Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

There's a growing sentiment around the web that when it comes to Android, stock is best. Many people prefer the clean look of Google's vision for Android, but manufacturers like LG will add features and themes on top of this base to differentiate themselves from the pack. But these OEM skins, as they're called, aren't always as overbearing as you might think.
During an event in Moscow earlier this year, Nokia announced a refresh to their Nokia 2, 3, and 5 series phones. While there is no official confirmation of a US release for the updated Nokia 2 and 5, we do know that as of July 2nd, you'll be able to snag a new Nokia 3.1.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

If you can't afford an unlimited plan, you're limited to a certain amount of data each month on your iPhone. Even some unlimited data plans have carrier-imposed mobile data caps that throttle the user if they exceed them. Keeping track of your exact usage each day will help make sure you don't get billed more or throttled like a chump near the end of the month.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

With Huawei's recent emergence as the second largest OEM in the world, the company was poised to finally make a big push into the US market. Instead, their efforts were derailed by an unlikely foe, the US government. As a result, American customers will miss out on the newly-released Huawei P20.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

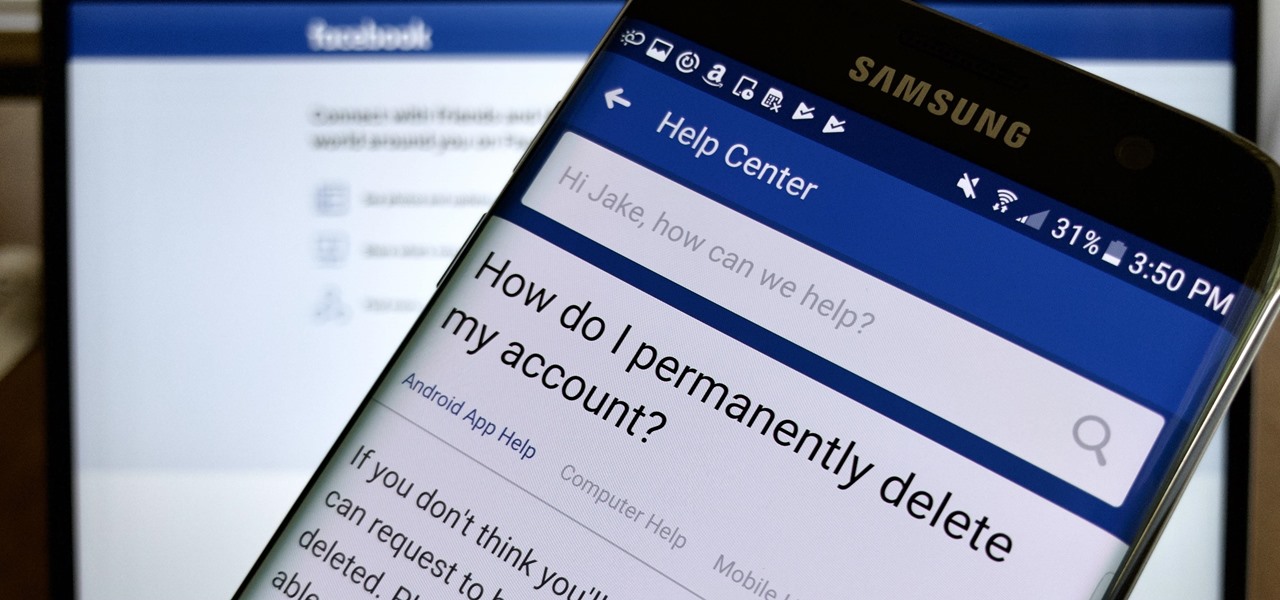
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account is actually a quick affair. You just need to know where to look.

Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices access to their visual voicemail apps. For that, there's Google Voice.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

Over the past week, we've had a number of important launches take place in the Android community. Samsung is in the middle of their rollout of the Galaxy S9, with preorders in the US shipping this week. Google also rolled out the first Android P developer preview last week. While these may seem unrelated, there are actually a number of Android P features inspired by Samsung software.

MoviePass may be popular with filmgoers on a budget, but it might not be with those of you who are concerned about your privacy, since MoviePass may be logging your location data even when you don't expect the app to do so.

During Mobile World Congress 2018, OEMs started to introduce the world to Android Oreo (Go edition). Android Go offers smooth performance on entry-level specs, allowing for genuinely good cheap phones. At first, the US only had one Android Go device, but it looks like a second will join in the near future, the Nokia 1.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

Because of quirks with cell radios and how Android was previously set up, custom ROM support for Galaxy S phones has been sparse these past few years. It's been almost nonexistent for US customers, while international users would see some ROMs. Thanks to Android Oreo's Project Treble, this will all be changing soon.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

When OnePlus announced the 5T, many were disappointed that it wasn't shipping with Android Oreo. To curb some of this disappointment, OnePlus quickly introduced an open beta for both the 5 and 5T and promised that each would receive the official version by Q1 2018. Well today, OnePlus has met this promise and pushed the OTA out for the official stable version of Android Oreo.

As expected, Apple began pushing out the final version of iOS 11.2.5 to all iPads, iPhone, and iPod touches today after 41 days of beta testing. Highlights include a fix for the ChaiOS vulnerability, a persistent Now Playing bar in Music, and some signs of AirPlay 2 just in time for the HomePod launch on Feb. 9.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

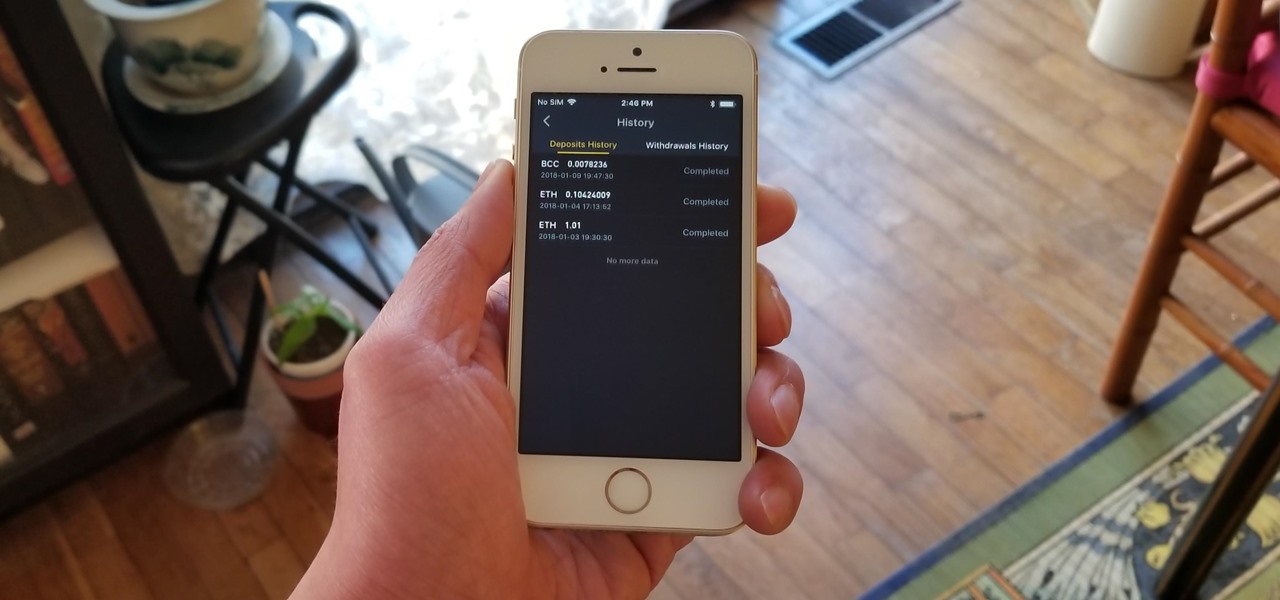
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

| Updated February 11, 2019 with new phones. When will my phone get Android Oreo? That's a question still being asked by many, even this late in 2018. Most OEMs have answered this question in one way or another, either releasing a stable OTA or confirming their device won't be receiving the update. We consolidated all these responses, and here's where we stand.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

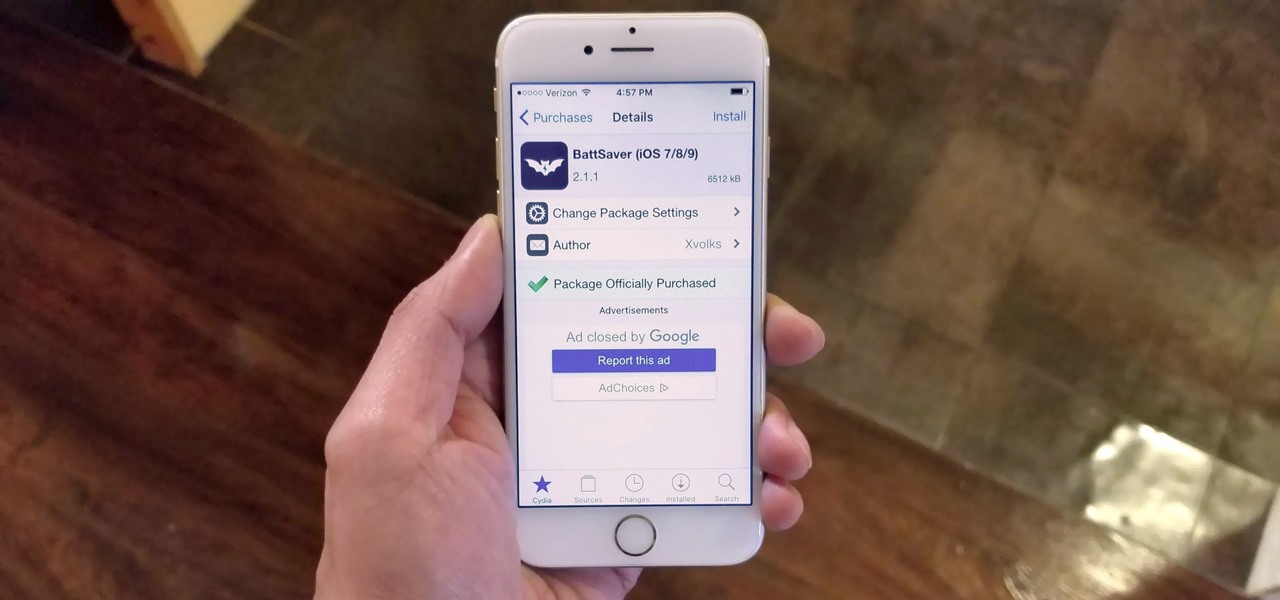
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.