When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

Here's a trophy guide for Payday: The Heist that requires excellent teamwork. To get the 'No Photos' trophy, you'll need to take out all of the security cameras in the level First World Bank within ten seconds of drawing your weapon.

About two months ago, the massive Gawker Media hack was a wake up call for many web denizens on the importance of proper password security. Data analyzed by the Wall Street Journal revealed the three most popular passwords recovered from the hack were downright idiotic—123456, password, and 12345678. If past events weren't motivation enough for crafting a strong password, then maybe a racy 8-bit stripper is. Naked Password is a jQuery plugin by Platform45 that rewards you with an accelerating...

When choosing a security system for the office, Billy Chasen decided to ditch the traditional lock & key barricade for something a little more 21st century. He hacked together a device that uses a web server, servo motor and some parts from Home Depot to enable locking & unlocking via text message. Chasen maintains a list which gives access to green lit office workers, who enter by simply texting "lock" or "unlock"... and voilà, open sesame.

The German police have their panties in a bunch over a highly inflammatory sculpture of a urinating policewoman by artist Marcel Walldorf. Entitled "Petra", the hyperrealistic figure depicts a female officer crouched, peeing with buttocks exposed. The most chilling detail is her riot baton casually propped on the wall next to her.

Note: Little Brother is available as a free ebook download. Warnings

Up for auction at Heritage, JFK's crusty old birthday cake, presented to him at his 45th birthday party in Madison Square Garden back in 1962. Marilyn Monroe performed her legendary “Happy Birthday, Mr. President” at this very event.

WonderHowTo loves paper artillery. More sophisticated in construction than Box Wars, plus tense on-camera drama to boot, Cardboard Warfare is a tight homage to the paper gun. Not completely sold on the acting, but I'm really digging the mise-en-scène. Says creator Clinton Jones, aka, pwnisher:

In this tutorial, we learn how to find an IP address in Hotmail. First, open up your Hotmail in box and right click on the email you want the IP address of. Now, select "view source" and find where it says "received: from" or "X-Originating IP". This will give you the exact IP of where this email was sent from. You can use this for any email you receive and the best part is that it only takes a few simple clicks of the mouse and a few seconds out of your day! This can help you bump up securit...

Congrats to MuscleNerd, the first to jailbreak the almighty iPad. Via DVICE:

Welcome, everyone! While Linux distributions are almost always used for exploits, security, pentesting and other stuff covered in Null Byte, knowing the Windows Command Line (or Command Prompt) is a useful skill that can help you in various ways, such as using exploit programs made for Windows or using the command line on someone else's Windows computer.

Hey Everyone! Welcome to my post. We have seen a numerous GUI Tool in kali linux. Armitage, wireshark, Burpsuite etc,. Lets see an another GUI tool.

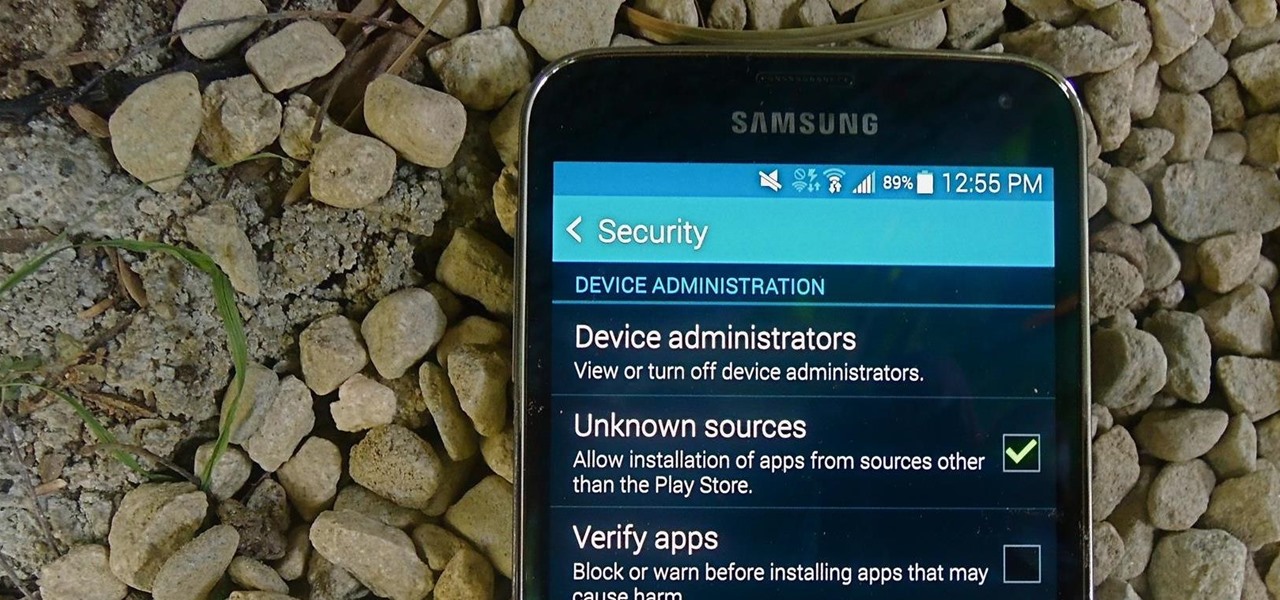
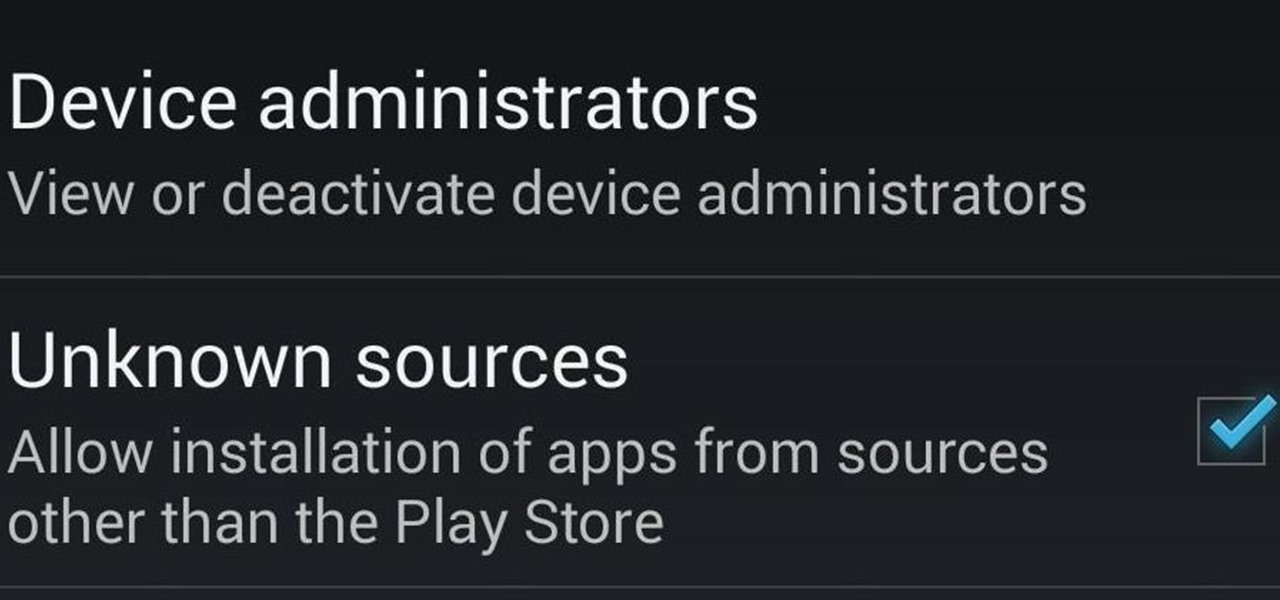
When you try to install third-party applications (meaning apps not found in the Google Play Store) you'll be met with a warning that notifies you that your device currently blocks installations not obtained from the Play Store. Enable Unknown Sources

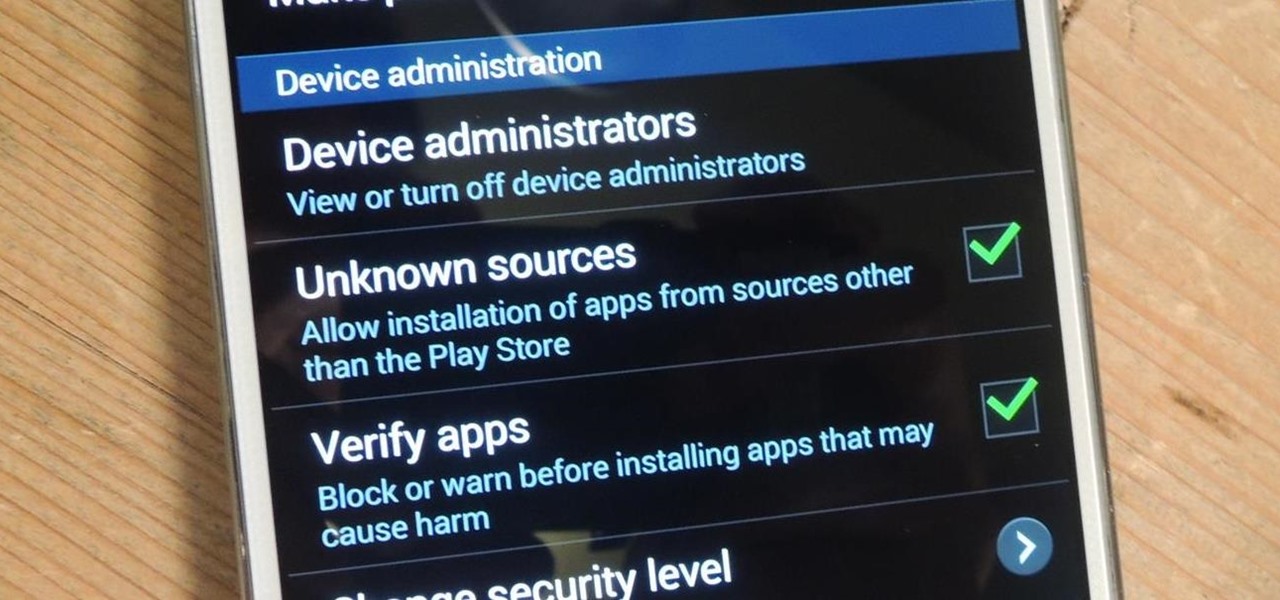
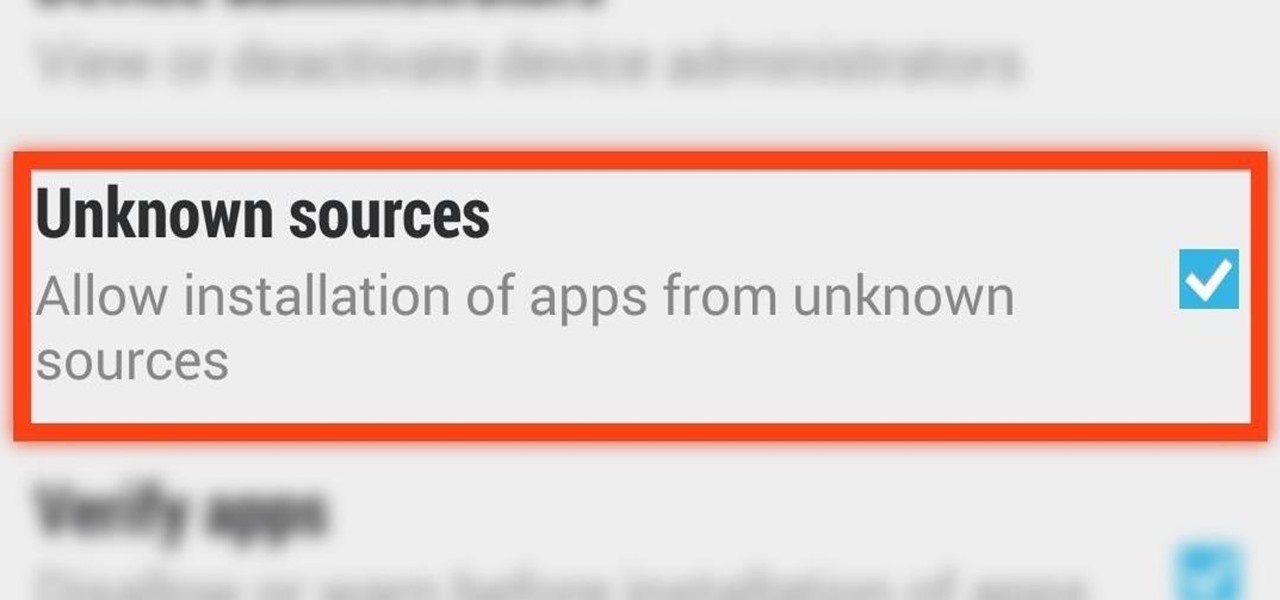
Installing applications that are not on Google Play requires you to enable a certain permission in the settings so that the whole process goes down smoothly. If you're downloading one of these third-party applications (in the form of an APK), you'll need to enable Unknown sources.

There are plenty of times where you'd want to install an app, but either the developer or Google has taken the app off the Play Store (like with Flappy Bird). To bypass the need for Google Play, you can just download the app's APK from a reliable source on the internet and install it manually.

Here's one of those modding must-haves that's basic, yet easy enough to forget about. If you're going to install apps that don't live in the Google Play Store, like the Google Experience Launcher, the OnePlus One lock screen, or something that needs root privileges like the Xposed Framework, you need to turn on this setting.

When i went to class today, a good friend asked me a question. He wanted to know what the best hacking software was to basically do everything. What i told him was this: Well there isn't an "Ultimate" tool boot there are a number of tools which deserve a "Medal." So what i'm trying to say here... What are some of the best hacking tools available right now? For starters i created a list with some of the tools.

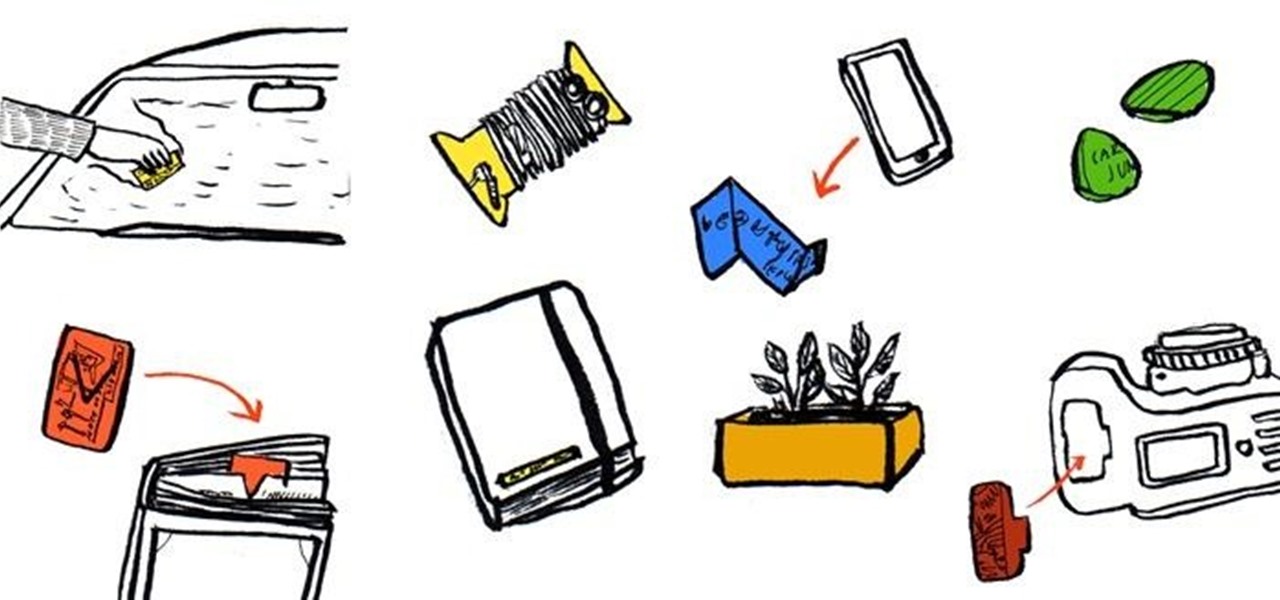
Do you have a junk drawer full of expired gift cards, membership cards, school ID cards, debit and credit cards, and other sturdy rectangular pieces of plastic you no longer use?

When you really think about it, registering for any website is a little scary. Not only do they now have your name, email address, and a username/password combination you might've used elsewhere, but certain sites and services ask for quite a bit more private information. From phone numbers to addresses to birth dates and more, that company now has all of your information stored.

Prank is played on Ehren: Have Johnny knoxville and Danger Ehren on Jimmy Kimmel with the premise that Johnny is going to do some trick with a gun. When Johhny and Ehren are on the set, have a reason for Johnny to give the gun over to Ehren and have Johnny tell Ehren to shoot it at Jimmy with the idea that the gun isn't loaded. The gun will fire a blank and Jimmy will have a blood packet in his chest go off and will pretend to have really been shot and then die. Soon as this happens, Ehren is...

Papercraft guns are the new origami. The new origami for boys, that is. WonderHowto and YouTube are chock full of paper gun tutorials. Many models are simple, but some are impressively realistic, not to mention functional. My personal favorite (unfortunately no tutorial) is the homemade Desert Eagle .50 cal by YouTube user Changmobile.

Store bought Nerf guns don't always achieve the velocity necessary for an effective assault. Zach Scott's solution: mod the toy. Known for his fantastic cat videos, Zach claims this hack increases trajectory by at least 25%! Every bit counts when you're in an all out foam war.

Admittedly, we've been quite hot on Kipkay lately, but can you blame us? This guy just keeps rolling out the wild inventions and bold pranks!

This week, California, like a growing portion of America is now 'handsfree'. As of July 1st, mobile phone use in cars became prohibited without the use of a headset.

Middle-aged man goes through the tools and process to install a security chain to a door. Tools include a door chain, screwgun, hammer, chisel and other listed tools. Step-by-step video explains thoroughly how to accomplish the chain installation. Mount a security chain to a door.
Collapse At Hand Ever since the beginning of the financial crisis and quantitative easing, the question has been before us: How can the Federal Reserve maintain zero interest rates for banks and negative real interest rates for savers and bond holders when the US government is adding $1.5 trillion to the national debt every year via its budget deficits? Not long ago the Fed announced that it was going to continue this policy for another 2 or 3 years. Indeed, the Fed is locked into the policy.

A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.
Some interesting news this week, from Obama's new political ad, to the $20,000 payments by Cardinal Dolan. Take a look:

As my in game name (TehGeekFather) would suggest I tend to like things on the Geekier side of things. Games being one of them. (duh I'm on a Forum dedicated to Minecraft) That being said I am a huge Fallout fan. (NO! not the band. <Sigh>) I'm referring to the post apocalyptic series first developed by Black Isle Studios, the roll playing game division of Interplay, back in 1997. Fallout 1 and 2 were pretty big back then open game play, being able to complete tasks in different ways depending ...

Password strength and encryption are important things when it comes to computers. A password is the entire security of your computer, and OS passwords are not hard to break. Most users believe that if you have a password on your computer via the OS, that you are safe. This is not true at all, sadly.

With Microsoft's release of the Kinect SDK, things seem to have slowed down a bit in the world of Kinect development. Have developers exhausted the uses of Kinect already? No way! Four researchers at Cornell University have created an AI-based system on the Kinect that can recognize what you're doing, and maybe even who is doing it.

He may have just started his teenage years, but Laurence Rock's future is looking pretty good after inventing an ingenious doorbell device called Smart Bell. He's already sold 20,000 units to telecoms giant Commtel Innovate, and is securing a second deal with an unidentified company that will land him £250,000. That's over $400,000!

With the globally rampant use of such social networking platforms as Facebook, Twitter, and Foursquare, the issue of privacy has become a prevalent concern for many. And for good reason—there's the violation of Facebook employing user names in ads, the Etsy slip-up, and of course, the everyman act of recklessly sharing too much information via common social media outlets: a night of drinking results in morning after embarrassment, or worst case scenario, sloppy Facebook posts and tweets resul...

Hello readers again! Sorry about the long wait (scary computer problems). Today I am going to talk to you about security problems on Wizard101. I have recently encountered many security flaws on Wizard101, including hacking, frauding and other crazy things. Wizard101 is the target for many online predators, many of who are fully-grown adults aged 60 or 70. Here is the link to an article I found about it: Wizard101 Internet Predators

Get to know Congresswoman Lucille Roybal-Allard: Congresswoman Lucille Roybal-Allard was born in Bolye Heights, Los Angeles, County, California on June 12, 1941.
Microsoft office 2010 is the successor version of office 2007 and is code named as office 14. It is the first 64 bit version of office which is only compatible with Microsoft service pack 3, Windows vista and windows 7. It was released on April 15, 2010. It is the first Microsoft application which offers free online version of word, excel, PowerPoint and one note. These can be easily used with all the popular browsing software. The various functionality which are added in office2010 are descr...

Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.

On June 23, 2003, Linden labs created a free client program known as Second Life. This program allows users, or residents, to interact with each other in a virtual world by using avatars. Thanks to this program, residents are able to explore, socialize, and create and trade virtual property, and services with each other. Second Life has become one of the most popular programs used by various age ranges from 16 to 60, but how do you enter this world and get your own avatar?

Introduction In the competitive world of today's video game scene, PC gamers are known to squeeze out the best possible visuals in their games. Every few months a new video card rolls out, and RAM is ever increasing; constant upgrading is the norm of staying ahead the curve. One of the most important things a PC gamer looks at is how many FPS (frames per second) he gets. It defines his gaming experience.

The community here on Null Byte has always been great and helpful in sharing their know-how, even before I took up admin duties in this World. I jumped at the chance of leading Null Byte because I enjoy teaching and informing people on all of the important need-to-know things out there, but more so than that—there is a deeper reason.