
News: Signal - the Encryption App That Keeps NSA & Governments Away!
Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?


Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.
It's a breeze to send videos and music from your phone straight to your TV with an Apple TV or Chromecast, but these devices don't support all file types. While MP4 videos and MP3 music files are the norm these days, I still have a ton of AVI and FLV files that I'd like to watch on a big screen.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something like that) and pentesting, but never made a full return. I will be occasionally coming back for a while.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.
OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Let's say you got a little careless while installing apps from unknown sources, and now your Android device has been infected by malware. Or perhaps your friend has come to you for help after they had haphazardly installed random apps until their phone was filled with popups and garbage like that.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

It seems like whenever someone sees my phone, they ask me two questions right off the bat; "What phone is that?" and "How did you get your Android to look like that?"
Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Locking your keys inside of your car is frustrating, to say the least, especially if you're in a hurry to get somewhere. You can always call AAA roadside assistance or a locksmith, but you'll probably have to fork over some money, as well as wait for them to get to you. You might even get towed.
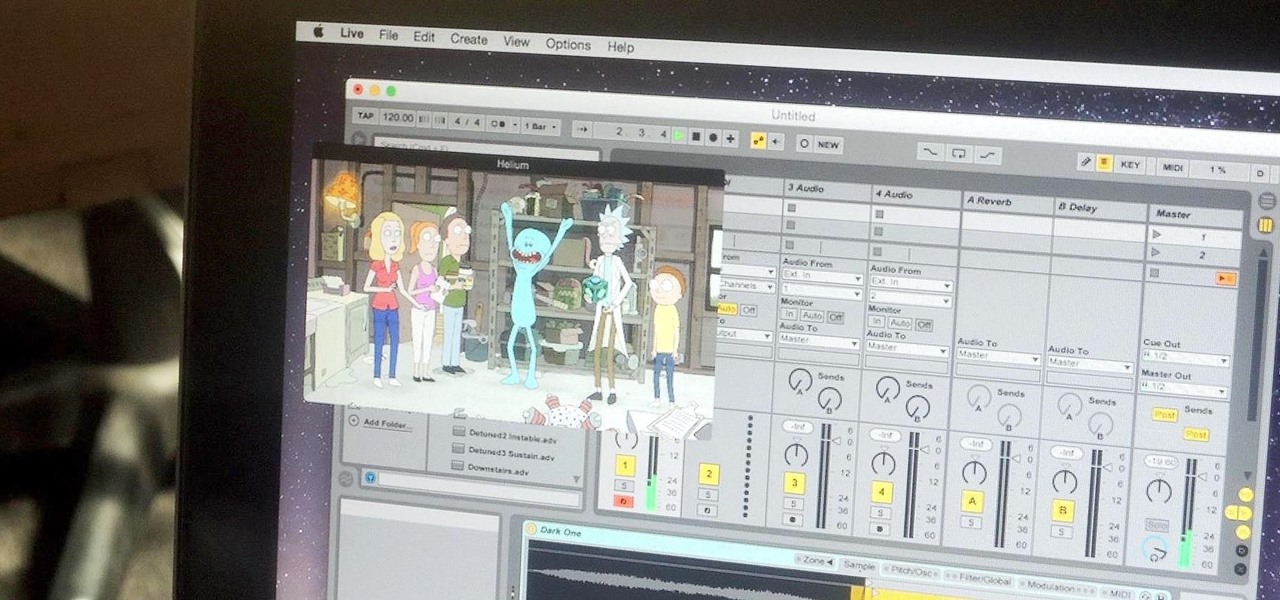
Like most people who spend a good deal of time in front of their computer—whether for work, school, or play—I jump back and forth from window to window, working and playing with different things at the same time to get my work done faster or procrastinate harder.

All of those keys on your keyboard can do much more than just help to update your Facebook status or fire off a scathing tweet. By learning all of the keyboard shortcuts for apps on your Mac, you can cut back on mouse or trackpad usage to perform actions faster and more efficiently.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Managing files can be time consuming on your Mac, for the simple reason that keyboard shortcuts and right-clicks sometimes lack the effectiveness we need. But with a simple third-part app, you can expedite the process of sharing, moving, deleting, and overall managing files on your computer.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Exclusive to the Samsung Galaxy S6 Edge, "Information stream" is a screen feature that lets you see quick, at-a-glance information with a simple swipe while the screen is off. It also supports plug-ins, or additional streams of information that can come from third-party sources. So developers are starting to come up with nifty little add-ons for Information stream, and the team at 3C has some cool new system feeds that might come in handy.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The Apple Watch is finally here! We'll have loads of guides and videos for you guys to check out in the following week and beyond, but we thought it'd be best to start off showing you how to set up and pair that brand new beautiful Apple Watch of yours to your iPhone.
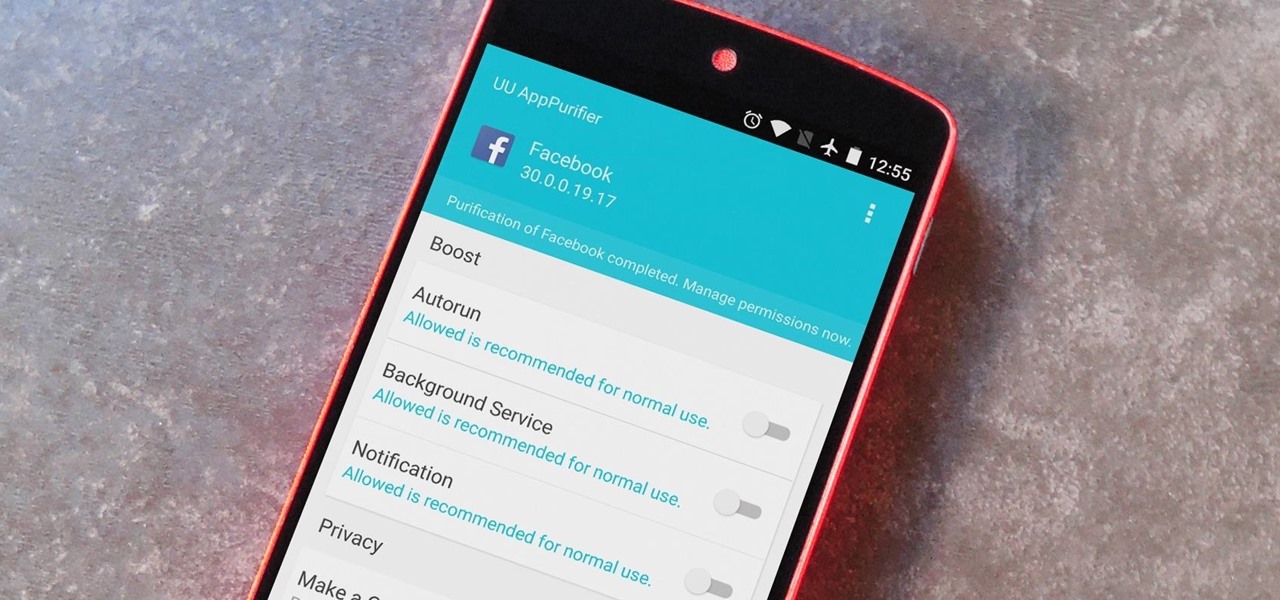
When it comes to app permissions, Android takes an "all or nothing" approach. You have no granular control over what data apps can access, so the only way to prevent an app from seeing your location or starting up on boot, for instance, is to not install the app in the first place.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

The Galaxy S6 won't hit shelves until later this spring, but that didn't stop the Android community from working its magic and pulling a handful of apps from the device's stock firmware. Several of these apps rely on framework elements that aren't present on current-generation Samsung Galaxy devices, but the new version of the Smart Remote app can be installed without much difficulty.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.
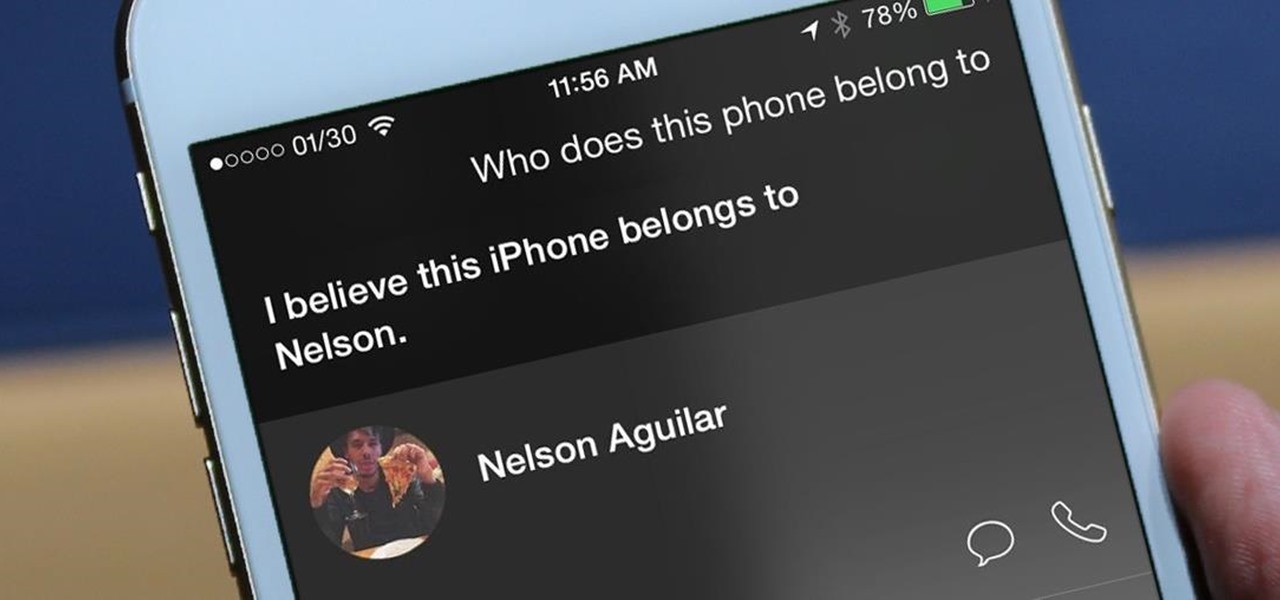
I misplaced my iPhone 6 just a few weeks ago, so I know firsthand that losing an iPhone sucks. Luckily, my tale didn't have a bad ending.

The camera in CyanogenMod, CameraNext, takes some pretty impressive shots when compared to those offered by HTC Sense and Sony Xperia, but it doesn't have many of the features that make it a real competitor. Even the Color OS version of the OnePlus One has received better reviews when comparing low-light shots, which implies that it's not the camera sensor that's lacking, but the software.