
HowTo: Cheat Your Way Through College
A man going by the pseudonym of Ed Dante has written an illuminating account on his life as a career cheater. His clients include ESL students, hopeless dummies, and spoiled, lazy rich kids:


A man going by the pseudonym of Ed Dante has written an illuminating account on his life as a career cheater. His clients include ESL students, hopeless dummies, and spoiled, lazy rich kids:

1. Involves gate crashing a big awards event or film opening (like what AAF did with their song 'These Days': http://www.youtube.com/watch?v=JNM2tV3PA_8).

A radical art group of Russian political pranksters, who go by the name of Voina, have delivered a giant "Up Yours!" to the Russian government... in the form of a 213-foot-tall penis.

DARPA and Dallas's Southern Methodist University are collaborating on a super high tech camera, capable of scanning eyeballs in a moving crowd.

Today's WSJ takes a tour of Russian billionaire Andrey Melnichenko's 394-foot insanely luxe yacht, coined "A".

Hiroshi Ishiguro is at it again, but this time "it" has a winning smile. Japanese researchers have developed a humanoid robot that can laugh and smile, mimicking a real person's facial expressions. The android, called Geminoid F, is modeled after a woman in her twenties, with long black hair, silicone skin and lifelike teeth.

First Ever User-Generated HD Contest Vimeo and Canon have launched this wonderful contest for filmmakers shooting on Canon's EOS 7D DSLR.

Working from home is already challenging. Add the threat of a cyberattack into the mix, and the situation gets even hairier.

The shift to remote working in response to the COVID-19 pandemic has not slowed Google's efforts to fulfill its annual Android update cycle, as the third developer preview of Android 11 dropped on Thursday.

Apple just released iOS 12.3 developer beta 5 today, Tuesday, May 7. The release coincides directly with Google I/O, Google's big hardware and software presentation, and comes eight days after the release of 12.3 dev beta 4.
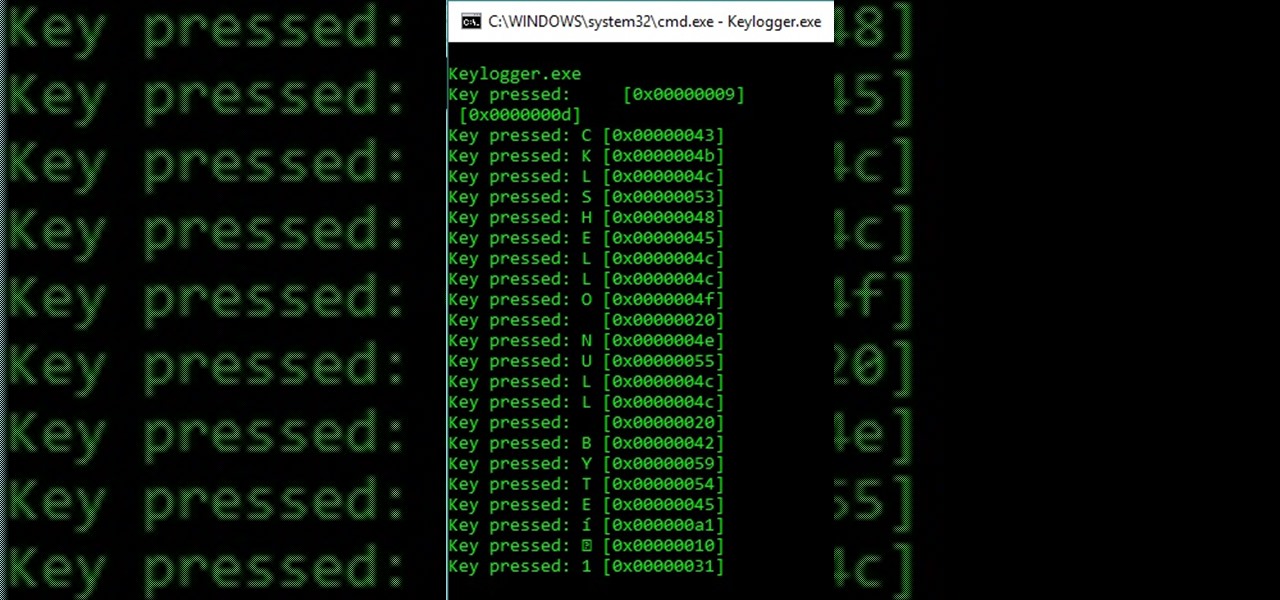
Yo yo yo, what's goin' on my devilish fiends? Have you come here to learn how to make a keylogger for malicious intent? You sly fox! But in all seriousness, this article will cover quite a simple method for creating the most basic of Windows keyloggers. You're in for a surprise! Let's dive right in!

Okay guys and gals, this will be a quick tutorial on using the incredibly helpful man pages. What Are Man Pages?
Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

So you've got your shiny new LG G3, your accounts are all set up, and Google has restored all of your apps. Well... almost all of them.

The latest update to Google Search, which is rolling out right now, brings automatic parking spot pinning through its Google Now platform.

Google is set to release an update to their Hangouts messaging service starting this week. The update to version 2.1.075 brings new features, with the biggest ones being merged chat and SMS messages and a home screen widget. Here's a complete breakdown of the new features you can expect.
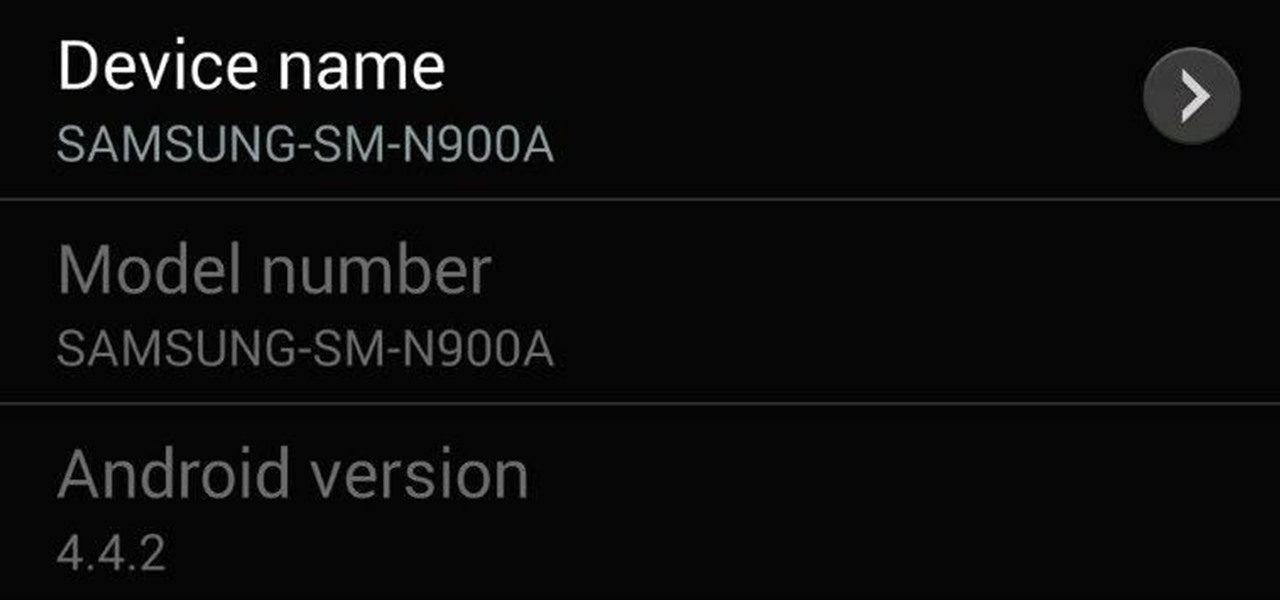
After leaks and rollouts from rival carriers, AT&T has finally released their official Android 4.4.2 KitKat update for the Galaxy Note 3. If you haven't received your update notification, force a manual check by going to Settings -> More -> About Device -> Software Update -> Check for Updates. Make sure you're connected to Wifi and have at least 50% battery remaining. This update includes:

The guys over at @evleaks continue their slow trickle of leaks about Samsung's upcoming flagship device. The first drop is simple enough, a confirmation that Samsung will continue its branding strategy, naming their next device the Samsung Galaxy S5. These next two are a little more interesting, despite their graphical shortcomings—screenshots of two APKs, or application files, from an "official" Galaxy S5 system dump.
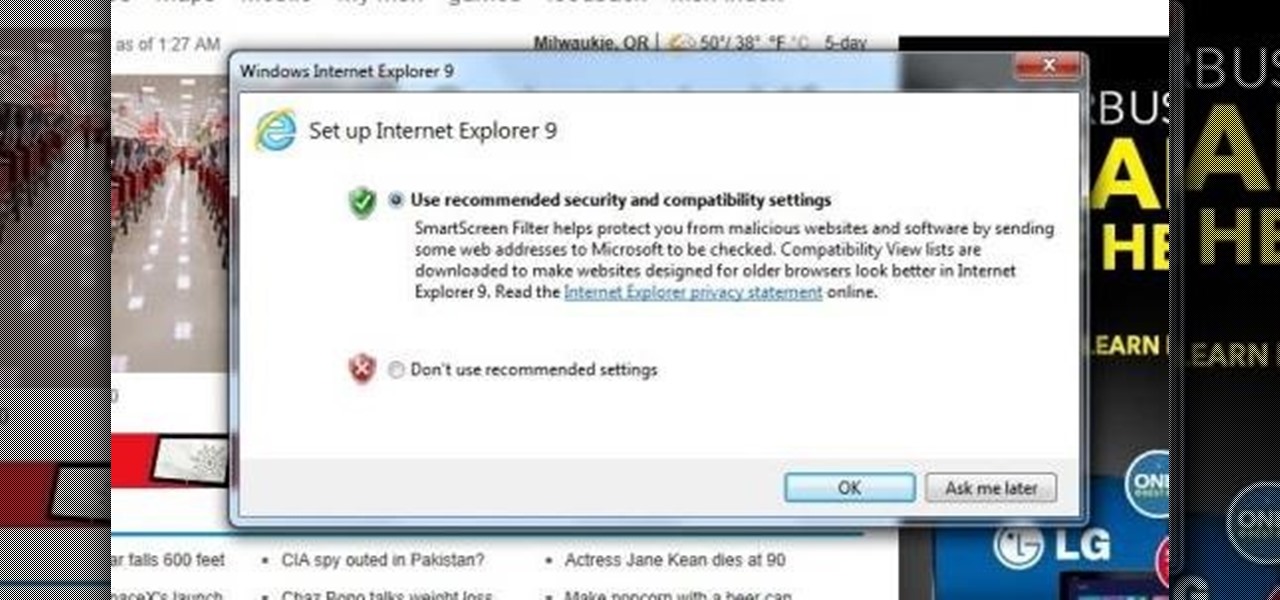
After you've updated Windows 7. Internet Explorer 9 is automatically installed. This is just a two step process of knowing it's been upgraded, and is ready to run and get you on the web.
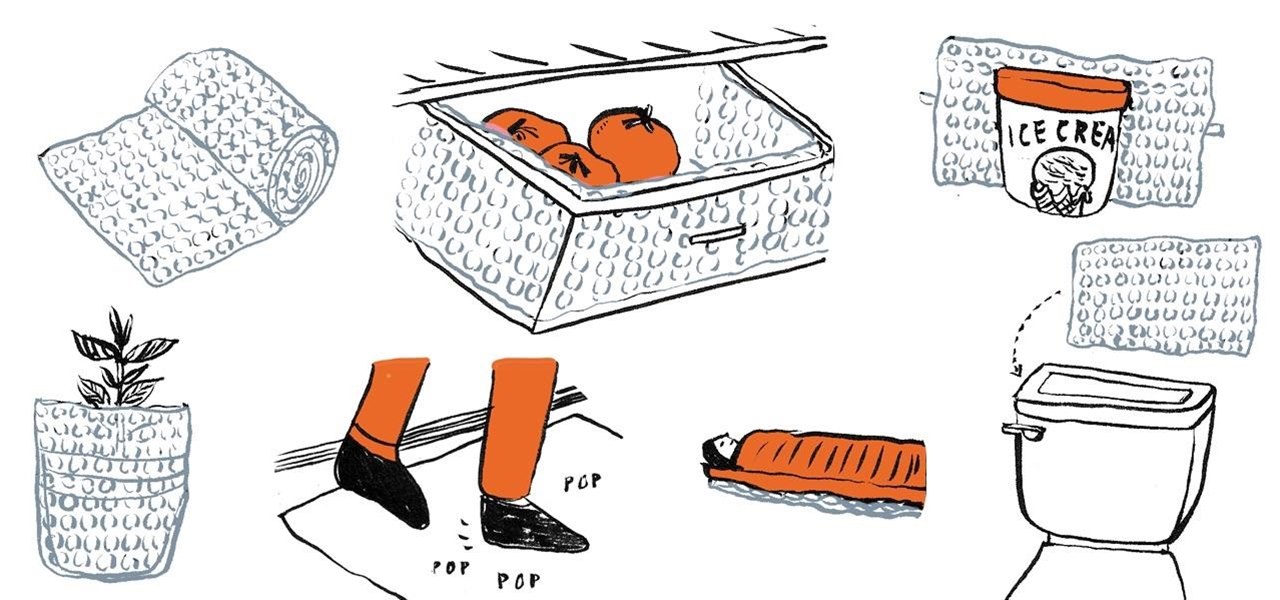
If you're like me, you have a secret dream of living in a house completely covered wall-to-wall and carpet-to-carpet in bubble wrap. Until you have enough of that pliable transparent plastic with air-filled bubbles, there are some truly practical things you can do with the little you do have—besides packing fragile objects.
Adblock Plus is a well known add-on for Google Chrome and Firefox that eliminates all of those annoying and obtrusive advertisements on the webpages that you visit.

There are so many unpleasant things about flying. You have to wait in line after line, take off your shoes, belt, and jewelry, and somehow make sure your luggage stays intact. And then, once you've made it onto the plane, there are the awful movies that most airlines play—if you even get a movie.

Imagine you're calling the court. You have this unpaid ticket and want to know if you can get an extension. First you type your ID number on your phone. Then the case number. Then your birthday. Then your social security number. Then you're directed to thirty different people.

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?

Microsoft just revealed the preview of its latest incarnation of Webmail, Outlook.com. One particular Outlook.com feature worth noting, is its support of multiple e-mail aliases. They're a great way to protect your primary e-mail address. And because you can't log in to your Outlook.com account with an alias, it adds another level of security. How To Add an alias

The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...

We all know the dangers of logging on to our personal accounts on public networks, but we pretty much all do it anyway—especially when it comes to Facebook. But the next time you're in a public place and can't wait to check out your Facebook news feed, use this simple trick to make sure that no one gets a hold of your password. In order for this to work, your mobile phone needs to be linked to your Facebook account. All you have to do is text "otp" (for one time password) to the number 32665.

Attention cheapskates and locksmith apprentices, this key copying solution is stunningly simple. We've really mulled over this one. As you can read in the comments below, people struggle with executing this successfully. But it can and will work. You just have to modify your key to fit your needs.

What is Internet Download Manager? Internet Download Manager (IDM) is a tool to increase download speeds by up to 10 times, resume and schedule downloads. Have you ever wanted to increase you download speed form 4kps to 80kps? If you answered yes then you need Internet Download Manager. It can and will increase your download speed so you can get the files you want quicker and easier than ever before.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

A Google trick to bypass computer security at your school and access blocked websites. Access blocked websites using Google.

How to bypass the web security at your school to go to restricted websites. Access any website at school.

As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end.

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

Just last week, the Flashback trojan scared a lot of Mac users. Now, there's yet another trojan spreading across Mac computers—SabPub. The same Java vulnerability that allowed Flashback in seems to be how this SabPub malware snuck in, along with an Office vulnerability, which was just identified this weekend.

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

US can legally kill Americans in terror groups You read it right. The US can now target Americans who are supposedly part of terrorist groups. Here's my analysis of Attorney General Eric Holder points (keep in mind though, these are point's brought up by MSNBC, original article here):