There's a lot of fighting to endure in the Xbox 360 game Bayonetta. In Chapter 1 - The Angel's Metropolis, it's your first real battle. Central Station Platform - Go to the far side of the platform and go through the security gates. The door on the far side of this hall is locked, but on one wall in the hallway you'll see a strange sphere. Walk up to it and start doing combos to open a door.

Knit blankets are comfortable and scream home and security, but they are expensive and making them is an arduous task. If you want to get started on a major knitting project, watch this video, and learn in general terms how to knit a blanket.
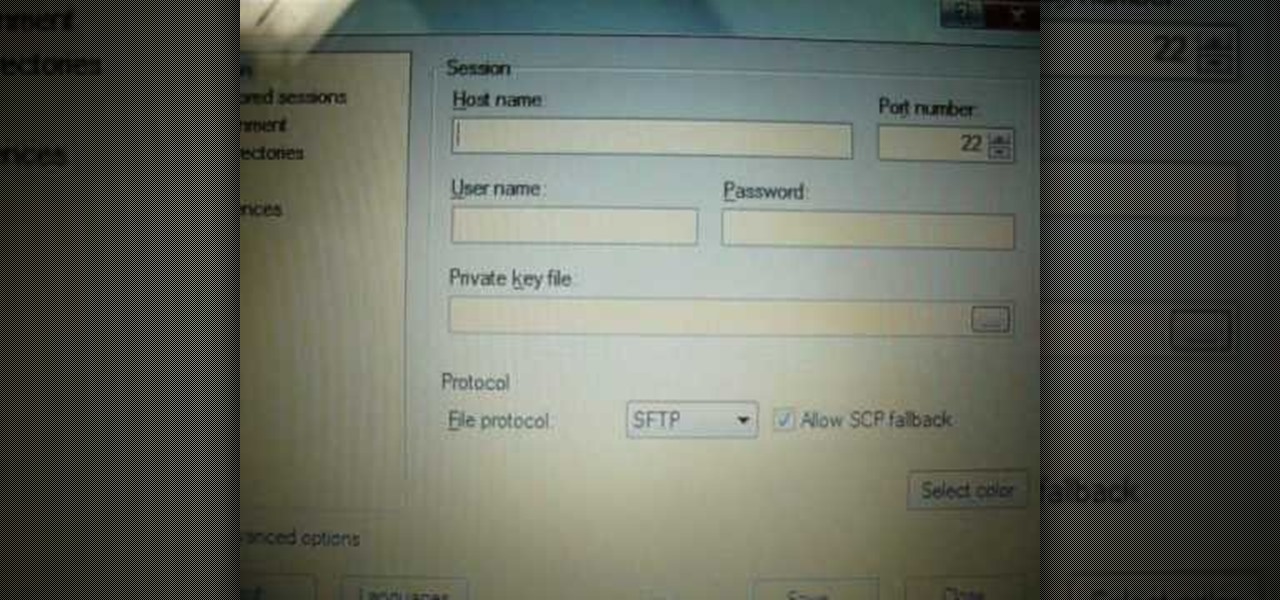
Take a look at this video and learn how to hack into a wireless Linksys router. This hack isn't applicable for all security enabled networks, only ones that use generic passwords.

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

The Thule Snug Tite hitch lock is for carrier to receiver security. This video shows you how it assembles first, then how the lock is applied to a bicycle rack.

This video demonstrates how to install or replace a dead bolt in your door. Having a dead bolt lock gives you a added sense of security, because it is more secure than just the lock on the door handle.

iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

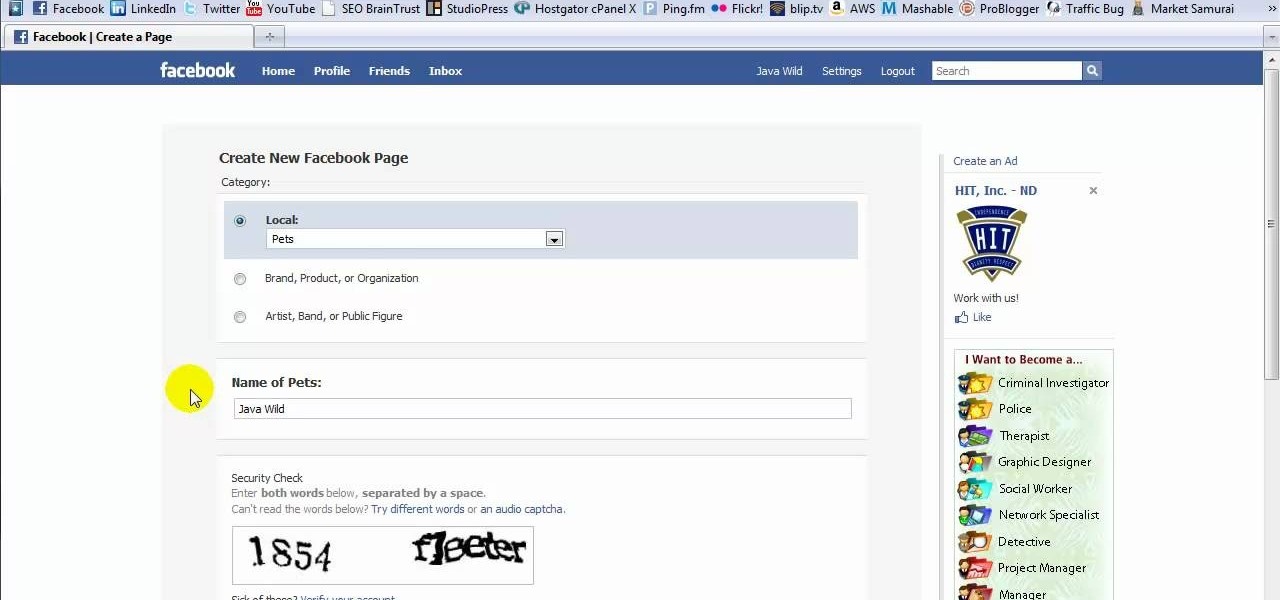
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

This video is a step by step guide for creating exposed teeth makeup . This is loosely based on the Harvey Dent character from Batman: the Dark Knight.

Reduce your chances of becoming the seatmate everyone hates by learning how to head off a screaming jag.

Research shows that color can have a powerful effect on our emotions. Start harnessing that power today. Watch this video to learn how to improve your life with chromotherapy.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

Investment in augmented reality remained robust in 2019. For the third consecutive year, we looked back on the biggest funding deals in the AR industry this week, and a familiar name came out on top.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

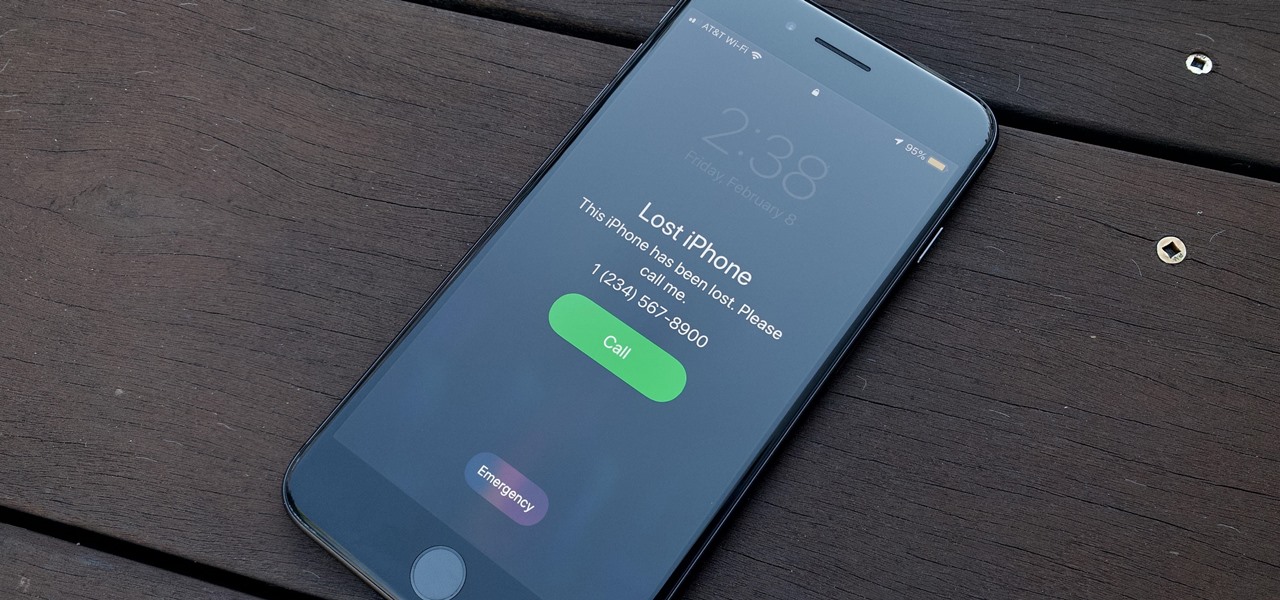
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

The Pixel 3 XL versus Galaxy Note 9. Stock Android versus Samsung Experience. When I began this comparison, I thought the Pixel 3 XL would be unfairly outmatched. But after looking at the specs side-by-side, you'll see a different picture. This year, Google delivered a worthy alternative to Samsung's best offering.

Apple may pride itself on its commitment to user privacy and security, but it isn't invulnerable. We now know there is a bug in the latest version of iOS 12 and iOS 12.1 beta that allows those in the know to bypass your passcode and access contacts and photos. This applies to both Face ID and Touch ID-enabled iPhones. Not only do we know about the bug itself, we know exactly how to exploit it.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.