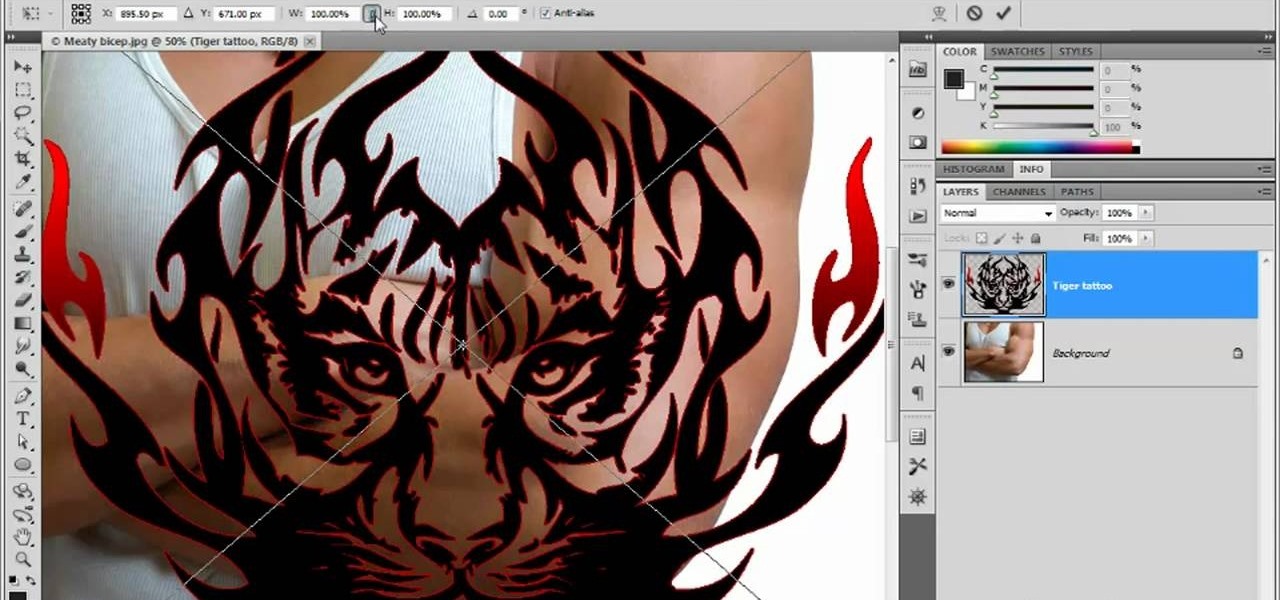
Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.
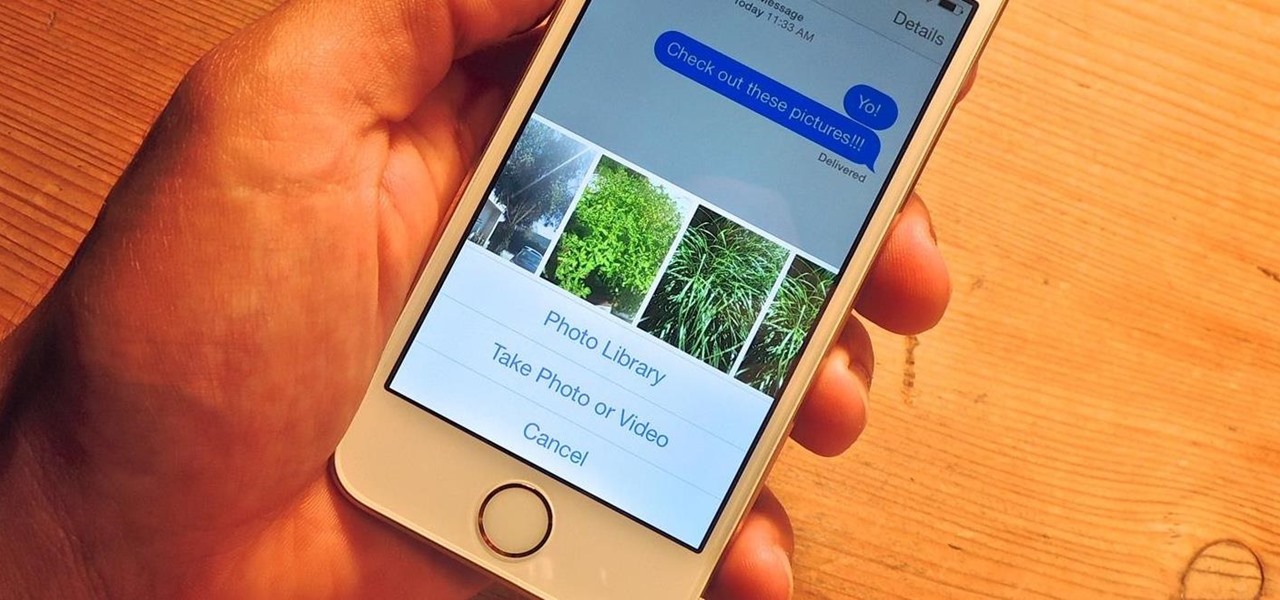
As it is right now, you can only send 5 images by email at the same time from your Camera Roll in iOS 7. There are some workarounds to increase that number, but a new feature in iOS 8 is finally making them unnecessary.

If you have Android KitKat, you're fortunate enough to be able to use the new Google Camera, which has tons of great features, including Photo Sphere, Tiny Planet, Panorama, and Fisheye. With so many photo options and no additional hardware needed, it's hard to not to like this camera.
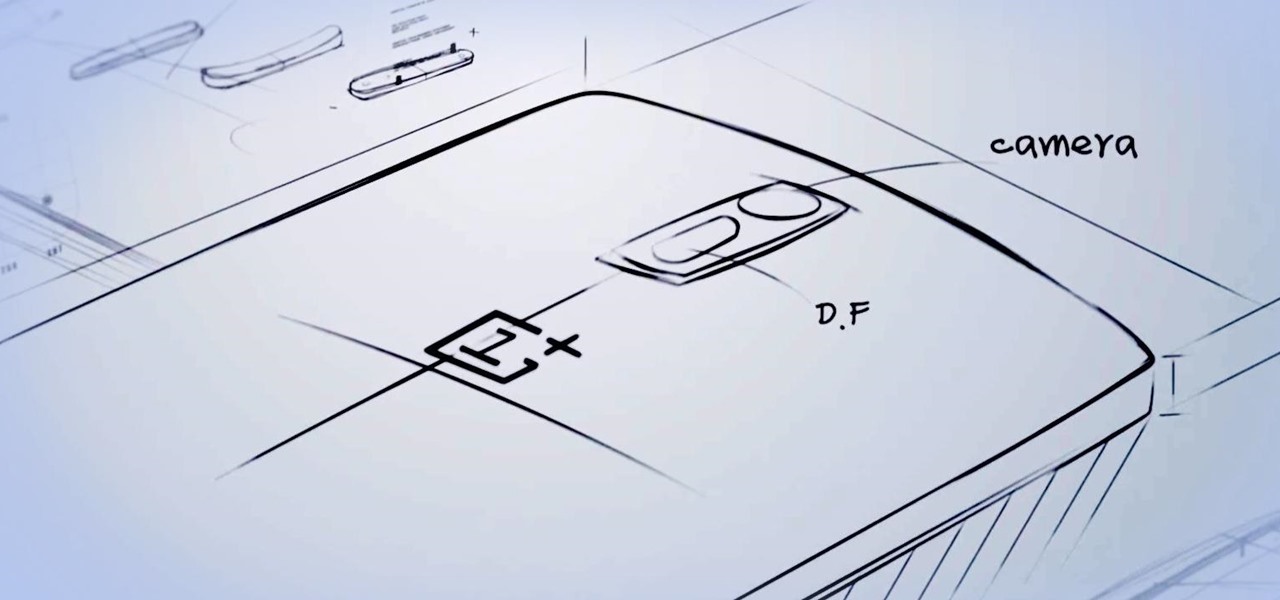
After lots of waiting and anticipation, the OnePlus One Android smartphone has been unveiled, and it's ready to take down the Nexus.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

Some of my favorites hacks are the ones that speed up the process of accessing my favorite and most-used apps. So, in this softModder guide, I'll be showing you a super fast way to open those apps straight from your Samsung Galaxy Note 3's lock screen.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

If somebody really wants to gain access to your iPhone, they'll get in. Phone thieves (and mischievous friends) can easily figure out your passcode just from looking over your shoulder or tracing over the oily smudges on the screen. And if you're using popular passcodes, birthdays, and addresses on your iPhone, you might as well disable lock screen security entirely.

The lockout feature in iOS 7, which securely locks your device after a few incorrect passcode entries, can be a real pain in the ass sometimes.

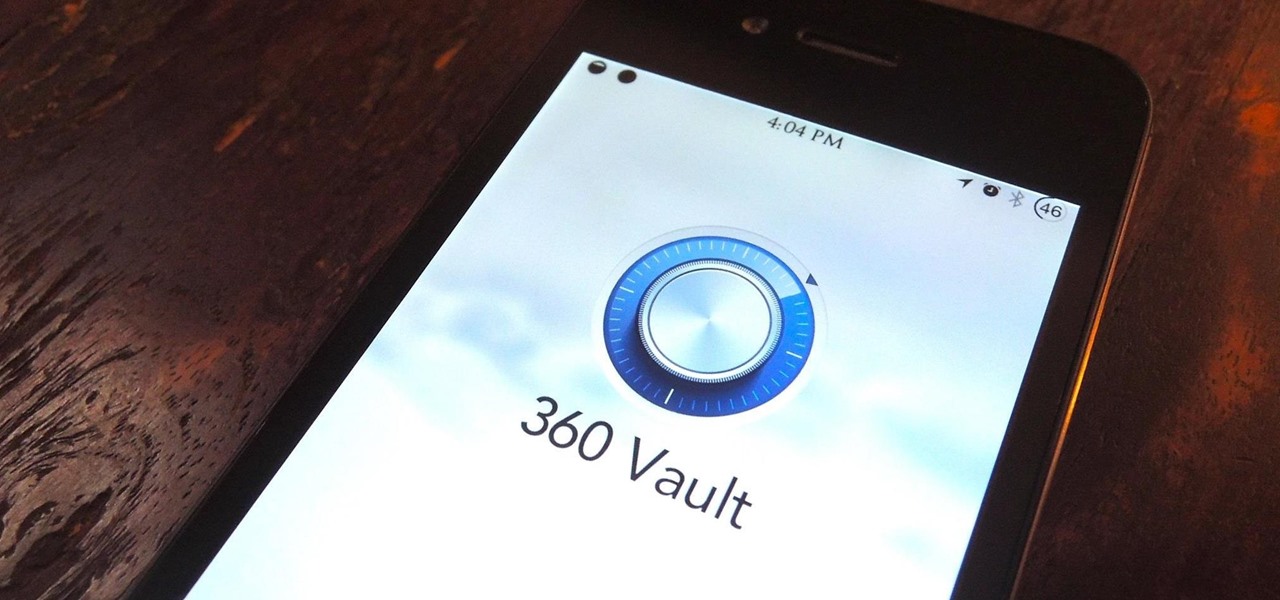
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

For those of you who have (or had) and iPhone, one of the cooler photo apps for iOS was VSCO Cam, an extremely popular camera with pro-quality filters and effects. Now this app is available for Android on Google Play for your Nexus 7 tablet and any other devices running Android 4.0 and up.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Selfies are on there way out. Not because I said so, but just because I want them to. They're both aberrant and curious. They carefully hobble between the lines of self-exploration and crippling insecurities terribly masked as blatant narcissism.

Cinema is a matter of what's in the frame and what's out, according to director Martin Scorsese, who asserted that when describing his life's work. Getting the perfect shot can turn an otherwise ordinary scene into something great, both on and off screen.

Even though iOS 6.1 was only released a couple of weeks ago, hackers released evasi0n a couple days after. Evasi0n, the only iPhone 5 jailbreak currently on the market, is the most popular jailbreak in history—with nearly 7 million iOS devices already hacked in the mere four days after its release. Well, now it seems that iOS 6.1 is being taken advantage of again, this time with a simple exploit figured out by YouTube user S1riOS6, which lets you bypass the lock screen on an iPhone running iO...

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks at Facebook are using this technology. Obviously, this brings up some pretty serious privacy concerns amongst most people, because honestly, who wants to be tracked? Right now, there's not a lot we can do about it being ...

UPDATE: A patch to fix the exploit has been released. Download it here.

Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on.

It can be incredibly frustrating to take closeup shots with an iPhone camera—or any smartphone camera for that matter. Even if your phone's camera is top of the line, you'll still get a fuzzy picture if you get to close to your subject.

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...

When it comes to working with people, the photographer can face quite a challenge. Everyone has a mind of their own, and with these few tips you will know how to advise your subject so they look fantastic in a picture. Join Erin Manning, professional photographer, as she shows us 5 handy tips for working with people.

Here's a quick, easy and useful tip: The next time you go to take a picture on your Apple iPhone, try holding the shutter button down as opposed to tapping it. The reason? Tapping can destabilize the camera, resulting in motion blur. Whereas holding the button will ensure that you get a great shot.

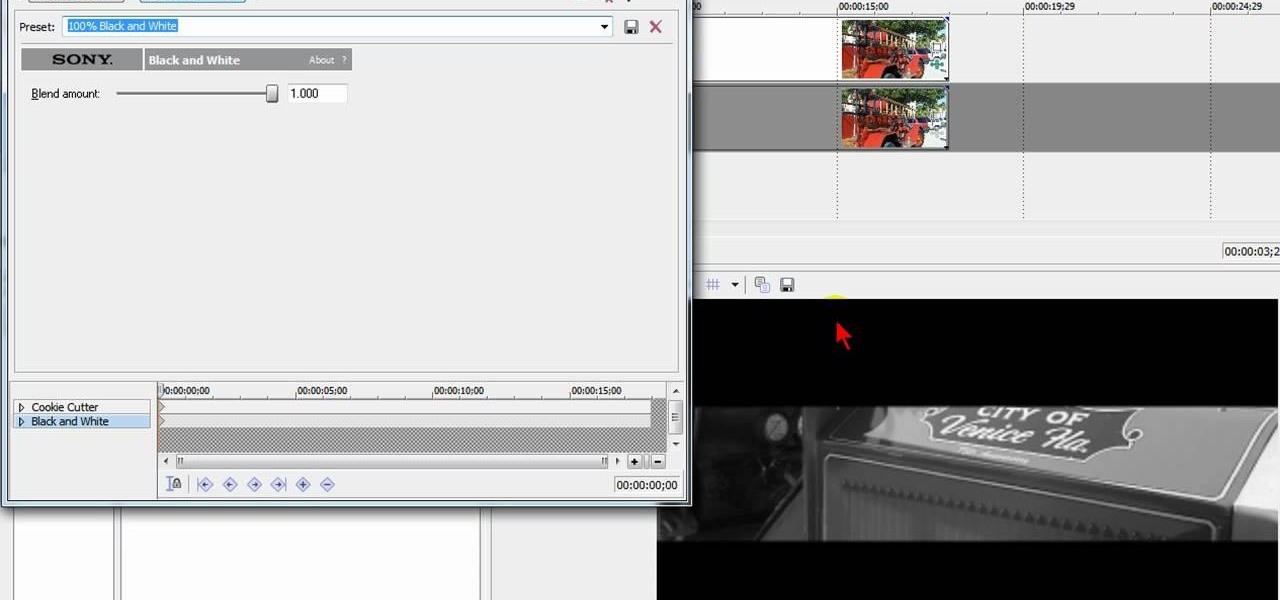
Lights, camera and coolness! You've seen this effect in several music videos and it's time for you to learn the trick yourself. Using Sony Vegas you can create a slick 'cookie cutter' effect (essentially slicing up the screen with a B&W bar). Impress friends and family and rock your home music video world!

This is a workflow tutorial for people who use the Nikon D90 camera and do most of the post production in Adobe After Effects. Convert, cut and export your video easily, and even fix the stair-stepping problem that might crop up.

Filming a wedding soon? What if you can only bring one lens with you to an event? This tutorial shows you the various video camera lenses you can use, and which ones are the best to use when filming a wedding or other special event.

This is a quick tutorial on a few pieces of film equipment that are especially well suited to filming outdoors - specifically, the Sony EX1 video camera, and the Letus Extreme 35 mm lens adapter, as well as the hardware you'll need to be able to use it.

You can still make great high definition videos using the Canon digital SLR camera line. This video gives you quite a few tips you can use to start creating your own videos and movies - the most important one of which is to have fun!

If you have a DSLR, you can take some interesting photographs of Christmas trees and holiday lights this year. Here are six different ways to achieve a special effects look for your Christmas photographs by adjusting the settings on your camera.

In this video tutorial, we learn how to create two separate exposures for the same image with Camera Raw when retouching a digital photograph in Adobe Photoshop CS5. Whether you're new to Adobe's popular raster graphics editor or a seasoned designer looking to better acquaint yourself with the new features and functions of the latest iteration of the application, you're sure to benefit from this free software tutorial. For more information, watch this video guide.

A green screen lets you add any sort of background to your movie in post-production. Part of a successful green screen shot is properly lighting your set so you can easily add the special effects later. Teach your camera crew these tips for your next film!

In this 35-minute clip, you'll learn how to take advantage of the Camera RAW feature in Adobe Photoshop CS4 and CS5. Whether you're new to Adobe's popular raster graphics editor or a seasoned designer looking to better acquaint yourself with the new features and functions of the latest iteration of the application, you're sure to benefit from this free software tutorial. For more information, watch this video guide.

Learn how to utilize depth-of-field camera effects in your MAXON C4D projects with this helpful guide. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get started using this trick in your own Cinema 4D projects, watch this 3D modeler's guide.

Thanks to the influx of purse-sized digital cameras and wads of blurry, hastily taken drunken photos posted on Facebook by partying college students, the quality of photography by the masses has gone down the deep end.

In this FCP tutorial, you'll learn how to keyframe the mask shape filter with blur to track the movement of the camera. Whether you're new to Apple's Final Cut Pro non-linear video editor or just looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial. For specifics, including detailed instructions, watch this Final Cut Pro lesson.