
How To: The Essential Skills to Becoming a Master Hacker
Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"


Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.

This is a trouser belt, but can also be applied as a bag strap, maybe used as a camera strap, etc. To make a macrame belt, measure the cords to your desired length. Tie using square knots.
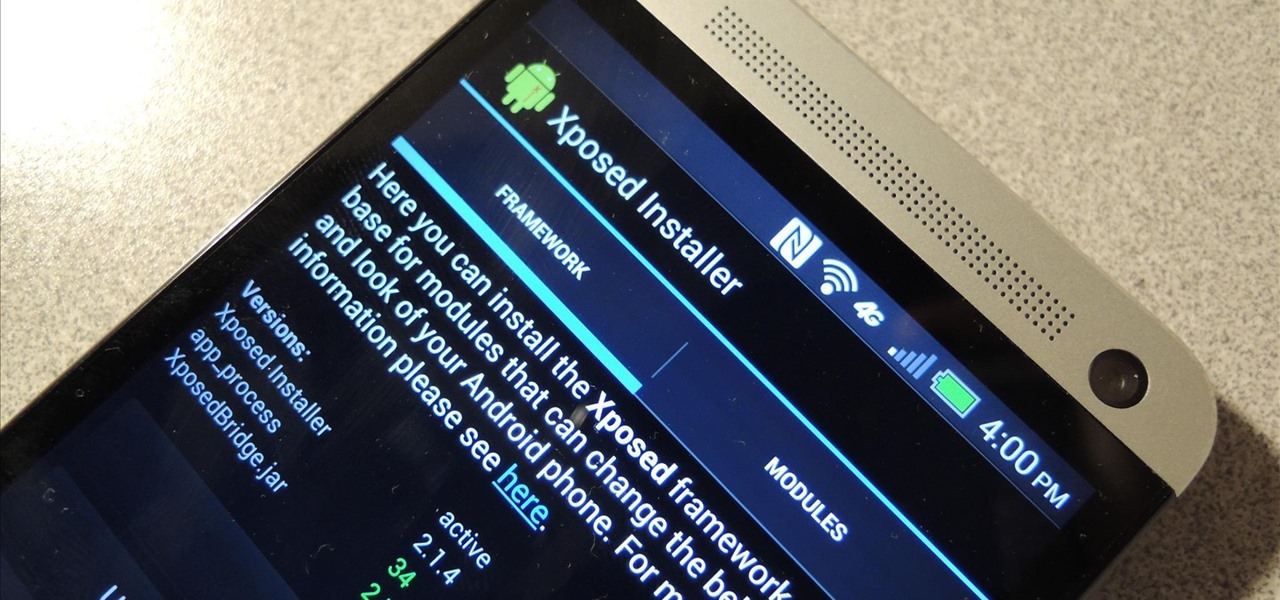
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the secrets that are lurking within Apple's newest mobile operating system.

Nine times out of ten, when you pick up your Samsung Galaxy Note 2, you already know what app you're going to be using. If you only have Swipe to unlock enabled, finding that app is as easy as swiping and locating the app on your Home screen or in the app drawer.
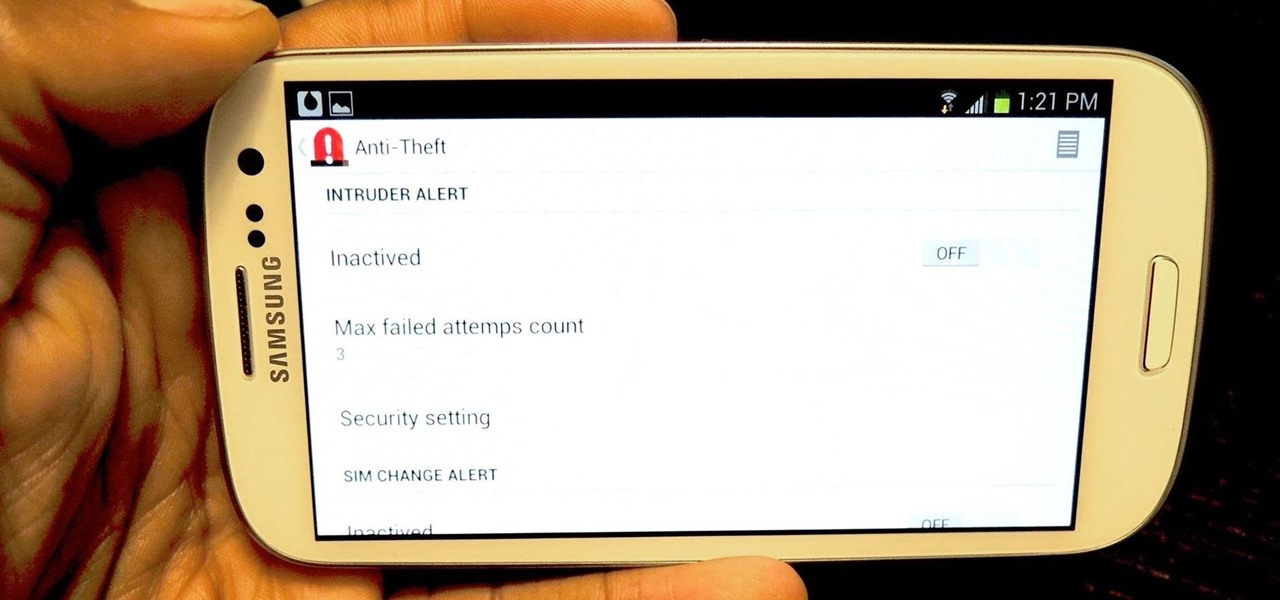
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.
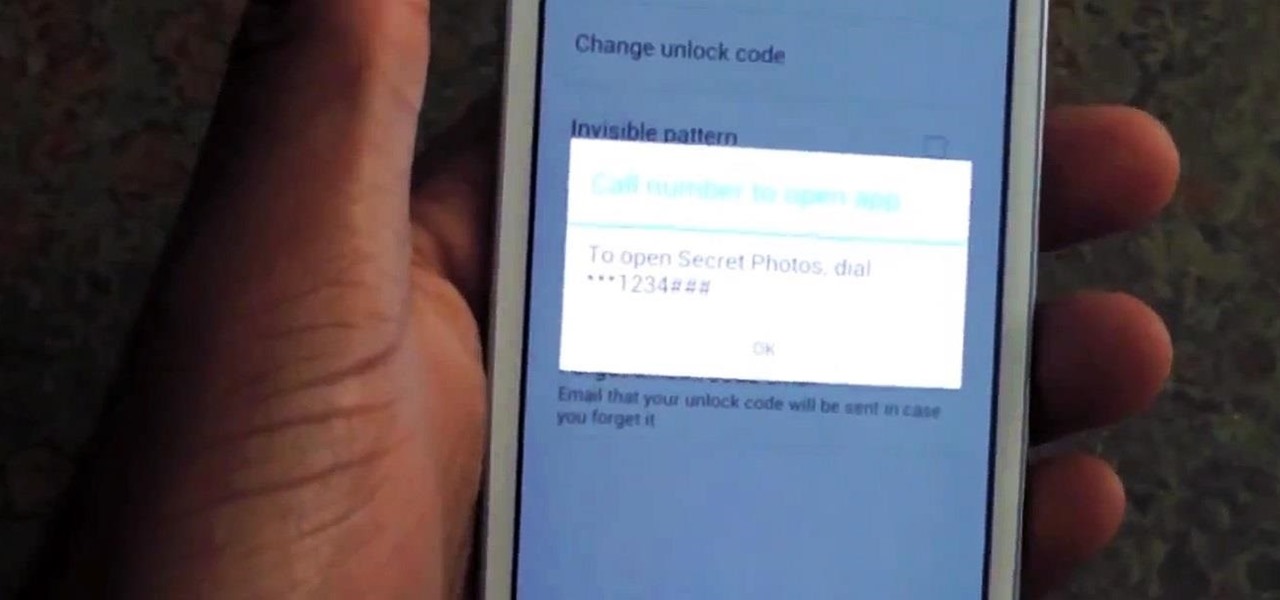
Whenever a friend borrows my Samsung Galaxy S3 to browse the web or make a quick call, I always pause to make sure there's nothing incriminating on it. I'm no superfreak, but some of my friends are, so I have more than a few photos on my device that I wouldn't wish upon anyone. I like to avoid these kinds of looks.

Video: . this codes help

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

Filming in low light is not easy, its tricky and challenging, but if you know the proper ways to set your DSLR camera even if you have the most ordinary lenses you can still capture great videos with less noise. So here are some settings and samples in Filming with your DSLR in Low light.

I go over how I draw a bug soldier. Quick drawing out of my head. I used a crummier camera on this one. For more videos go to:

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

Outdoor lighting is an important part of your landscape. It's serves multiple purposes, but wouldn't you want to make sure you're getting the right lights, for both daytime and nighttime use? Lowe's has the answers to help you plan and install outdoor lighting in your yard.

In this video from macmostvideo we learn how to import unsupported video in iMovie. This happens sometimes when you buy a camera that is not compatible with iMovie. You can add certain video formats to your Mac to make your Mac understand these video formats that don't work with your iMovie. A common one is called mpeg2. You can get this trough Apple. In other cases you get the software with the camera. If you need to convert a video file, try to open it through QuickTime first. If that works...
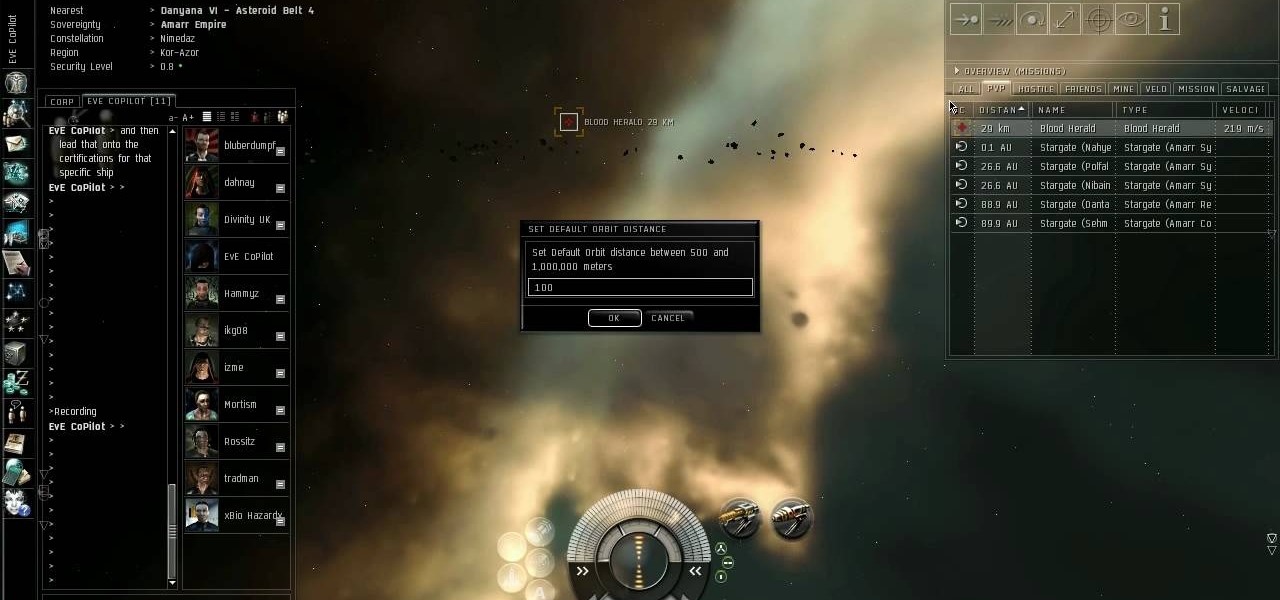
Quickly turn a profit during a combat mission by ratting - killing NPC enemies who spawn in asteroid belts. The difficulty of rats depends on how secure your system is - the lower security, the harder the rats are to kill. This tutorial shows you the best way, as a new player, to earn money by ratting.

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

You don't want anybody to have access to your cell phone. Nobody. Well, instead of the standard unlock mechanism, the one anybody can unlock your cell phone with, the Motorola DROID, and Android enable mobile device, allows you to create your own unlock pattern, secret to anyone else, which wakes it from sleep mode. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up a secure lock on a Motorola DROID cell phone.
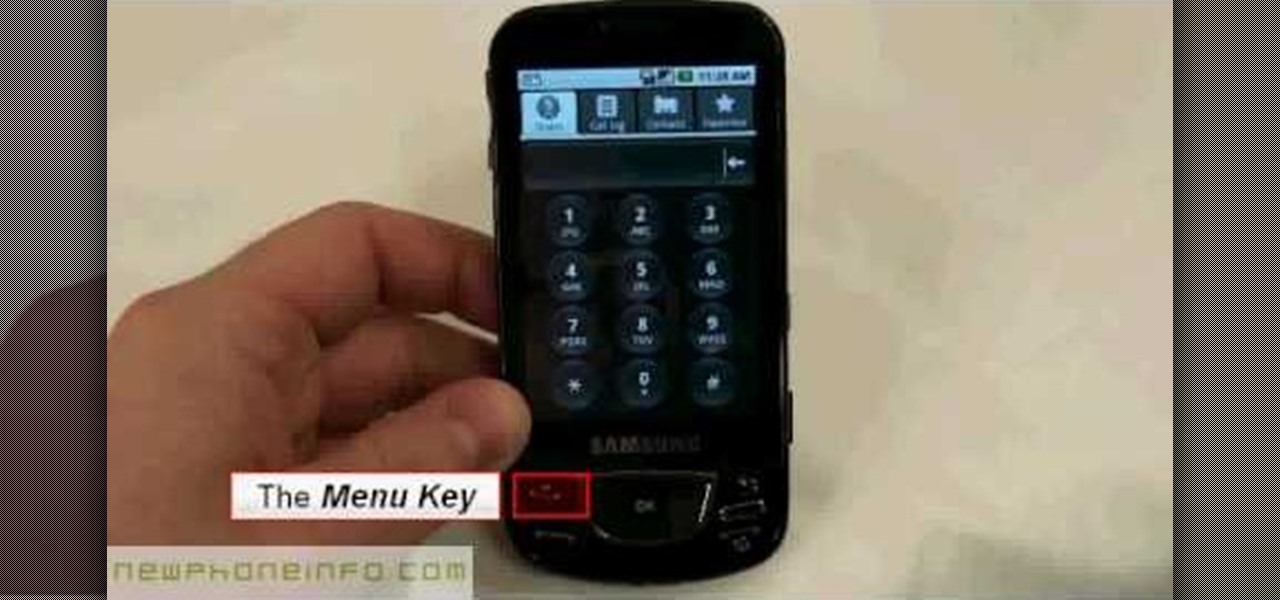
Follow this video to learn some basics on how to use a Samsung Galaxy I7500 mobile phone. Switch on the phone by pressing the power key in the bottom right corner. To navigate around the screen press with your finger on the touch screen and swipe to the left or right. If you want to open a particular application simply press the icon relating to it. Press the menu key to open the home screen with its various options. Press the dial key to open a screen where you can dial in the numbers for a ...
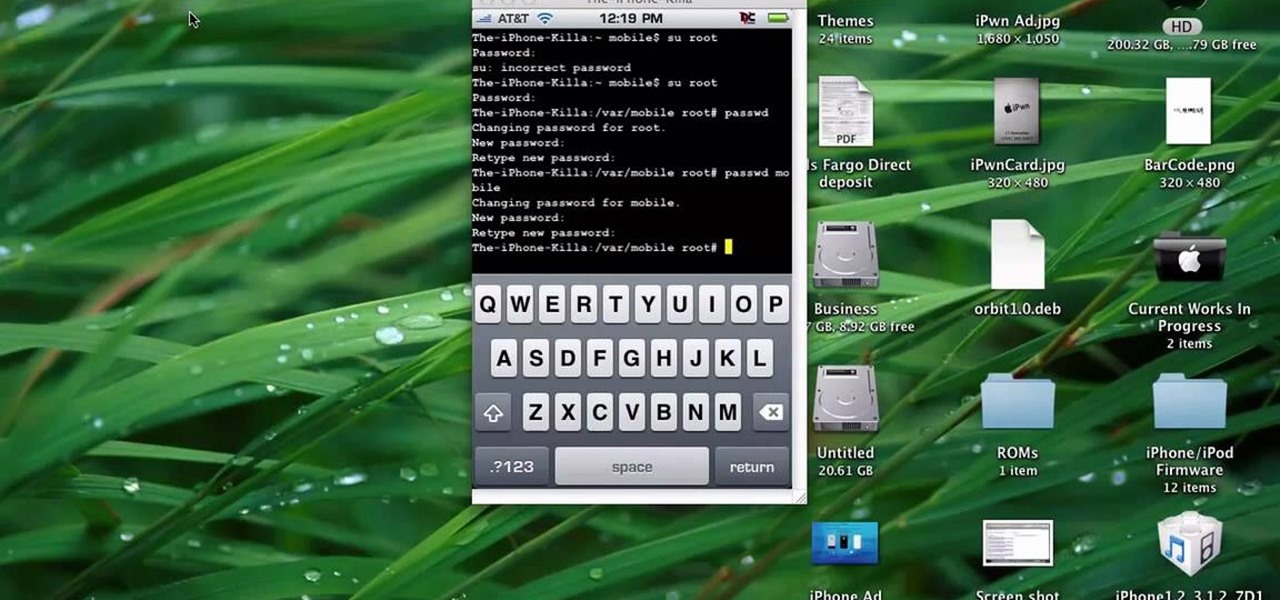
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

Make your way through The Saboteur for the Xbox 360. In the eighth mission in Act 1: Doppelganger, the ambassador will rendezvous with a German official near the Place des Vosges. Security will be tight around the ground level, but you should be able to find a vantage point among the rooftops. For more info, watch the whole gameplay.
New to Windows? No problem... here's a beginner's video tutorial that will teach you how to prevent cut, paste, copy, and delete on Windows files.

Check out this 2 part walkthrough of RE 5 Chapter 2-3 Savanna. This Resident Evil 5 Walkthrough is being played on Veterans Difficulty in Co-Op mode with Chris Redfield being played by Reule and Sheva Alomar being played by RavenVanHelsing.

Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Check out this walkthrough of Residential Evil 5, Chapter 6-2: Main Deck. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Before you attempt this firmware install, if you have already installed custom firmware on your PSP this measure might brick it. Don't double install if you have already hacked your PSP.

This kid has great instincts for teaching magic or card tricks as he instructs with multiple camera angles the best methods for shooting cards in the air. He also has different finger and grip techniques for multiple cards and different spins.

Need some smooth pan shots for your indie film? How about a cool dolly zoom effect? Well, you don't need to be a professional filmmaker to use such a device, but you do need the money for the gear. But—if you can work your way around the workshop, you can probably build your own camera dolly and track just fine. And for under $100! This video shows you how to build your own DIY dolly and dolly track, and all you need are the parts listed below. Then you just need to learn the art of the dolly...

The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.
If you're looking for a cool way to add text to your videos, like for an opening sequence to a film where the credits are displayed, embedding the text directly into the scene is the way to go, especially if you like the hit television show "Fringe", who used these kind of embedded title effects in establishing shots. Car adverts use this technique a lot, as well. "Panic Room" also use this effect in the opening title sequence.
Software needed: Voodoo motion tracker, virtual dub and blender

Breaking into a low-security lock is easy (and thus, why it's the subject of a googolplex number of Youtube tutorials made by mischievous prepubescent boys). But add a combination number to a lock and your lock-picking life gets much harder.

This video teaches how to increase the surface area of the support under your tripod by using snow shoes. You can get snow shoes from various manufacturers. The bottom of the snow shoe has a very wide surface area. You can compare this with the width of the tripod base. The snow shoe makes the tripod more stable on the ground when you are using it on mud or snow or on sand. The snow shoe stops your tripod from sinking into the ground. On top of the snow shoe, you have a little rubber strap an...
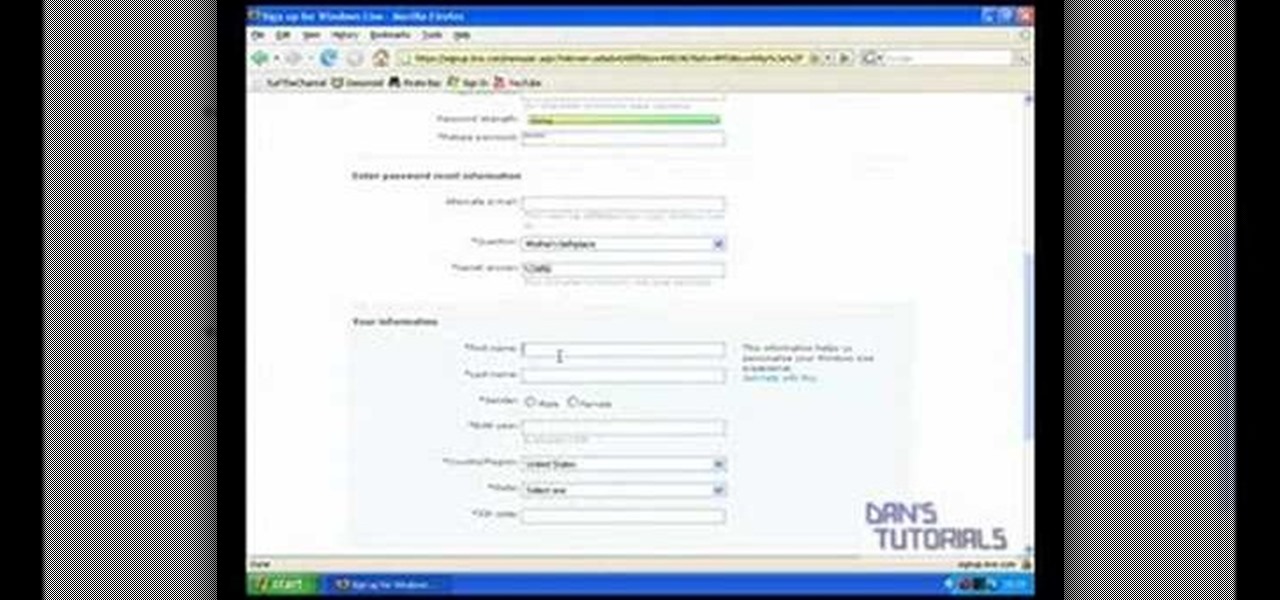
This tutorial shows how to create an email account in Windows Live. Use Google search to find the Windows Live Hotmail page. When you get to that page, click on the button that says, "Get it Free". On the next page, you can choose your email address, ending with either @live.com or @hotmail.com. If the email address is already in use, pick something else or add some numbers. Next, choose a password. There is a bar that shows how strong your password is. You can set a security question that ca...
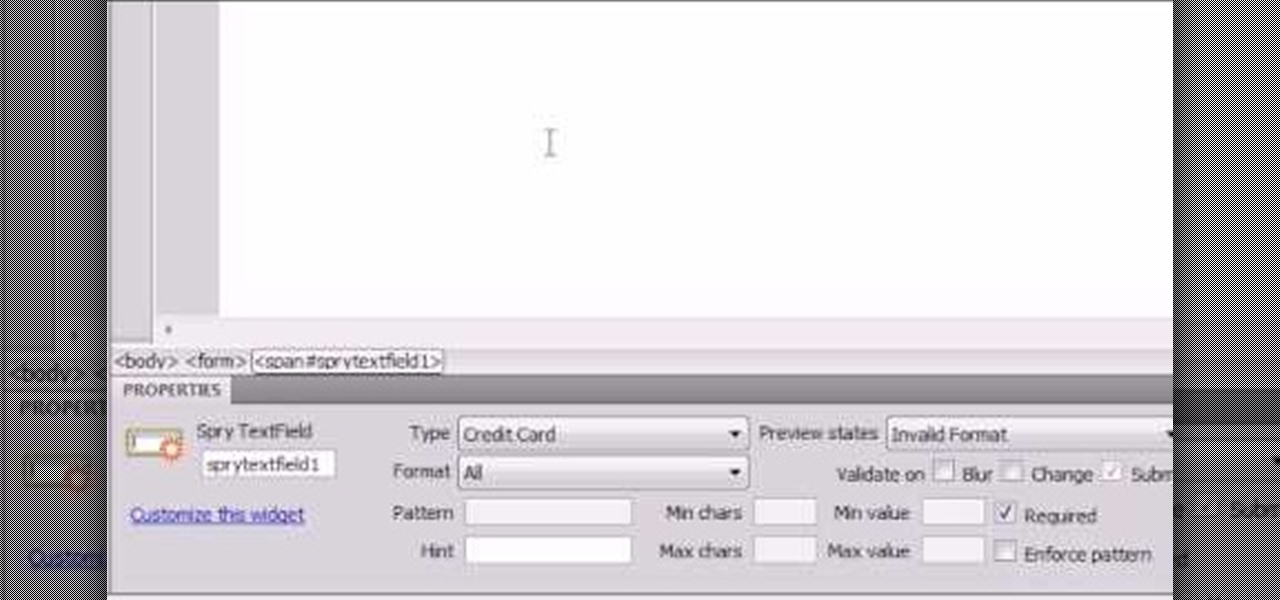
Here the New Boston shows you some tips about using the Spry Validation Text Field. To begin you will go to the Spry Validation Text Field, on Dreamweaver CS4. Looking at the bottom of the page notice the various options that are available for Properties. You find drop-down boxes for Type, Pattern, Minimum or Maximum values, Required, Enforce pattern, Format, Validate on, Blur or Change and Preview States. You can see the types of text available for validating by left mouse clicking the Type ...
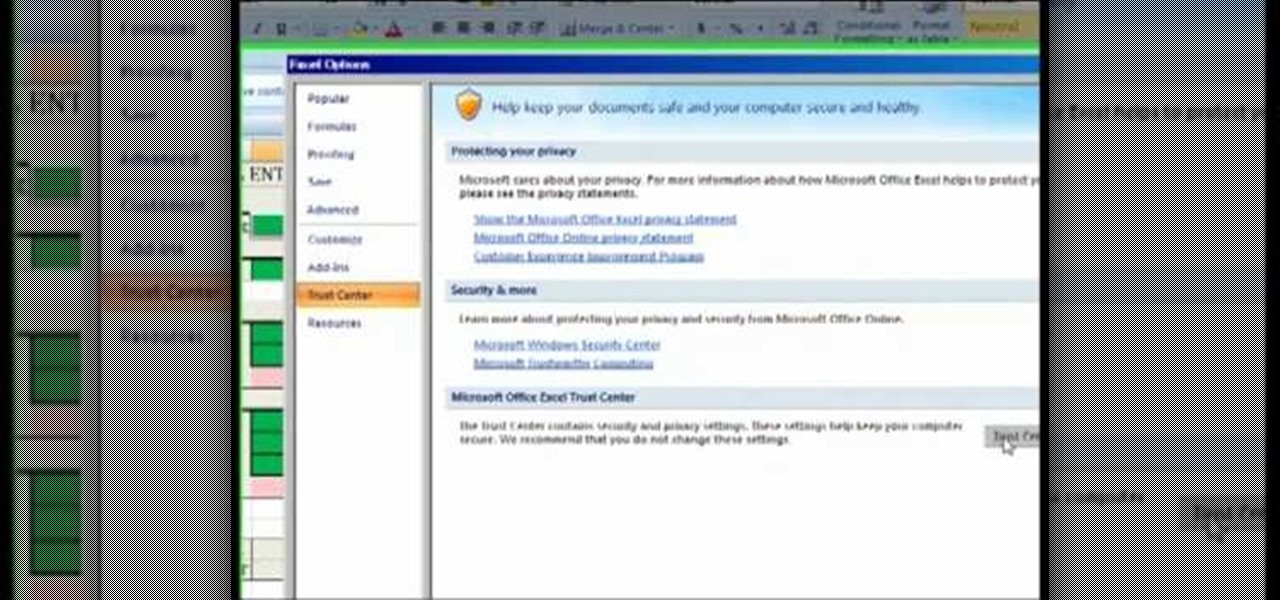
The Costsheet demonstrates how to enable macros in Excel 2007 to run correct spreadsheets. First, open up the spreadsheet. Make sure that the macros are enabled. If they have not, enable the macros by placing them in a trusted source by saving them in a particular folder. You can also choose to recognize the publisher as a trusted source. Click the office button and scroll down to Excel options. Click on the trust center option and go to trust center settings. Then, view the trusted locations...
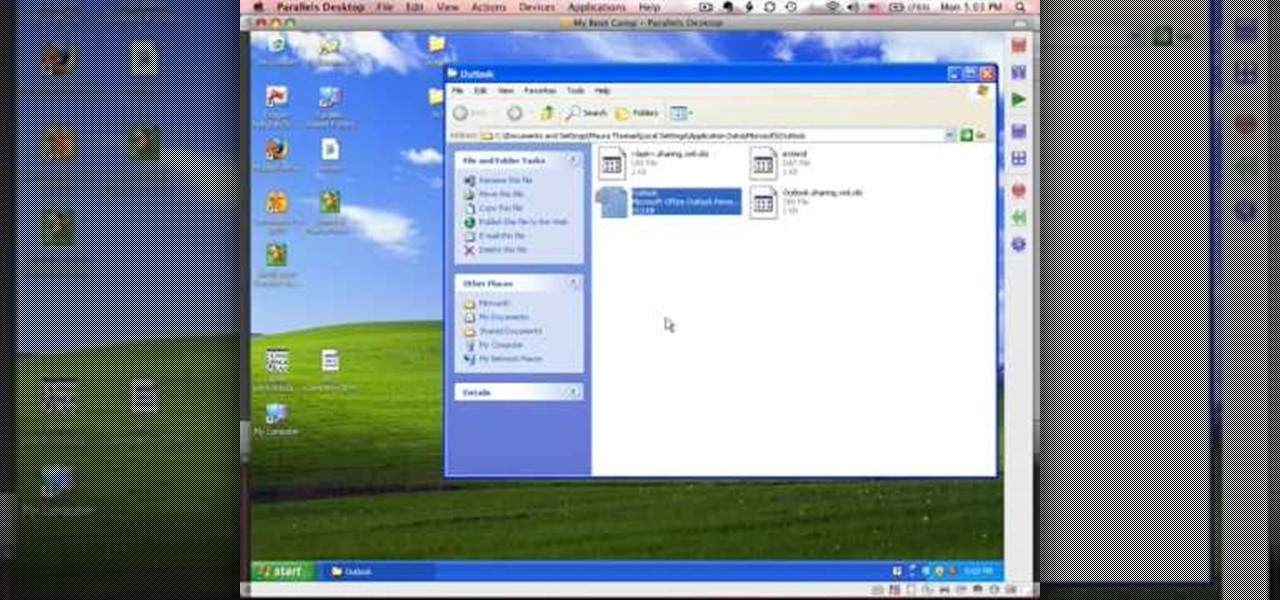
This tutorial describes how to backup the PST file of Outlook.

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.