This cinematography tutorial explains how to setup the Redrock mircroShouldermount for the first time. The video covers two basic configurations: for a stock video camera and for an existing camera setup. The Redrock shoulder mount is a modular system designed to meet an individual's customizable needs.

Watch this quick instructional cinematography video that shows how to balance a Canon XL2 professional HD digital camera on a GlideCam 4000 Pro. Learn how to secure the camera using this handheld camcorder stabilizer to prevent unwanted swaying, shoot fluid traveling shots, and produce professional works.

See how to use the depth of field adapter, the Letus Extreme, for your digital camcorders. Also see 35mm adapters for your digital cameras. Great for that professional look you need in your film.

Want to be an astrophotagrapher? Here is the simple facts of taking photos of those beautiful stars using your telescope and a camera. More advanced photographers tend to use a chilled camera though, so watch and learn.

This video will give you shocking results. Find out how to make a couple of alterations using paper clips and a screwdriver to turn a disposable camera into a taser.

This is a pretty intense tazer (or taser) construction using a disposable camera and some hard core circuitry.

In this DIY video, we show you how we built our camera crane. This was all done with a table saw, drill and hack saw.

Learn to to make a fisheye lens for your digital camera using only a peep hole from a door and some tape.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Turn your digital footage into something that looks more like film! Set your frame rate to 24 and shoot with a low depth of field to mimic the look of a film camera. Also make sure you pick the right aspect ratio, resolution and use a tripod!

New to the world of DSLR video and need a hand distinguishing between different lens types? This video offers some pointers for would-be shooters. For details, and to get started using different lenses with your own Canon or Nikon DSLR, watch this video guide.

If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...

Don't fret too much if your watermark is barely noticeable when you're finished with this project - the less obvious it is, the better a job you've done. Watermarkers are present in many types of paper, especially the monetary kind. If you hold up a ten dollar bill you'll see a watermark of Thomas Jefferson's face on the right, proving the bill is real.

Use Microsoft Windows 7? Miss the old Ctrl-Alt-Delete log-in prompt? It's easy to restore. So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete overview of the restoration process in just over a minute's time. For more information, and to get started restoring this useful security feature on your own Windows 7 PC, watch this free video tutorial.

If you move around a lot, you may notice that you can't play the same DVDs from country to country. The world is separated into different regions, and not all movies will play in all places. There are ways around this security measure, however, if you follow this tutorial.

In order to get the Canon 5D Mark II production ready, you're going to need to invest in a few accessories to get you up to speed. Fortunately, this video from Mauro Media gives a great breakdown of how you can get your slick camera up and ready to go for any handheld doc, narrative, or ENG shoot.

Canon recently released a firmware update to fix a lot of the v.1 bugs. This tutorial explains the process of updated the firmware from downloading on the Canon site to easily installing it on your camera.

The PhotoshopUniverse team effectively teaches a method of adding a watermark to an image, as a security feature to make it harder to copy or steal. Instructions are simple and easy to follow, using as an example a photo of two girls that one might have in his or her family album. Using Photoshop, the text that will become the watermark is added, rotated and patterned across the entire image. To finalize the watermark, the opacity is edited to a desired value so that it does not interfere wit...

This video shows you how to make a security device out of a door bell. The concept is that most thefts happen when people are away from home. To make sure of this the thief rings the door bell to make sure that nobody is home, if nobody answers then they will break in. A lot of people have dogs and alarm systems which will scare off the thieves, but this alarm system combines both. To make this devise you have to buy a speaker system that connects to your door bell. When the door bell rings i...

Videomaker Associate Editor Tom Skowronski explains how four basic steps can be used to improve the lighting effects for a video and give it a more professional look.

DreamWelder Productions presents this video tutorial from their show Info Tech, hosted by Jay A. Kelley. They take an exciting new look into new equipment for the film and television industry, showing you the best gear for your movies and shows.

Check out this RESIDENT EVIL 5 Chapter 2: Gigante walkthrough from Machinima.com The behemoth from RE4 returns with some new tricks up his sleeve.

There are two ways to properly lock your seat belt. You can use the childlock auto adhjustment. Or you can recline the seat, but then push forward to make your seat belt very tight. You don't want to be flopping around in the car. The bottom of your wrist is on top of the steering wheel and your shoulder is in the seat. It will loosen up when you get on the track.

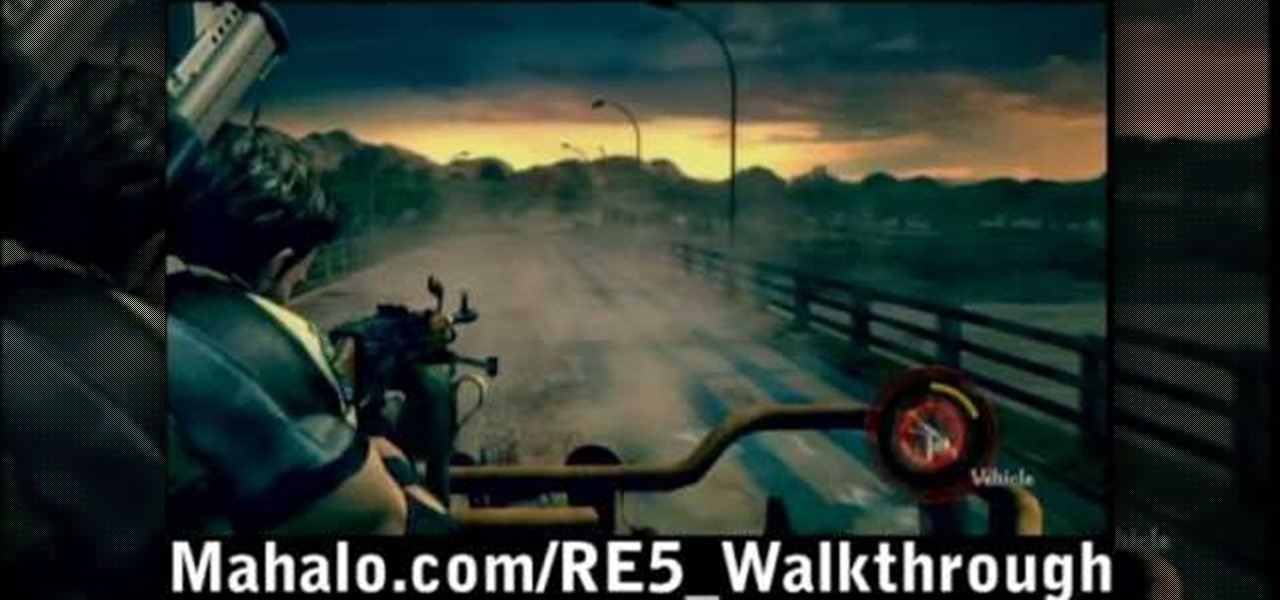
Check out this Mahalo video walkthrough of Savannah in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

This video will show you how to fake a RAM, Flash, or entire memory clear. Lots of teachers and test administrators go around and clear your calculator so students don't cheat. This is any easy way to subvert the teacher's security measure. This is a good thing to know if you want to cheat on your GED, SAT or ACT test / exam.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

If you're interested in creating a dosimeter using simple tools, take a look at this video. Using a digital camera, a plastic scintillator, and some tape a radiation dosimeter can be crafted allowing for radiation information to be collected with simple materials.

Looking for a way to record what you see from your motorcycle? Check out this video and learn how to mount a 1080p HD camera in a motocross helmet. Capture awesome high quality video of your rides with this 1080p helmet cam mount.

The iPad 2 had two cameras built in, put them to use! You can film video with your iPad's camera and then edit it using the iMovie app from Apple's app store. This video will show you how to use iMovie for video editing.

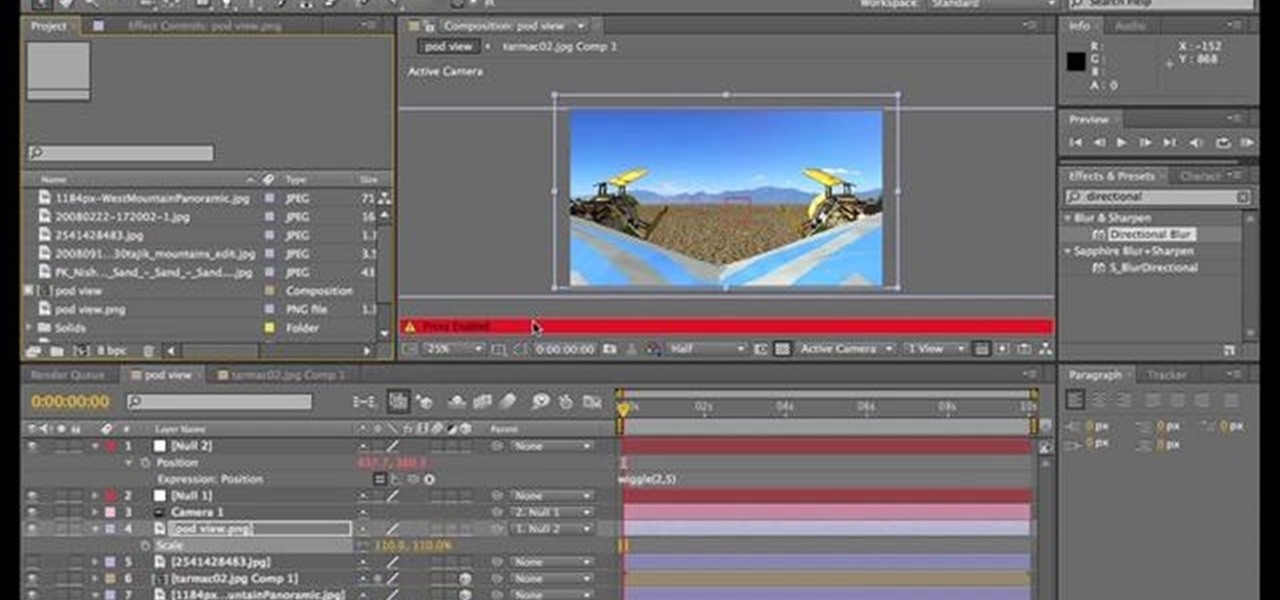
In this tutorial, After Effects is used in actual realtime to create a video comp that simulates a forward three-dimensional movement. Several images are arranged into a layered, three-dimensional composition, and a single image is tiled into a surface pattern that is offset tilted and scrolled forward indefinitely. Several additional elements are also mentioned to add realism and depth to the forward scrolling movement, including foreground elements, background images, camera shake, camera p...

This system won't replace the need for a tripod entirely, but it's a great way to use both a superclamp and an articulated arm to give you a little extra camera support if you can't use a tripod for a particular shot.

This tutorial shows you how to set up a very stylized shot that's ideal for shooting music videos. Choose and set up the right kinds of lighting setups, and then make sure you get just the right camera angle for your project.

Start with a Targus Monopod, and then follow along with this tutorial to create a BodyPod - a body harness that will let you 'wear' your camera. This modification costs less than fifteen dollars, and lets you cut down on the gear you'll need when filming.

The Bolex is an amazing professional quality camera. This is quick tutorial that shows you how you can load film into one, and a few more basic features that you can take advantage of to get the best film quality possible for your projects.

Trying to get that perfect ground shot done, but just can't seem to make it work? This is the tutorial for you! This video covers a few techniques any cinematographer can use to pull off a stunning movie shot with a low camera angle.

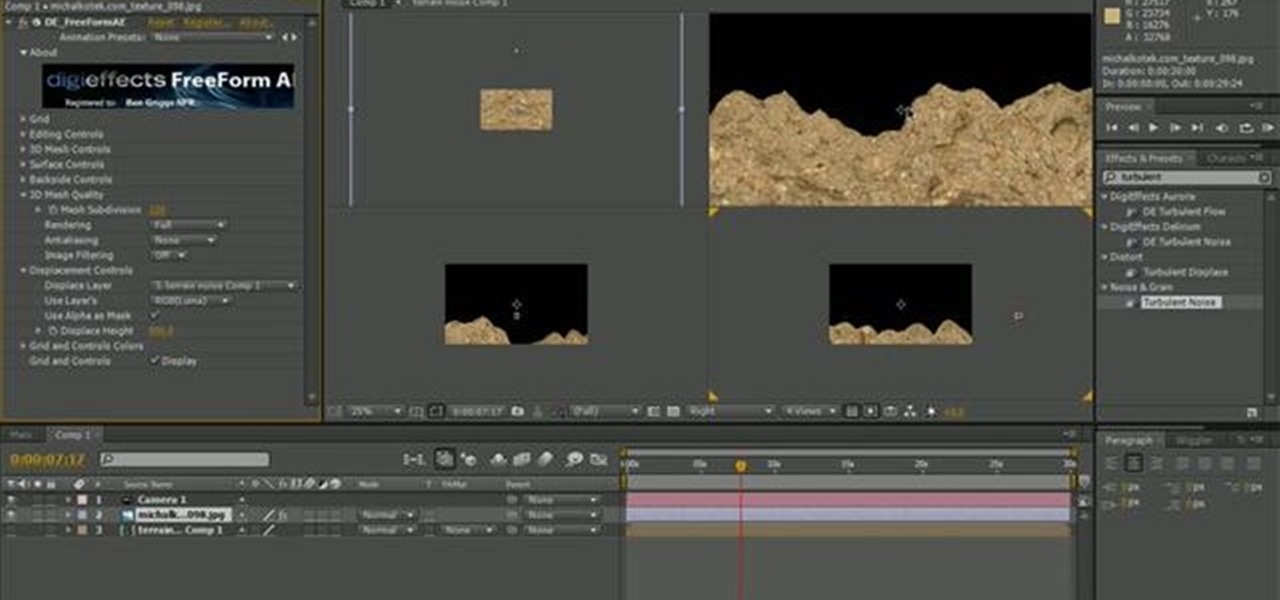
This tutorial shows you first how to create some basic outdoor terrain in Adobe After Effects. Then, create a camera effect which makes it look like your camera is slowly flying over the terrain using the FreeForm plugin for After Effects.

What's this mysterious .thm file? Why are they cluttering up your SD card? Can they be safely deleted? This video has the answers! A .thm file is created specifically by Canon cameras when you're filming a movie, and this video shows you how to use your .thm files.

No extra tripods or dollies required! This tutorial shows you the 'steadyhand' technique: a way for you to hold your video camera in your bare hands without any tremors or shaking. The trick is to not hold it too tightly.

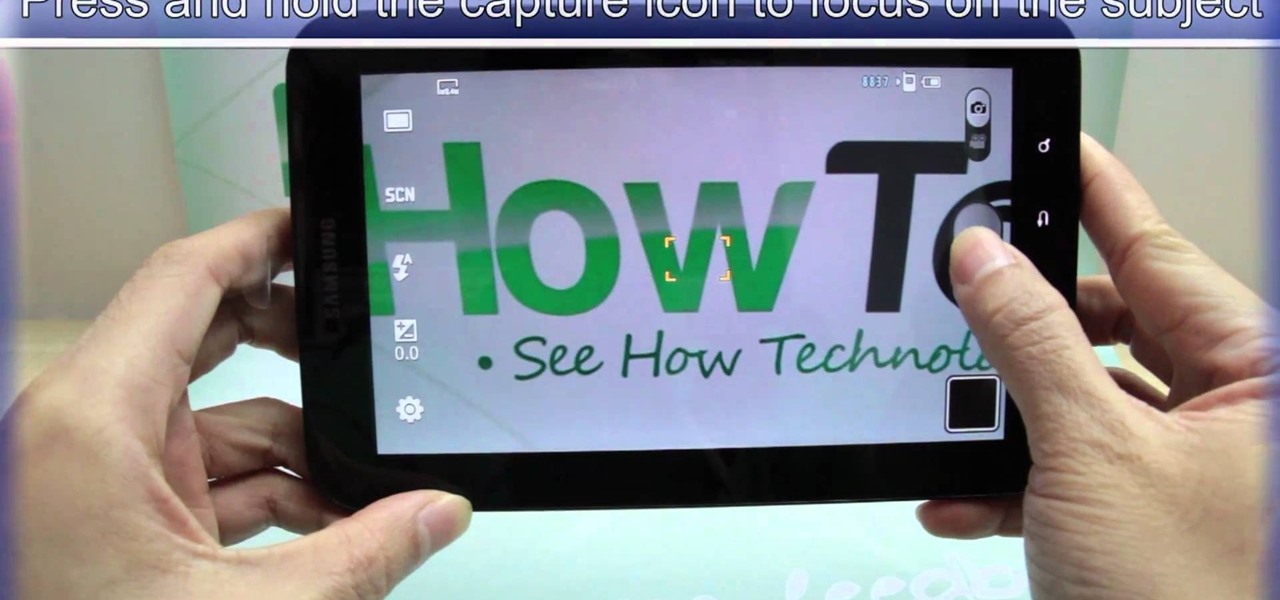
This video shows you how to use the camera on Samsung GALAXY Tab.