
Security Summit Search Results


Hack Like a Pro: How to Evade AV Detection with Veil-Evasion
Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

How To: Root Almost Any Galaxy S6 or S6 Edge Without Tripping KNOX
Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

How To: Use Android Device Manager to Find, Wipe, & Lock Your Android Phone or Tablet
If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.
How To: Remove the malicious System Tool and System Tool 2011 from you computer
System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.
How To: Start using your new Samsung Galaxy Tab with these 10 tips
The iPad's got some stiff competition these days, especially from Android, who plans to invade the tablet market with their high-end mobile operating system. And they're off to a good start with the Samsung Galaxy Tab, available from AT&T, T-Mobile, Vodafone and Verizon Wireless, along with other carriers.

How To: Pull five fantastic, funny, and facile pranks
What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

How To: Perform a trick with a nickel, cup, and match
Do you remember "The Heist" from episode 21? Well, the sequel is even more unfair than the original! Check out this video if you want to stump people with a trick called "The Heist II." For this trick, you need only a few simple supplies: a match, a cup, and a nickel.

How To: Build a firewall from a junk PC to protect networks
Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

How To: Set Up a Virtual Card Number for Apple Cash on Your iPhone to Use Where Apple Pay Isn't Accepted
For years, you could only make purchases with your Apple Cash balance on your iPhone using Apple Pay, but a new update gives you the power to set up a virtual card number you can use just like a debit or credit card.

How To: Keep Law Enforcement Out of Your Android Device
With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.
News: New iOS 13.3 Features & Changes You Don't Want to Miss
It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released Dec. 10, has a decent amount of new features too.

How To: 10 Privacy Settings in iOS 13 That Everyone Should Double-Check
Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

How To: The Paranoid Mac Owner's Guide to Defeating Remote Snooping & Evil Maid Attacks
If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.
News: Meet the Nokia 9 PureView — the Pixel 3 XL You Wanted
After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

How To: The Top 80+ Websites Available in the Tor Network
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

How To: It's Not Just Your Camera & Mic — Here's All the Crazy Ways Your Phone Could Be Used to Spy on You
As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Brief Reality: AR Hits the Conference Circuit
Every Tuesday, Next Reality will give readers a rundown of the augmented and mixed reality news briefs from the preceding week that we didn't cover already. This way, you'll never miss anything of importance in the Next Reality landscape, and will always know what's going on with new augmented and mixed reality tech and applications.

How To: The Essential Skills to Becoming a Master Hacker
Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

How To: Use the security features on an HP Compaq 2710p PC
The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

How To: Write an annotated bibliography
An annotated bibliography is very important when writing a scholastic paper or essay. In this tutorial, learn how to create an annotated bibliography, step by step.
How To: Run Windows or Ubuntu on any PC using a flash drive
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

How To: Clean Nintendo NES classic games
No more q-tips! No more alcohol! No more blowing in your cart! Did you know alcohol actually damages the carts? This is a much more effective, safe and long term way to restore the connection.
How To: Setup a VPN on your computer for your Mac Mini server
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How To: Pick a normal lock
This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.

How To: Browse the Internet Safely for 10 Years with This VPN
There are so many things in place that make browsing the internet difficult. From geographical walls to malicious software and spying — there's a lot to consider any time you do the most basic of functions online. VPN.asia: 10-Year Subscription is a VPN that can streamline your security process and make browsing the web so much easier, and right now, it's on sale for just $79.99.

How To: Protect Your Privacy with This 2-Part Security Bundle
Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

News: 2020 iPhone SE vs. iPhone XR — How Apple's Cheapest Smartphones Stack Up Against Each Other
Up until April 2020, the iPhone XR was, for many new users, the first entrance into the world of Apple because it was the cheapest iPhone model since the original iPhone SE. Now, the second-generation iPhone SE has shown up at the same initial starting price as its predecessor, giving budget-friendly buyers another choice.

How To: Add & Use More Accounts on Instagram for Easy Profile Switching
When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device?

News: Here's Why You Should Be Using Private DNS on Your Phone
Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

How To: Securely Sniff Wi-Fi Packets with Sniffglue
Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

News: All the Best Black Friday 2019 Deals on Smartphone Accessories
The holidays are here. From the week of Thanksgiving until the end of the year, retailers will be offering massive discounts on your favorite items. So if you're looking for smartphone accessories, this is the time to buy. From Walmart to Best Buy, there are deals everywhere on a host of items.

Market Reality: HoloLens 2 Secrets Revealed, Nreal CEO on AR Future, Meta Lawsuit Update, & Verizon Teams with Vuzix
As Microsoft continues to bask in the glow of its HoloLens 2 unveiling and begins ramping up the hype to launch, Nreal and Vuzix are carving out their own niches in the AR hardware landscape.

How To: Check & Delete Devices Connected to Your Apple ID to Remove Items You No Longer Use
With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

How To: The Best 'No-Logs' VPN Apps for Safe & Private Mobile Browsing
There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

How To: Use All 10 Fingerprints for Touch ID on Your iPhone — Not Just 5 of Them
While Apple has moved on from Touch ID to Face ID in newer iPhone models, there are still plenty of iPhones with fingerprint sensors — in fact, Apple's second-generation iPhone SE is the first new Touch ID iPhone in three years. With Touch ID, you can register up to five fingerprints, but it doesn't stop there. Using a little-known trick, you can sneak another five fingerprints in there for a total of ten.
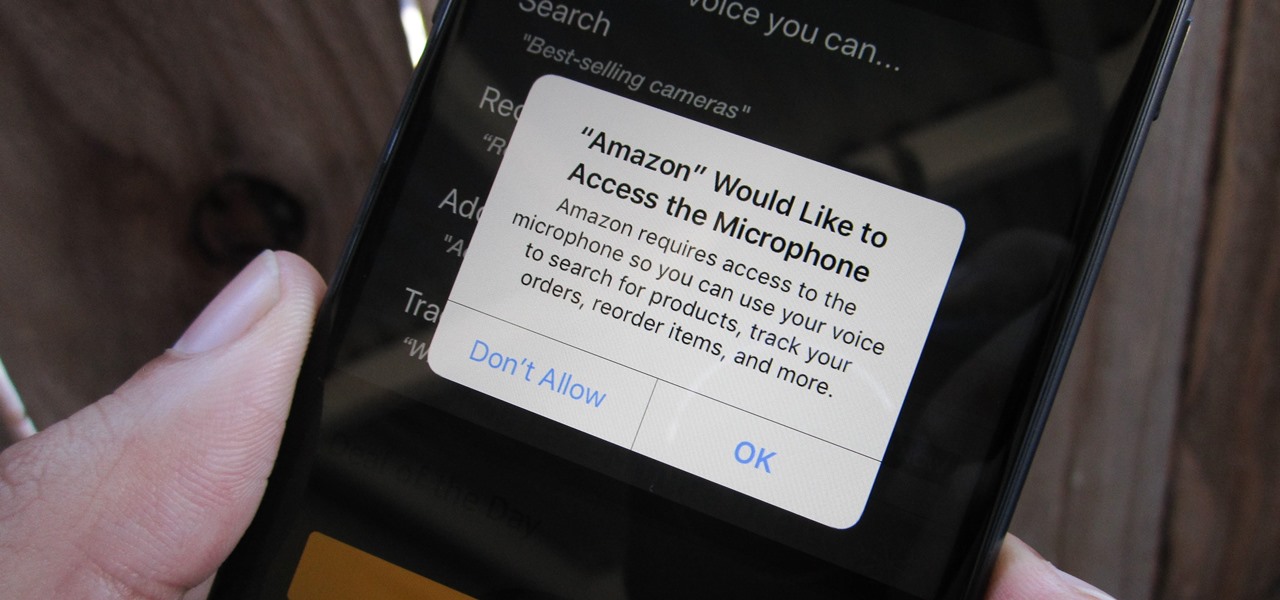
How To: Prevent & Stop Apps from Using Your iPhone's Microphone & Enhance Your Privacy
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

How To: Get Android's Smart Lock Feature on Your iPhone
As great as passcode and biometric security features like Face ID are for preventing unwanted access, they aren't needed 100% of the time. When you're at home with a locked door between you and anyone you wouldn't trust with your phone, they really only serve to slow you down. Android has long had a solution for this, but a new Cydia tweak has now brought a similar solution to iPhones.

News: 4 New iOS 12.1.1 Features for iPhone You Don't Want to Miss
The last update to iOS 12 featured more emoji, Group FaceTime, eSIM functionality, real-time depth control for new iPhones, and a few other interesting tidbits and fixes. Now, in the latest for iPhones, iOS 12.1.1, Apple brought back a few things that were removed or made more difficult to access in previous updates, and it even has a few new features to offer, albeit small ones.

How To: Use Commix to Automate Exploiting Command Injection Flaws in Web Applications
The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

