Smartglasses from Apple have become the holy grail of augmented reality, and 2020 has been the rumored time horizon for the product's arrival for the past two years. The latest analyst report sheds more light on its potential debut next year.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.
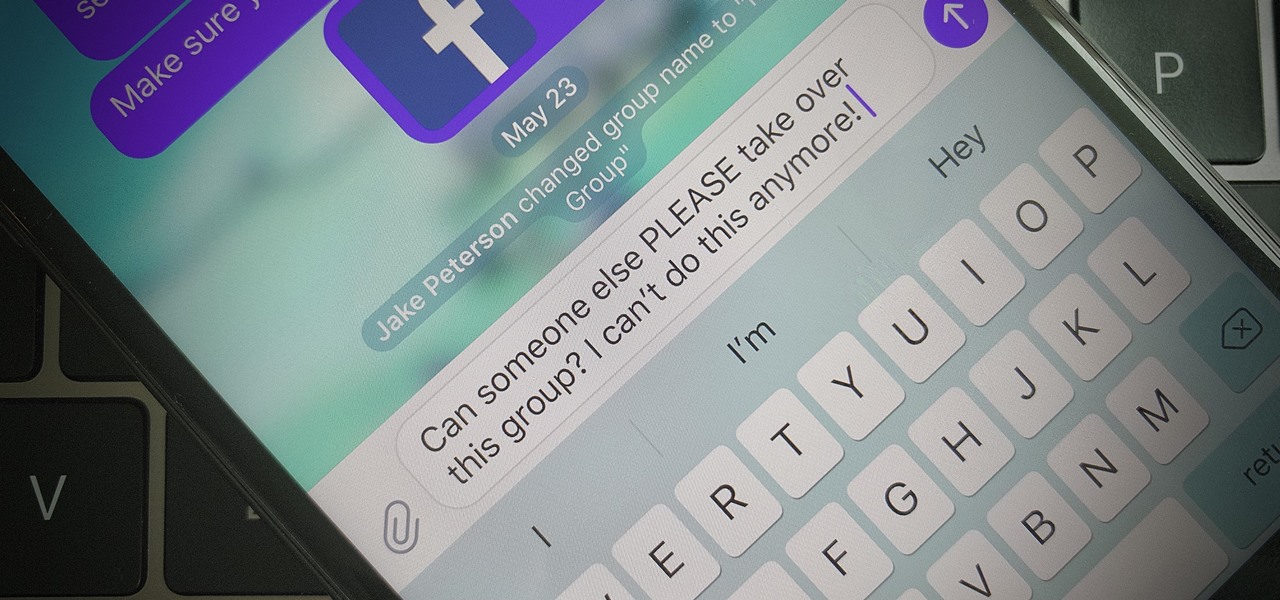
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?
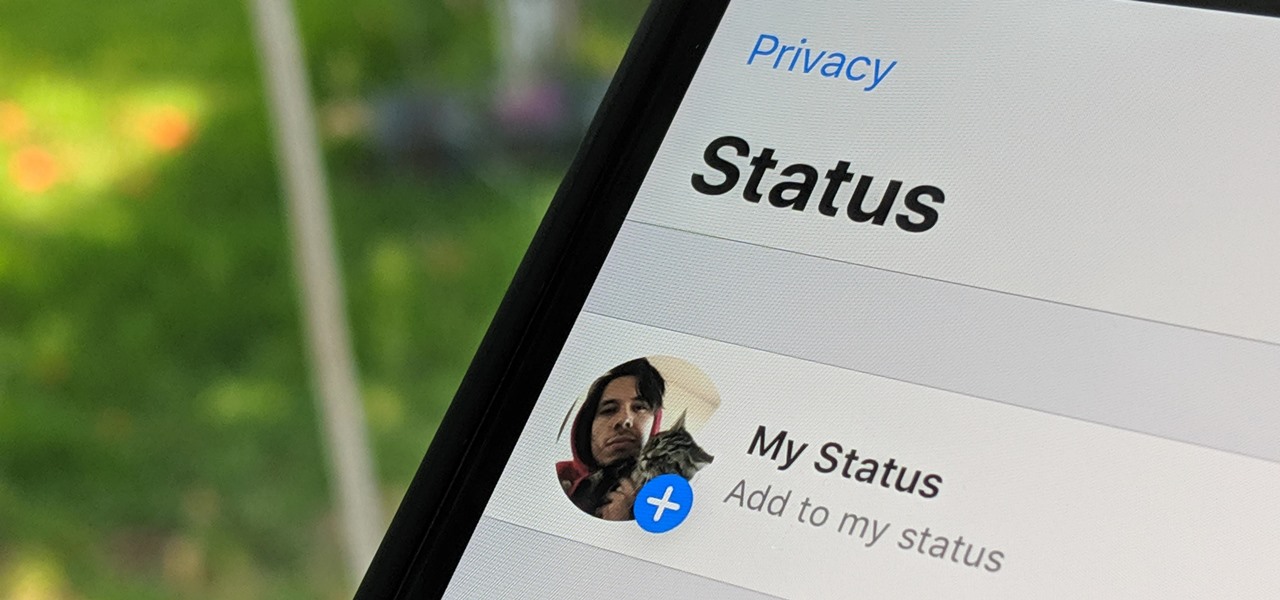
WhatsApp, the popular messaging app owned by Facebook, has several important privacy and security-related features, including end-to-end encryption, screen lock, read receipts, and two-step verification. If you're an avid WhatsApp user, you'll be happy to know there are more privacy features you might not know, such as hiding your profile photo from other users.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

The Moto G7 Power is a phone that screams battery life. From its display resolution to the massive battery, it was designed for those who hate to recharge each night. But unlike other battery-focused smartphones, it comes at a price almost anyone can afford.

Seven days ago, Apple released the first public beta for iOS 12.2. Now, public testers have access to the latest beta update since Apple released 12.2 public beta 2 on Tuesday, Feb. 5. The company released the developer beta one day earlier, which includes bug fixes, new Animoji, and more.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

With new iPhone models out, you'll have updated cameras to try out, a faster processor, and new colors to choose from. The only thing that could stop you from picking one up yourself is, well, your current iPhone. Here's how to check if you're eligible to upgrade to iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max, or any other iPhone still being sold.

If you've been getting that "Please update from the iOS 12 beta" alert continuously in iOS 12 public beta 9, Apple just issued a fix for it Friday, Aug. 31, with iOS 12 public beta 10 — just in time for Labor Day weekend. This marks the second update this week as dev beta 11 and public beta 9 were released on Monday. It's also just one day after Apple announced its Sept. 12 event.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

Using a passcode on your Apple Watch is a good way to keep other people out of your data, but what happens when you see that "Wrong Passcode" screen yourself? You can, of course, try again in a minute, but if you've forgotten it for good, there's still a way to get back into your Apple Watch.

Confirming a previous report from last week, Qualcomm announced its Snapdragon X1 platform designed for augmented and virtual reality devices during an event at the Augmented World Expo in Santa Clara on Tuesday, with Meta and Vuzix among the first manufacturers to adopt it.

Android has gotten significantly better at handling intrusive ads over the years. Things have gotten to the point to where these nuisances are largely a non-issue for most of us. However, there are still a few ad-laden apps that fall through the cracks — particularly the kind that bombard your lock screen with ads.

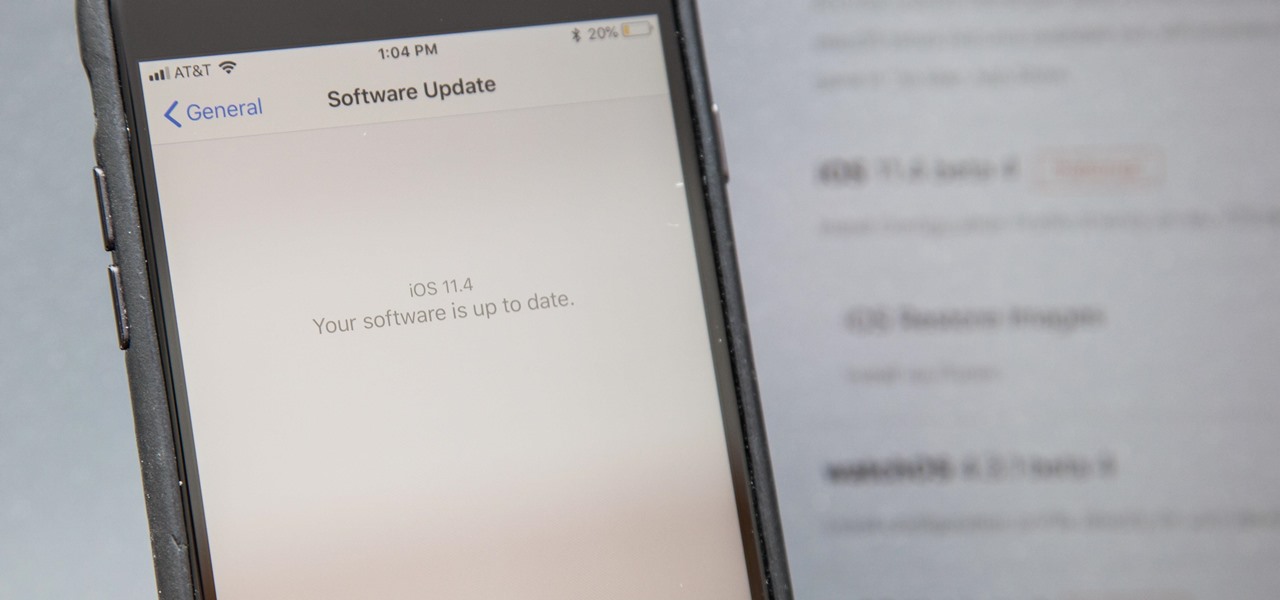
Apple is speeding things up in the iOS 11.4 development. The company released to developers the fifth beta for iOS 11.4 on Monday, May 15. Public beta testers got the update just hours later. The update comes just one week after the release of the fourth 11.4 beta, which introduced minor bug fixes and security patches to iPhone running the software. This beta version doesn't seem any different.

Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

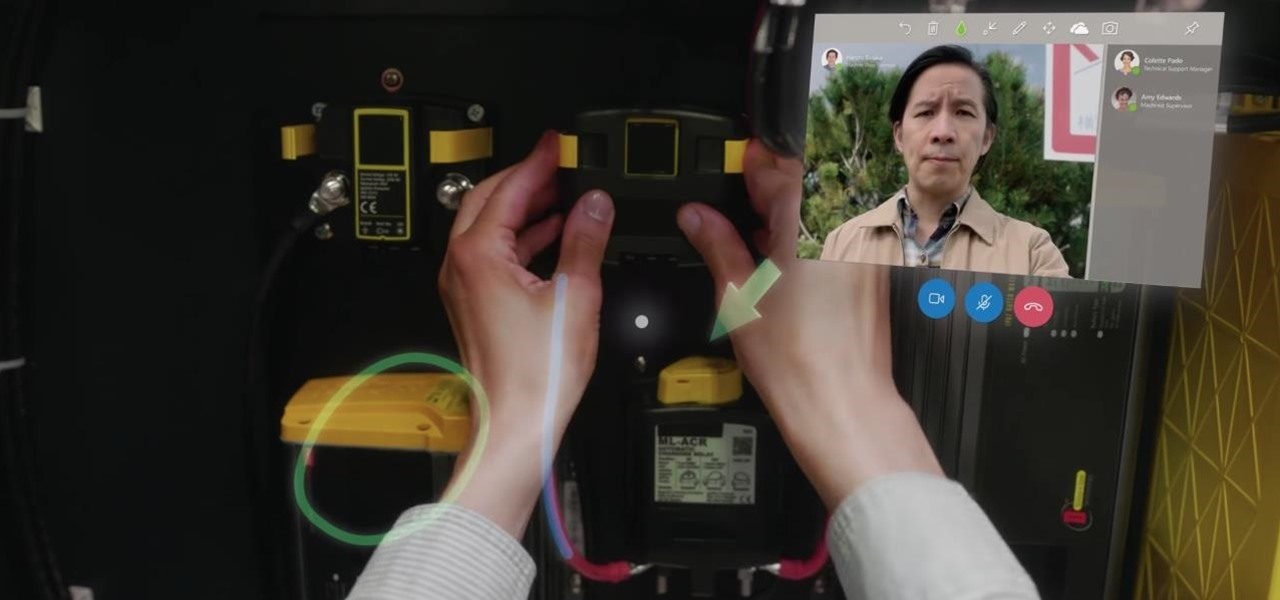
On Monday, at its annual Build developer conference, Microsoft revealed two new apps for the HoloLens apps.

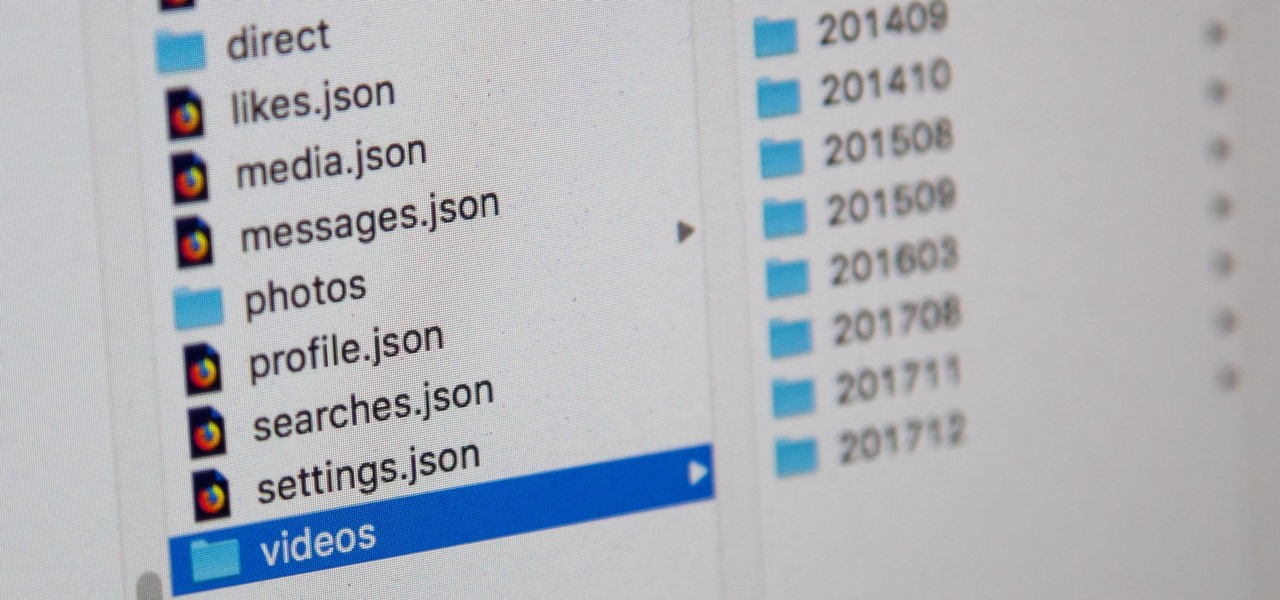
Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just in Europe.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

In the Android community, Samsung's slow updates have long been the accepted norm. With the Note 8's recent Android Oreo update, Samsung completed annual version updates to their 2017 flagship lineup. Now is a great time to look back on how Samsung has fared with updates over the past few years. Hint: It's not pretty.

It turns out that the government of Saudi Arabia has managed to do something last month's Game Developers Conference couldn't — give us a few new glimpses of the Magic Leap One being worn by someone other than Shaq.

Google just released Android 9.0 Pie, but the Android community is already working its magic. Developer Quinny899 quickly ported the updated Pixel Launcher from the new build, so you can try it out on other phones right now.

WhatsApp comes with a ton of great features that make it the go-to messaging app for millions of people around the world. Among these is the ingeniously simple Read Receipts that let you know your message has been viewed. If you want to read a message without alerting the sender, however, there are simple tricks you can perform to give yourself plausible deniability.

Last week, the first possible image of the upcoming OnePlus 6 leaked. It was met with mixed reactions, most notably for its apparent iPhone X-style "notch." OnePlus fans seem concerned that the company is implementing a design choice based on what it thinks is trending, not necessarily what's best for the product. If you're one of those uneasy about OnePlus' future, don't be. At least not yet.

While it may not be an obvious feature, Apple actually built a way into iOS that lets you hide specific pictures and videos in the Photos app that you want to keep on the down-low, for your eyes only. If you show off your photos a lot or stream slideshows to your TV, this is a great way to keep less appealing content private.

If you have an iPhone, you probably know that iOS 11 hasn't been the smoothest iOS version released, to put it lightly. We've seen bug after bug cripple the software's usability, many times within the Messages app. Now, yet another glitch has emerged to drive us crazy, one where just a simple Indian character can crash Messages as well as other third-party apps.