Taking a cue form Snapchat, WhatsApp Status lets you share updates that come in the form of GIFs, photos, videos and good old text. This awesome feature is available for both iPhone and Android users, and it even lets you choose which contacts to share with while disappearing after 24 hours.

A pair of organizations recognized companies working in augmented reality for their innovative technologies over the past week. Meanwhile, another company used augmented reality for a sector that is overdue for a technology makeover, while another company has developed new camera modules that could usher in the next evolution of mobile AR.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.
Once upon a time, Flash games reigned as some of the best entertainment the internet had to offer. But then came the smartphone, which quickly overtook this genre with similar games that you could play no matter where you were. If you yearn for the good old days, though, you'll be happy to know that you can still use the Puffin browser to safely play old favorites and discover new gems.

It's always nice getting paid to do something you love. That's why Nintendo is offering all Nintendo Switch owners a chance to find vulnerabilities before another hacker beats them to it first. Depending on the vulnerability you find, Nintendo is willing to shell out rewards starting at $100, all the way to $20,000, to the first bug reporter who uncovers it.

Pinterest, a worldwide catalog of ideas shared by over 175 million users every month, is dominated by Android users, who are now the app's fastest growing group. Pinterest has since taken notice, and has started to incorporate handy home screen shortcuts for users with Android 7.1 or higher.

At Adobe Summit 2017 this week, Adobe announced they are looking to occupy a new space in the market by combining their analytic capabilities with augmented reality. Teaming up with Microsoft, the company has combined Adobe Sensei software with the HoloLens, reports GeekWire. Together, the tech and software create a new tool for retailers to track their consumers' habits.

If you were a particularly good little girl or boy this year, Santa might have finally brought you that cool new smartphone you've been wanting. Or perhaps you just took advantage of a great sale and treated yourself to a new gadget this holiday season—totally justifiable, and surely a well-deserved gift.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

The Google Chrome browser for Android is packed with many great features, but it definitely has a bad rep for being slow and laggy on low-end or midrange devices. Without a top-notch processor, you'll likely notice some stutter with choppy scrolling, and pages can take too long to load in general.

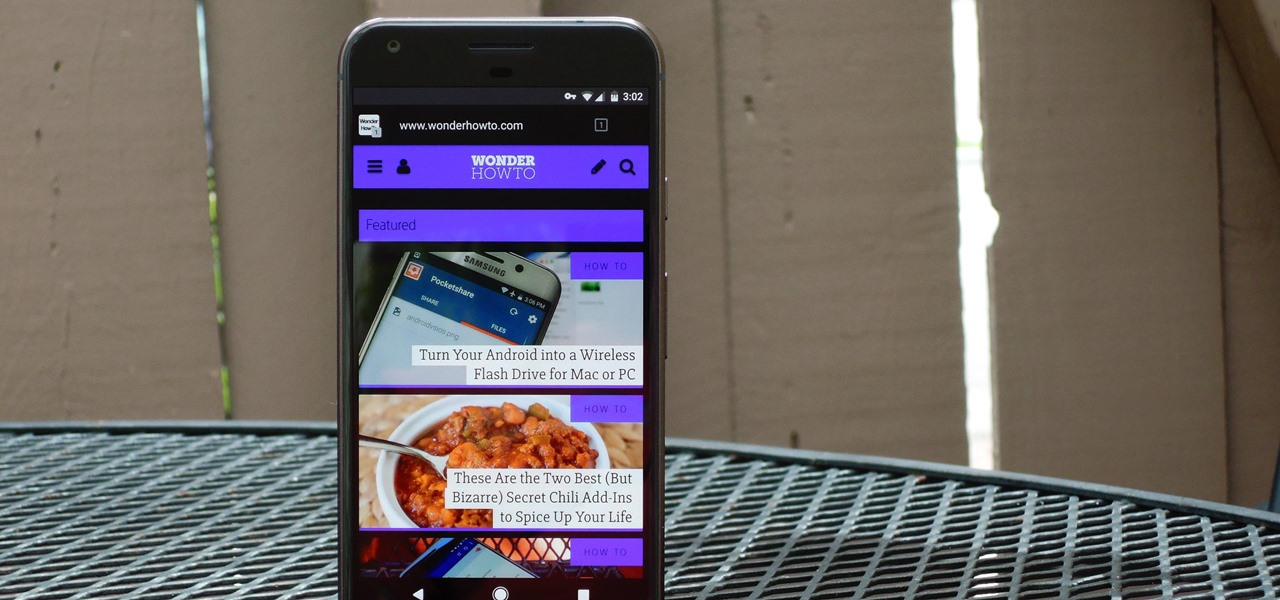
Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.

You can use the F1 key to notably dim your Mac's display, but sometimes that just isn't dark enough. If you're working in pitch black conditions, have a migraine or tired eyes, or just want a more comfortable environment, you might want your screen even darker—without making it pitch black.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

To serve as a framework for the "Nexus Imprint" feature in their new Nexus 5X and Nexus 6P smartphones, Google added native fingerprint scanner support to Android 6.0. Sure, Android devices have had fingerprint scanners in the past, but this is a unified, system-wide implementation that all devices can use—meaning that in the near future, we may finally start to see apps that let you log in to your account with your fingerprint instead of a password.

When you have some form of lock screen security enabled, Android makes sure that you don't have to fumble around to enter your pattern, PIN, or password before you can call 911 in an emergency. It does this by adding an "Emergency Call" button to the bottom of the screen—but as handy as this may sound, most of the time it's more trouble than it's worth.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

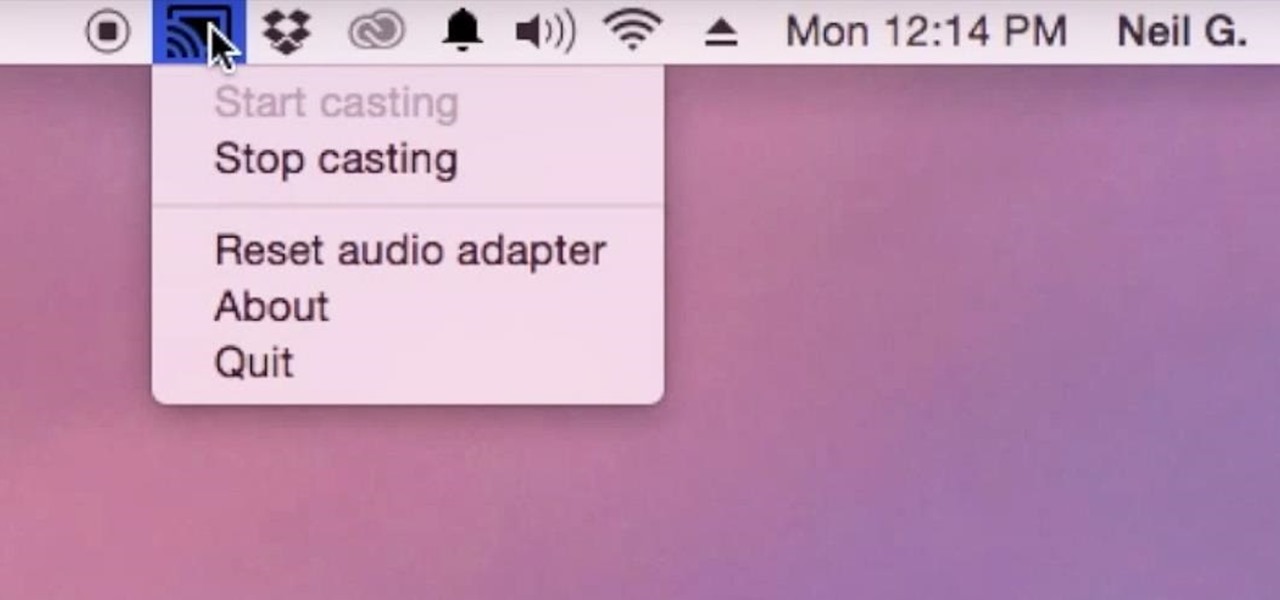
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

Keyboard shortcuts can make using your Mac faster and easier, and leave your mouse feeling archaic. With just a few taps, you can save files, open new tabs, or play a movie—all without using your mouse even once.

Samsung has a long-standing reputation for packing their devices with lots of added functionality, and the Galaxy S6 Edge is no exception. It comes with a nifty feature called "Information stream," which allows you to get quick, at-a-glance information by swiping the edge of your screen back and forth while the display is off.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

On mobile devices, the Notification Center received a huge facelift when iOS 8 was released, but it wasn't until Yosemite that its Mac OS X counterpart received the same amount of love—especially the much needed ability to add custom widgets, like a FaceTime dialer.

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

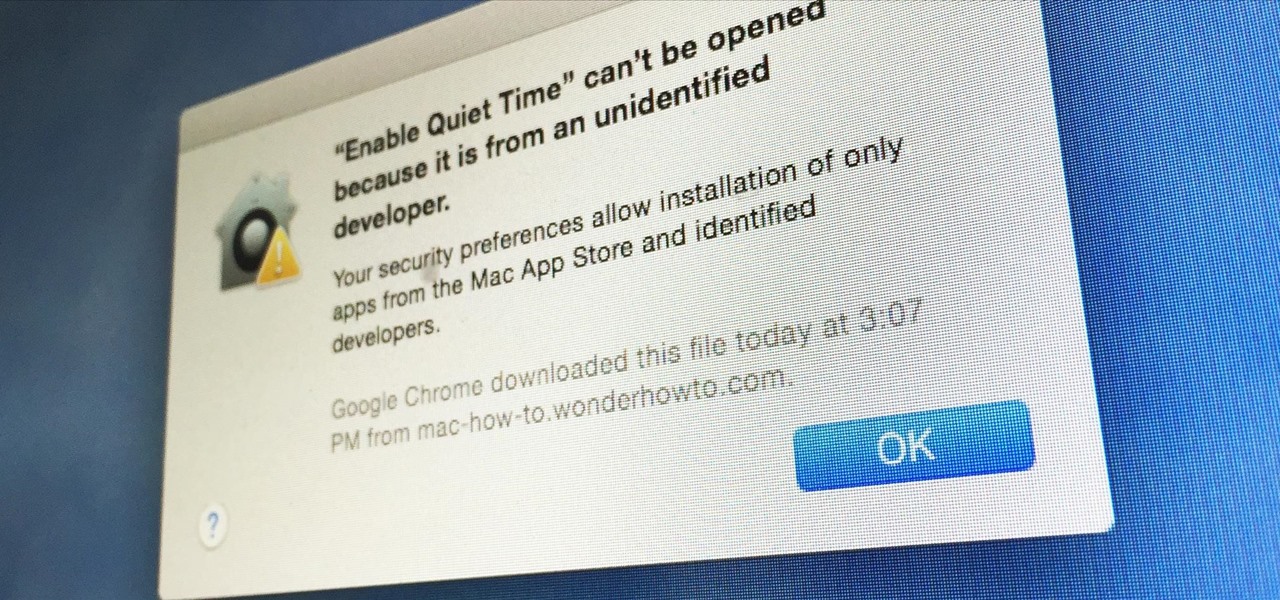
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it.

We live in a time where privacy is rare and our files can be easily accessed by just about anyone. Having your phone protected by a passcode is great, but if someone figures it out, they can easily access anything on your phone.

Most times when you take your smartphone out of your bag, pocket, or purse, you probably know exactly what you're going to do with it. Make a call, send a text, take a selfie, browse viral videos on YouTube, or one of the other many things a smartphone can do nowadays.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

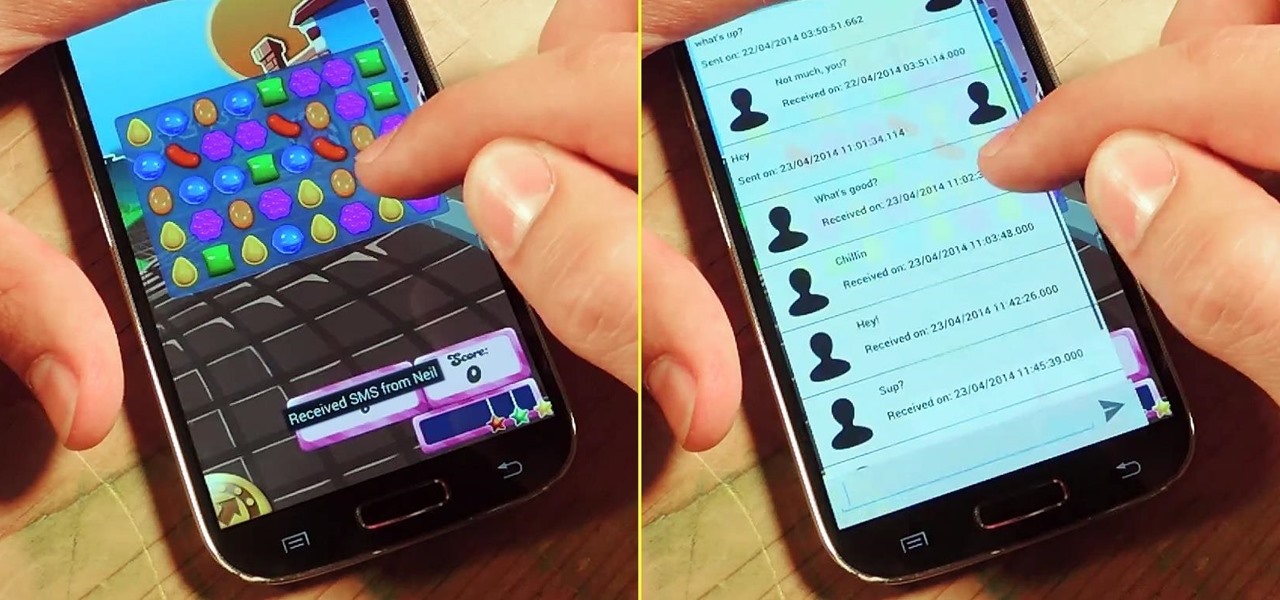
I'm a textaholic, as I've said many times before, but even textaholics forget to respond sometimes. When I'm watching a YouTube clip or devouring delicious snacks in Candy Crush Saga, I'll often ignore incoming texts and forget to respond later.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

As respectful as you may be, it's hard to resist looking through someone's iPhone when given the chance. You're not trying to snoop around, but it's just too easy to open up apps and read embarrassing emails or find scandalous Instagram follows. It's like looking through a digital diary riddled with deep, dark secrets.

Sometimes it's the little things that make our days better, like finding a dollar in our recently washed jeans or a box of donuts in the lunch room. But your Nexus 7 tablet's lock screen isn't typically one of those things—it's just a lock screen after all.