Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

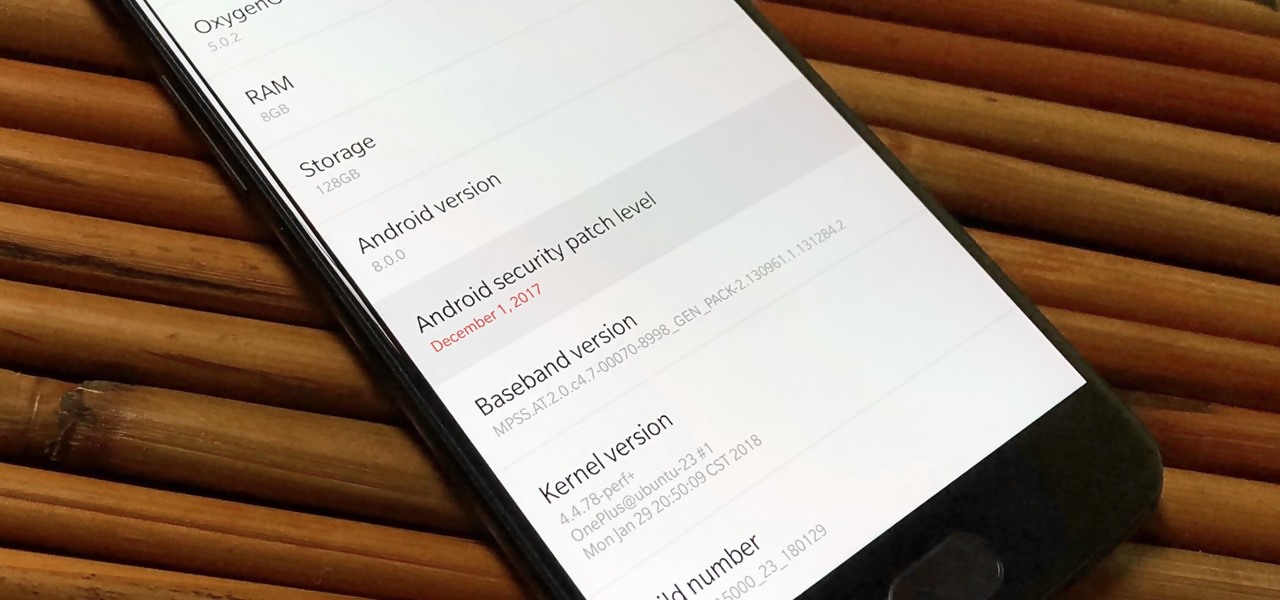
Samsung just began rolling out the Oreo Beta 2 to registered users of the Galaxy S8 and S8+. The update's changelog promises the inclusion of the October 2017 security patch. Unfortunately, after downloading the update, we've noticed this is not the case. Omission of the more recent security patch is notable in that it leaves devices vulnerable to several known exploits, such as KRACK.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

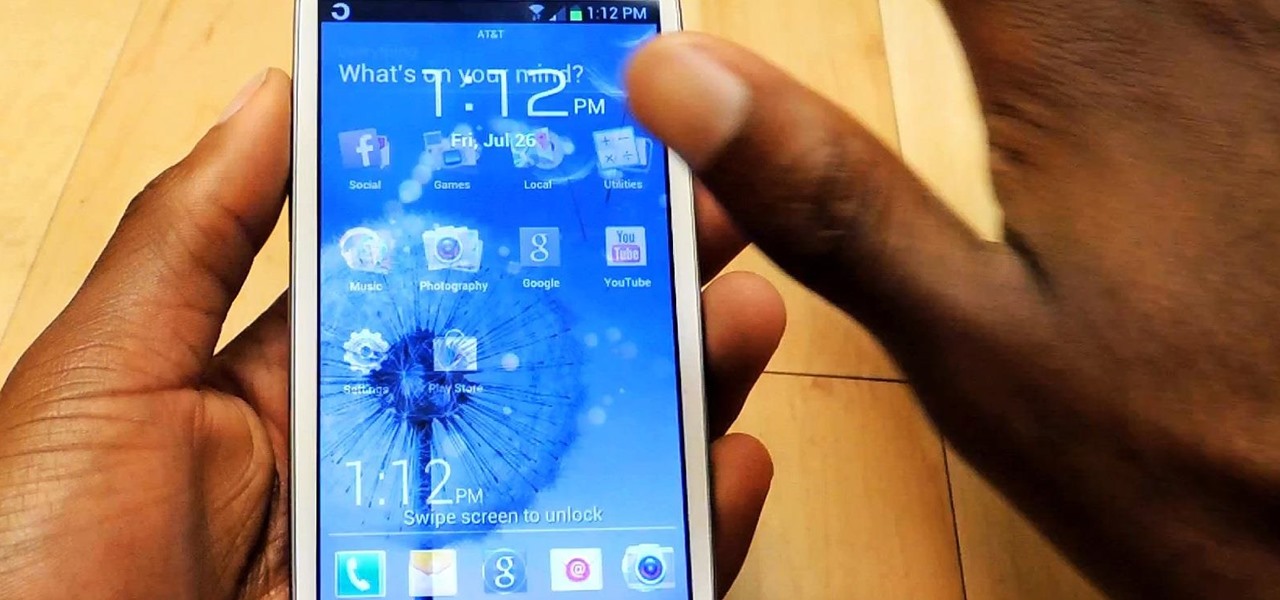
David Blaine has made millions off his magic tricks and mind-bending illusions, so why shouldn't we get in on the action, too? Well, your Samsung Galaxy S3 can do all kinds of things, but magic isn't one of them...yet.

If you own or have access to an auto-ranging or manual-ranging multimeter you can measure several different aspects of circuits, resistors, and the like. For example, you can determine the resistance, voltage, continuity, and current with the multimeter to help you determine the precision of a resistor. This guide will help you learn how to use a multimeter to perform these tasks.

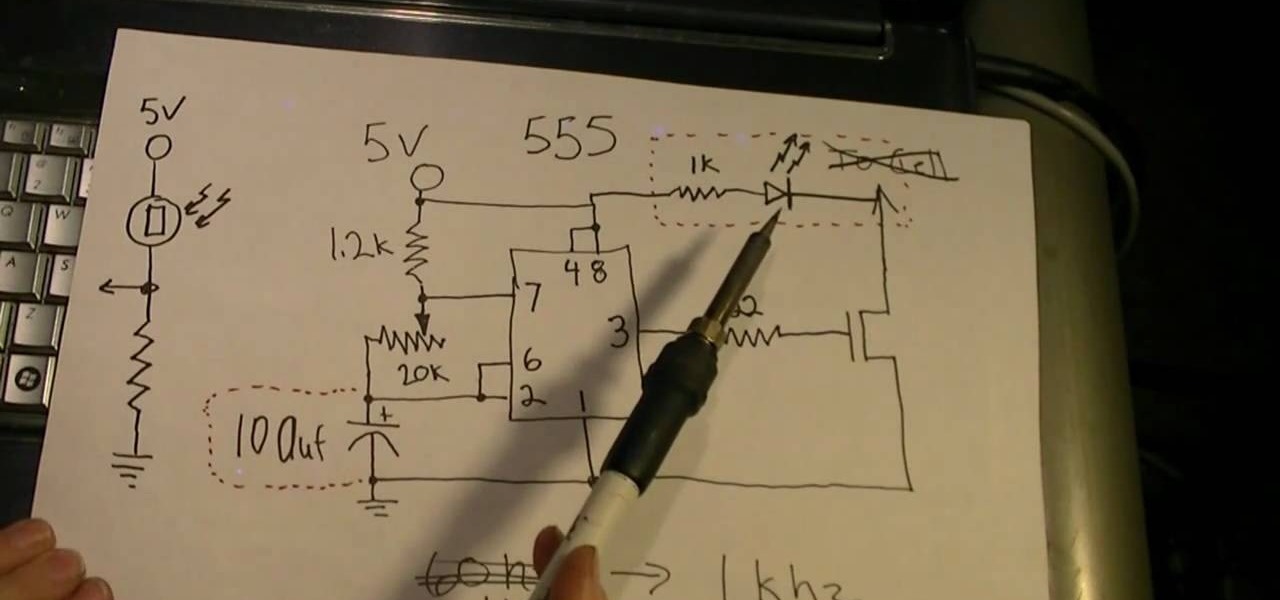
Phosphors are great for lighting up areas where fire will not burn, and also for keeping humans alive in very small quantities. Quenching phosphors allows you to use them for all sorts of cool projects, and this video will show you how to make an IR detection device with quenched phosphors and also how to measure temperature with thermally quenched phosphors.

In this video from TheCurrentCustom she teaches how to enhance your breasts. First she says you need to measure your breasts to figure out the right kind of bra for you. Take the measuring tape below your bust, and wrap around back, and then measure right above your bust. Round down to the nearest even number if you get an odd number. Then measure your bust size by wrapping the tape measure around the largest part of your bust, typically where your nipples are. Then subtract the bust size fro...

Cover a heart shaped or round box with designer paper

This is a video guide for measuring your foot and calf size correctly. This is important in order to properly fit shoes. It's a video intended for athletes and individuals sensitive to their foot and leg health. This is brought to you by a retailer that fits wide or narrow feet with proper shoes. You'll need a wall and a measurement guide. Measure for both feet and sometimes you have two different sized feet.

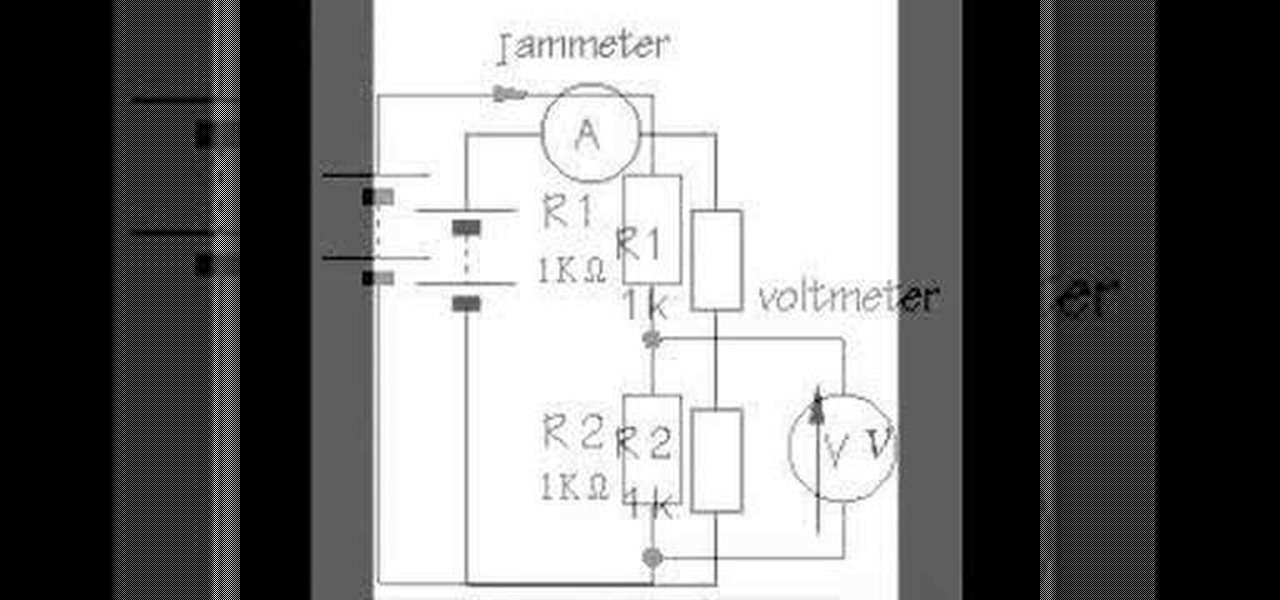
This is a guided hands-on laboratory activity to help a student understand the proper and safe use of a multimeter to measure voltage using an electronic labs kit. This video guides the student through the proper techniques for measuring voltage with a multimeter.

This guided hands-on laboratory activity to help a student understand the proper and safe use of a multimeter to measure current using an electronic labs kit. This video guides the student through the proper techniques for measuring current with a multimeter.

Often times a recipe will call for a sticky ingredient like ketchup, honey, or jam preserves. And if you're one to follow the recipe at a precise level, you'll definitely toss that ingredient into a measuring cup or spoon. But once you dump the ingredient out a lot of it gets stuck on the measuring tool.

One of the best ways to monitor your diet is by measuring your body fat content. In this three part tutorial, learn how to measure body fat using a caliper. A caliper is a device used to pinch and measure the fat on your body. A caliper is cheap, fast and accurate and makes an excellent alternative to electronic devices. Check out this video and stay on top of your new workout regime - mind the scale and use the caliper to know what's muscle and what's excess.

When doing woodworking projects, it's important to know how to measure things properly. Not doing so, can result in crooked pieces and unbalanced projects. So in this tutorial, you'll find out how to measure stuff without using a ruler in woodworking. Good luck, enjoy, and always play it safe!

Not sure what to do with that tape measure? Be the queen of DIY style and learn how to create a silver bracelet with an everyday object—like a tape measure! In just a few minutes, this Beads Baubles and Jewels project will take your style from drab to fab!

If you're making a bespoke shirt or suit, use this video to learn how to accurately take your neck measurement. You can go to a professional and have them measure it, but why waste time and possibly money when you can easily do it yourself. All you really need is a measuring tape and your neck. Enjoy!

If you are looking to purchase a new pair of pants or suit, you will need to know how to measure your waist size. In this quick tutorial, learn exactly how to use a piece of measuring tape to take your measurements and ensure your new outfit fits you perfectly.

Trying to lose some weight and inches off your belly, bottom, or legs? It is essential to measure your body before starting an exercise program. In this video, learn how to accurately measure your body parts for the purpose of monitoring your weight loss' progress.

Explore the universe in your microwave. Measure the speed of light with chocolate. The wavelength of light creates hot spots in the microwave that you can measure to show the speed of light. Chocolate has never been so useful.

In this how-to video, Ron Hazelton, do-it-yourself expert, shows you how to get exact measurements with a tape measure, even when the tape measure "rolls" to an inside corner. Quick and accurate measurements will make any home improvement go faster, and turn out better. Watch this video tutorial and learn how to get exact measurements with a tape measurement.

Take a look at this instructional video and learn how to use the tape measure tool in Google SketchUp. You can use this tool to measure edges and distance, create construction geometry or dashed guidelines, and resize individual groups or the entire model. This tutorial covers all three of these functions in a step by step guide.

This video explains how to read a tape measure. Discover how tape measures are divided into different fractions. Color coding is also used to help with spacing things 16 inches on center.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

As far as overall security updates are concerned, we all know that iOS reigns supreme over Android. But just how bad do Android devices fare against Apple in general? A recent report will have you second guessing some companies the next time you're in the market for a handset.

Samsung's 2016 line of smartphones has a new update, at least for the devices on AT&T. The update brings the Galaxy S7 to version G930AUCS4BQL1 and the Galaxy S7 Edge to version G935AUCS4BQL1. Here's what's on the table.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

Locking individual apps on your Android device gives you an added layer of security by safeguarding app data from unwanted attention. I personally prefer using an app locker over a standard lock screen because my kids play with my phone, and they've completely disabled it after inputting the wrong PIN. So app lockers give me the right balance between giving my children access to my device, and the security of locking down my data from would-be intruders.

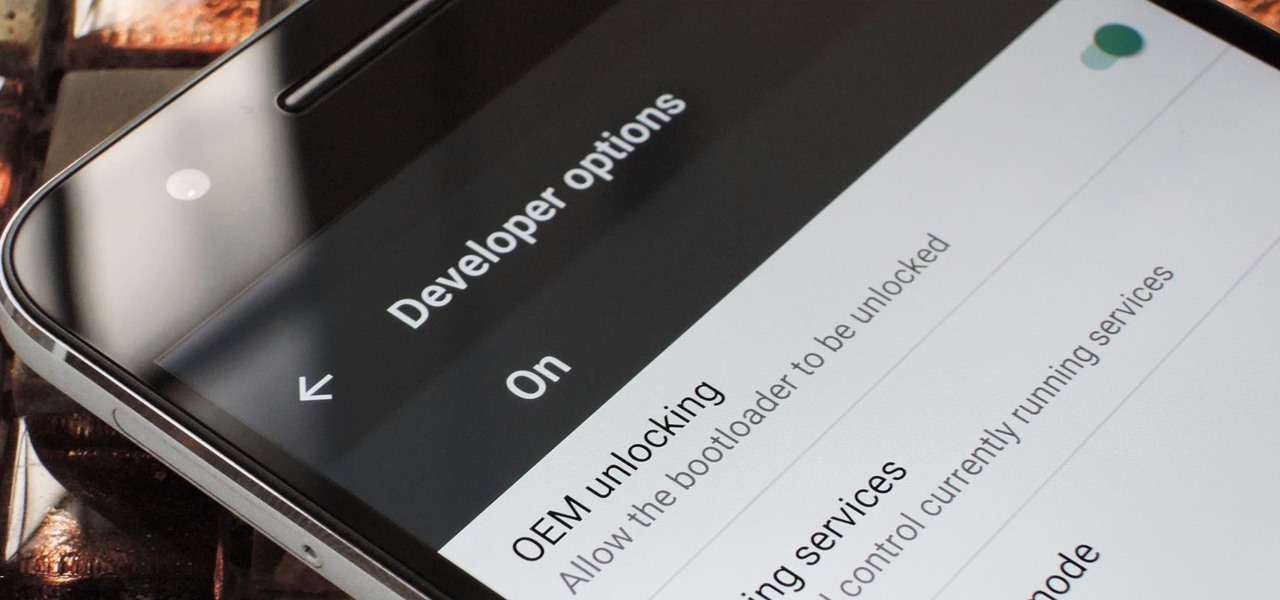
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.