Are you tired of your snoopy coworkers and friends lingering over your shoulder as you type in your security passcode? Unless you have the newer iPhone 5S with Touch ID that scans your fingerprint, you've only got a couple of security options—either a 4-digit numeric passcode or a cumbersome password.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

Ubuntu isn't just a cool sounding name, but pegs itself as the world's favorite free operating system. It gained its popularity for being lightweight, fast, and visually appealing, and now that great look and speed can be placed right on the lock screen of your Samsung Galaxy S3.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Keep your possessions safe from thieves with these tips. You Will Need

Burglary is common, but is also quite preventable with these tactics. You Will Need

Most oil cooler kits cost $250 or more, but the guys at Poor Man Mods show you how to make your own oil cooler for only $60! Oil coolers are great security for longer lasting and better performing engines, especially high-performance engines and in warmer climates.

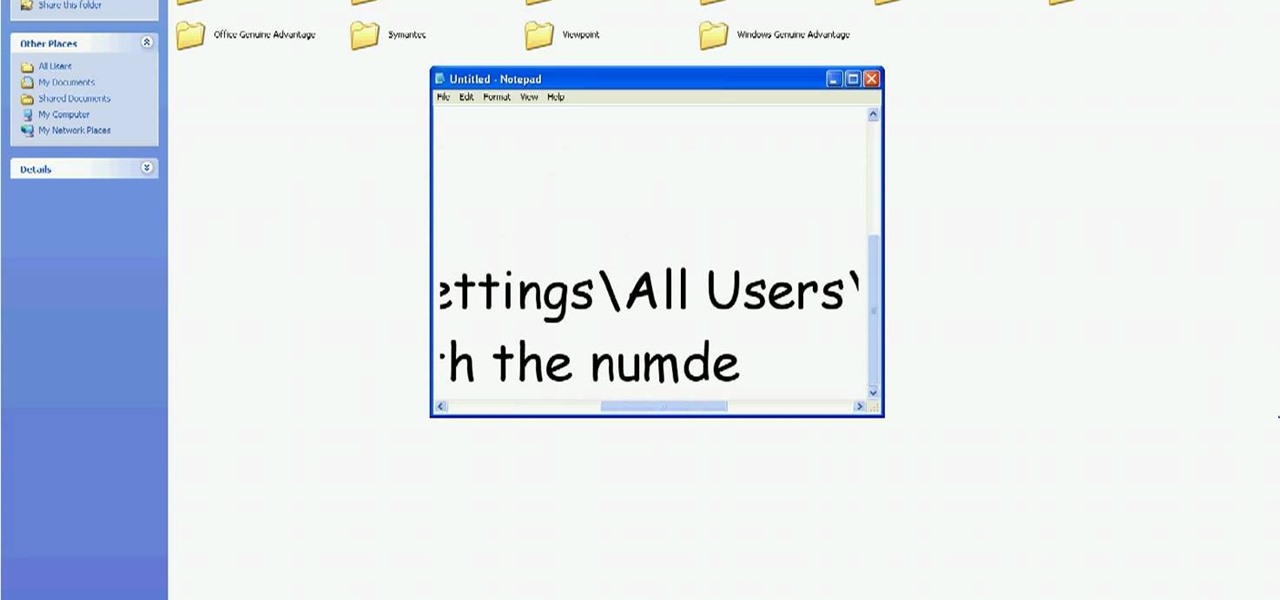
In this tutorial, we learn how to delete Security Tool from your computer. First, you will need to restart your computer. After this, go to your documents on your computer. Then, type in "Type C:/Documents and Settings\All Users\Application Data". After this, delete the file with all of the numbers. If you now get an error that says "access denied" then restart your computer again. Once the starting screen appears, press "F8", then select safe mode and redo the steps that you just took. After...

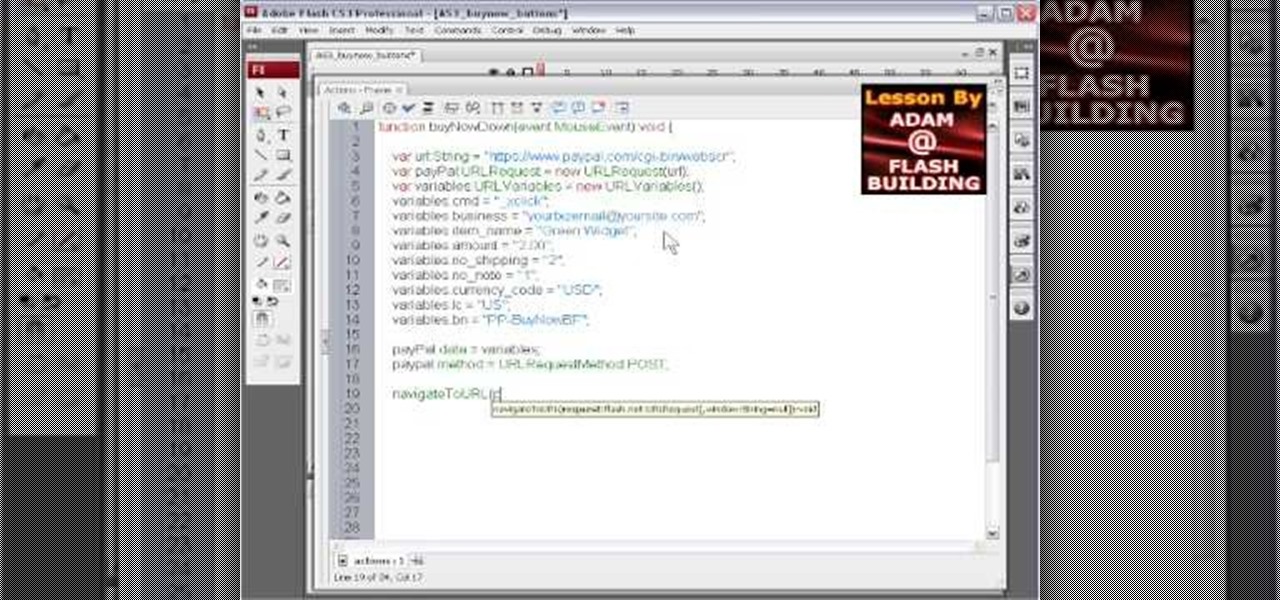
Add an extra level of security to your website by creating your own dynamic 'Buy It Now' button for PayPal-using visitors to your website. Coding this button is very easy, and you can even animate it to draw more attention to your webstore.

Deadbolts are a security lock which are usually put on exterior doors. Many saftey experts recommend increasing the strength of your home deadbolt lock. This quick tutorial teaches you how to make your deadbolt extra secure and increase the safety of your house.

Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and using high-security passwords yourself, watch this video tutorial.

Need to install a pre-hung door? Lowe's has your back. A quality front door makes a positive first impression on guests... not to mention, a weathered and worn door can compromise your family's safety and security. In this video, learn how to install a new pre-hung exterior door with the following instructions from Lowe's.

First of all cut of the top and the bottom of the cylinder to get two circles. Now take a scissors and cut of the cylinder into two halves from the top to the bottom as shown. Now you get a rectangle shape. You can easily measure the length of the cylinder but to measure the base is a problem. So mark a point on the table with tape and also make a mark on the can or the object you want to measure. Now place the two points over each other. Now use a ruler as a guide and move the can so that th...

This is a great way to turn your treadmill into a walk station quickly and cost effectively. You only need a few things for this project: a tape measure, four shelf mounting brackets, screws, a drill, and a shelf.

In figure competition, or female bodybuilding, measuring and keeping tabs on body fat is important. Check out this three part tutorial for information on how to use a digital caliper to measure body fat. Some of the advantages of a digital or electronic caliper include the fact that it takes an accurate, easy to read measurement in seconds, that it beeps so you know exactly when it is ready, and it is very simple to use. Another great feature of a digital caliper is that you can set it with y...

iPod and iPhone home automation remote control using Girder is only an install away. Run the lights, heat, security system among other things in your space age home for the 21st century. Make your home a modern marvel with this app for iPhone.

In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on a Microsoft SQL Server (or SQL Server Express.) See how easy it is to obtain a shell in a Microsoft SQL database with this how-to.

In this installment from the Unorthodox Hacking series of computer security tutorials, you'll learn a number of methods for hacking Windows shares as well as means of mitigating those hacks. For detailed instructions on Windows shares, and what you can do with them, watch this helpful video guide.

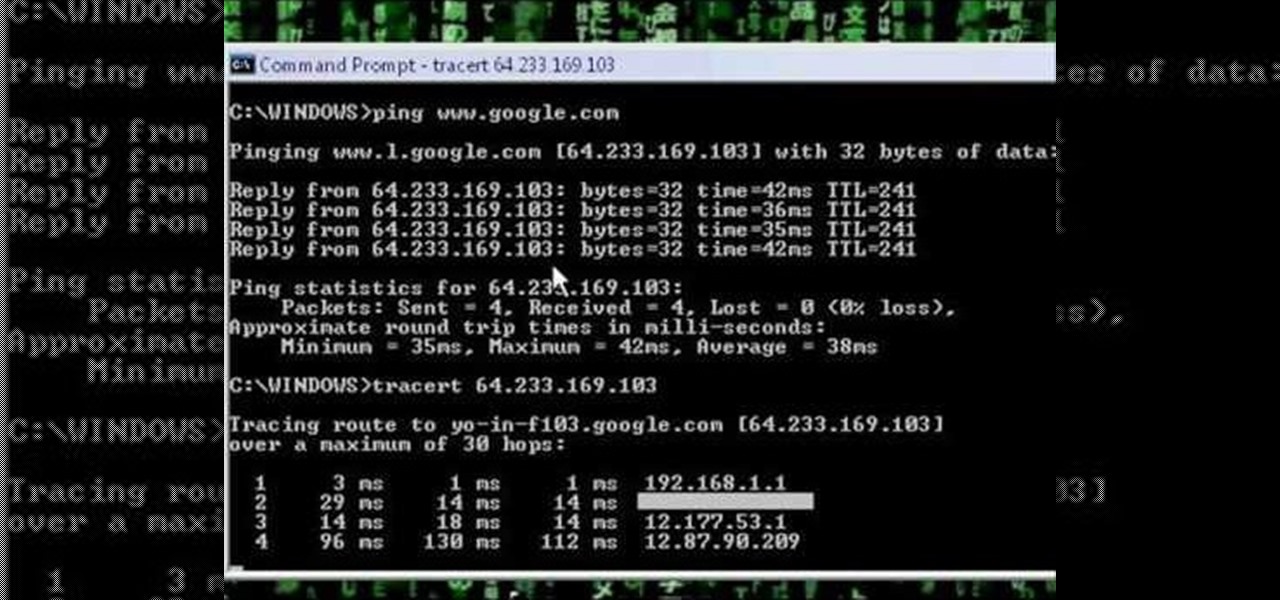
A network security tutorial on using ping and tracert to show th IP of a webserver, your own IP, your ISP's IP, who they connect to, and what computers your request goes through before reaching a destination.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

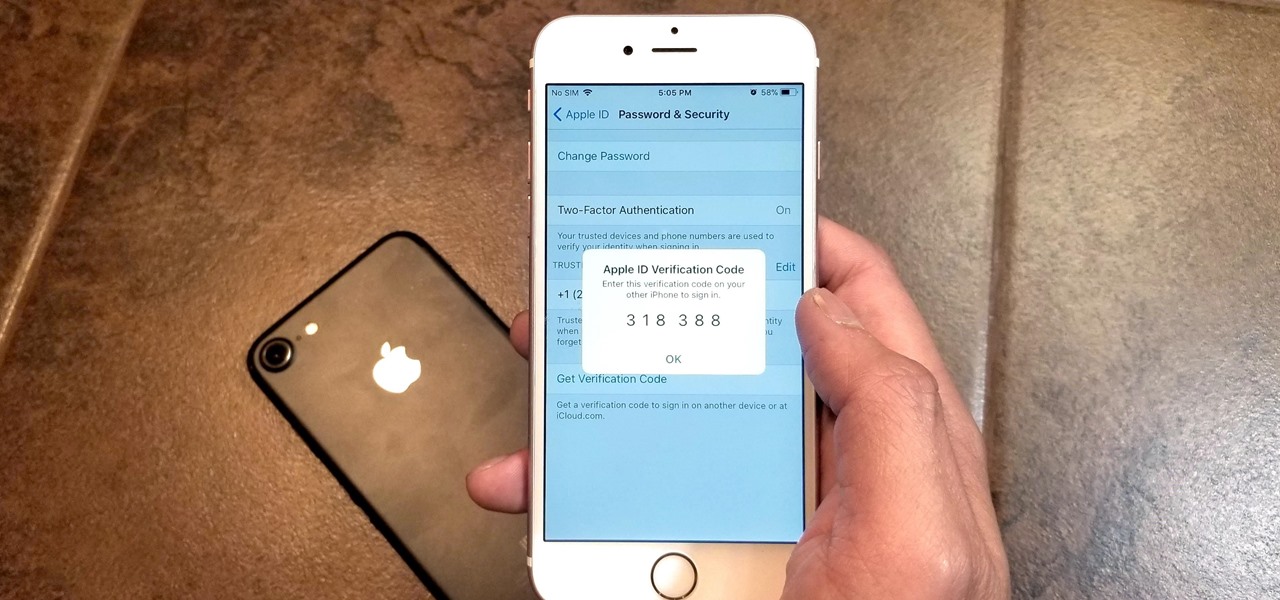
Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

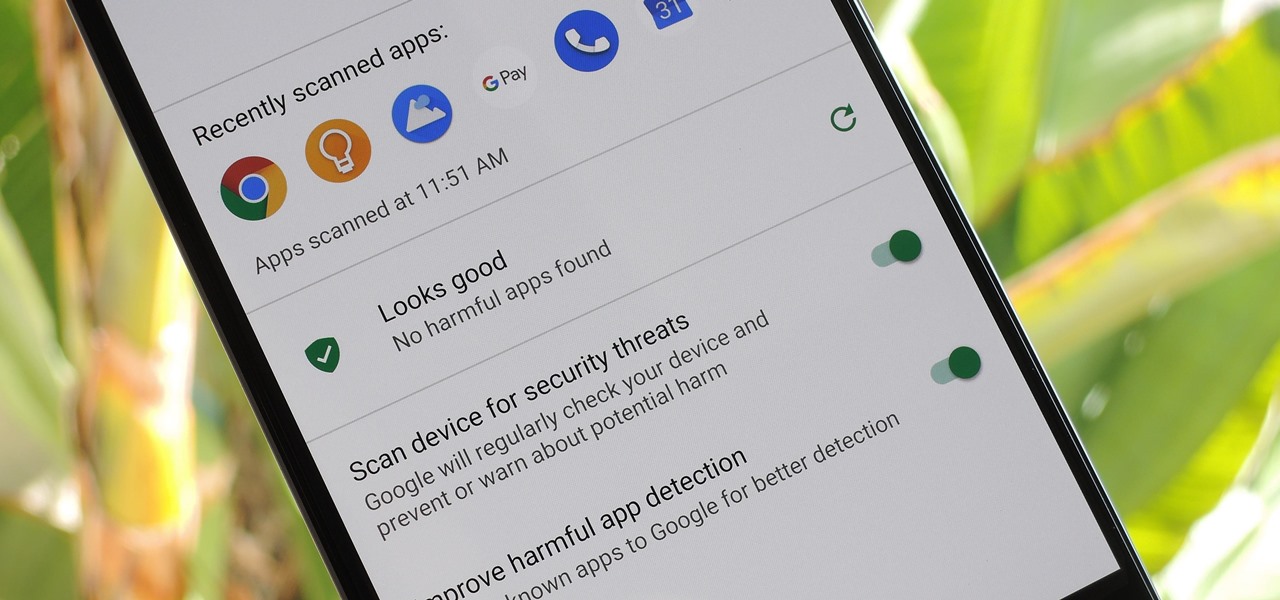
According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

Apple released the fourth public beta for iOS 12 to public beta testers on Tuesday, July 31, just one day after the company seeded the fifth developer beta to eligible users. Both releases are surprising, as Apple had appeared to stick to a two-week release schedule for the iOS 12 beta season, and these updates both came one day earlier than expected.

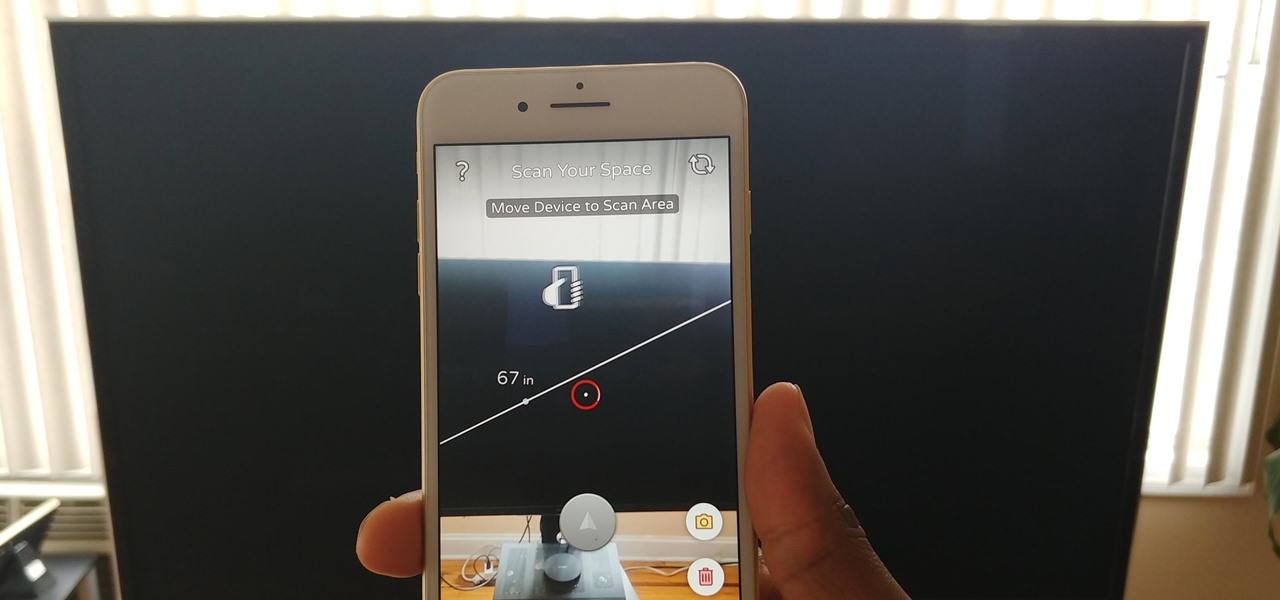
Thanks to Apple's ARKit 2.0 augmented reality framework in iOS 12, we now have a "Measure" app built right into our iPhones that can measure real-world objects. No more physical tape measure or ruler. No more guessing. Just whip out your iPhone, open the app, put your camera, and get measurements. Before you do, however, there are a few things you'll want to know.

Our phones have evolved past a simple pocket computer. They have become more like Swiss Army Knives, opening up possibilities that were previously considered Sci-Fi material. Thanks to the recent push into augmented reality, a new world of tools is becoming available to mobile users.

Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

CyanogenMod has been building upon open-source AOSP apps for many years now. They've made improvements to apps like the stock SMS client, the stock Audio Mixer, and a whole slew of others.

I've used the flashlight feature on my iPhone more times than I can count. It's an invaluable tool that's super easy to activate; just pull up the Control Center and hit the flashlight icon. However, turning it off isn't always as easy, especially when you're on the lock screen.

Android enthusiasts have their own opinion as to whether you need antivirus software on an Android device. This debate will never end, provided that Android malware is in existence. This guide is not here to say, "Yes, you need antivirus," or "No, you don't." It's to give you all the facts, so that you can make a decision as to whether or not you need antivirus on your Nexus.

Screen timeouts serve mostly as security measures and energy savers, but they can also interrupt you when you're reading a book or editing a document. There is no built-in way to manage screen timeouts on a per-app basis, but if you've got root access, you can do just that using Never Sleep from Android dev Hamzah Malik.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

» Homeland Security Report Lists ‘Liberty Lovers’ As Terrorists. A new study funded by the Department of Homeland Security characterizes Americans who are “suspicious of centralized federal authority,” and “reverent of individual liberty” as “extreme right-wing” terrorists. » British police get battlefield weapons.

In this tutorial, we learn how to make a pole camera with John Park. You can take some amazing pictures by just using a pole to mount your camera onto and take pictures with. Most cameras will work with a general pole as long as they have a tripod mounting pole. To help you press the shutter button the camera while it is up in the air, you will need to create a rig that will press it when you trigger it to press. After this, you will need to build an inner frame that tilts up and down to take...

In this video, we learn how to play "Losing My Religion" by R.E.M. on guitar. This song will be done in the open position. Start out with the intro, which will have the chords: F, A minor, G, D minor, D, E minor, and C. This song does not have any split measures, so every chord should get one to two measures as you play. Play this slowly, then when you have it repeat this four times and change up on the fifth time. Once you are finished, you can breeze through the song and simply learn the ch...

When in repose upon the toilet, the last thing most people want is for something to jump out at them. And that is exactly what will happen to them if you pull this prank. It turns out that the actual tape from a tape measure is a great little prank tool, and in this video you'll learn how to attach one to a roll of toilet paper so that when your victim attempts to wipe, they will be attacked by tape and scared... witless. Yes, witless.

Using a Strat guitar since it has a basic type of string system, this demonstrator shows how to properly adjust the string height of a guitar. In order to do this, one must use an Allen wrench screw or a screwdriver for each saddle, a flathead screwdriver, and a 64th ruler. The viewer is given an example of a height that could be used for a solo guitar. It is important to measure the distance you want correctly by measuring from the top of the fret, not the fretboard to the string. This video...

In this how-to video by Lowe's department store you are showed an intermediate do-it-yourself installation of beaded plank paneling and molding. He shows where you can get information on how to do this but then goes on to show the different paneling and molding you can make. He goes on to show how to measure and cut the paneling to your desired length. After describing how to measure and cut the panel he goes on to show how to prepare the paneling with the paint. He goes on to show the differ...