Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

In this video tutorial, you'll find a step-by-step guide to how a n00b hacker (like you?) can get usernames and passwords easily through one of the security flaws of the Ethernet ADSL router. More than half of Internet users never change their default password which makes this "hack" easy. Take your time to read the text on the slide. For more, and to get started testing the security of your own Ethernet ADSL router, watch this hacking how-to.

Notice: This is probably not new to many people. This *IS* new for some people however, and meant for them! Post interesting cameras you find.

A killswitch is exactly what you think it is: A switch that kills an operation in an emergency situation when the operation can't be shut down in the usual manner. It shuts your operation no matter what the consequences.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.
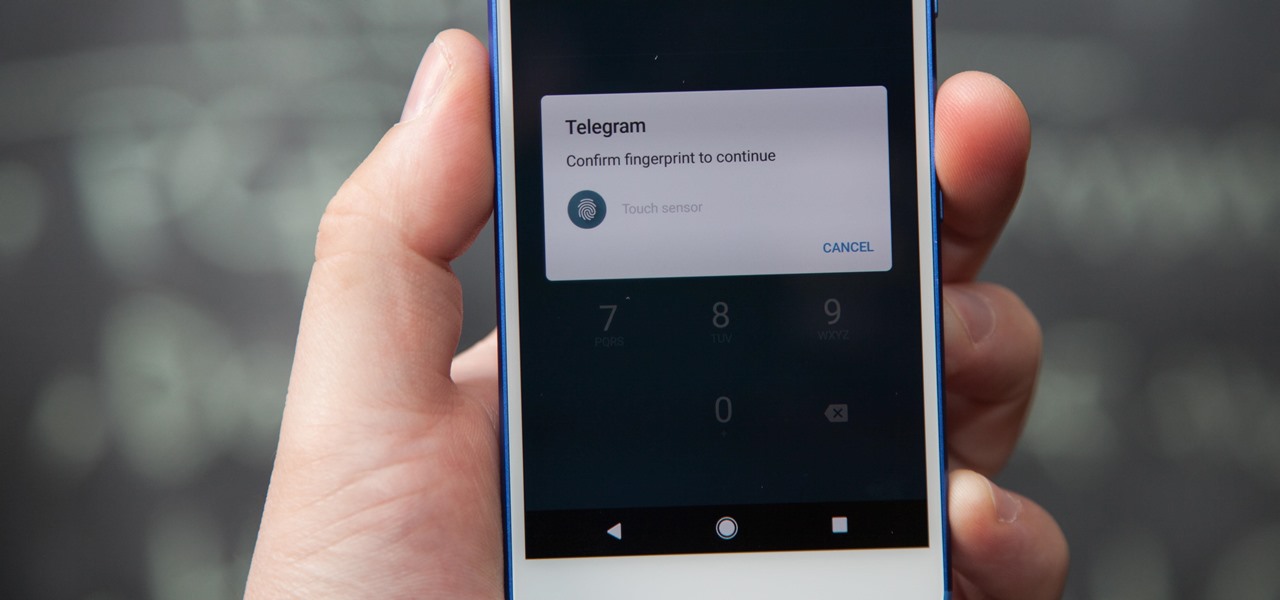
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

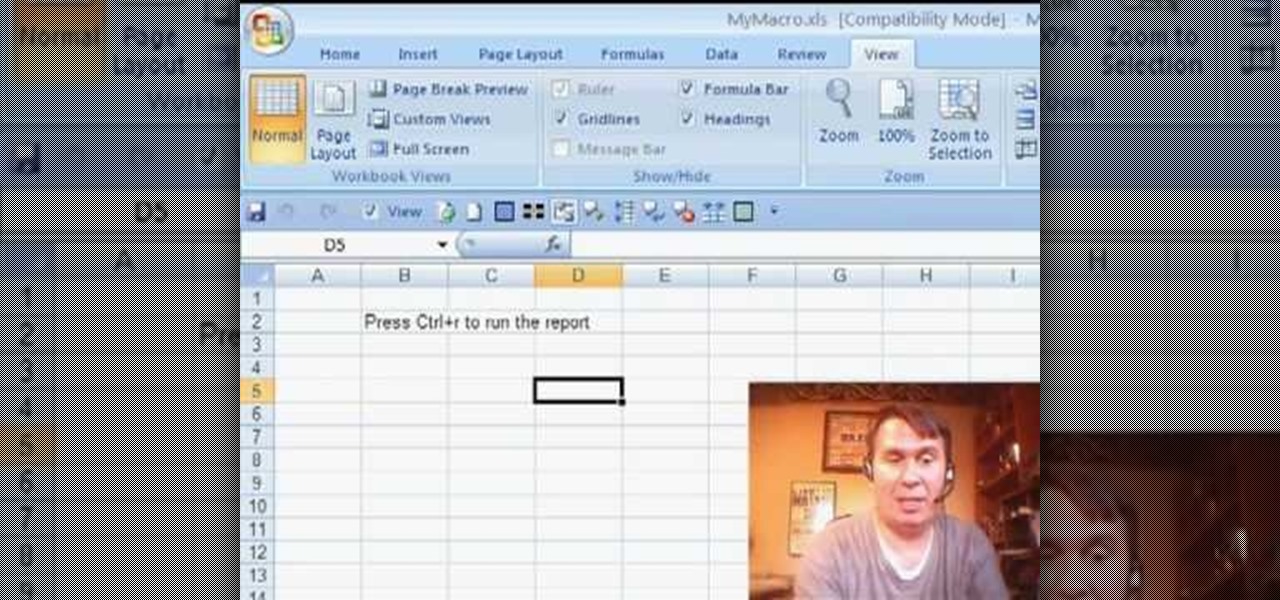
Some times when you upgrade your Microsoft Excel software to Excel 2007 your old macros may stop working. Some times this may be due to the settings and by enabling the macros you can get your old macros to work. Macros are turn off by default in Excel 2007. You can turn this on from the macro security settings. But the settings option is it self completely hidden. You cannot find it in any of the tabs present on the top of the program. Even the macros option present in the view tab has no se...

This how to video teaches you to cut ornamental grasses back in the spring to promote great summer growth. In the summer ornamental grasses look gorgeous, but after the winter these grasses are dry and are a fire hazard. Watch this video and learn how to easily prune your ornamental grasses.

Perhaps it's a coincidence that the Vuzix Blade smartglasses look like the sunglasses that a police officer would wear, but a new partnership with an AI software company makes the wearable a perfect fit for law enforcement.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Following in iOS 11's footsteps, Android 9.0 Pie will include a security feature that lets you immediately disable the fingerprint scanner as well as extended Smart Lock features. After initiating the feature, you will be required to insert your PIN, pattern, or password before any other unlock methods will work again.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

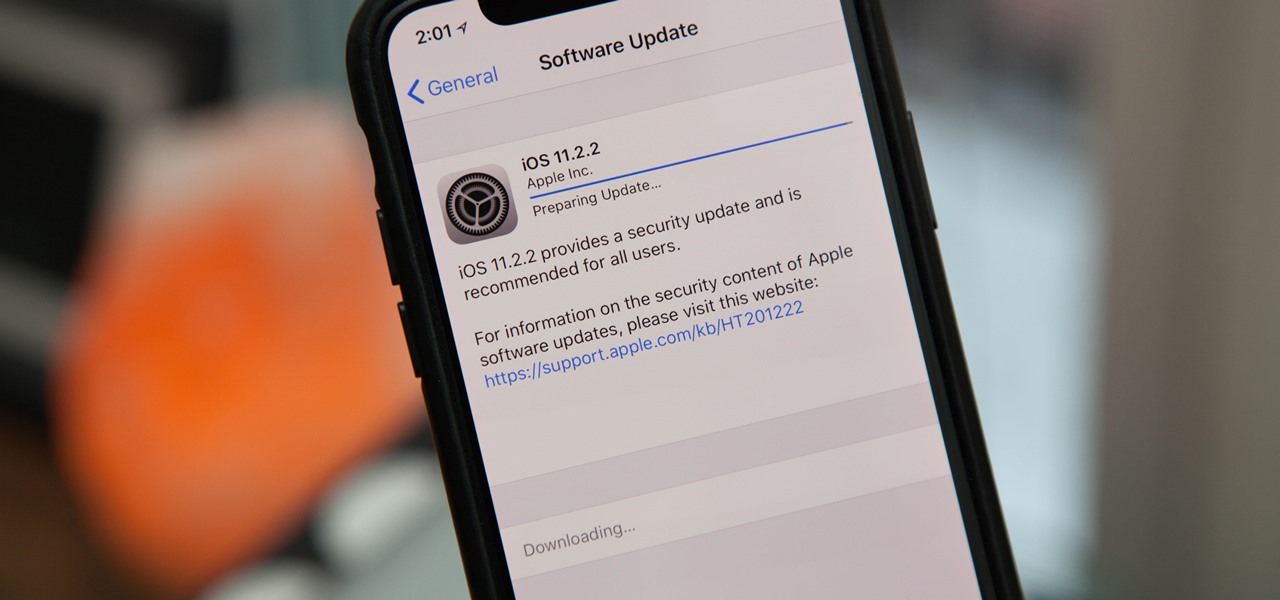
Apple released an iOS 11.2.2 update on Monday to iPads, iPhones, and iPod touches. The update comes as no surprise since news broke last week of a massive security vulnerabilities, named Meltdown and Spectre, which are found in smartphone chips throughout the industry. This update in large part addresses the security risks imposed by these chip flaws.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.

The May 2017 security update has begun rolling out to Nexus and Pixel devices, which is usually great news. It means that your device is now being updated to protect you from the latest exploits and vulnerabilities found in Android. At other times, though, security updates patch root methods like Dirty COW, which is extremely frustrating for users and developers alike. Especially since most OEMs don't condone rooting or even unlocking the bootloader on their devices.

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

Although John Chen of BlackBerry still sees Qualcomm as a partner, the chip maker and telecommunications company has just been given a preliminary order to pay BlackBerry $814,868,350 in royalty overpayments.

The latest Google Play Services update has somehow broken major functionality in both Titanium Backup and Substratum. Titanium Backup has suddenly become stuck at zero percent while restoring, and Substratum simply fails to apply themes anymore. Both of these apps do require root, but they've slowly become essential to rooted users, especially since apps like these come into play when you're deciding what your next phone should be.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have already been ported over, but any type of lock screen customization has been noticeably absent.

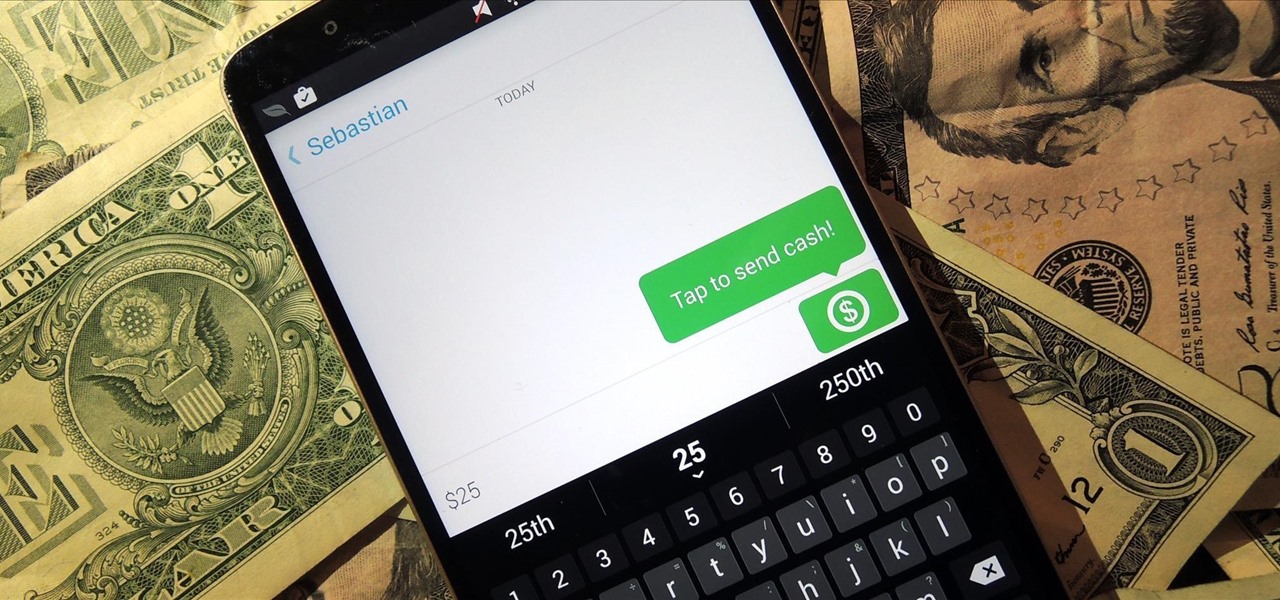
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Are you tired of your snoopy coworkers and friends lingering over your shoulder as you type in your security passcode? Unless you have the newer iPhone 5S with Touch ID that scans your fingerprint, you've only got a couple of security options—either a 4-digit numeric passcode or a cumbersome password.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

Ubuntu isn't just a cool sounding name, but pegs itself as the world's favorite free operating system. It gained its popularity for being lightweight, fast, and visually appealing, and now that great look and speed can be placed right on the lock screen of your Samsung Galaxy S3.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.