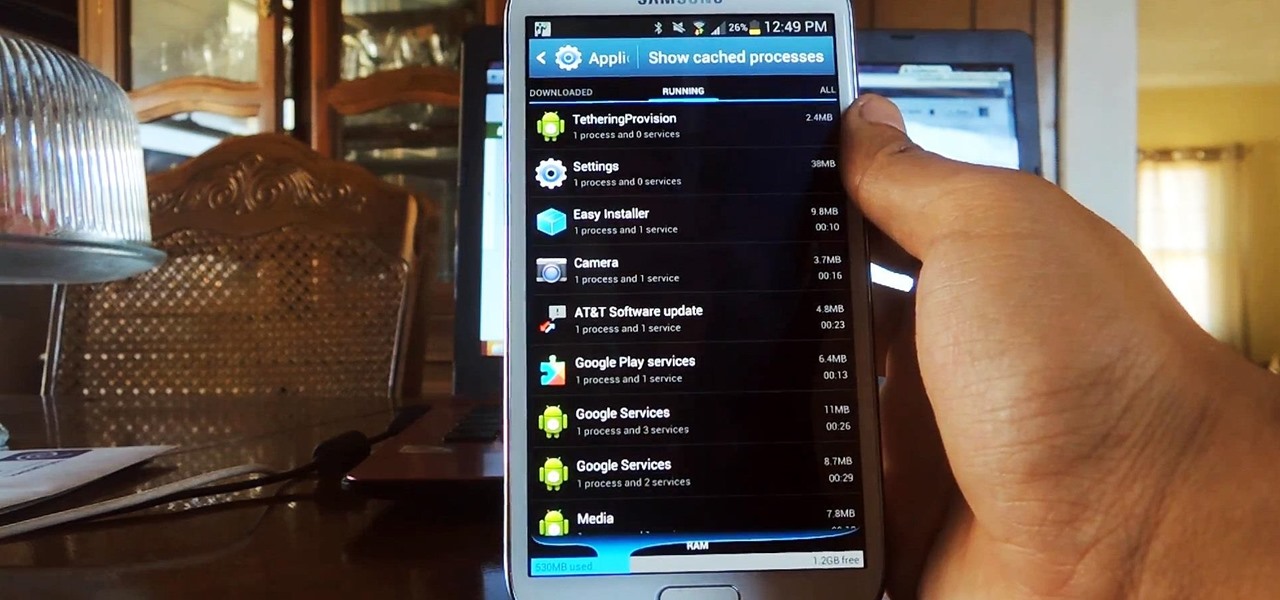
A certain selection of applications on your Android device (both system and downloaded) start running as soon as your Samsung Galaxy Note 2 turns on, laboriously hammering away at whatever tasks they have to do.

If you use your Samsung Galaxy Note 2 consistently throughout the day, you're more than likely to encounter the low battery warning on occasion—anytime you dip below 15 percent remaining. While the low battery warning may be a convenience for some, it can also be a nuisance for others (like me), as it continues to appear intermittently after dropping from that 15 percent. In this softModder tutorial, I'm going to show you how to get rid of that annoying low battery alert for good.

For now, the redesigned and fresh-faced Android 4.4 KitKat is exclusive to the new Nexus 5, though it will be rolling out to other Google (Nexus 4, Nexus 7, Nexus 10) and Google Play Editions (Samsung Galaxy S4, HTC One) devices in the next week or two.

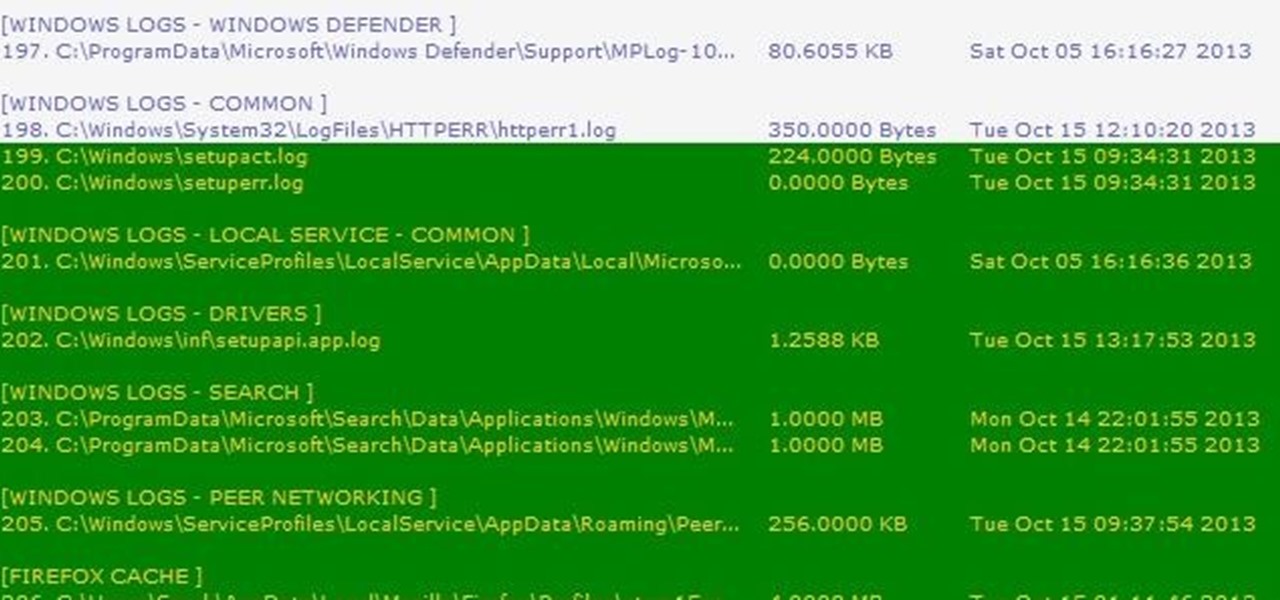
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

Phone interruptions are commonplace, as is evident by my historically epic missed phone call list, ranging from annoying sales people to my mom checking in every five minutes to see if I'm still alive.

Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.