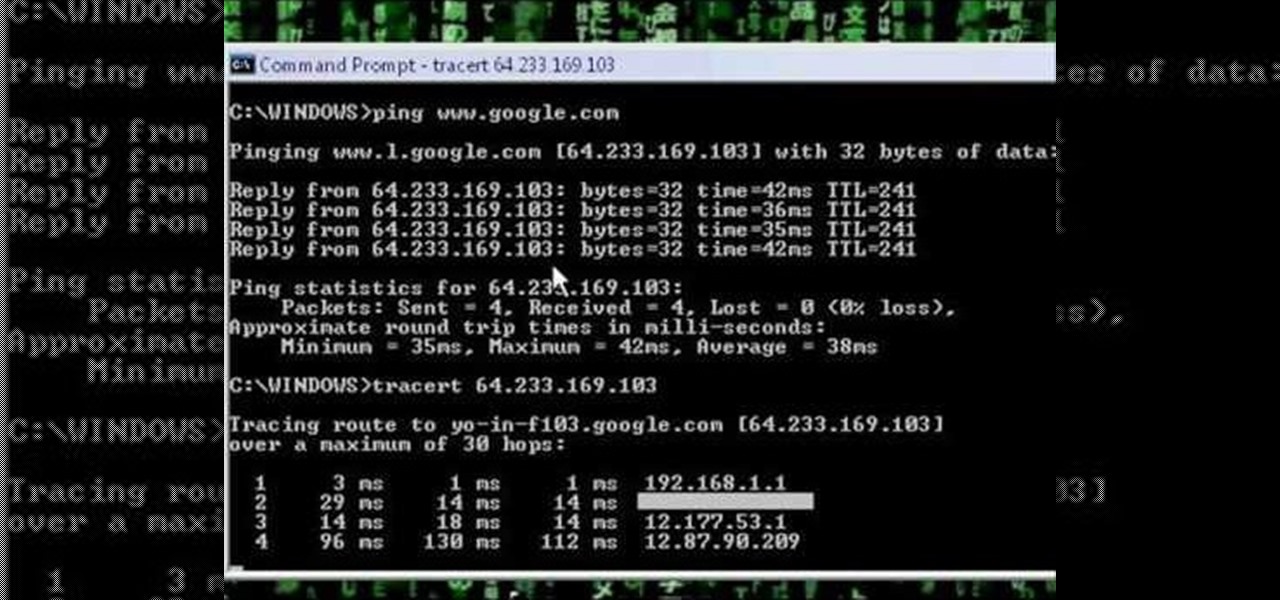
How To: Ping and trace a network
A network security tutorial on using ping and tracert to show th IP of a webserver, your own IP, your ISP's IP, who they connect to, and what computers your request goes through before reaching a destination.


A network security tutorial on using ping and tracert to show th IP of a webserver, your own IP, your ISP's IP, who they connect to, and what computers your request goes through before reaching a destination.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

When it comes to web-based augmented reality, 8th Wall has emerged as one of the leading platform providers, and the company just cranked up its capabilities another notch for AR marketers.

In the business world, it's sometimes said that "where there's smoke, there's fire." At Snapchat parent company Snap, Inc., it appears the equivalent of smoke is executive turnover.
The Pixel 3 XL versus Galaxy Note 9. Stock Android versus Samsung Experience. When I began this comparison, I thought the Pixel 3 XL would be unfairly outmatched. But after looking at the specs side-by-side, you'll see a different picture. This year, Google delivered a worthy alternative to Samsung's best offering.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

CEO (and NR50 member) Tim Cook and Apple unveiled the long-awaited lineup of next-generation iPhones today on stage of the Steve Jobs Theater, packed with hardware improvements to facilitate AR experiences from ARKit, which will arrive with the iOS 11 on Sept. 19.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.
After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.
Google's monthly Android security updates are generally welcome—at the very least, they provide a feeling of security that our device is now somewhat safer than it was 30 days ago. Vulnerability patches, slight enhancements to performance, and overall bug fixes are generally included in the monthly OTAs, but as it turns out, they're not always for the better.
Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.

Nearly nine months after the release of the iPhone 6 and 6 Plus, we finally have some solid information on the "S" model of Apple's flagship device, slated for release this fall. Coming straight from Apple analyst Ming-Chi Kuo of KGI Securities (via AppleInsider), quite a few upgrades will be included in the next iPhone model.

If you keep sensitive data on your phone, you've surely considered a "lockout" app before. There are many such apps that can add an extra layer of security to other apps within Android. For instance, you can require a PIN or password before anyone is able to launch a particular app.

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

#FOMO. If it bugs the living hell out of you that you don't know what that means, you're presently FOMO, as in you've got a Fear of Missing Out.

Most hardcore Android fans loathe carrier or manufacturer additions to the Android operating system. Whether it's bloatware or changes to the user interface, many enthusiasts prefer the clean look of stock Android.
» Homeland Security Report Lists ‘Liberty Lovers’ As Terrorists. A new study funded by the Department of Homeland Security characterizes Americans who are “suspicious of centralized federal authority,” and “reverent of individual liberty” as “extreme right-wing” terrorists. » British police get battlefield weapons.

So you want to control the flashes on your camera using a remote, and you know that you need to get to Master mode on your Canon 580EX II to be able to do that. But Canon made Master mode for this particular model of camera very difficult to locate and enable. However, this video shows you every single step you need to take with your camera in order to be able to set up this particular functionality for your next shoot!

The Arriflex S is a high grade, professional quality 16mm camera. It can shoot steady, consistent film footage. This tutorial shows you how to properly load your film into the camera and a few other tips for getting the most out of your equipment.

This tutorial goes over the Canon manual lenses that are produced with film cameras in mind, but you can buy an adapter to fit them to your digital cameras. This tutorial shows you how to use these FD lenses, and why you would want to.

The Camera Mapper plugin for Adobe After Effects shows you how to create a realistic zoom, where objects in the foreground move faster than objects in the background. Set up a realistic parallax and sell your shot by using Camera Mapper.

Not only does this camera mount take less than five minutes to make, you can do it for less than ten dollars. Mount a camera to your car for greater versatility in how and what you film for your next project!

A remote control for a camera? Why not! You won't have to worry about racing the timer function any more! Build a remote control for your digital camera that will take the picture whenever you want. The range is as far as two miles!

Cell phones and mobile devices are getting more and more advanced everyday, and so is the equipped camera technology. You can now shoot HD (high-definition) video on newer mobile phones, which makes it easier to start your filmmaking projects, because it's a lot cheaper to buy a phone than a video camcorder. But, phones come in small packages, which means the video from your camera will be extremely shaky, no matter how steady of a hand you have. That's when it's necessary to have a camera st...

Wow. Forget about buying an expensive pro-style digital camcorder. You can make your DSLR camera into a moviemaker camera with a simple DIY shoulder mount. The goal of this video is to give you a way to create a low budget way of mounting your camera and necessary gear onto a cheap shoulder mount. It works really well. See for yourself!

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to lock the camera as well as create lighting effects, city terrain, and short cinematics in the Starcr...
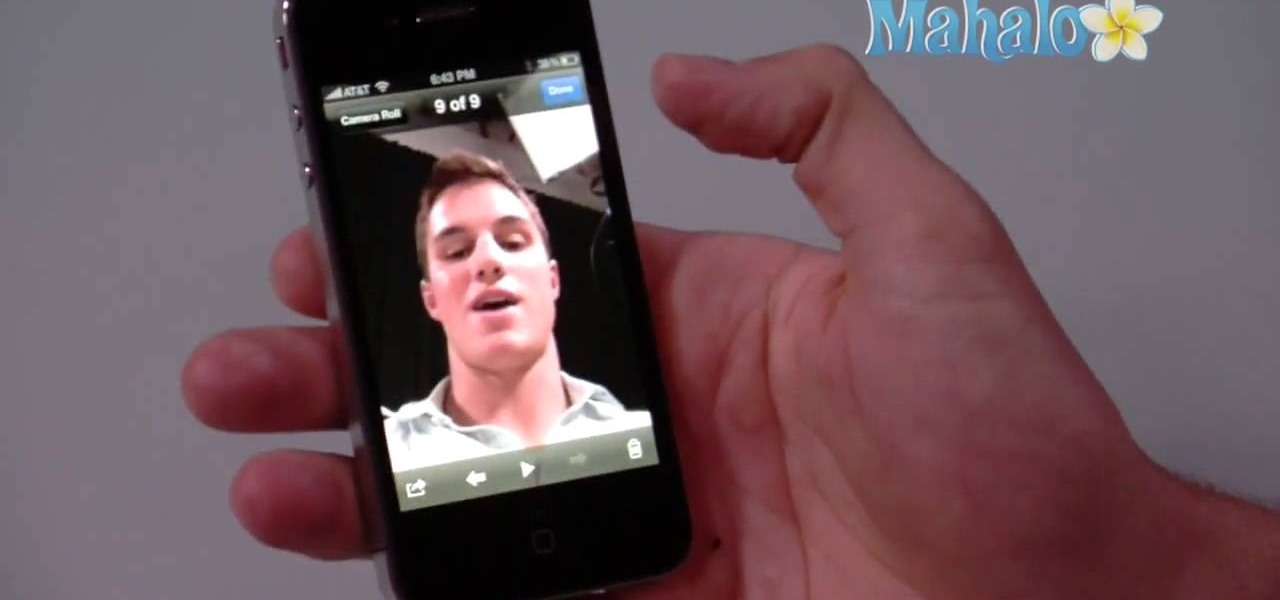
The iPhone 4 is unique because it comes with not one, but two cameras. The front facing camera on your phone can be used to take your own picture, for games or to use the new FaceTime app to video call your buddies. This tutorial will walk you through how to use this fun new feature and how to make the most of it.

A great way to get picture perfect shots and protect your camera in the process is to use a lens hood. When shooting on your DSLR outdoors, a lens hood will definitely come in handy. In this tutorial, learn how to get the best and most affordable lens cover for your camera and make sure you take an amazing shot every time.

For this Final Cut Studio video tutorial, Zach King will teach you how to use the camera in Motion. If you want to cover the basics of adding and using a camera in the Motion 3 program, this is the perfect video to help you out. Let the Final Cut King show you how!