Apple officially unveiled iOS 14 on June 22 at its first all-virtual WWDC. After months of beta testing, iOS 14 hit iPhones on Sept. 16, but that doesn't mean that Apple is done beta testing iOS 14. There will be new features to try out right up until iOS 15 comes out next year.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra help. That's where these video recording apps come into play, to ensure the footage you capture is as good as can be.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

With smartphone cameras and software getting better and better every year, more and more users are getting passionate about photography. So when you're shopping for a gift to get someone, if they have a smartphone, chances are they'll more than appreciate some tools and accessories for taking better photos with their pocket friend — and we've got some gear ideas they'll love.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

In this tutorial, learn about applying and removing security options in Acrobat 9. For more Adobe software tutorials from Layers Magazine, search Layers Magazine on WonderHowTo. WonderHowTo indexes all Layers Magazine tutorials for Illustrator, InDesign, Photoshop, Acrobat, After Effects, Premiere Pro, Dreamweaver and Flash.

This hour-long hacking tutorial looks at the Nmap security scanner. In particular, this Nmap tutorial looks at port scanning concepts, TCP three way handshake, stealth scans, idle scans, bounce scans, version detection, OS detection, NSE/LUA scripting and firewall logs. To get started using Nmap, watch this video tutorial. Use the Nmap security tool.

The Ironkey is a high security thumb drive designed to provide strong AES encryption, tamper resistance and other security services. Some of the topics covered will include: How is the drive mounted without admin privileges in Windows? How is it mounted in Linux? How does the "Self Destruct" feature work? What is Secure Sessions? How is the Ironkey better than just using Truecrypt? For answers to these questions, take a look. Use the Ironkey High Security Flash Drive.

You've all probably heard about Apple's attempts to thwart iPhone 4 users from opening up their own devices, thanks to their sly maneuvers in switching out everyone's screws with those funky pentalobular screws. But one thing Apple will never learn— they will never have complete control. Where there's a will, there's a way. And if someone wants to fix their own iPhone or modify it slightly, they're going to do it, regardless of what screws bind it together.
he Senate Appropriations Committee on Tuesday moved forward with legislation to increase airline passenger security fees, beating back a GOP attempt to keep them at current levels.

Waiting in line at the airport can be a drag, but here are a few tips for catching your flight hassle-free. See how to get through airport security in a snap from this how-to video. Airport Security Tips - Fly Through Airport Security Video.
Ok, now lets introduce myself i am also a newbie but conducted many pentests.This is the tutorial for customizing kali linux

Hi everyone. I'm relatively new here and I have learned a great deal from many of you already and would like to try and give a little something in return.
Multiple airport screeners have been arrested for allegedly taking handsome bribes to look the other way while loads of illegal drugs slipped through security at Los Angeles International Airport, federal officials announced today.

Check out the winner from Beyond the Still's Chapter Two: Job Security. "Job Security" written & directed by Josh Thacker.

In this video tutorial, viewers learn how to set and encrypt the wireless password using WEP Apple Airport. Begin by opening the Apple Airport utility program. Then find the network's name and double-click on it. The Configure "Apple Airport Express" opens, click on the Airport tab. Then click on the Wireless Security button. Now click on the Wireless Security drop-down menu and select 128-bit. Click on the Set WEP Password button, type in the password and verify it. Finish by clicking on Upd...

In this video tutorial, viewers learn how to set and encrypt your Wi-Fi password using WPA on a Linskys router. Begin by opening your web browser and type in the address: Click Enter. Now type in your user name and password, and click OK. Then click on the Wireless tab and select Wireless Security. In the Security Mode drop-down menu, select WPA Pre-Shared Key and then type in a password under WPA Shared Key. Finish by clicking on Save Changes. This video will benefit th...

Installing a deadbolt is a relatively quick and simple do-it-yourself project. You can make your home much safer – and less attractive to thieves --- with a little effort and a few simple tools.

How many of you have or know people who have a smartphone? There's a lot of you, right? Well, depending on how most of you use those smartphones, there could be all kind of sensitive information stored on it, and that doesn't just mean sensitive personal information, but it could also contain all sorts of sensitive corporate data for work.

Hi fellows! I finally decided to join this forum, which I find very interesting and has some great contributions into the tech and security space, appreciate it!

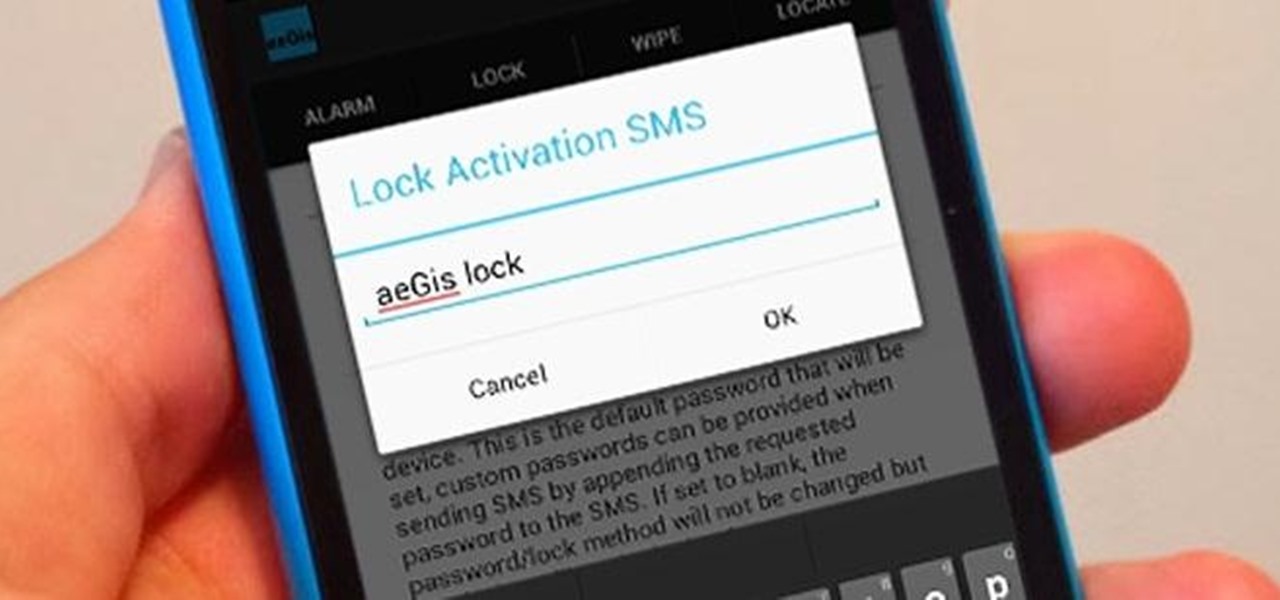
The great thing about security apps (other than the obvious) is that there is an abundance of them littered throughout the Google Play store. Cerberus, Got Ya!, Avast! Mobile Security, Norton Security & Antivirus, and Android Lost Free are just a few of the gems you can find in the plentiful sea of security apps for Android. Once in awhile, though, a new security application comes along that stands out from the rest, like AeGis.
In late 2011, representative from China, Russia, Tajikistan and Uzbekistan submitted a proposal called the International Code of Conduct for Information Security (ICCIS) to the UN Secretary General Ban Ki-moon that called for international consensus of a global set of rules and regulations that standardize information flow on the internet.
The department of Homeland Security released a list of 'words and phrases' it uses to search social media for terrorism, and whatever else they decide they are looking for that day. Read some of these. A few are obvious "bomb, nuke" and some "target, event" are just down right vague. More reasons to watch what you do on the Internet. You are not the only one watching!

UK-based artist Matthew Nicholson is a man of many talents: designer, photographer, professional free runner and papercraft engineer—and in the latter of which, he generously posts free downloadable DIY kits for your folding pleasure.

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

The end of Daylight Saving Time means two things: a little less light and, as a result, a little less security. This CCTV lamp will give you more of both. And in the nick of time! We fall back to Standard Time at 2 AM on Sunday, November 7th. Better get building!

Four key Syrian military officials including Defense Minister Gen. Daoud Rajha and President Bashar al-Assad’s brother-in-law Assef Shawkat, who served as his deputy, were killed at a top-level meeting in central Damascus. Syria's top security ministers slain in Damascus bombing — RT.

Check out this computer software tutorial from Dummies.com. This tutorial is made for PCs. Increasing a PC's Windows Vista security is easily done by turning on the Windows firewall and Windows Defender. There's no need to download the firewall or Defender. Protection against spyware and other security risks increases upon enabling these free, built-in Windows solutions. Enable the Windows firewall and Windows Defender.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task.

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?

In this video tutorial, viewers learn how to password protect their files. This task can only be done on a Windows computer. Begin by creating a Microsoft Word document. Simply right-click on the desktop, go to New and select Microsoft Word Document. Then double-click on the document and create your text document. Now to save it, click on File and select Save As. Name the file. Now click on the Tools drop-down menu and select Security Options. Then type in a password, reconfirm the password a...

In this Computers & Programming video tutorial you will learn how to encrypt a D-Link router with WEP password protection. First you connect to your wireless network. Open your browser and type in http://192.168.0.1. Type in your base station username and password and press OK. Under the SETUP tab, select WIRELESS SETTINGS, scroll down to 'Wireless Security Mode' and select 'Enable WEP Wireless Security'. Scroll down to WEP. Under WEP Encryption pull down menu select 128Bit. Now create a pass...

In this video tutorial, viewers learn how to set and encrypt a NET-Gear router with WEP password protection. Begin by opening your web browser and go to the router website: Router Login.. When the Prompt window appears, type in your router user name and password, and click OK. In the sidebar, under Setup, click on Wireless Settings. Once again, type in your user name and password, and click OK. In the Security Options, check WEP (Wired Equivalent Privacy). Then select the Pass-phrase box, typ...
Moscow, May 21 — Some Western countries are still considering a military operation against Iran as an option over its nuclear programme, a Russian minister said Sunday.

Have an HTC smartphone? Chances are that some of your stored personal data has been hijacked by malicious apps on your device. Android apps that have permission to access the Internet, which is pretty much every ad-supported app out there, can snag valuable information such as email addresses, location history, phone logs, text messages, and more.

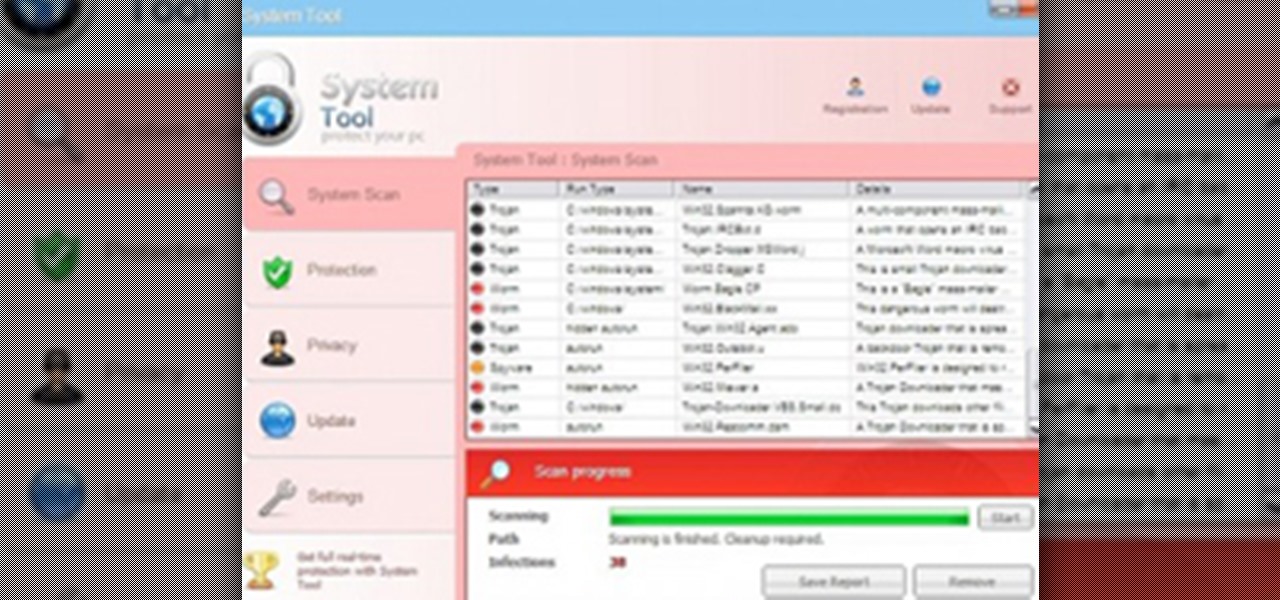
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.