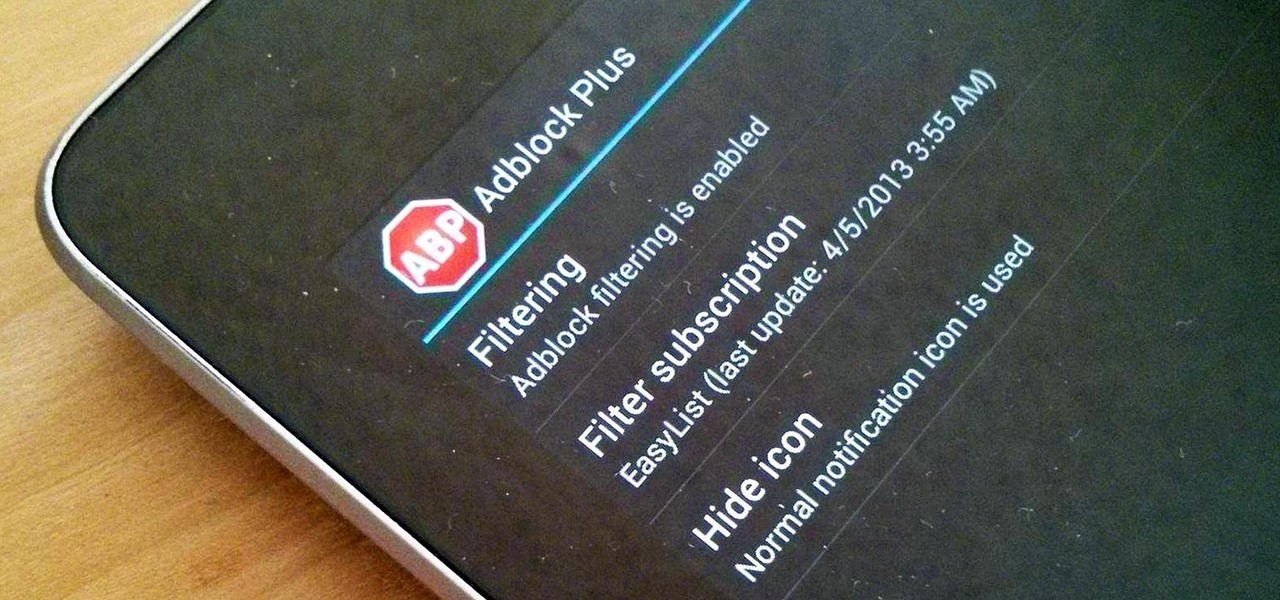
How To: Block Every Single Annoying Ad on Your Nexus 7 (In Both Apps & Websites)
Adblock Plus is a well known add-on for Google Chrome and Firefox that eliminates all of those annoying and obtrusive advertisements on the webpages that you visit.


Adblock Plus is a well known add-on for Google Chrome and Firefox that eliminates all of those annoying and obtrusive advertisements on the webpages that you visit.

There are so many unpleasant things about flying. You have to wait in line after line, take off your shoes, belt, and jewelry, and somehow make sure your luggage stays intact. And then, once you've made it onto the plane, there are the awful movies that most airlines play—if you even get a movie.

Imagine you're calling the court. You have this unpaid ticket and want to know if you can get an extension. First you type your ID number on your phone. Then the case number. Then your birthday. Then your social security number. Then you're directed to thirty different people.

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?

Microsoft just revealed the preview of its latest incarnation of Webmail, Outlook.com. One particular Outlook.com feature worth noting, is its support of multiple e-mail aliases. They're a great way to protect your primary e-mail address. And because you can't log in to your Outlook.com account with an alias, it adds another level of security. How To Add an alias

The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...

We all know the dangers of logging on to our personal accounts on public networks, but we pretty much all do it anyway—especially when it comes to Facebook. But the next time you're in a public place and can't wait to check out your Facebook news feed, use this simple trick to make sure that no one gets a hold of your password. In order for this to work, your mobile phone needs to be linked to your Facebook account. All you have to do is text "otp" (for one time password) to the number 32665.

Attention cheapskates and locksmith apprentices, this key copying solution is stunningly simple. We've really mulled over this one. As you can read in the comments below, people struggle with executing this successfully. But it can and will work. You just have to modify your key to fit your needs.

This ten-part video tutorial series covers all the new features and uses of Fireworks CS4. This is a great introduction to any user new to Fireworks in general, or wanting to learn what changes have happened from Fireworks CS3 to CS4.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

A Google trick to bypass computer security at your school and access blocked websites. Access blocked websites using Google.

How to bypass the web security at your school to go to restricted websites. Access any website at school.

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

What is Internet Download Manager? Internet Download Manager (IDM) is a tool to increase download speeds by up to 10 times, resume and schedule downloads. Have you ever wanted to increase you download speed form 4kps to 80kps? If you answered yes then you need Internet Download Manager. It can and will increase your download speed so you can get the files you want quicker and easier than ever before.

Final Fantasy 14 the MMO is now live. The special edition priced at $75 enables people to play eight days earlier than people getting the regular edition, which comes out on September 30th. Mine arrived yesterday and here are some pictures of what's inside the special edition version of the game:

It seems like nowadays, whenever Facebook rolls out a new feature, it's immediately controversial. Social Ads put your name and face in the spotlight, Instant Personalization shared your information with partner sites, third-party apps were allowed to access your home address and phone number, and now Tag Suggestions implement facial recognition software to automatically identify your friends in uploaded photos. Most are calling it problematic or creepy, some insinuate CIA involvement, and it...

Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websites let ad companies track our private usage. We've seen how Facebook mucked up their privacy controls. We even saw how websites like Gawker are prone to hackers stealing user information. And now, Etsy has made what was ...
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.

Health, safety and security are three main issues which determine if your cruise is a successful vacation.

Have you ever wanted to make your own Minecraft server on Windows? This tutorial will teach you how, without having to download Hamachi.

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end.

Just last week, the Flashback trojan scared a lot of Mac users. Now, there's yet another trojan spreading across Mac computers—SabPub. The same Java vulnerability that allowed Flashback in seems to be how this SabPub malware snuck in, along with an Office vulnerability, which was just identified this weekend.

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

US can legally kill Americans in terror groups You read it right. The US can now target Americans who are supposedly part of terrorist groups. Here's my analysis of Attorney General Eric Holder points (keep in mind though, these are point's brought up by MSNBC, original article here):

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

This is it! That last basic mission. Last Friday's mission was to accomplish solving HackThisSite, basic mission 11. This final mission in the basic series was made to give us the skills and a place to apply our Apache server knowledge. This will teach us how to traverse through awkward and custom directory structures.

Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).

We love tearing apart security here at Null Byte. Several years back, upon returning items to Wal-Mart due to a malfunction, I noticed something very peculiar about the way their overall procedure goes. I brought the item up to the desk, and the woman asked if it didn't work, which I responded affirmatively. Without a moment's notice, she takes it right off to the defective items area and asks if I would like cash or store credit.

Last Friday's mission was to accomplish solving HackThisSite, basic mission 8. This meant that we had to learn some more basic Unix commands.

Another great Community Byte in the bag! This week was really cool, especially with programming going on twice a week. We transitioned to the new times very smoothly with no one left behind, from what I can tell.

Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.

Welcome to another Community Byte announcement from Null Byte! The goal of the Community Bytes is to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you, so that is exactly what we do! In our sessions, we have started to both code and complete HTS missions. This means that there is something for everyone here, so make sure you join us.

Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do not show up on time, we have to go backwards and catch everybody up. This wastes time and will also make other users' experience less enjoyable when they have to watch and listen to the same thing 100 times. Punctuality as...

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

When Windows stores a password, it is done so by hashing the password in an LM hash and putting it in the Windows SAM file. In the scary moment that you lose your password, but don't want to pay some geek to have full root access to your computer, you need to recover it using Ophcrack. Ophcrack doesn't remove the password, or bypass it, it cracks the password hash using rainbow tables.