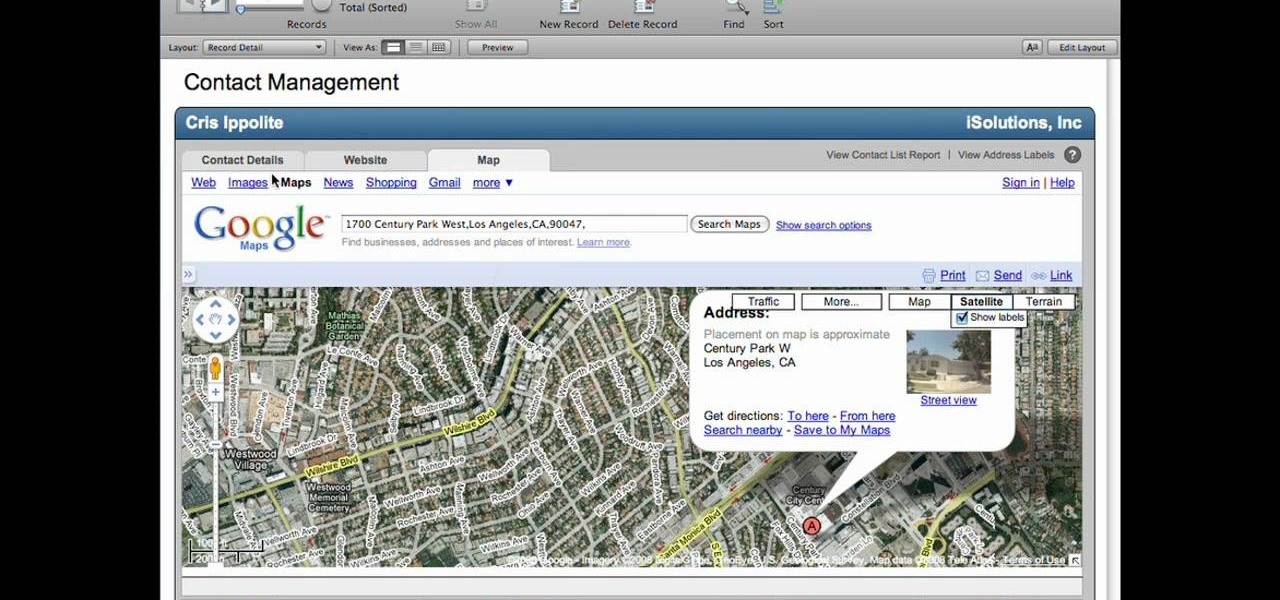
Lyndapodcast teaches you how to create a database using FileMaker Pro 10. You can link one contact with multiple addresses and information and store that into a single database. You can also add content from the web into your FileMaker layout, including maps, pictures and music. You have a security module where you can set permissions for the users using the database. You can also publish the FileMaker database to the web. For this go to File - Sharing - Instant Web Publishing. Another featur...

In this video you will learn how to do a Flair bartend: vertical toss grab reverse grip. Start this trick with an over hand grip, then reverse grip right hand. Reverse grip and pour. Make sure you are holding your bottle security. Your holding the bottle and spinning with the other hand. You might have to practice the end pour so you don't spill as you bring the bottle back up. This video does the sequence many time so you can get the hand work done correctly.

This video will allow you to view your saved usernames and passwords in Firefox. This may be useful for users in case you forget what your user names or passwords are for different sites and would like an easy way to find them. Under the Firefox toolbar, go to "Tools" and then "Options" in order to get a popup which will allow you to view different aspects you can change in Firefox. Go to the security tab and then click on the button which says "Saved Passwords" in order to view all your save...
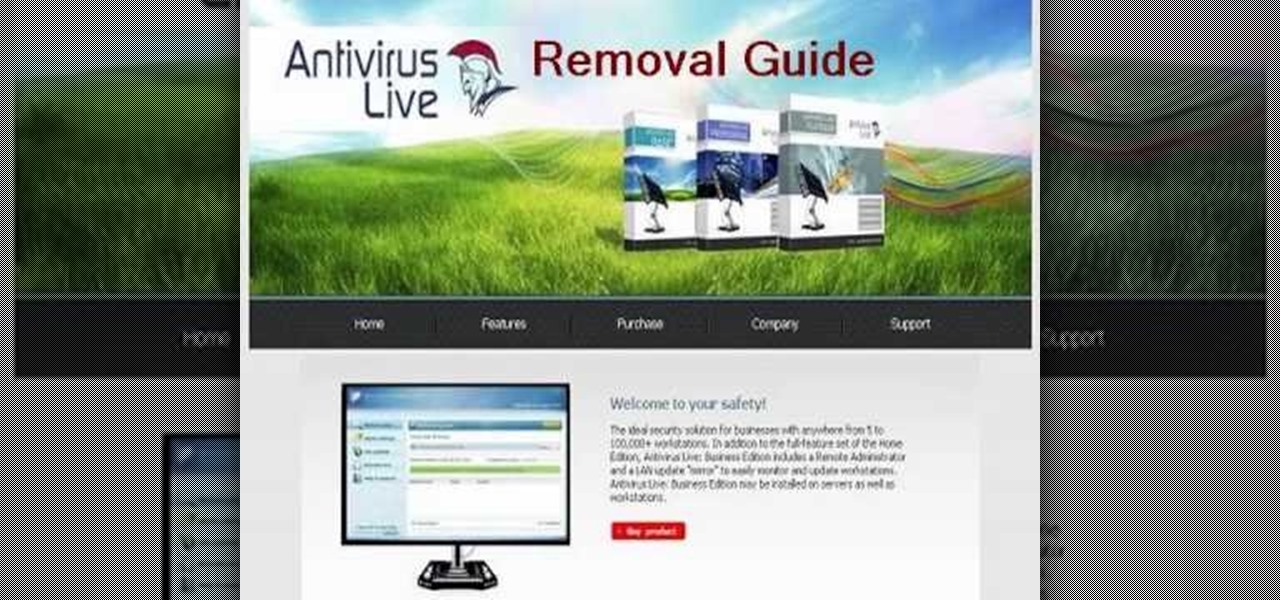
AntiVirus Live is a fake antivirus software which comes onto your system and asks you to buy it. It doesn't provide any security to the computer. Here is the procedure to remove it: (1) disable the proxy server for your LAN in Internet Explorer. 2) download the process explorer from ms technet. 3) locate and kill the sysguard.exe. 4) finally remove AntiVirus Live. After following all these steps reboot the computer. Protection against future intrusion is mentioned. You should be aware of the ...

This video shows you how to easily set up Bluetooth on your Motorola Droid phone and use it with a Bluetooth headset. The first thing you have to do is go to Settings and then go to Wireless and Networks. In the pop up menu, you have to go to Bluetooth settings and check the first box. That will turn Bluetooth on. Next, you have to turn on your Bluetooth headset device and press the Scan for Devices button on your phone in the Bluetooth settings window. Insert the password and hit OK. That's ...
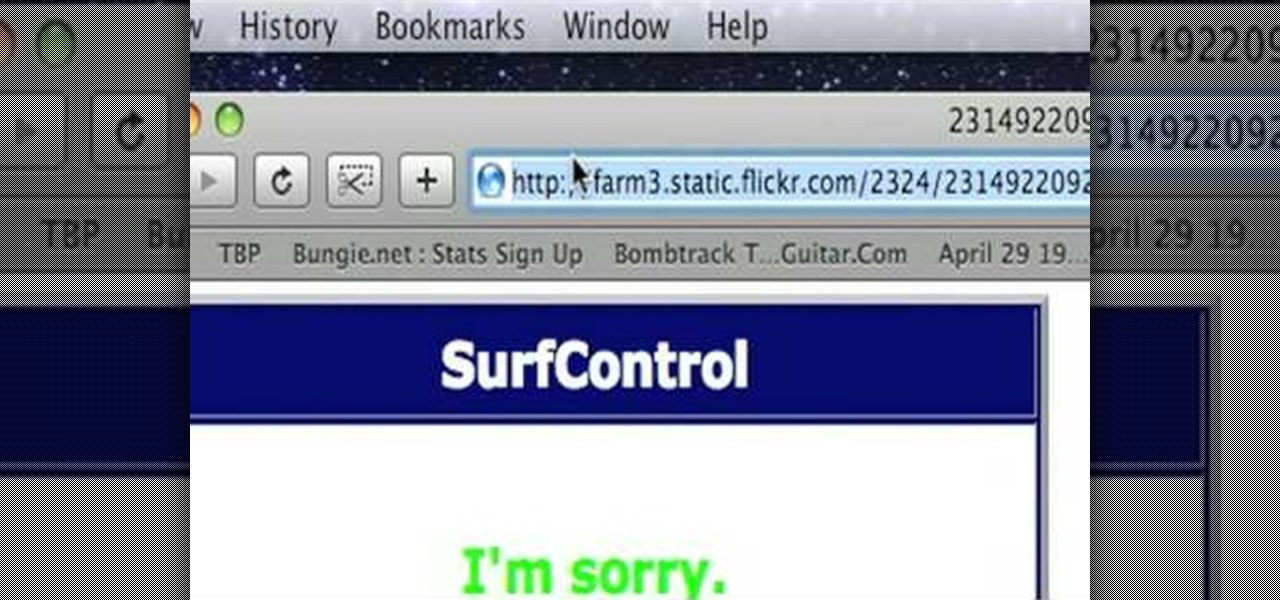
The author shows how to bypass SurfControl and access blocked websites at school. He shows how to open the OperaMini website from Google and to access the demo of OperaMini in that website. Now in that demo we can key in the website address and easily access the website from there. In this manner we can easily bypass small security software like SurfControl. If you are having trouble accessing websites because of SurfControl just follow the steps in this tutorial and you will be able to acces...

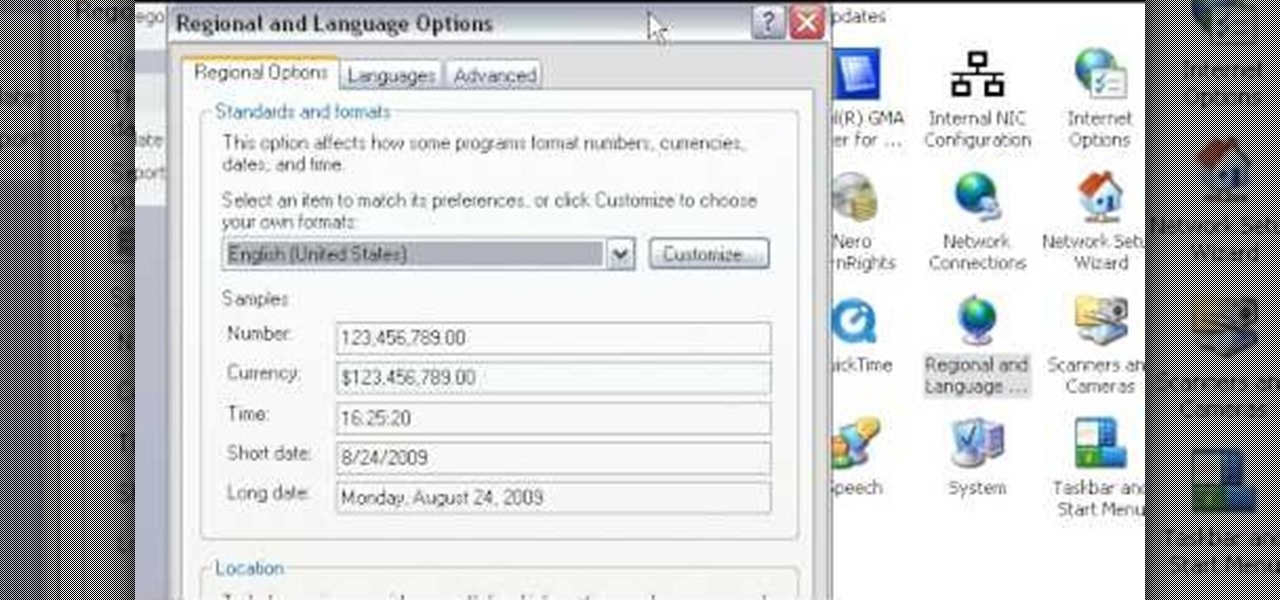
This video will show you how to change your time from military time to the 12 hour time scale on a Window's computer. After being infected by a virus or if you accidentally changed the time on your computer, you can easily change the time display on your computer screen back by following the easy steps in this video. You will first have to go to the Start bar and find the Control Panel. From the Control Panel, find Regional and Language Settings and choose to customize your regional settings....

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to install a Wii homebrew hack using the Twilight Hack.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup Wii games to SD to play in HD.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn a Fon+ wireless router into a network tap.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to get free WiFi by tunneling through DNS.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a web-enable remote controlled tank.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to make a Twitter tamagotchi bot with PHP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to set up SSH tunneling to securely transmit HTTP traffic.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to session hijack with a pineapple.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to boot Windows from a USB flash key.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to configure Cisco and iptables firewalls with a utility.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to packet sniff networks with the fundamentals.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to break down IP and TCP header with Wireshark.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn any Windows application into a service.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to organize your desktop with Microsoft Scalable Fabrics.

Low battery – two words you never want to hear. Banish them with these tips. You Will Need

Beat the Level 2-3 Boss in Resident Evil 5 via this walkthrough and gameplay. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

When setting the shutter speed and aperture of a camera, use a light meter to take a reading, then set the aperture or shutter speed, depending on which is more important for the photograph. Set the shutter speed and aperture of a camera with the tips in this free instructional video on photography tips from a professional photographer. For novice photographers, setting the shutter speed and aperture is an important first step in mastering the art of photography.

Whether you're dressing up as a snow queen, maybe from Narnia, or just going for some sort of wintery look, this how-to video shows a way to make some stunning costume makeup. The cosmetics used to create this look are Coty Translucent Setting Powder, Matte Texture Cream, Sugar, Brows: Platinum Plus Pro Lash Mascara, MAC Pixel Paint, MAC Silver Fog Pigment, MAC, Dovefeather Eye Shadow liner, MAC Facsinating Eye Kohl, Dovefeather Eye Shadow, Platinum Plus Pro Lash Mascara, Makeup Forever White...

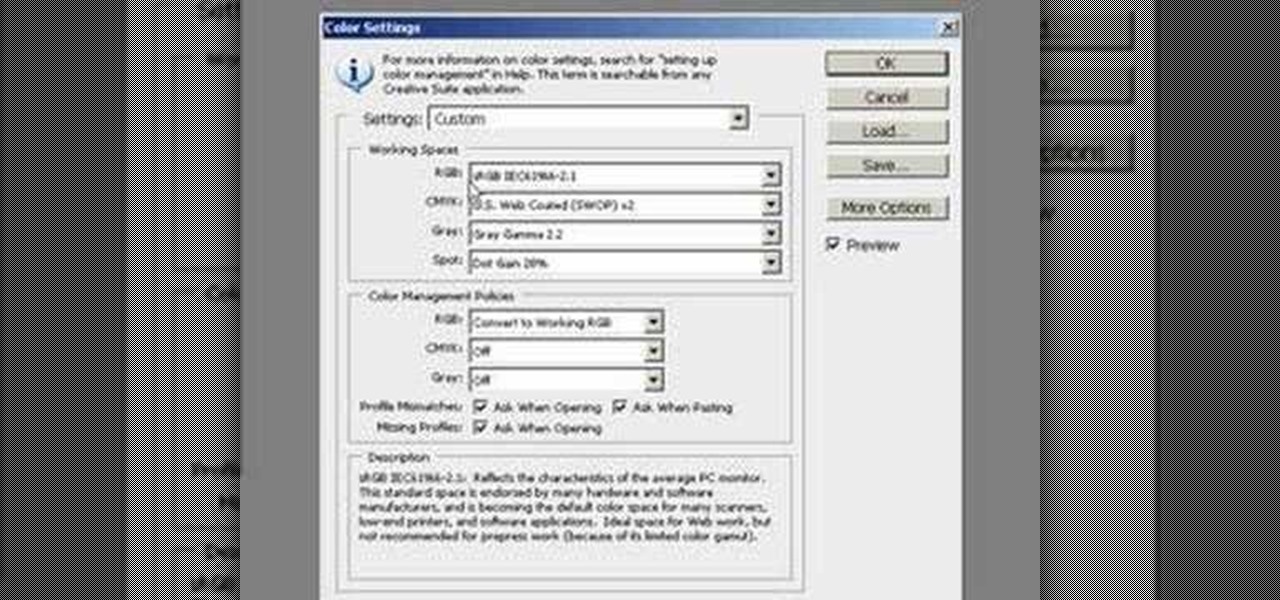
If you are a professional photographer or artist, as great as Photoshop CS3 is, it doesn't do you much good if your print quality and coloring isn't correct. This software tutorial shows you how to set up your Photoshop workspace to be sRGB in the Color Settings dialog for the purpose of lab printing.

Add to your jewelry making techniques by snap setting gemstones. This jewelry how to video tutorial demonstrates the proper way to snap set a ring. Begin by placing your stone face down on a flat surface. With your casting in hand gently push the ring setting over the gem stone. It should securely snap into place.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Do you do a lot of printing on your Apple computer? In this tutorial, Molly Stanberry from MacMost.com demonstrates the extended print settings in Mac OSX. Learn to set up custom print options with this how-to.

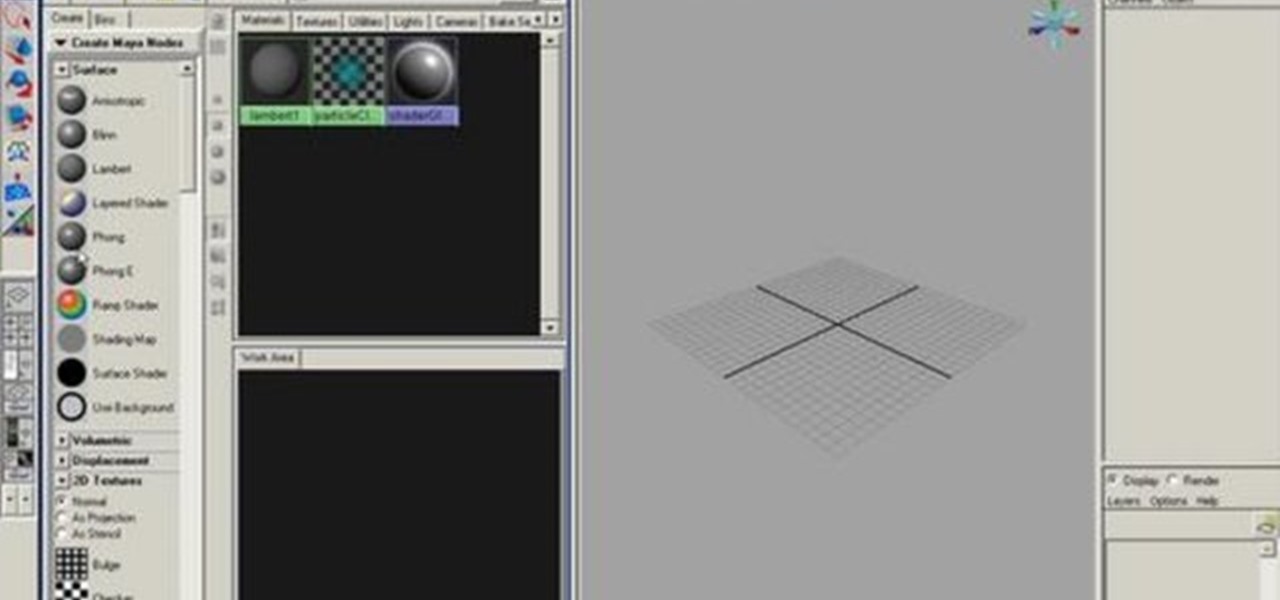
First off, a bit of explanation. The hypershade in Maya is a quick way to create and connect rendering nodes, which include textures, materials, lights, and special effects. Hypershade is one of the most important features in Maya to learn and master.

There’s an art and a science to setting up camp, and this how-to video is going to teach you both. Setting up a camp sit is difficult for most, so these simple instructions can teach you a lot about how-to set up your campsite.

Check out this video tutorial to see how to construct an alarm system, that's based on the principle of motion detectors, which work by touch. It's very useful to catch unpleasant visitors red-handed. So make sure your chocolate bar never gets snagged again, catch the bandits with a motion detector alarm! Or just keep you kids away from the birthday present closet where peeping is not allowed.

This is a tutorial that shows you how to view and control your computer screen from your iPhone/iPod Touch. But this method is for people who have a jailbroken iPhone/iPod Touch. This works on Edge and Wifi. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

Did you know that you can add parental controls and change font sizes in iTunes? Learn how to customize the various settings in iTunes to fit your needs.

See how to make an X10 wireless security camera into a nice helmet cam on the cheap in this three-part video. All it takes is an X10 camera, ten bucks in parts, and two hours of your time.

Setting up the menu's and Custom Functions of the Canon 1D MKIII camera. Highly technical and boring except for owners of the Canon 1D MKIII who want some insight to setting up this camera.

From Windows 95 through Windows XP, setting file and folder permissions was accessed in the same way. With the introduction of Windows Vista, many things have moved, including this feature. While it works in largely the same way, the steps you take to access these features has changed. This short video will take you step by step through changing file and folder permissions in Vista, with a focus on setting hidden files to show in Explorer.

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.

The Red Cine Application is essential to learn if you plan on shooting with the RED ONE camera. This tutorial goes over output settings, including path, name, size and format.